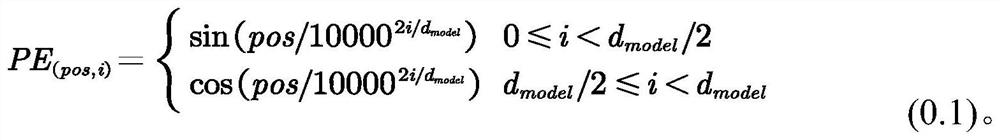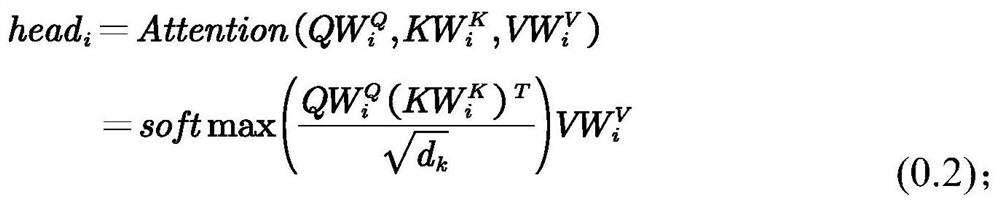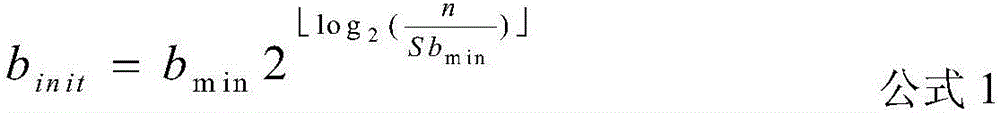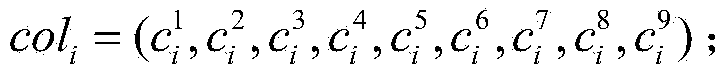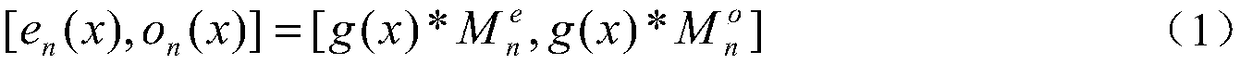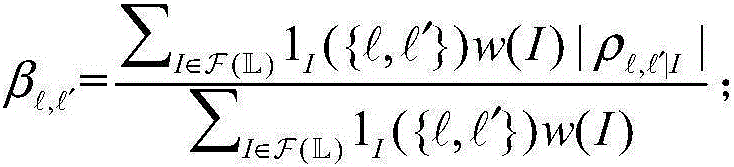Patents
Literature
42results about How to "Retain relevance" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
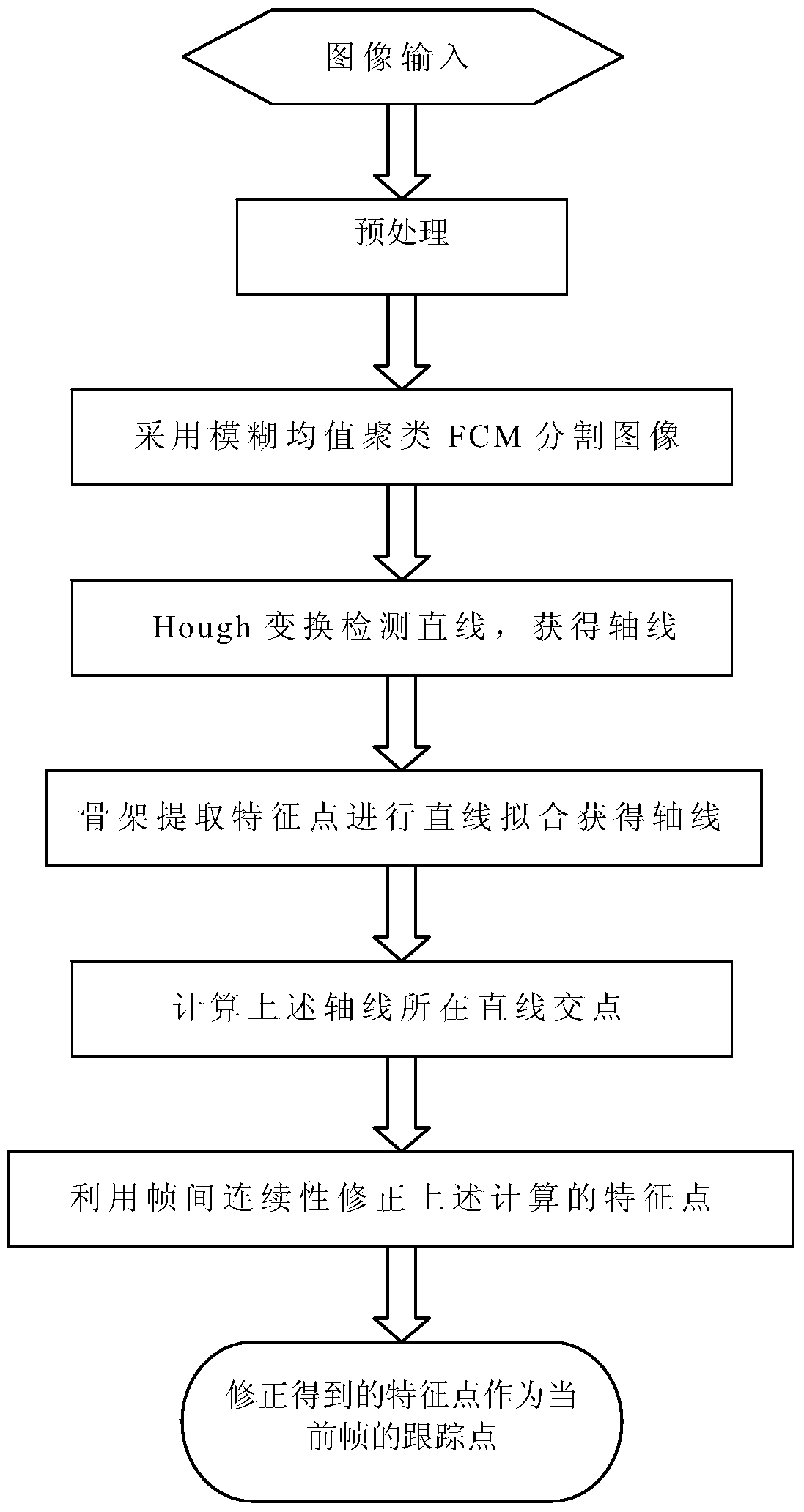
Method for tracking extended targets by means of extracting feature points by aid of frameworks
ActiveCN103632381AIn line with the real situationRetain relevanceImage enhancementImage analysisPattern recognitionIntersection of a polyhedron with a line
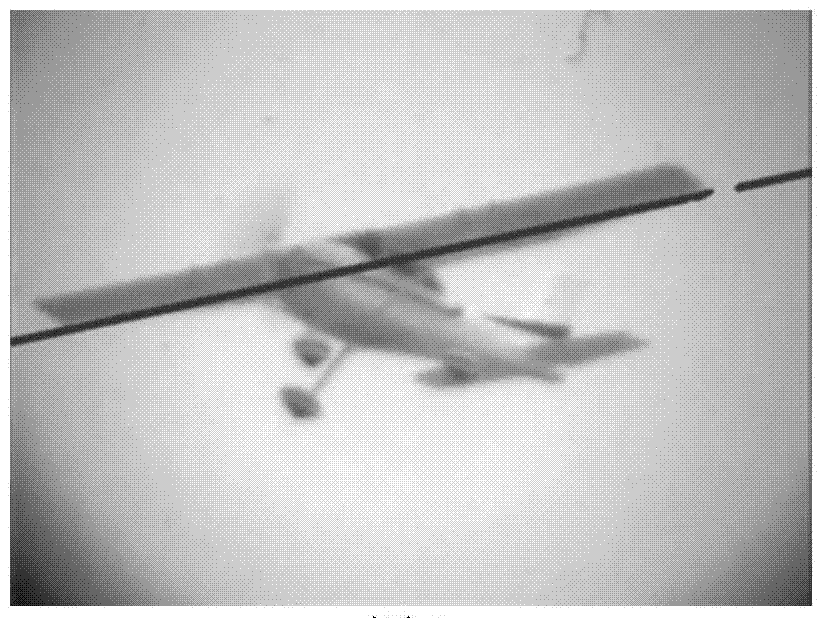
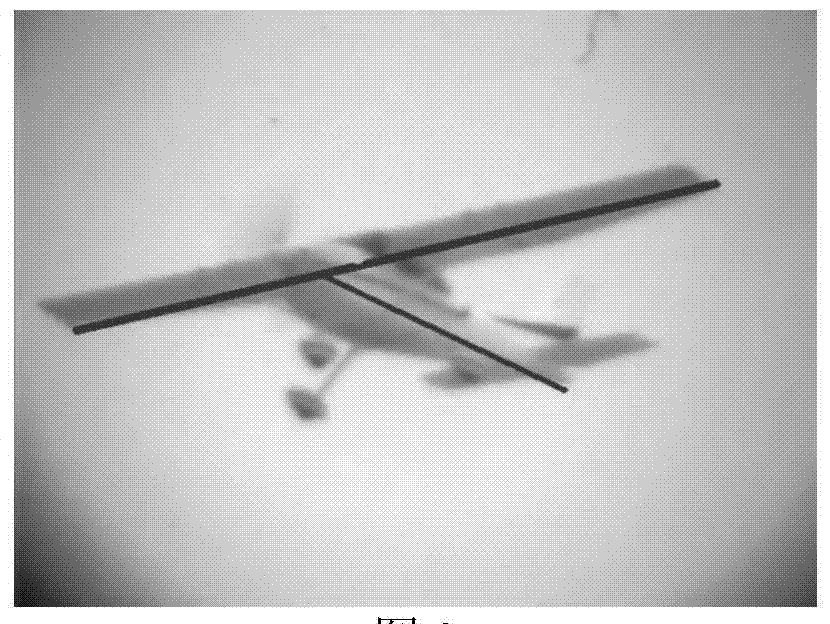
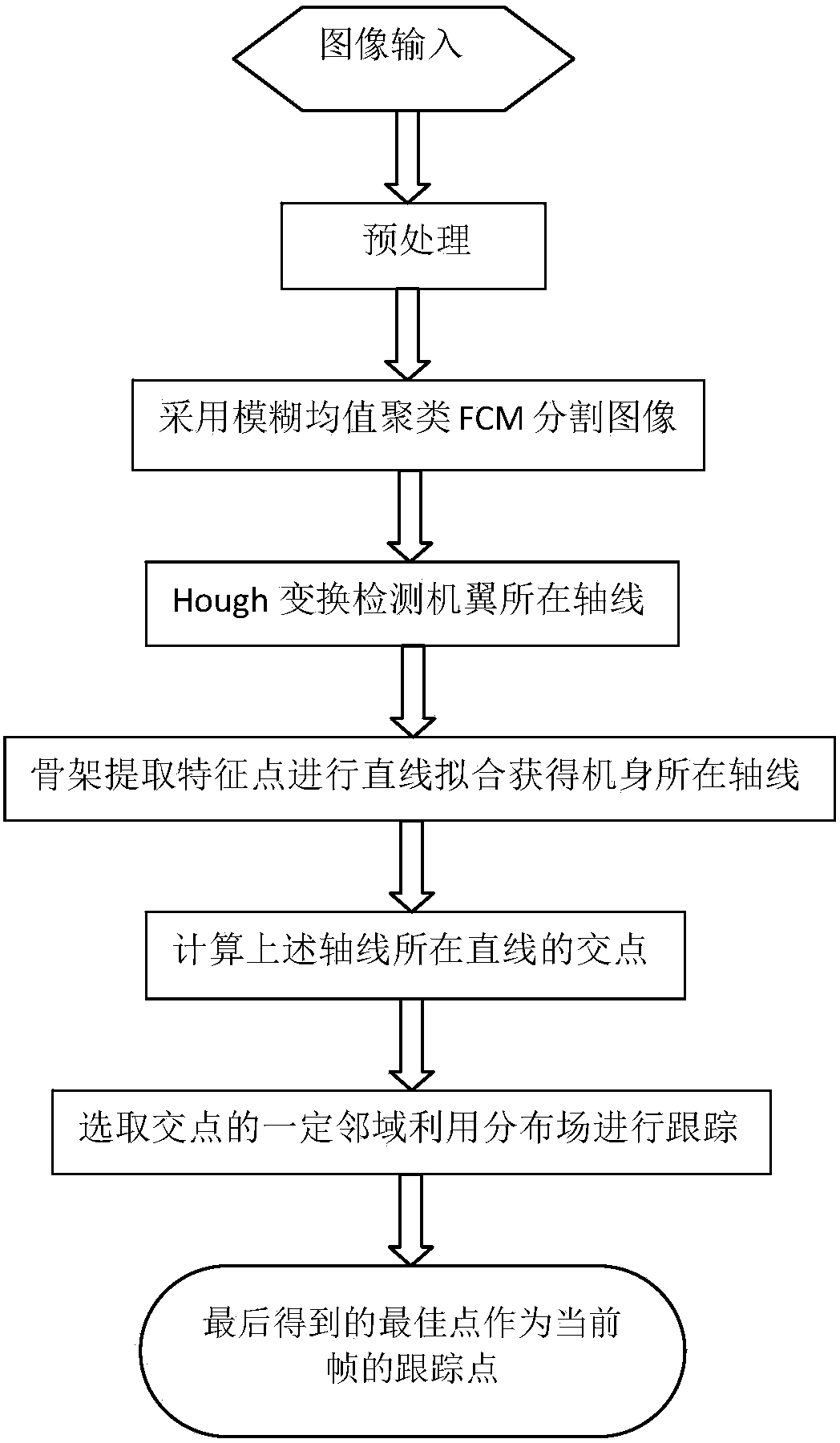
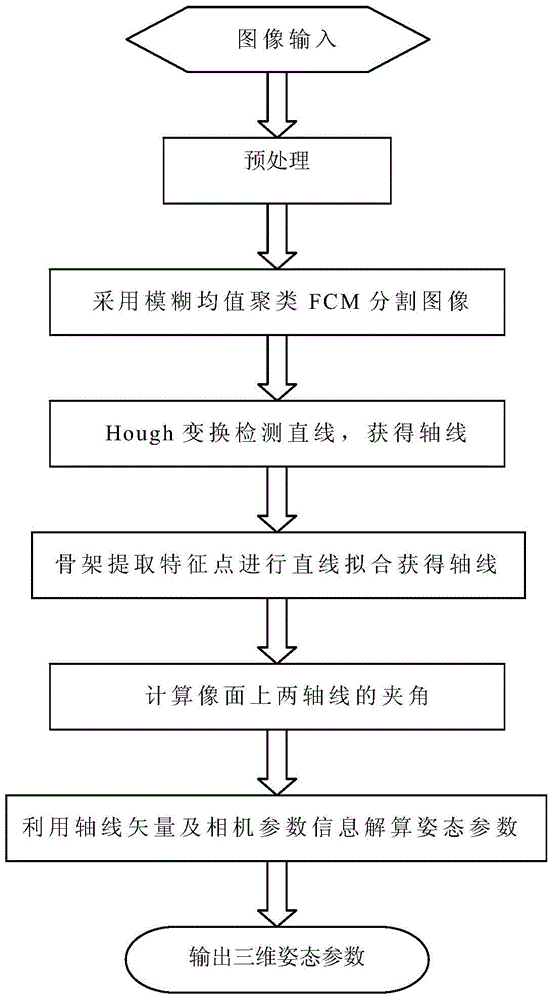
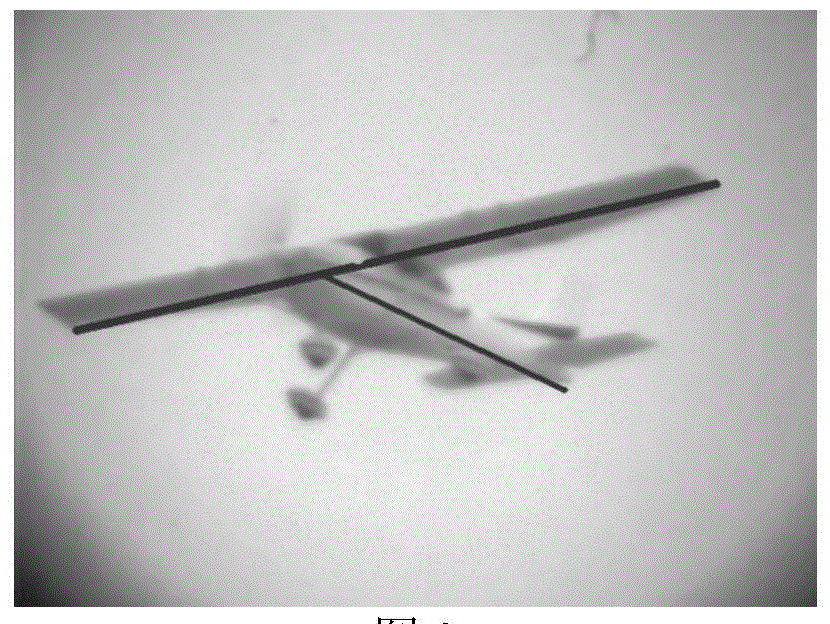
The invention discloses a method for tracking extended targets by means of extracting feature points by the aid of frameworks. The method includes preprocessing to-be-processed images by means of Gaussian smooth filtering so as to remove influence of noise on follow-up algorithms; dividing the smoothened images by an FCM (fuzzy C-means cluster) algorithm to acquire binary images; performing Hough transformation on the binary target images acquired by means of dividing the smoothened images, detecting first certain portions on the targets, extracting the feature points of second certain portions on the targets by the aid of the frameworks, linearly fitting the feature points on the frameworks to acquire axes of the targets, and utilizing intersection points of straight lines of the axes as final tracking points. Linear features of the first certain portions on the targets are obvious. Linear features of the second certain portions on the targets are unobvious. The method has the advantage that the targets can be stably tracked under the condition of violent posture change.
Owner:INST OF OPTICS & ELECTRONICS - CHINESE ACAD OF SCI
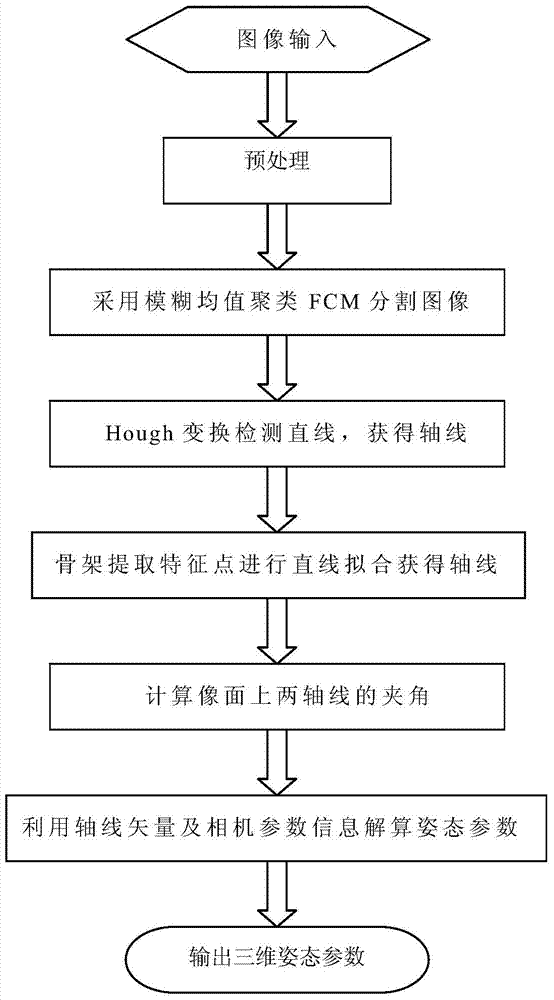
Airplane three-dimensional attitude computation method
ActiveCN103617328AIn line with the real situationRetain relevanceSustainable transportationSpecial data processing applicationsJet aeroplaneCluster algorithm
The invention provides an airplane three-dimensional attitude computation method. Firstly, preprocessing is carried out on an image to be processed by the adoption of Gaussian smooth filtering to eliminate influences of noise on follow-up algorithms; secondly, the smoothened image is segmented by the adoption of a fuzzy C-means clustering algorithm (FCM) to obtain a binary image, then Hough conversion is carried out on the binary image obtained through segmentation, a part, with obvious linear features, on a target is detected, feature points of the part, with non-obvious linear features, on the target are extracted by the adoption of a framework, and then linear fitting is carried out on the feature points on the framework to obtain a target axis; finally, the obtained axis, the actual size of the target, camera parameters and other information are combined, and a three-dimensional attitude parameter of the target under a camera coordinate system is calculated by means of projective geometry knowledge. On the basis of geometrical features capable of reflecting the structure of an object and by means of Hough conversion and framework extraction of the whole target image, the obtained axis is more accurate, and the obtained three-dimensional attitude parameter is more precise.
Owner:INST OF OPTICS & ELECTRONICS - CHINESE ACAD OF SCI
Extended target tracking method based on combination of skeleton characteristic points and distribution field descriptors
InactiveCN103854290ARetain relevanceImprove noise immunityImage analysisCluster algorithmHough transform
The invention provides an extended target tracking method based on combination of skeleton characteristic points and distribution field descriptors. The extended target tracking method comprises the following steps: firstly, preprocessing images to be processed by using Gaussian smooth filtering to remove influence of noise on a subsequent algorithm; and subsequently, cutting the smoothed images by using a fuzzy C-means clustering algorithm FCM to obtain binary images, carrying out Hough transform on the cut and obtained binary images to detect a part with an obvious linear characteristic on the target, extracting characteristic points from a part without obvious linear characteristic on the target by using a skeleton, then carrying out linear fitting on the characteristic points on the skeleton to obtain a target axis, taking a intersection point of the straight lines of the obtained axis as an initial track point, then calculating a distribution field in a certain neighborhood field of the point and searching a best position in the neighborhood field when a next frame comes, so as to obtain the current best track point. Through the extended target tracking method, the fuzziness problem is solved; and the extended target tracking method is capable of stably tracking the extended target under a condition with a great posture change.
Owner:INST OF OPTICS & ELECTRONICS - CHINESE ACAD OF SCI
Multi-region power load time sequence scene modeling method considering time-space correlation
ActiveCN111401757ARetain relevanceGood precisionCharacter and pattern recognitionResourcesAlgorithmMulti dimensional data
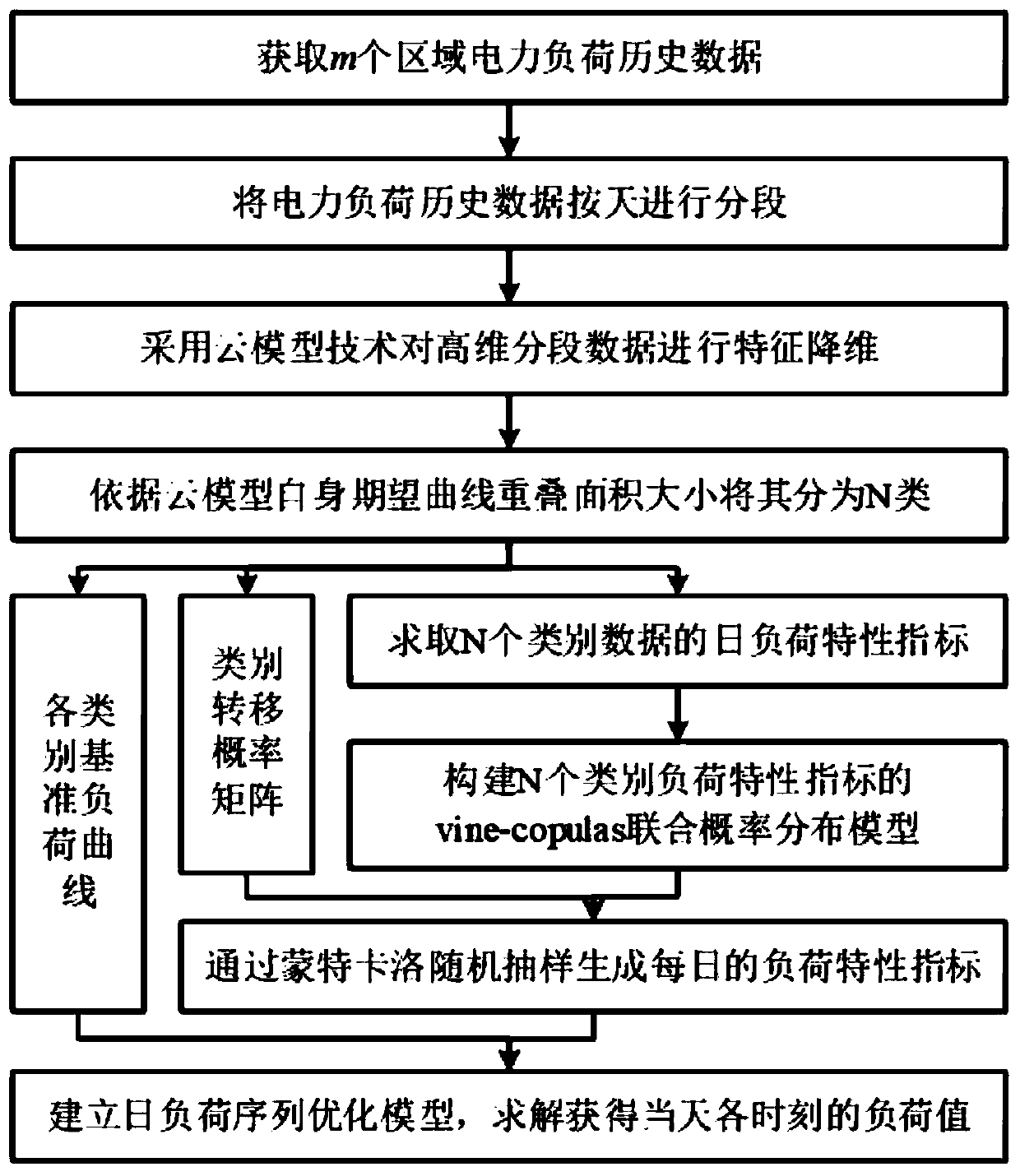
The invention discloses a multi-region power load time sequence scene modeling method considering time-space correlation, and the method comprises the steps: firstly employing segmented cloud to approximately reduce the dimensions of a time sequence, measuring the similarity between segmented time sequences through the overlapping area of a cloud model, and clustering multi-dimensional data; secondly, based on the daily load characteristic index of each type of time series data, establishing a correlation copula model of a plurality of regions by constructing vine-copulas joint probability distribution; and finally, establishing a daily load sequence optimization model based on each type of reference load curve, and obtaining a multi-region power load time sequence scene with correlation.According to the method, the effectiveness and the practicability of the method are verified by comparing different scene generation methods and load characteristic index results.
Owner:XI AN JIAOTONG UNIV +1
Speech translation method and system
ActiveCN111783477AReduce mismatchReduce training difficultyNatural language translationInternal combustion piston enginesSpeech translationWord list
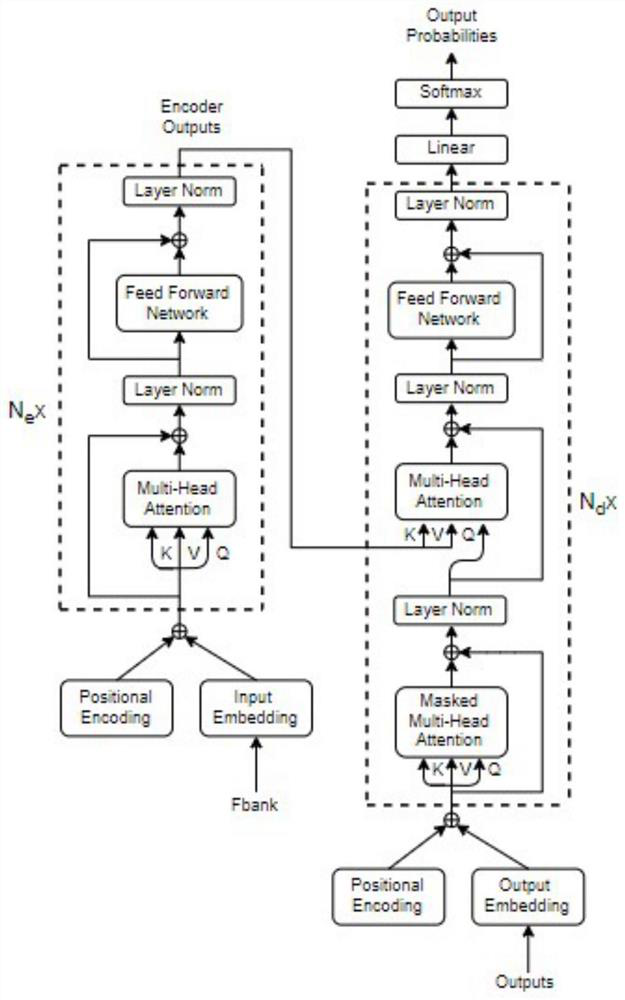
The invention discloses a speech translation method and a speech translation system. The speech translation method comprises the following steps of: constructing a small language and mandarin replaceable word list; constructing a sub-word dictionary; carrying out one-hot coding on each character; to-be-recognized voice is acquired, and voice features are extracted; calculating a position coding vector of the to-be-recognized voice feature; summing the to-be-recognized speech features and the position coding vectors; inputting a to-be-recognized input vector into the trained speech translationmodel; and outputting the recognition text by the speech translation model. According to the invention, the training difficulty of the speech translation model is reduced and the training speed is improved.
Owner:XIAMEN KUAISHANGTONG TECH CORP LTD
3D (three-dimensional) video signal compression coding-decoding method, device and system
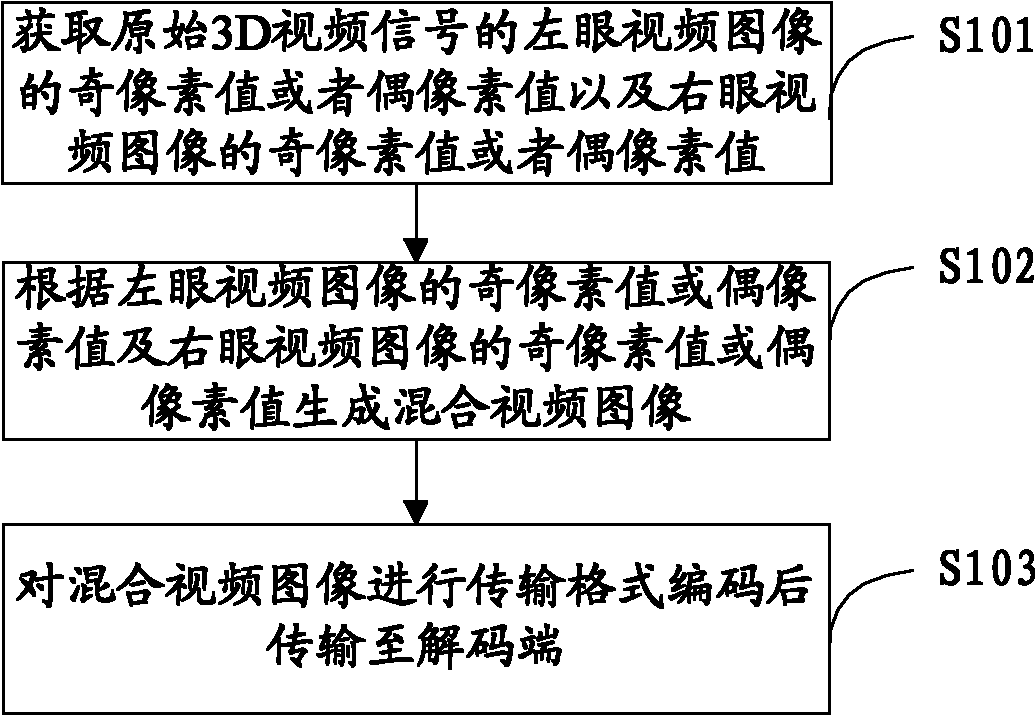
ActiveCN102215405AImprove clarityHigh resolutionTelevision systemsDigital video signal modificationCoding decodingSignal compression
The invention is suitable for the field of multimedia information processing and provides a 3D (three--dimensional) video signal compression coding-decoding method, device and system. The compression coding method comprises the following steps: obtaining an odd pixel value or an even pixel value of a left eye video image and an odd pixel value or an even pixel value of a right eye video image of an original 3D video signal; and generating a hybrid video image according to the odd pixel value or even pixel value of the left eye video image and the odd pixel value or even pixel value of the right eye video image. The size of the newly generated hybrid video image is the same as that of the left or right eye video image so as to solve the problem of insufficient transmission bandwidth; and meanwhile, various frequency components of the left and right eye video images are completely preserved to reduce the distortion of the images, and the relativity of the left eye video image and the right eye video image is basically preserved so that the efficiency of coding and decoding the transmission format of the hybrid video image is high, and the compression ration is high.
Owner:SHENZHEN SKYWORTH RGB ELECTRONICS CO LTD
Time sequence classification method and system based on time sequence two-dimension and width learning
InactiveCN112766360ARetain relevanceIncrease time costCharacter and pattern recognitionNeural architecturesFeature extractionDimensionality reduction
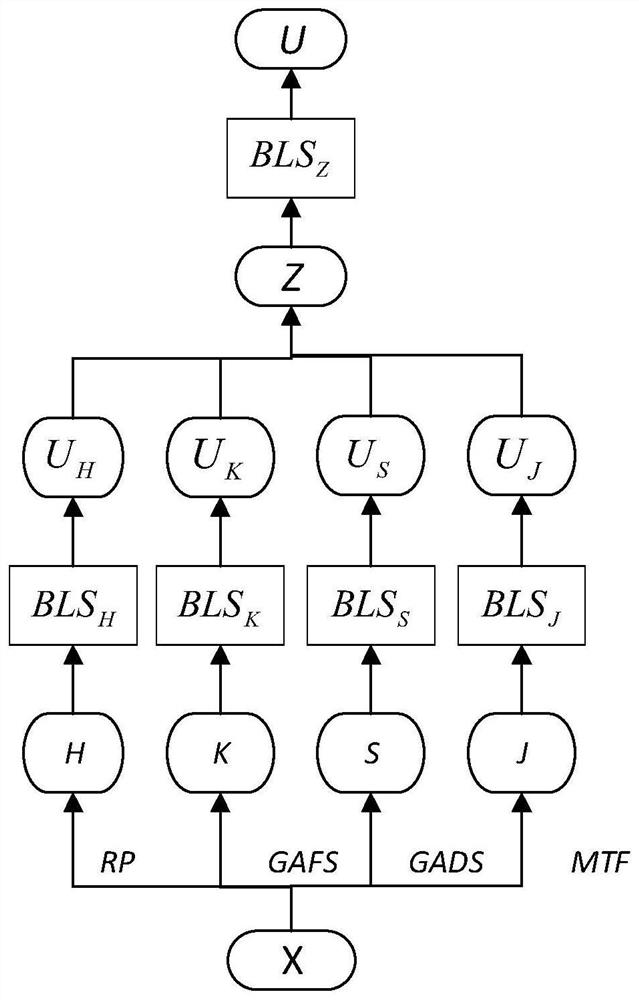
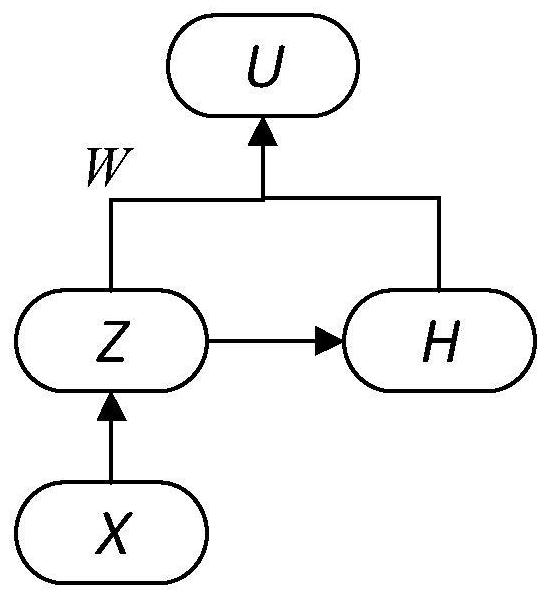
The invention discloses a time sequence classification method based on time sequence two-dimension and width learning, and the method comprises the following steps: 1), carrying out the normalization processing of input data, and obtaining X; 2) performing feature extraction on X by using four sub-width learning systems and width learning to obtain an input U of the deep cascade width learning system; and 3) classifying the input data U by the deep cascade width learning system. According to the method, width learning and time sequence two-dimensionalization are combined, a feature extraction mode is provided, the features of the time sequence can be fully extracted, the dimensionality reduction effect can be achieved, and data more suitable for a deep cascade width learning system can be extracted. After feature extraction is completed, a deep cascade width learning system is used for classification, so that the time cost and the calculation cost can be remarkably reduced. The invention further provides a time sequence classification system based on time sequence two-dimension and width learning.
Owner:ZHEJIANG UNIV OF TECH
Sparse representation three-dimensional point cloud compression method adopting geometric guidance
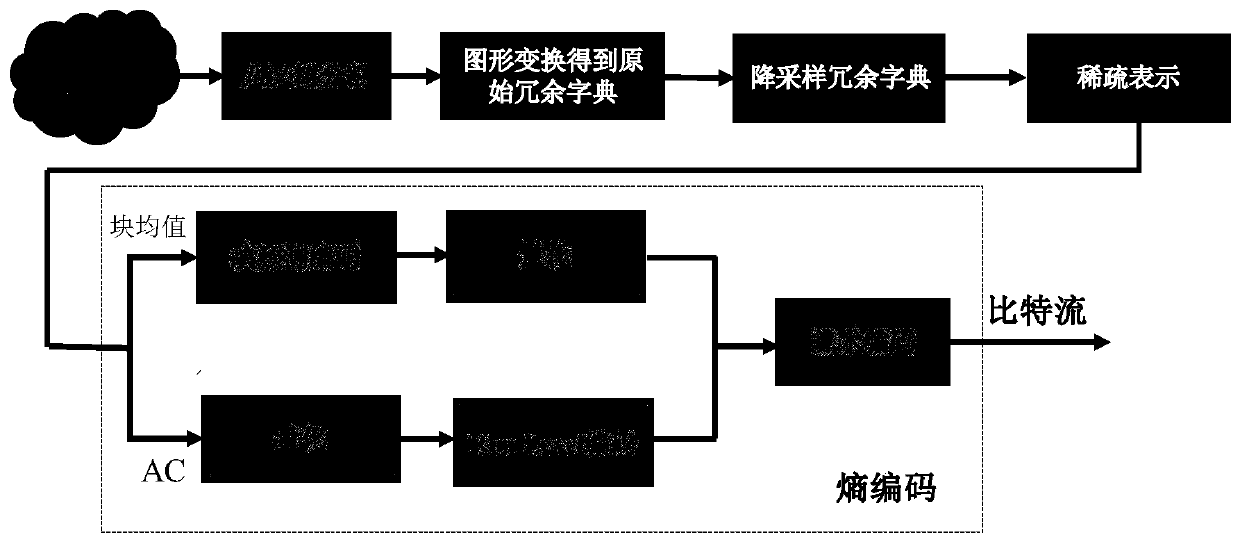
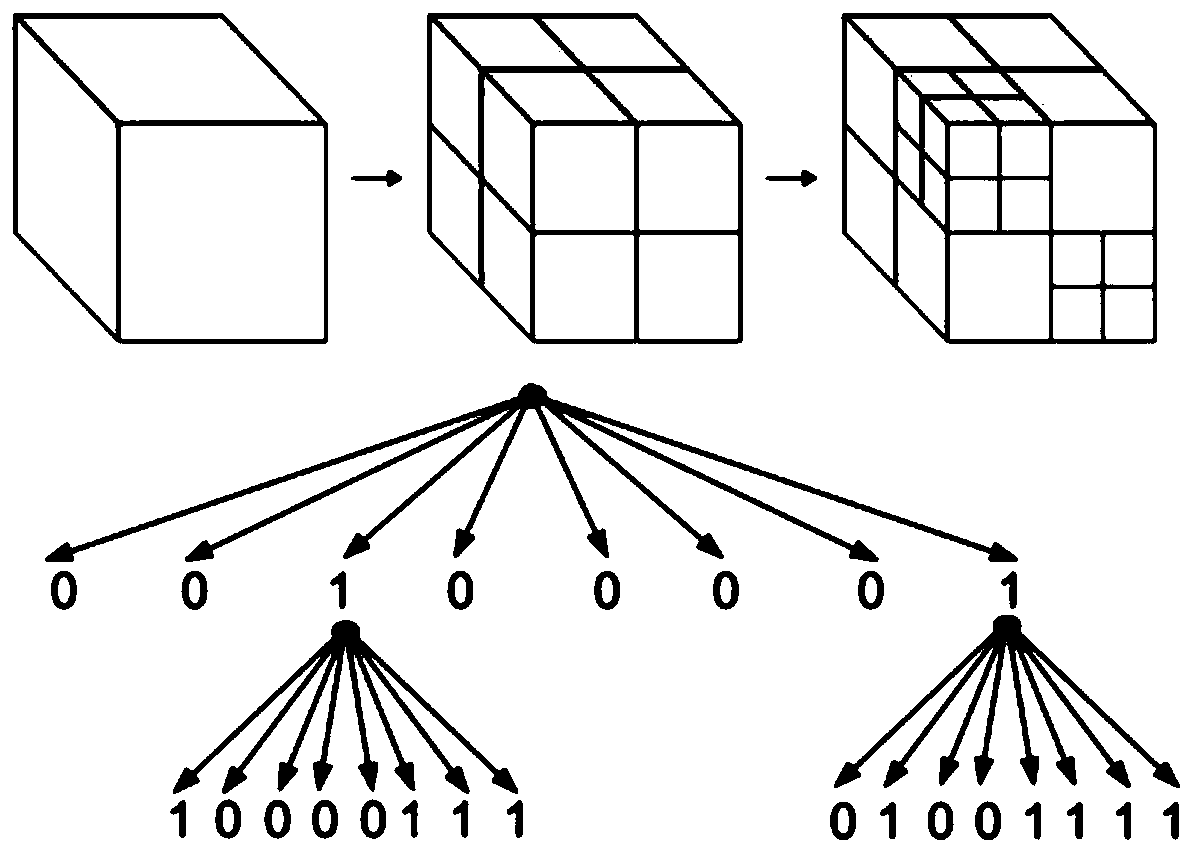
ActiveCN110278444ARetain relevanceSame sizeDigital video signal modificationGraphicsPrediction algorithms
The invention discloses a sparse representation three-dimensional point cloud compression method adopting geometric guidance, and belongs to the field of video coding. The method comprises the steps of partitioning an input three-dimensional point cloud through an octree; obtaining an original redundant dictionary by adopting a graphic transformation method; down-sampling the original redundant dictionary by using the geometrical information of the point cloud in the block; carrying out mean value removal on each unit block, and then carrying out sparse representation on the color information subjected to mean value removal on a down-sampling dictionary; performing predictive coding on the mean value of each coding unit block by utilizing a block mean value prediction algorithm based on the octree; encoding the quantized sparse coefficient by adopting a Run-Level method; and finally, carrying out entropy coding on all coded parameters by using an arithmetic coder. According to the method, by utilizing the sparse representation, the huge three-dimensional point cloud data can be efficiently compressed, and the transmission and storage efficiency of the three-dimensional point cloud is greatly improved.
Owner:HUAQIAO UNIVERSITY
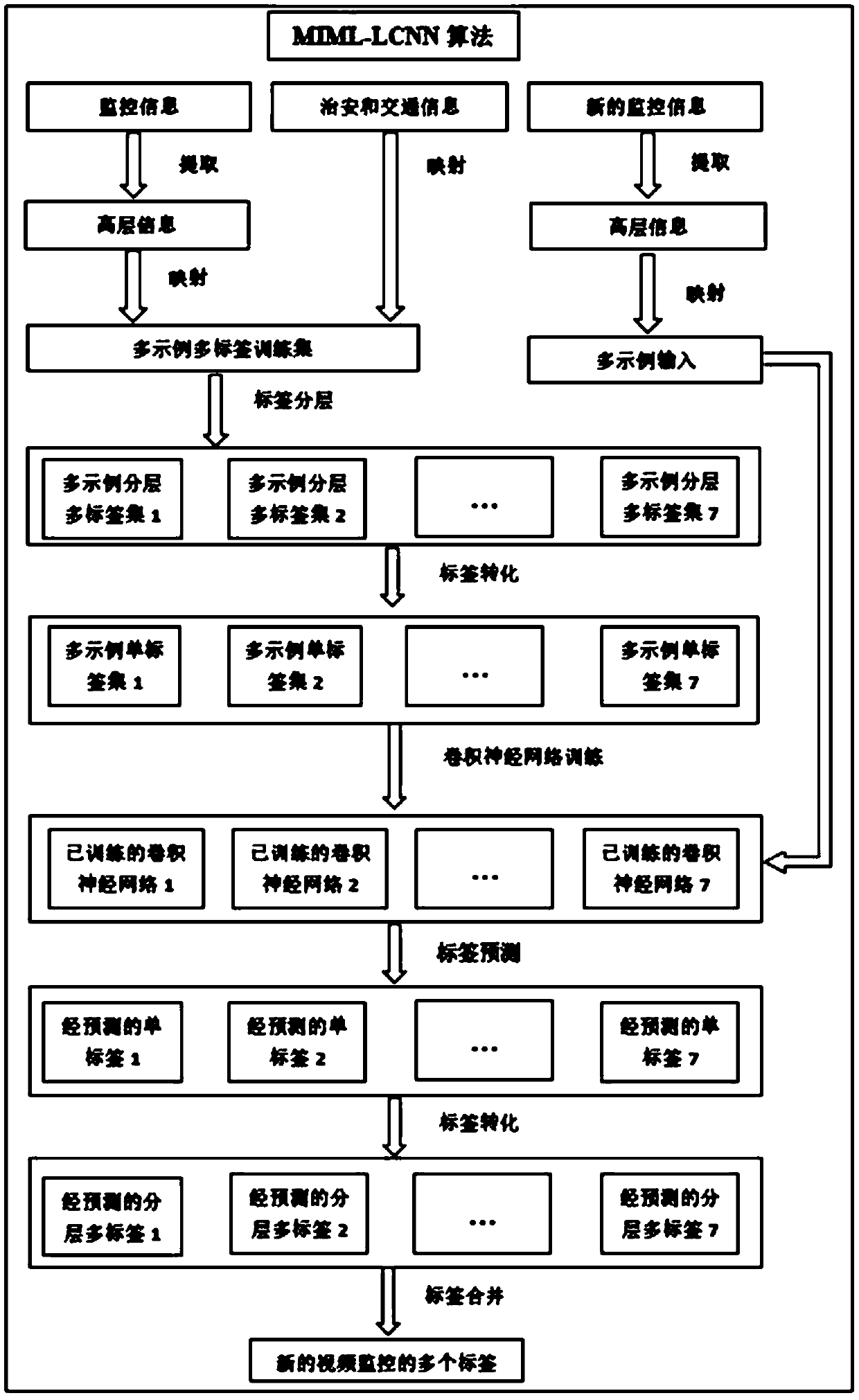
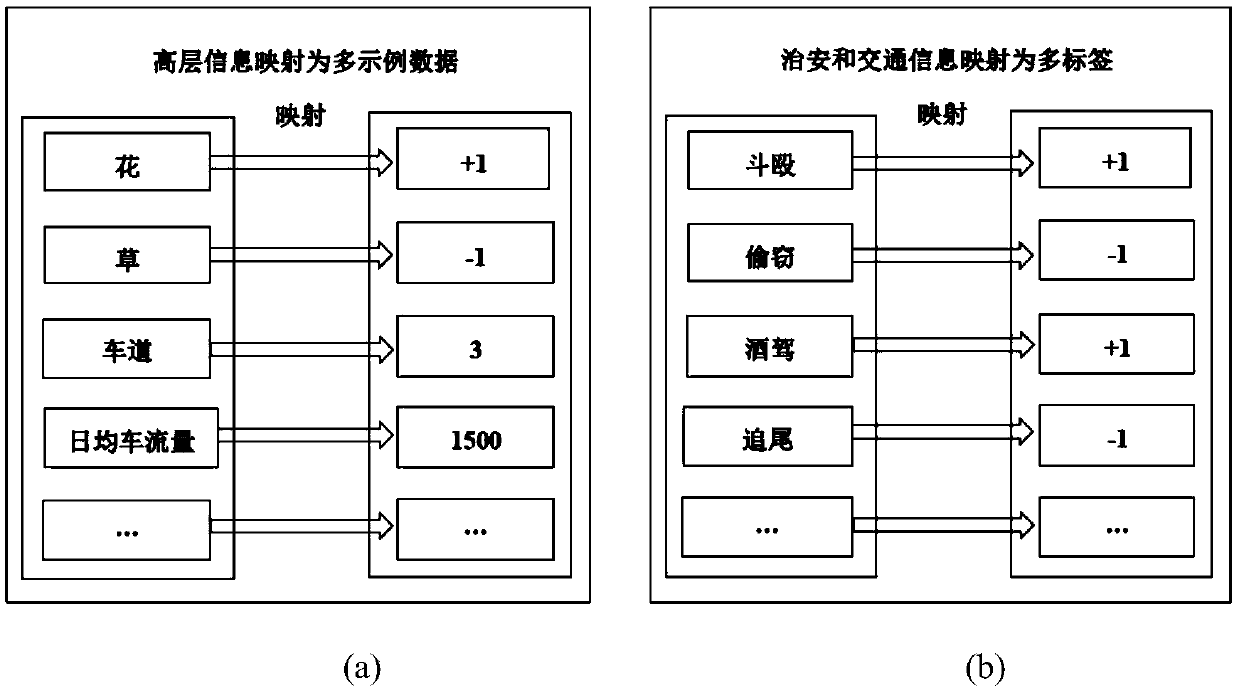
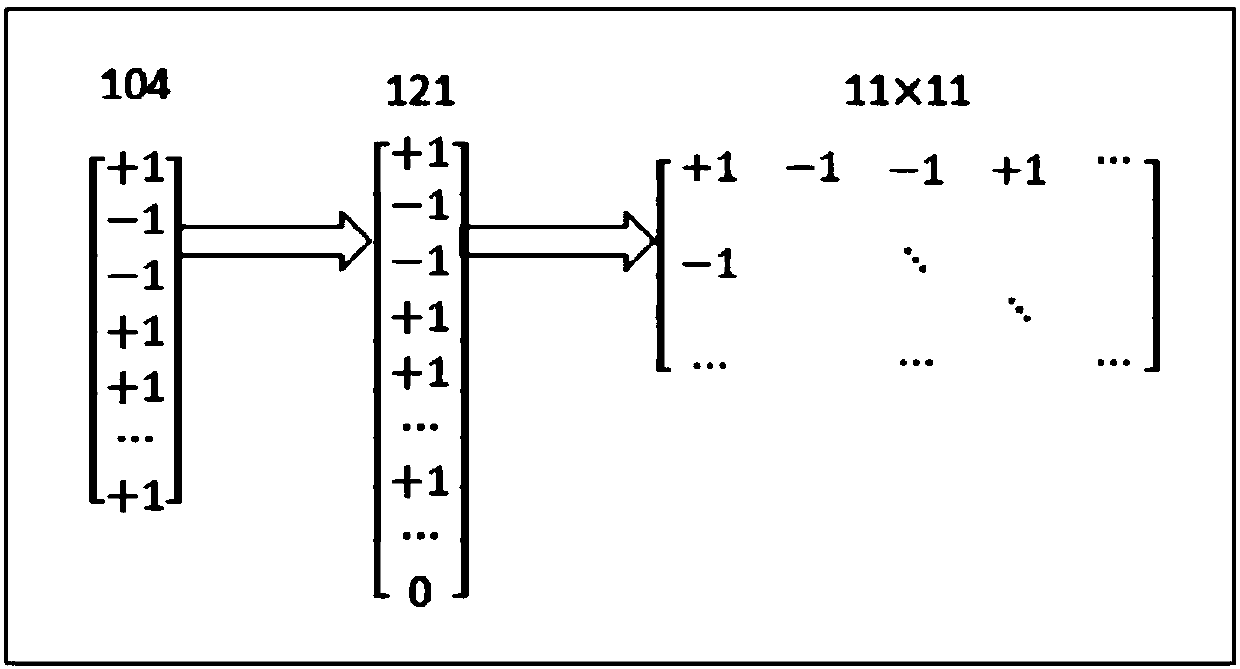
Multi-example multi-label learning method for video surveillance application of safe city
ActiveCN108764192ASolve too many problemsPrediction is accurateCharacter and pattern recognitionNeural architecturesVideo monitoringData set
The invention discloses a multi-example multi-label learning method for a video surveillance application of a safe city. The invention obtains a multi-example multi-label data set of video surveillance of a safe city, and taps the internal connection between the multi-example data and the multi-tag data to predict the new video surveillance so as to determine the possible multiple security and traffic conditions implied in the area where the new video surveillance is located. The invention mainly contributes to two aspects, which firstly adopts a layered label strategy to solve the problem ofa large number of labels, thereby achieving the goal of retaining the integrity of multiple tags without losing the associated information between the labels, and secondly induces the convolutional neural network into the video surveillance network of a safe city at the first time, thereby fully deep learning the correlation between examples by taking advantage of the convolutional neural network,and fully exploring the information between the examples.
Owner:HUAZHONG NORMAL UNIV
JPEG image bit stream encryption method based on alternating current statistical characteristic change
ActiveCN109889687AImprove securityIncrease aggressivenessDigital video signal modificationComputer hardwareBitstream encryption
The invention discloses a JPEG image bit stream encryption method based on alternating current statistical characteristic change. The method comprises: in a JPEG bit stream, a user selects the last non-zero communication coefficient entropy code in a part of image blocks by using a user key to encrypt; hiding the secret information into a part of image block entropy codes through a histogram translation method; statistical characteristics are obtained through a user secret key and an alternating current coefficient, a direct current coefficient encryption secret key and an alternating currentcoefficient encryption secret key are generated in a self-adaptive mode, inter-group scrambling and differential coding iteration scrambling are carried out on the direct current coefficient, and intra-block scrambling and inter-block scrambling are carried out on the alternating current coefficient; and the receiver extracts secret information from the encrypted bit stream and decrypts the secretinformation, recovers the direct current coefficient and the alternating current coefficient encryption key according to the user key and the alternating current coefficient statistical characteristics in the encrypted bit stream, decrypts the alternating current coefficient and the direct current coefficient, recovers the alternating current coefficient entropy code in each image block entropy code, and obtains the original bit stream. The method is high in security and small in encrypted file expansion.
Owner:SOUTHWEST JIAOTONG UNIV
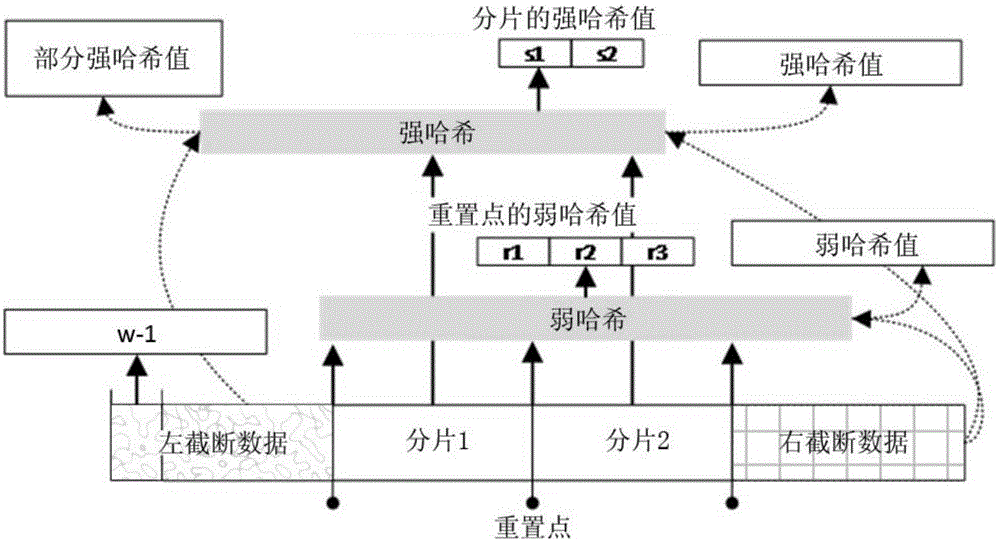
A real-time summary generating method for streaming data
ActiveCN106407400ARetain relevanceReduce occupancyFuzzy logic based systemsSecuring communicationMemory footprintStream data
The invention provides a real-time summary generating method for streaming data. Streaming data summary calculation is performed by employing the method of storing intermediate calculation results, and the phenomena of data shortage and damage, disorder and overlapping can be handled; the matrix multiplication is used as the strong Hash algorithm to reduce memory occupation, so that the method can calculate streaming data summaries in real time with less memory.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
Medical data processing method for predicting cardiovascular disease
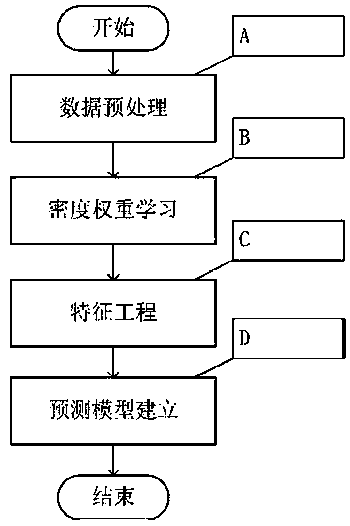
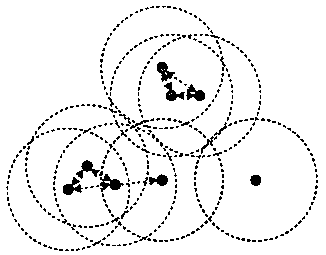
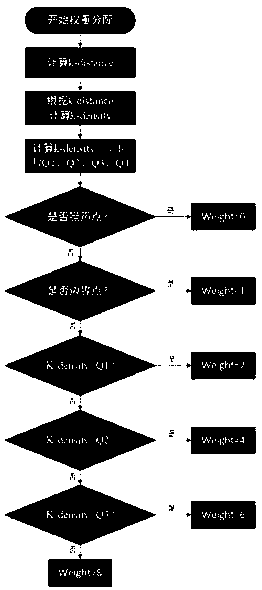
PendingCN110176309AHighlight substantiveIn line with the real situationMedical simulationMedical data miningData setAlgorithm
The invention provides a medical data processing method for predicting a cardiovascular disease. The method of the invention comprises three steps of 1, data preprocessing, filling deletion values ina data set, and performing standardizing processing on the attribute in the data set; 2, performing density weight learning, based on a fact that the sample points are divided into core sample points,noise sample points and boundary sample points by means of a DBSCAN algorithm, further quantifying density information of the core sample points, and endowing different weights to points in the areaswith different densities; and 3, performing characteristic engineering, adding the weight values of all sample points as one-dimensional new characteristics into the data set, and then performing characteristic selection and data discretization on the whole data set. According to the medical data processing method, through endowing the corresponding weights to the sample points with different distribution densities, the contribution degree of the core sample point in model establishing is emphasized, thereby helping establishment of a machine learning model decision boundary, and improving cardiovascular disease predicting precision of the model.
Owner:SHANGHAI UNIV
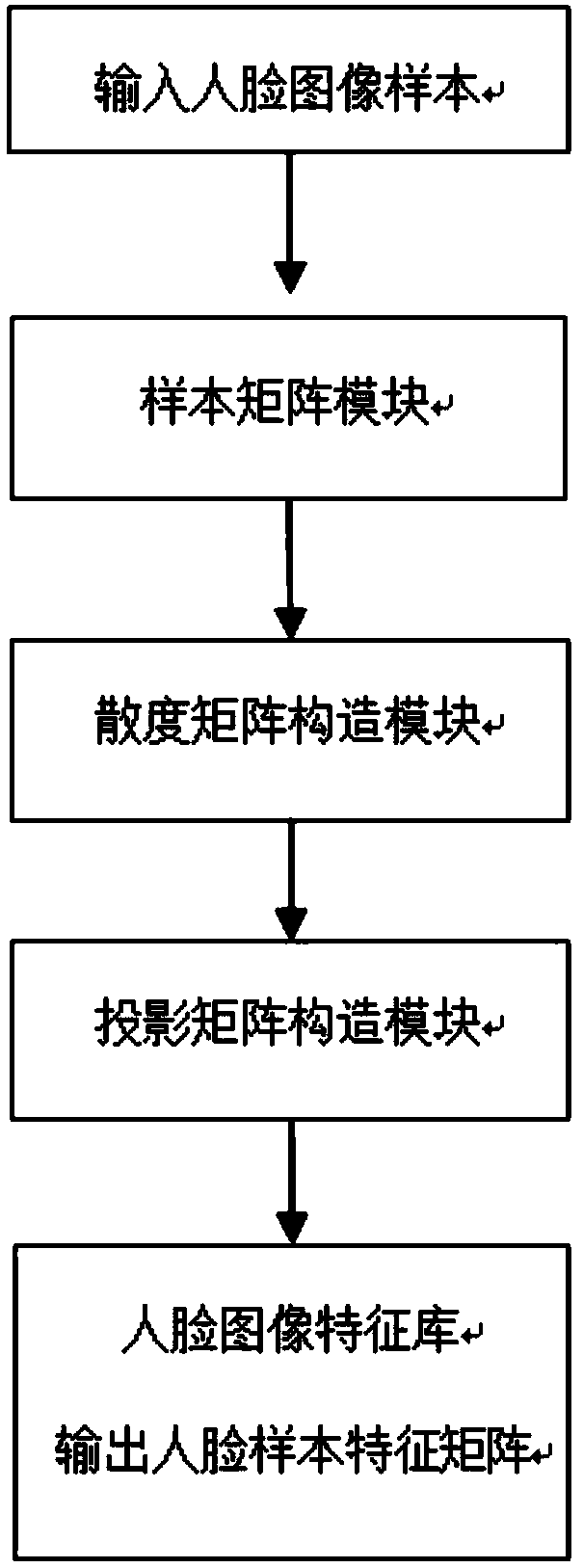
Nearest feature line based facial feature extracting method and device
InactiveCN104112147ARetain relevanceReduce computationCharacter and pattern recognitionHat matrixFeature extraction
The invention provides a nearest feature line based facial feature extracting method and device. The nearest feature line based facial feature extracting device comprises a sample matrix module, a divergence matrix construction module, and a projection matrix construction module. According to the nearest feature line based facial feature extracting method, image matrix data are directly used for calculation to obtain projection points on a feature line generated by facial image samples of the same kind, the projection points and the facial image samples are both matrixes, and a two-dimensional nearest feature line based intra-class divergence matrix is minimized to obtain a linear transformation so that two-dimensional feature line based intra-class divergence is minimum after the facial image samples are subjected to linear transformation. Compared with traditional nearest feature line space methods, the nearest feature line based facial feature extracting method has the advantages that the amount of calculation is reduced, and meanwhile, relevancy among neighboring pixel points of an image matrix per se can be also retained as much as possible.
Owner:HARBIN INST OF TECH SHENZHEN GRADUATE SCHOOL +1
Method for describing target detection area features based on merging between first order and second order
ActiveCN103440652ARetain relevanceGood Object CharacterizationImage analysisCharacter and pattern recognitionFeature vectorFeature Dimension
The invention provides a method for describing target detection region features based on merging between a first order and a second order. The method comprises the following steps: firstly, extracting features of a HOG inside a target detection rectangular region img1, and obtaining a feature vector hog; secondly, extracting a combination feature vector of a real target region in the target detection rectangular region img1; thirdly, conducting combination on the feature vectors and the merging between the first order and the second order, and obtaining the final feature vector of the target detection region. According to the method, firstly, interference from non-target regions is removed, a position feature vector is introduced to describe the relation between the image texture and the position, the merging between the first order and the second order is carried out on the position feature, the color feature and the texture feature to obtain the final feature description vector, the relevance between different feature dimensions is reserved, therefore, the better target feature description is obtained, and the method is suitable for various targets.
Owner:HOPE CLEAN ENERGY (GRP) CO LTD
High dynamic color image quality evaluation method based on feature similarity
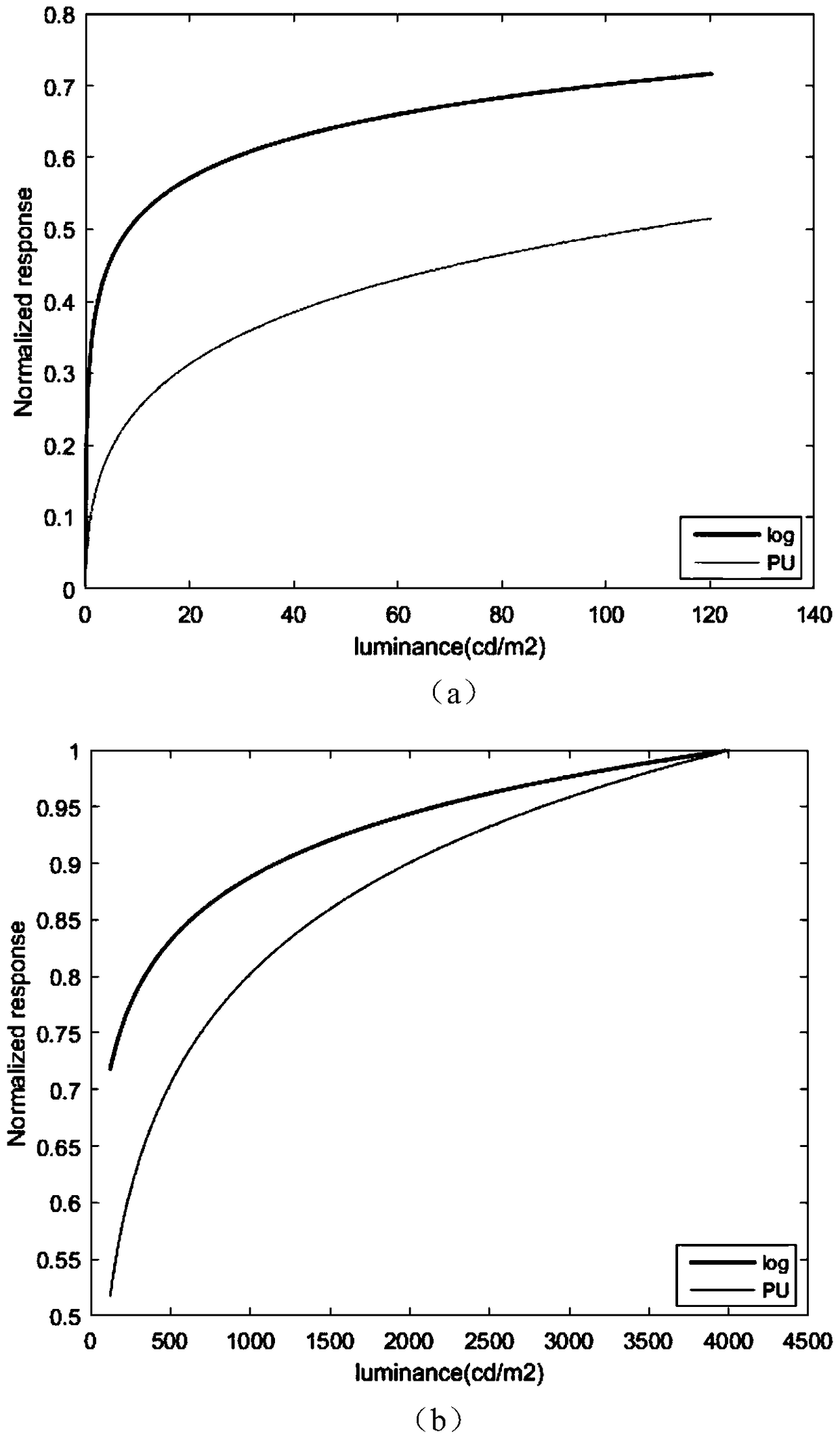
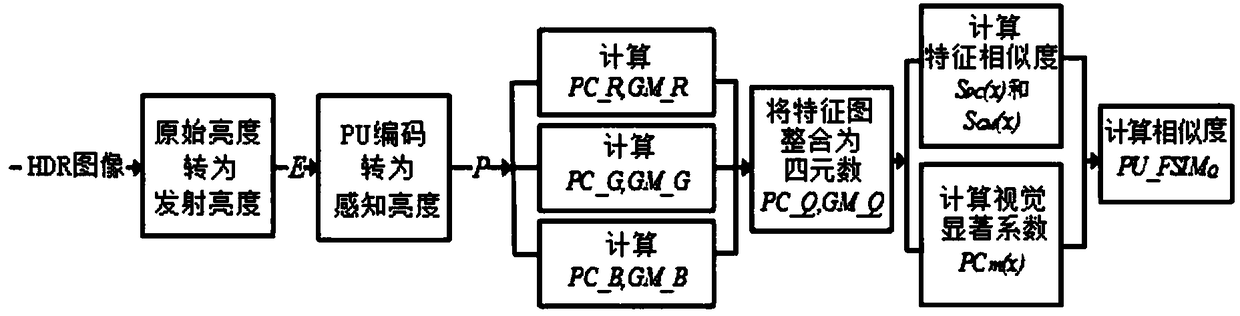
InactiveCN109191431AImprove consistencyImprove the accuracy of evaluationImage enhancementImage analysisColor imageComputation complexity
The invention discloses a high dynamic color image quality evaluation method based on feature similarity, The method comprises the following steps: 1, converting the original brightness into perceptual brightness, 2, calculating PC_R, PC_G and PC_B R of R of G and B color components of the color LDR image identical in phase, 3, calculating the gradient magnitude (GM) of R, G and B components of color LDR images GM_R, GM_G and GM_B; 4, integrating the PC feature map and the GM feature map into a quaternion matrix, and converting the feature map of color LDR images into pure imaginary form, 5, calculating feature similarity and realize quality evaluation. The invention retains the correlation of R, G and B color channels, and has high consistency with the subjective quality evaluation of human eyes. The algorithm has high evaluation accuracy for different distortions and low computational complexity, so it can achieve real-time quality evaluation.
Owner:TIANJIN UNIV
Sleep physiological signal feature extraction method and system based on tensor complexity
ActiveCN111539472ARetain relevanceAccurate responseCharacter and pattern recognitionDiagnostic recording/measuringSleep stagingFeature extraction
The invention discloses a sleep physiological signal feature extraction method and system based on tensor complexity. The sleep physiological signal feature extraction method comprises the following steps: a sleep physiological signal is collected, and a multi-guide time sequence of the sleep physiological signal is converted into tensor representation, wherein the sleep physiological signal is expressed as an N-order tensor, and the N-order tensor is composed of N-order sub-tensors; and the difference between the elements in each sub-tensor and the elements in the global sub-tensor is judgedto determine the approximate entropy of the N-order tensor, the tensor approximate entropy is used as the feature of sleep physiological signal extraction, the extracted feature can accurately reflectthe internal feature of the sleep physiological signal data, and then the sleep staging is more accurate in the subsequent classification processing.
Owner:SHANDONG UNIV
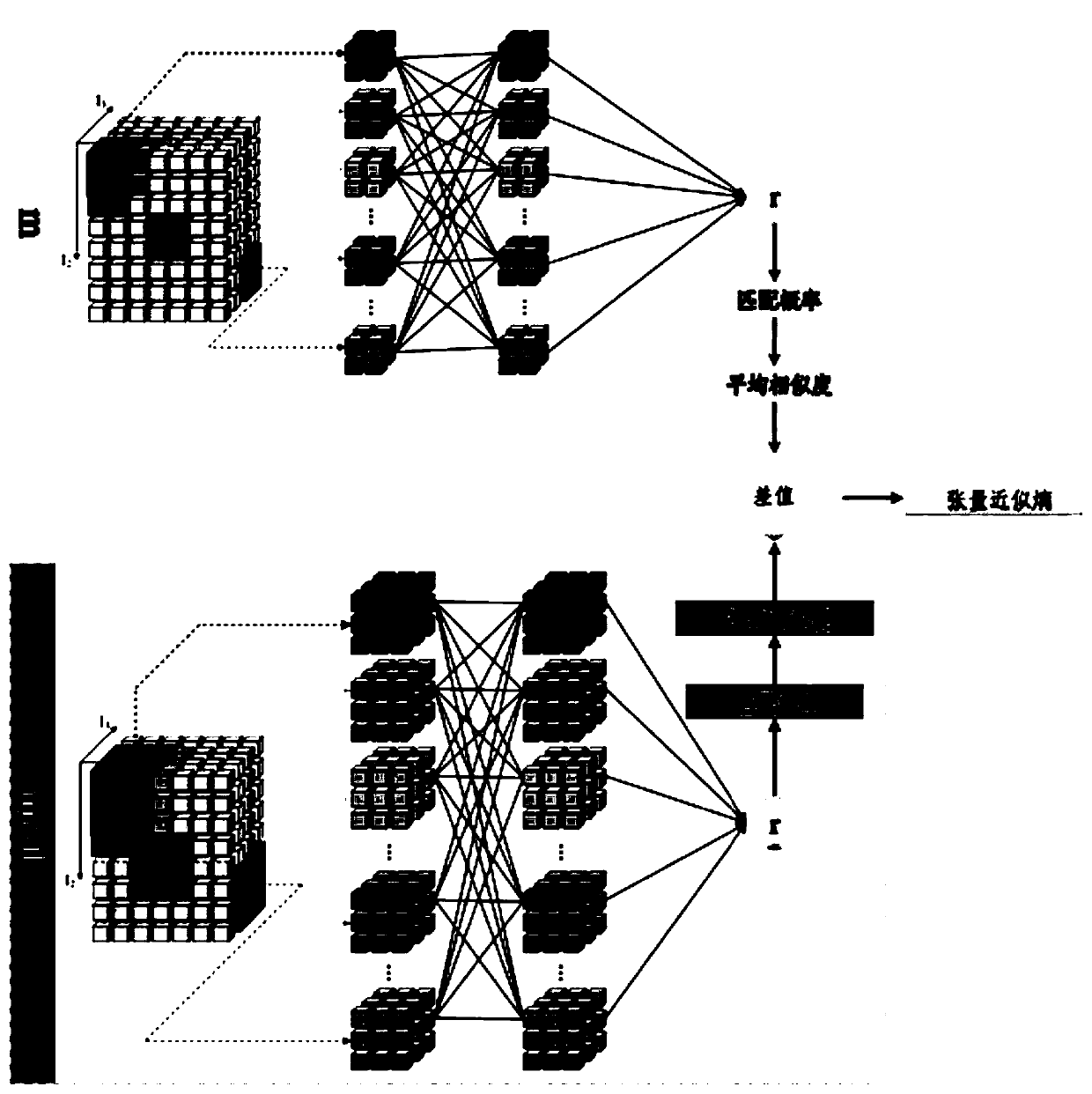
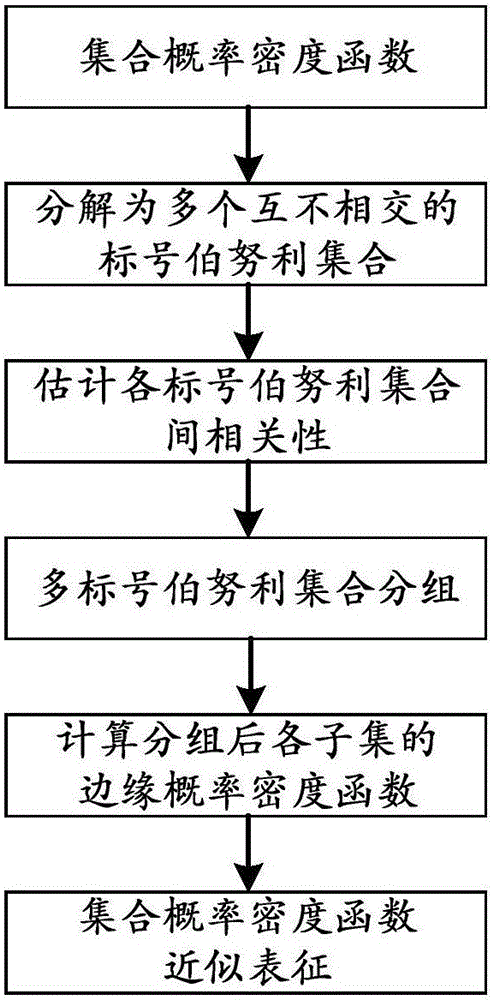
Approximation method of label set probability density function
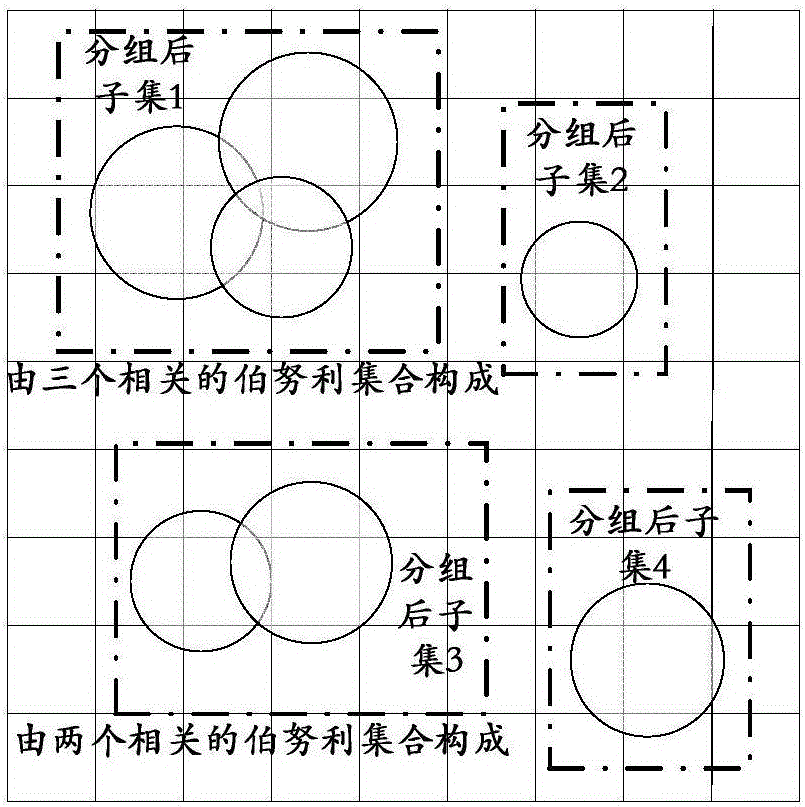
InactiveCN106202001ASimplified Ensemble Probability Density Function RepresentationRetain relevanceComplex mathematical operationsCorrelation coefficientNormal density
The invention discloses an approximation method of a label set probability density function. An existing set probability density function approximation method does not consider the real correlation between targets, and is unsuitable for a generalized multi-target system. Therefore, the invention provides a set probability density function approximation method based on correlation between the targets. The method comprises the following steps of: firstly computing a correlation coefficient between the Bernoulli sets corresponding to the targets; and then grouping the Bernoulli sets according to the obtained correlation coefficient; secondly providing the probability density function of each group of subsets based on the computing criterion of the set marginal probability density function; and finally utilizing a mutual independent relation between the subsets to jointly represent the multi-target posterior probability approximation by the probability density function of each group of subsets. Through the adoption of the method disclosed by the invention, not only the real correlation between the targets is retained, but also the dimensionality reduction of the high-dimensional and complex set multi-target probability density is performed; the representation of the set probability density function is greatly simplified, the approximation error is small, and the method has good engineering application prospects.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Overhead bare-handed three-dimensional target selection method based on half-contour highlight
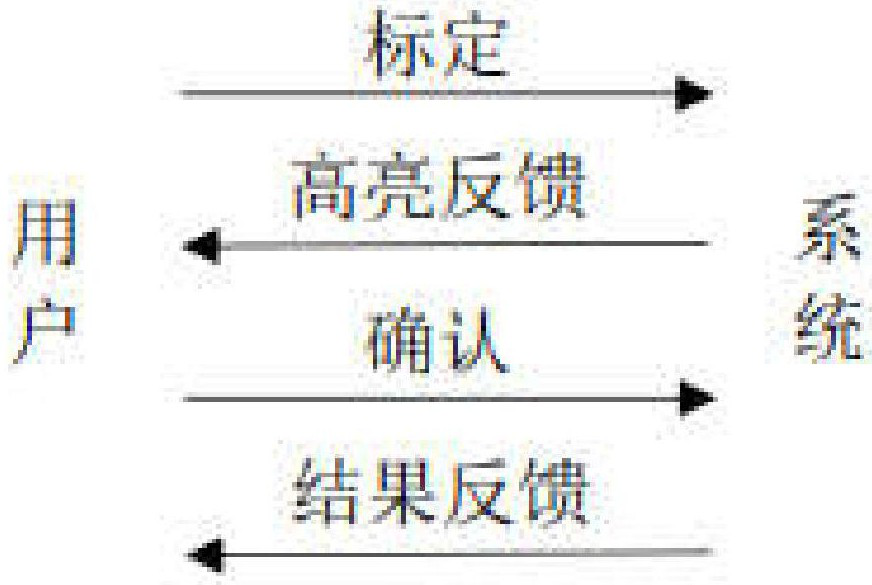
ActiveCN112306231AHolisticRetain relevanceInput/output for user-computer interactionGraph readingPattern recognitionMedicine
The invention discloses an overhead bare-handed three-dimensional target selection method based on half-contour highlight. The method comprises the steps: (1) a preparation stage: a system presents ascene to a user, and configures a half-contour shielding model for each candidate object; (2) a calibration highlight feedback stage: a dynamic calibration method based on cone rays is adopted for selecting four or less than four objects as alternative sets for confirmation selection, and half-contour highlight feedback is carried out on the objects; and (3) confirmation result feedback stage: theuser executes a corresponding selection confirmation gesture operation according to different highlight forms of different objects, and then the system obtains a confirmation intention of the user according to analysis and recognition of the gesture, matches the confirmation intention with a corresponding highlight object and gives feedback of a selection result to the user. By utilizing the method, the user can accurately express the selection intention through inaccurate operation, and the selection performance of the object and the user experience are improved.
Owner:ZHEJIANG UNIV
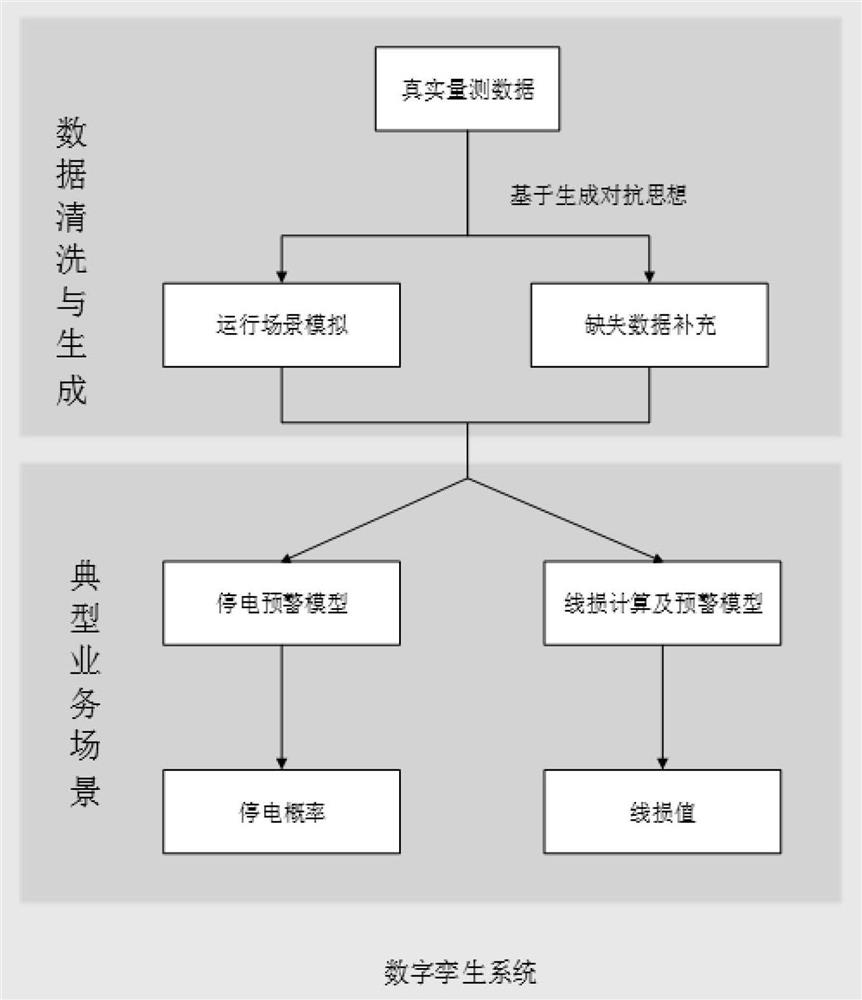
Power distribution network typical service scene early warning method based on digital twinborn body
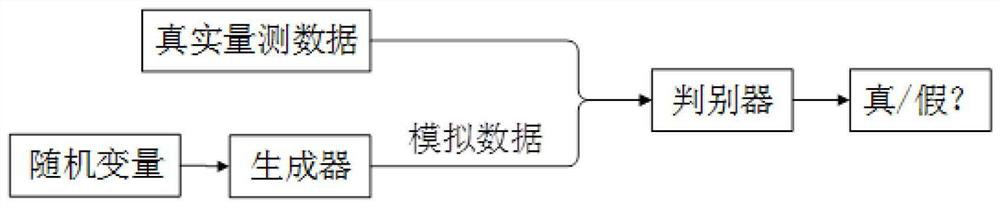
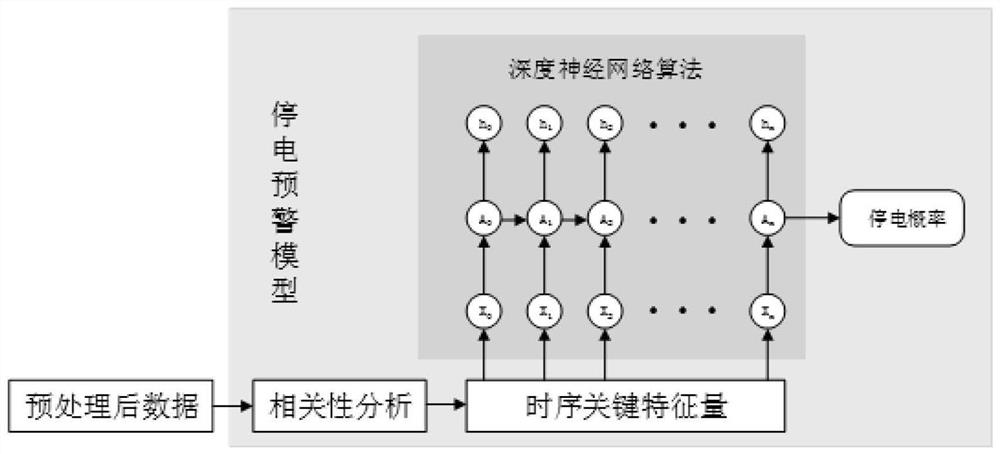
PendingCN114492150AHighly integratedHybrid strongForecastingDesign optimisation/simulationPhysicsSource data
The invention discloses a power distribution network typical service scene early warning method based on a digital twinborn body, and relates to the field of electrical engineering, and the technical scheme is that multi-source data generation and fusion are carried out based on a generative adversarial idea; building a digital twin system framework of the power distribution network; constructing a power failure early warning prediction model; constructing a line loss calculation and early warning model; collected power grid data are input, and early warning is carried out through a digital twin system. The method has the beneficial effects that missing data can be repaired from a data source by adopting an adversarial game idea, multi-source data can be fused, time sequence characteristics and correlation of measurement in a power system can be reserved, and the method can be applied to modeling and simulation of an actual scene which is high in integration level, strong in mixing type and rich in information link. And analysis and solution of a physical system mechanism and fine description of information-physics fusion features are realized.
Owner:CHINA PETROLEUM & CHEM CORP +2
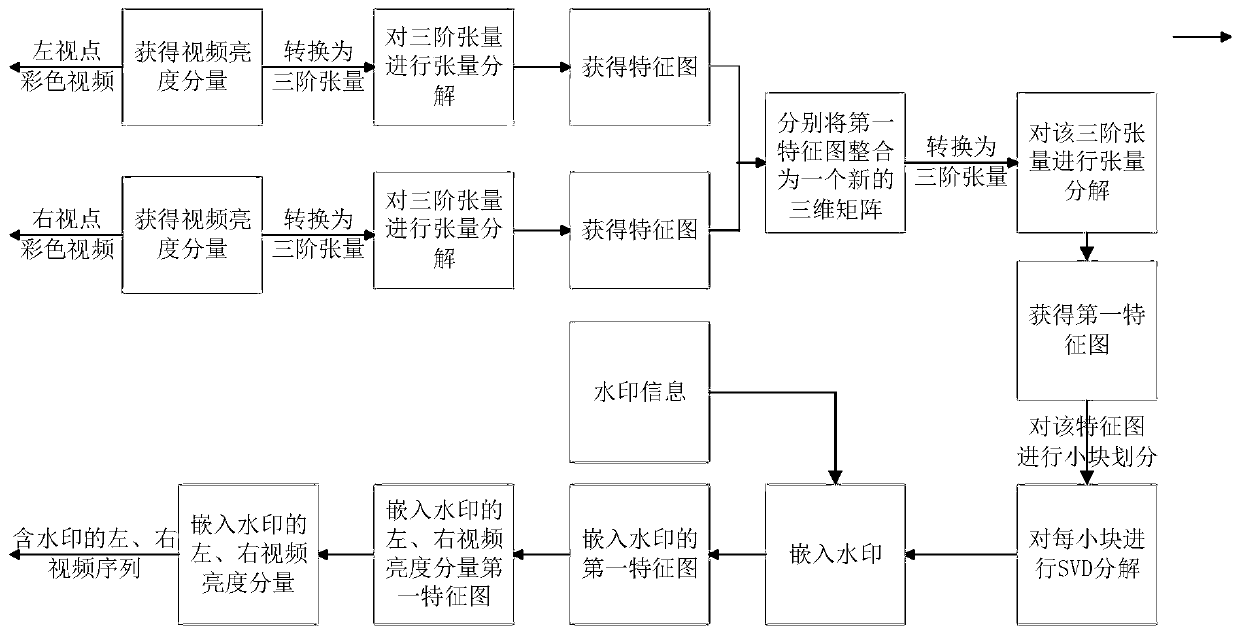
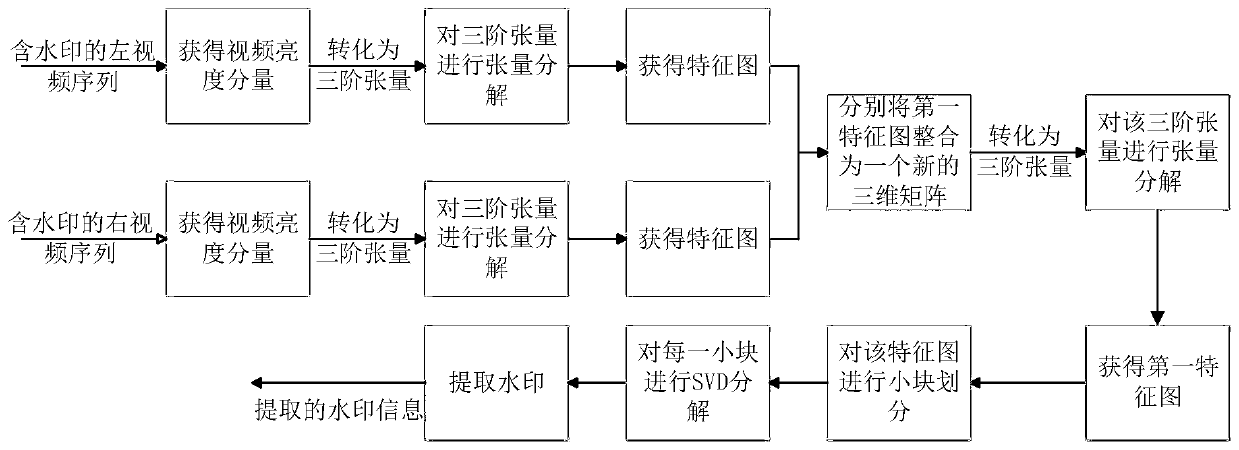
Stereoscopic video robust watermarking method based on tensor decomposition
PendingCN110838082AGuaranteed relevanceImprove robustnessImage watermarkingPattern recognitionStereoscopic video
The invention discloses a stereoscopic video robust watermarking method based on tensor decomposition. A watermark is embedded into the watermark embedding end, the brightness components of the left viewpoint color video and the right viewpoint color video are converted into third-order tensors; tensor decomposition is carried out on the third-order tensor; the two-dimensional matrix representations of the two feature maps containing the main energy are synthesized into a three-dimensional matrix in sequence; the three-dimensional matrix is converted into a three-order tensor; tensor decomposition is carried out on the third-order tensor; non-overlapping sub-image block processing is carried out on the obtained feature map containing the main energy, to-be-embedded blocks are determined,a coefficient in a left singular matrix of each to-be-embedded block is modified according to each bit in an original binary watermark sequence to obtain a corresponding watermark-containing block, and inverse operation is carried out on the watermark-containing block to finally obtain a watermark-containing three-dimensional video; at a watermark extraction end, image block processing is performed in the same way, to-be-extracted blocks are determined according to the to-be-embedded blocks, and watermark information are extracted from each to-be-extracted block. The method has the advantages of being good in robustness and imperceptibility.
Owner:COLLEGE OF SCI & TECH NINGBO UNIV
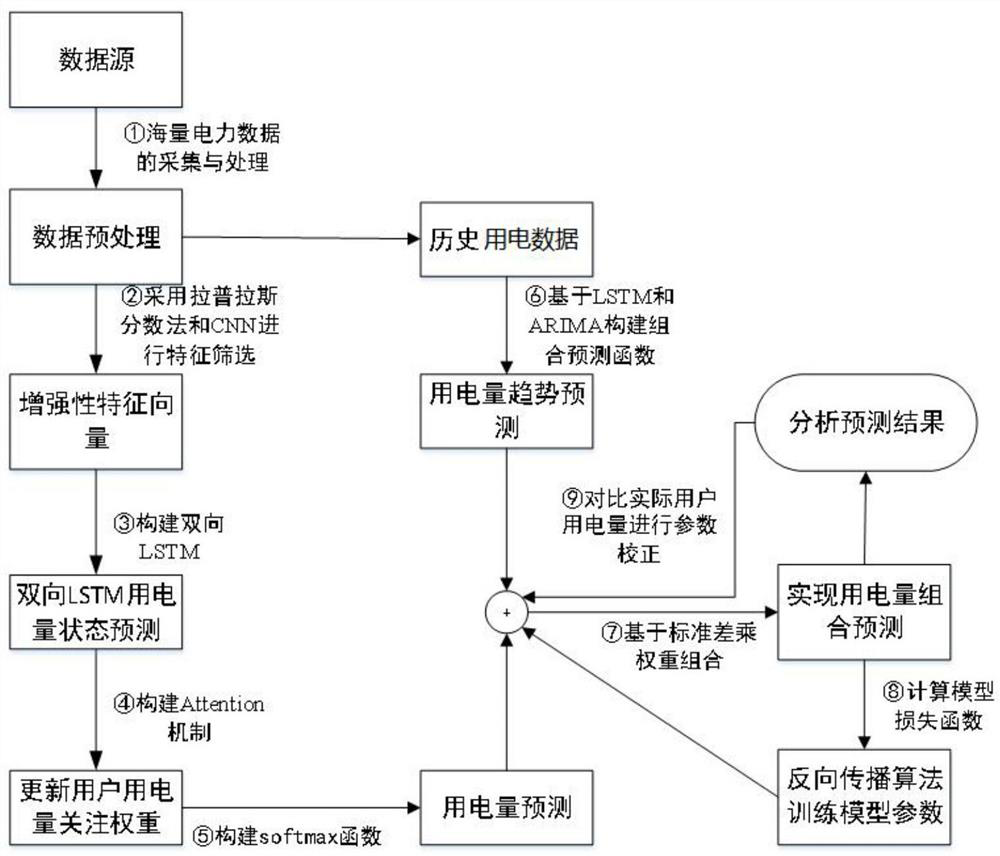
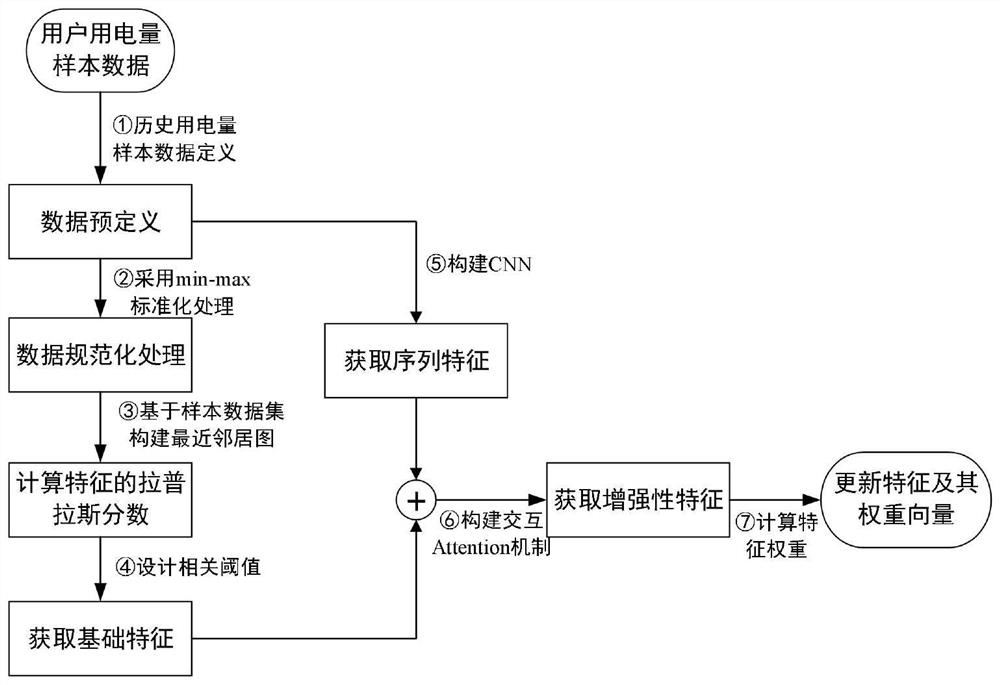
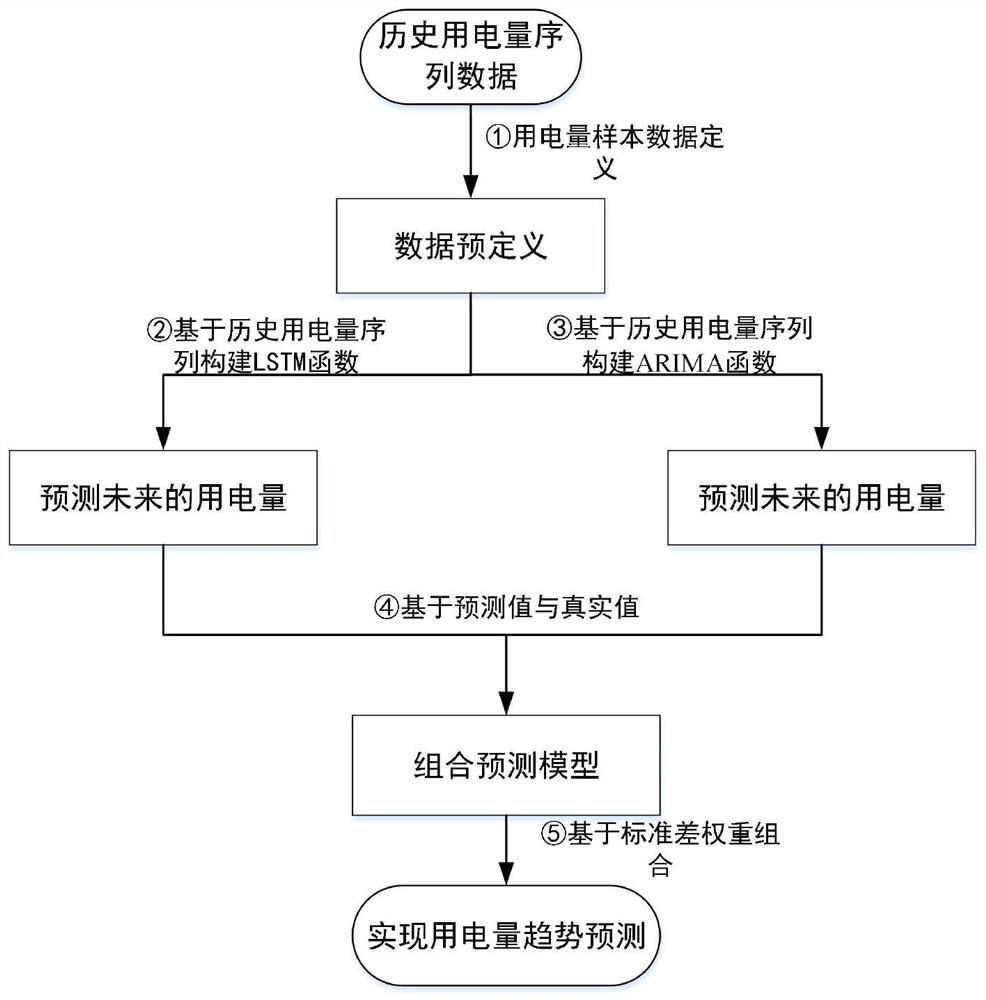
Power consumption prediction method and system based on features and trend perception
ActiveCN113449919AImprove accuracyRealize user power consumption status predictionForecastingCharacter and pattern recognitionMachine learningEngineering
The invention provides a power consumption prediction optimization method and system based on features and trend perception. The method comprises the steps of obtaining historical power data of a to-be-predicted user; based on the historical power data, using a pre-trained power consumption prediction model to predict the power consumption of the user; the training method of the power consumption prediction model specifically comprises the following steps: based on historical power training data, separately extracting power consumption features and a power consumption change trend, and training a feature-based power consumption prediction model and a trend-based power consumption prediction model to obtain a first prediction vector and a second prediction vector; and by combining the first prediction vector and the second prediction vector, finishing the training of a final power consumption prediction model by using a weight recombination method. The power consumption is predicted from the two aspects of the change trend of the historical power consumption of the user and the influence of the feature factors on the power consumption, and the prediction precision is higher.
Owner:STATE GRID SHANDONG ELECTRIC POWER +1
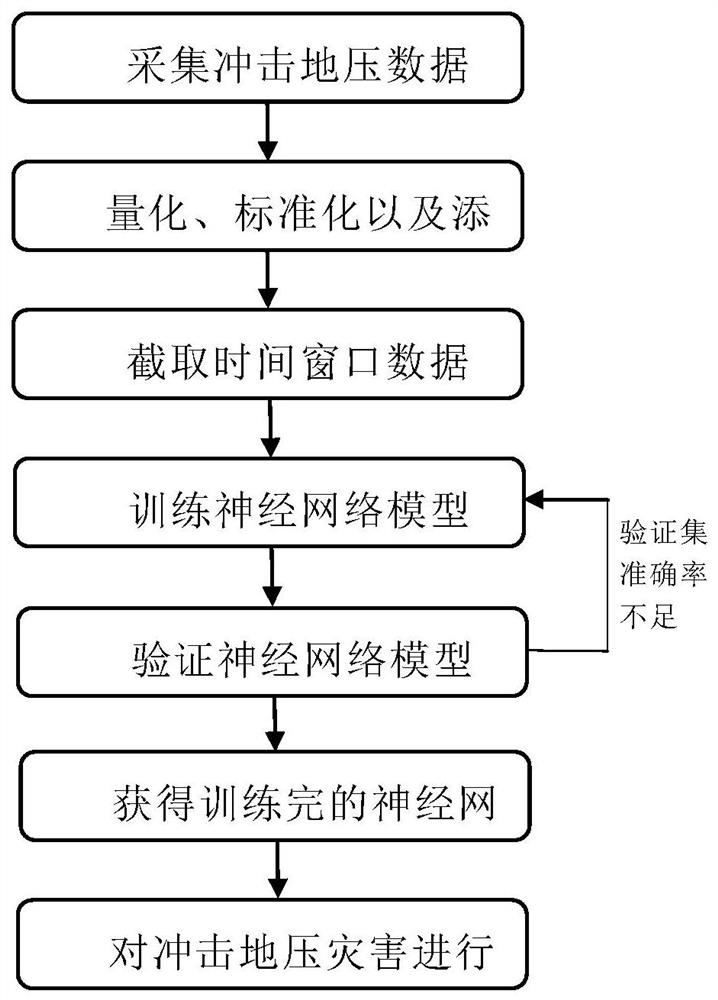
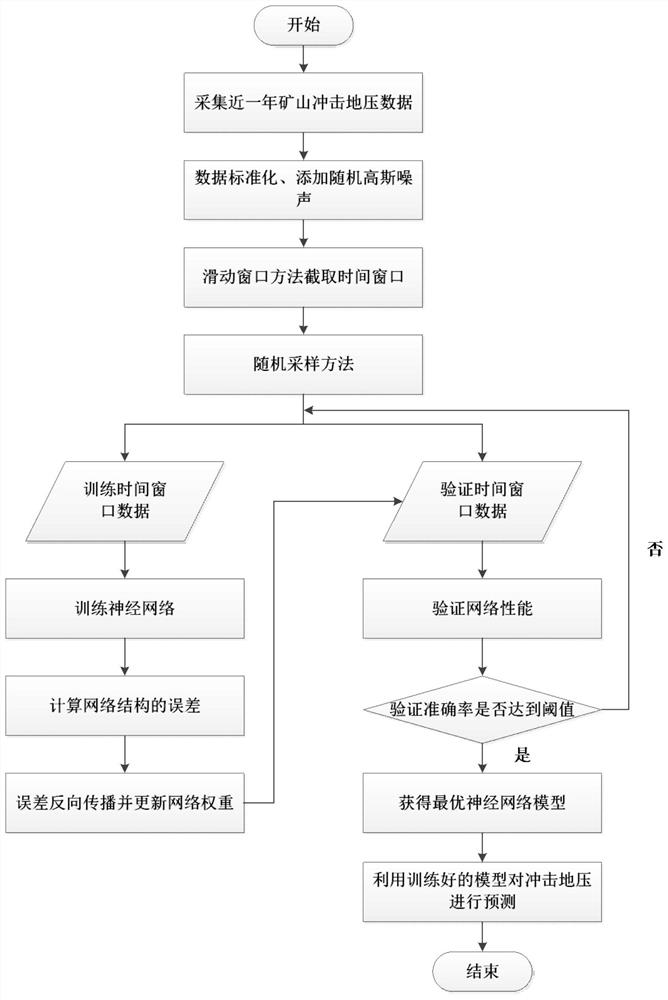
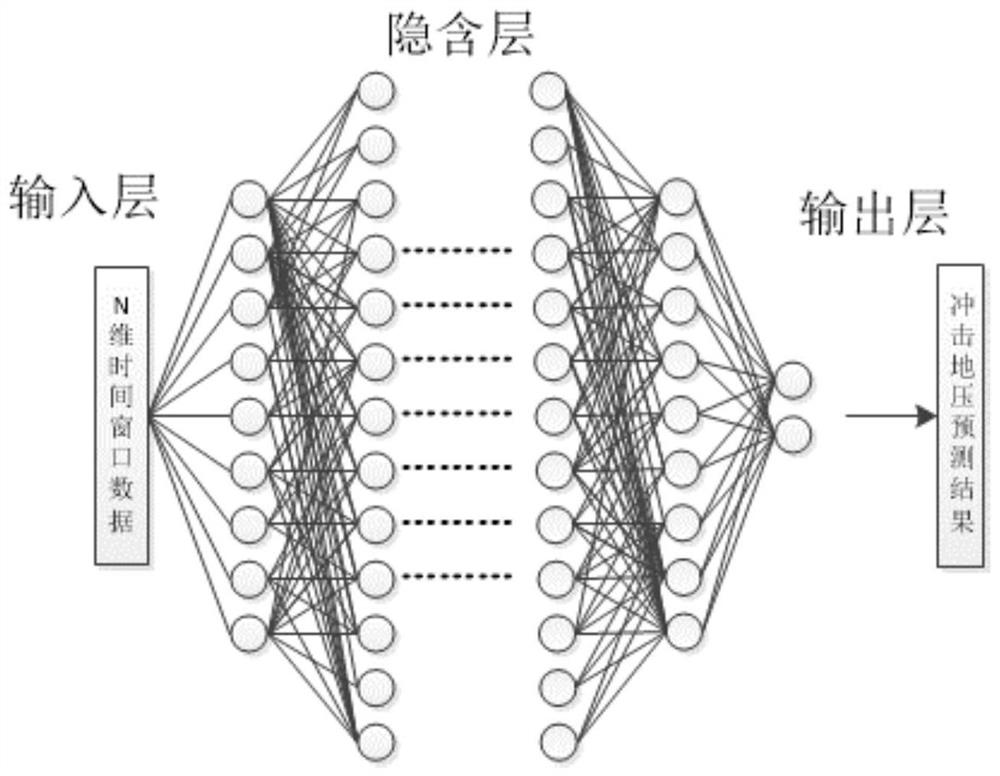
Neural network rock burst prediction method based on time sequence data
PendingCN113139681ARetain relevanceAvoid interferenceDigital data information retrievalForecastingEngineeringRandom noise
The invention relates to a neural network rock burst prediction method based on time sequence data, and the method comprises the steps: collecting rock burst data through mine data collection equipment, and carrying out the quantitative processing of main influence factors; standardizing the quantized data and then adding random noise; intercepting a quantitative time window through a sliding window method to construct sample data; dividing the time window data into a training set and a verification set through a random sampling method; training the established neural network by using the training set data, and adjusting network parameters by using the verification set test network performance; and predicting the rock burst of the mine by using the trained neural network model to obtain danger early warning information. The method is high in reliability, the neural network is trained through time sequence data, the problem that rock burst prediction is limited by short-time data is solved, rock burst long-term dynamic prediction is achieved, and rock burst disaster early warning can be effectively conducted.
Owner:INST OF ENERGY HEFEI COMPREHENSIVE NAT SCI CENT (ANHUI ENERGY LAB) +1
3D (three-dimensional) video signal compression coding-decoding method, device and system
ActiveCN102215405BImprove clarityHigh resolutionTelevision systemsDigital video signal modificationCoding decodingSignal compression
The invention is suitable for the field of multimedia information processing and provides a 3D (three--dimensional) video signal compression coding-decoding method, device and system. The compression coding method comprises the following steps: obtaining an odd pixel value or an even pixel value of a left eye video image and an odd pixel value or an even pixel value of a right eye video image of an original 3D video signal; and generating a hybrid video image according to the odd pixel value or even pixel value of the left eye video image and the odd pixel value or even pixel value of the right eye video image. The size of the newly generated hybrid video image is the same as that of the left or right eye video image so as to solve the problem of insufficient transmission bandwidth; and meanwhile, various frequency components of the left and right eye video images are completely preserved to reduce the distortion of the images, and the relativity of the left eye video image and the right eye video image is basically preserved so that the efficiency of coding and decoding the transmission format of the hybrid video image is high, and the compression ration is high.
Owner:SHENZHEN SKYWORTH RGB ELECTRONICS CO LTD
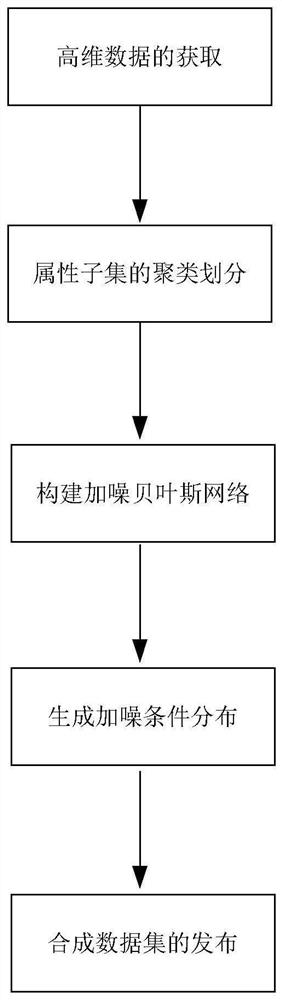
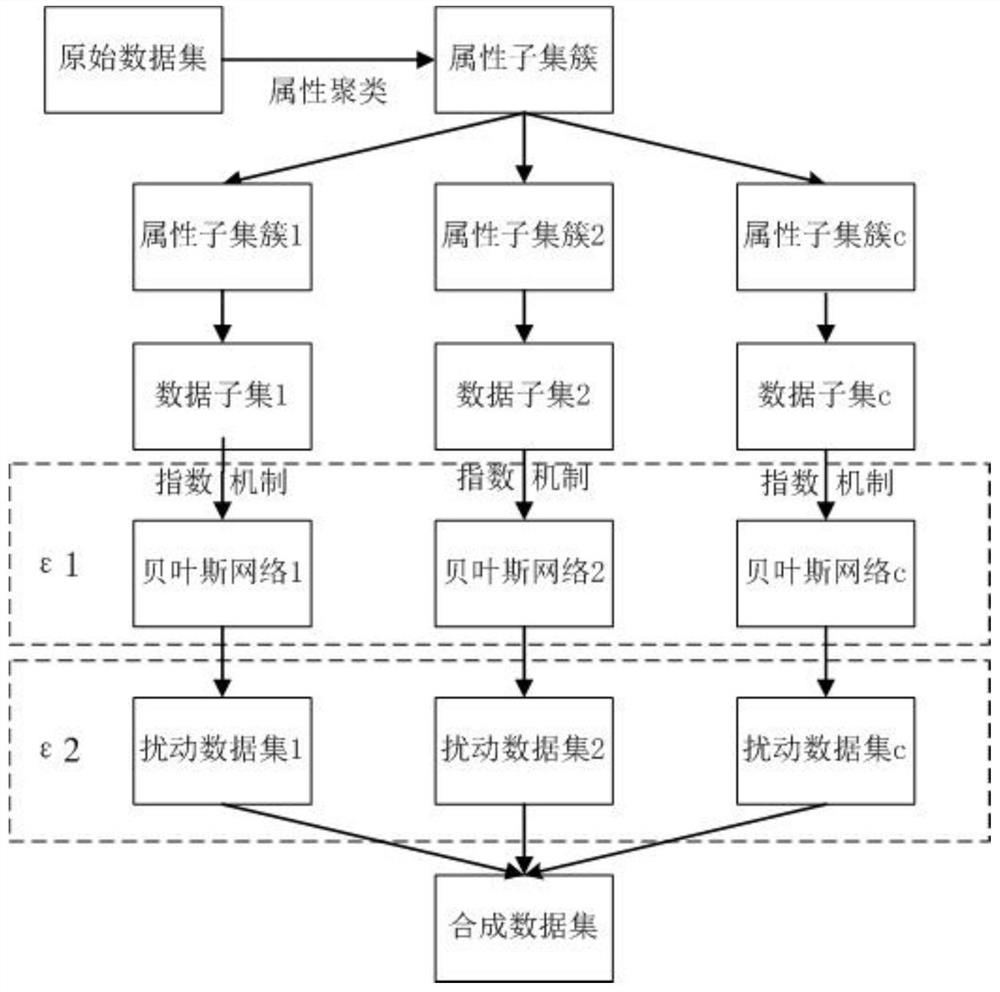
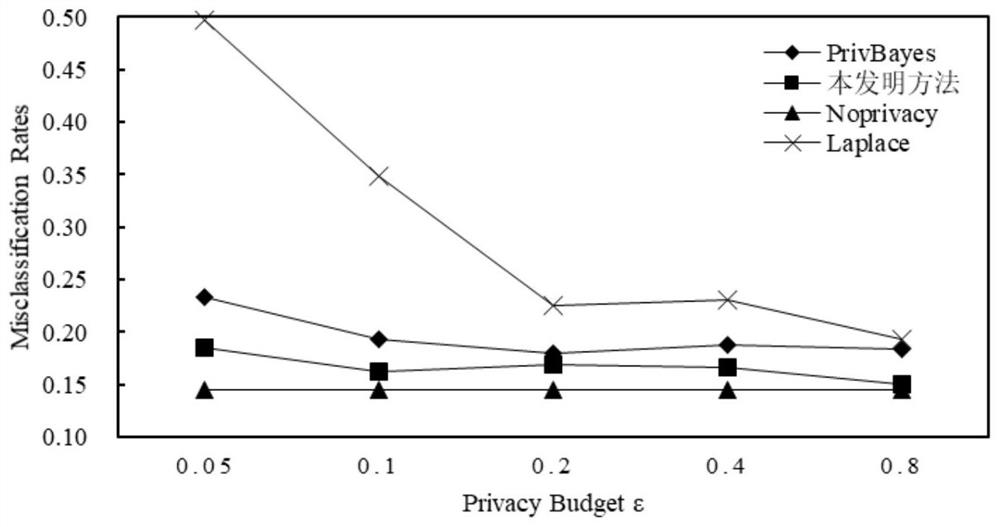
High-dimensional private data publishing method based on Bayesian network attribute clustering analysis technology
PendingCN112131604AEfficient releaseEnsure privacy and securityCharacter and pattern recognitionDigital data protectionEngineeringBayesian network
The invention relates to a high-dimensional private data publishing method based on a Bayesian network attribute clustering analysis technology. Compared with the prior art, the defects that high-dimensional private data noise adding publishing is large in error, poor in availability and low in efficiency are overcome. The method comprises the following steps: acquiring high-dimensional data; clustering and dividing the attribute subsets; constructing a noise-added Bayesian network; generating noise adding condition distribution; publishing of synthetic datasets. In a high-dimensional big dataenvironment, the operation time of a data release algorithm can be shortened while the data privacy security and availability are ensured, and effective release of private data in the high-dimensional big data environment is realized.
Owner:HEFEI CITY COULD DATA CENT +1
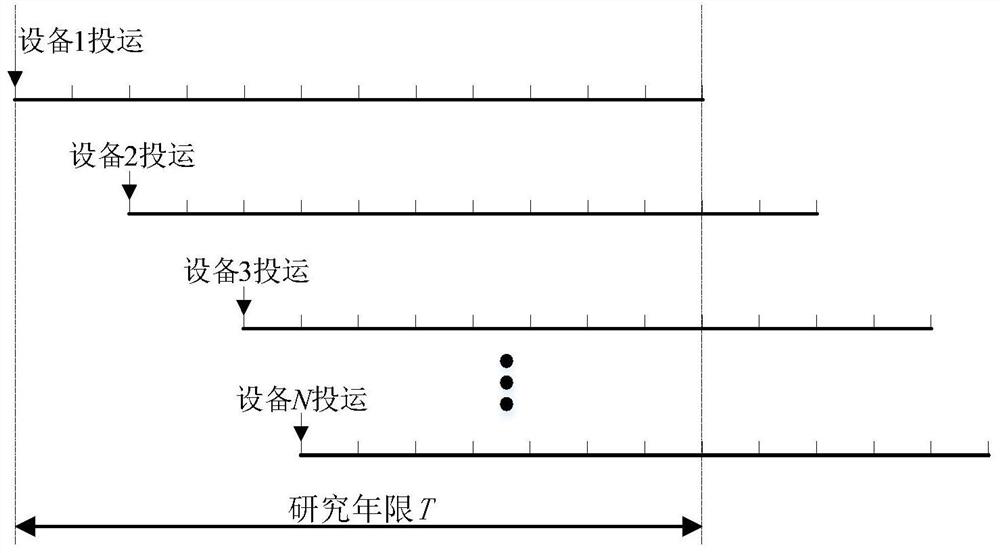
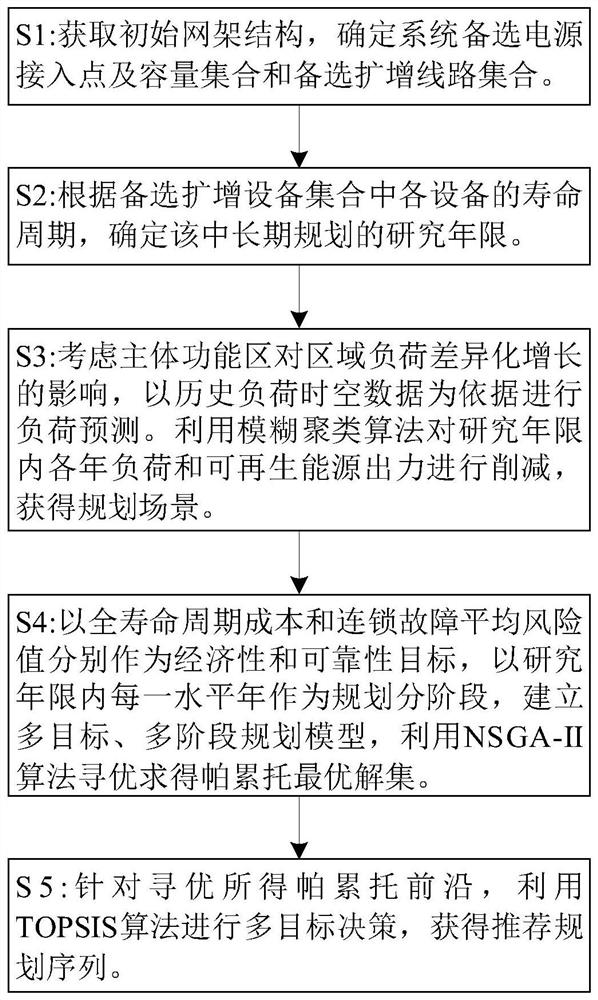
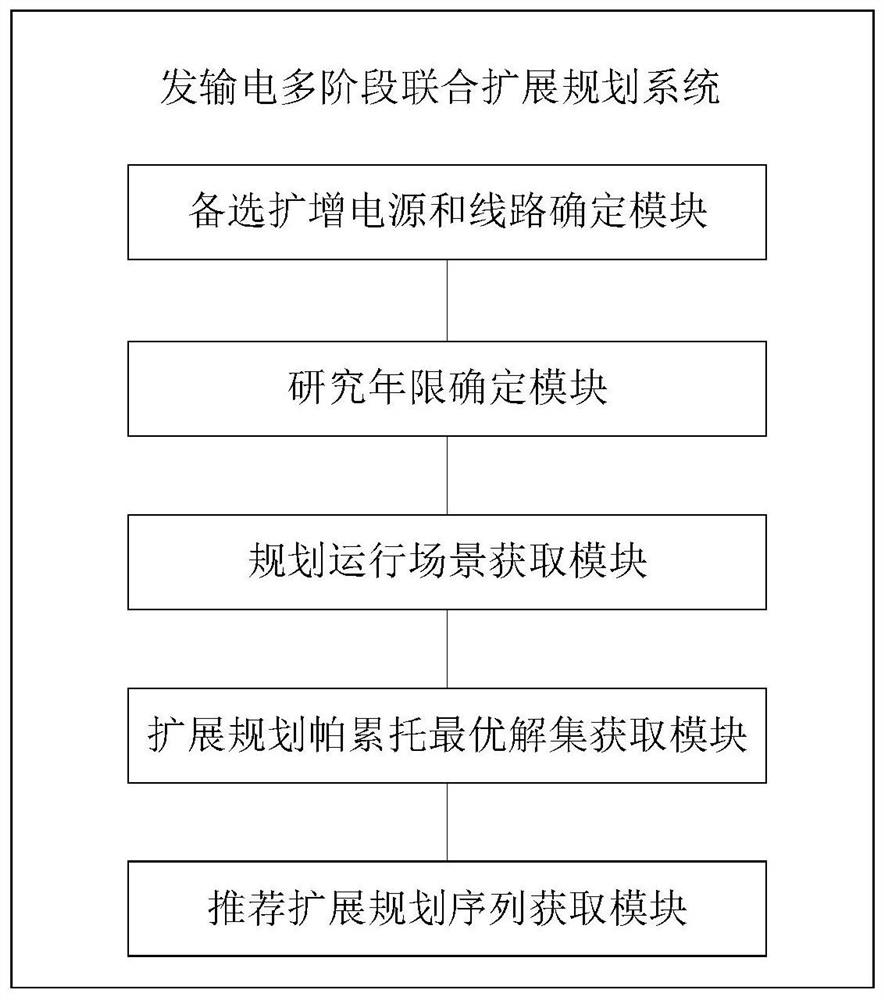
A method and system for multi-stage joint expansion planning of power generation and transmission
InactiveCN109583655BRetain relevanceReduce computing scaleForecastingResourcesCascading failureFull life cycle
The invention discloses a power generation and transmission multi-stage joint expansion planning method and system. The method comprises the following steps: reducing operation data with space-time characteristics by using a fuzzy clustering method to serve as a planned operation scene in a research period, and establishing a multi-objective and multi-stage power generation and transmission jointexpansion planning model for optimization by taking the full life cycle cost and cascading failure risk as economy and reliability targets and taking each horizontal year within a research year as a planning stage. According to the method, the economy and the operation reliability of the system are coordinated within the whole research period, a progressive expansion planning mode that a network source structure is matched with a load demand is formed, and a Pareto optimal solution set and a recommended staged expansion planning sequence can be obtained through optimization.
Owner:RES INST OF ECONOMICS & TECH STATE GRID SHANDONG ELECTRIC POWER +1
A 3D Attitude Calculation Method for Aircraft
ActiveCN103617328BIn line with the real situationRetain relevanceSustainable transportationSpecial data processing applicationsJet aeroplaneCluster algorithm
The invention provides an airplane three-dimensional attitude computation method. Firstly, preprocessing is carried out on an image to be processed by the adoption of Gaussian smooth filtering to eliminate influences of noise on follow-up algorithms; secondly, the smoothened image is segmented by the adoption of a fuzzy C-means clustering algorithm (FCM) to obtain a binary image, then Hough conversion is carried out on the binary image obtained through segmentation, a part, with obvious linear features, on a target is detected, feature points of the part, with non-obvious linear features, on the target are extracted by the adoption of a framework, and then linear fitting is carried out on the feature points on the framework to obtain a target axis; finally, the obtained axis, the actual size of the target, camera parameters and other information are combined, and a three-dimensional attitude parameter of the target under a camera coordinate system is calculated by means of projective geometry knowledge. On the basis of geometrical features capable of reflecting the structure of an object and by means of Hough conversion and framework extraction of the whole target image, the obtained axis is more accurate, and the obtained three-dimensional attitude parameter is more precise.
Owner:INST OF OPTICS & ELECTRONICS - CHINESE ACAD OF SCI
Encryption method of jpeg image bit stream based on the change of AC statistical characteristics
ActiveCN109889687BImprove securityIncrease aggressivenessDigital video signal modificationAlgorithmTheoretical computer science
A JPEG image bitstream encryption method based on the change of AC statistical characteristics, the user selects the last non-zero AC coefficient entropy encoding in the part of the image block in the JPEG bitstream by the user key, and uses it as secret information through the histogram translation method It is hidden in the entropy coding of some image blocks, the statistical characteristics are obtained from the user key and the AC coefficient, the encryption key of the DC coefficient and the encryption key of the AC coefficient are adaptively generated, and the inter-group scrambling and differential coding iterative setting are performed on the DC coefficient respectively. Intra-block and inter-block scrambling of the AC coefficients; the receiver extracts the secret information from the encrypted bit stream and decrypts it, and recovers the DC coefficient and AC coefficient encryption keys from the user key and the statistical characteristics of the AC coefficients in the encrypted bit stream , and decrypt the AC coefficients and DC coefficients, restore the AC coefficient entropy coding in each image block entropy coding, and obtain the original bit stream. The method has high security and the encrypted file has a small extension.
Owner:SOUTHWEST JIAOTONG UNIV
Facility and equipment evaluation method and device based on probability distribution
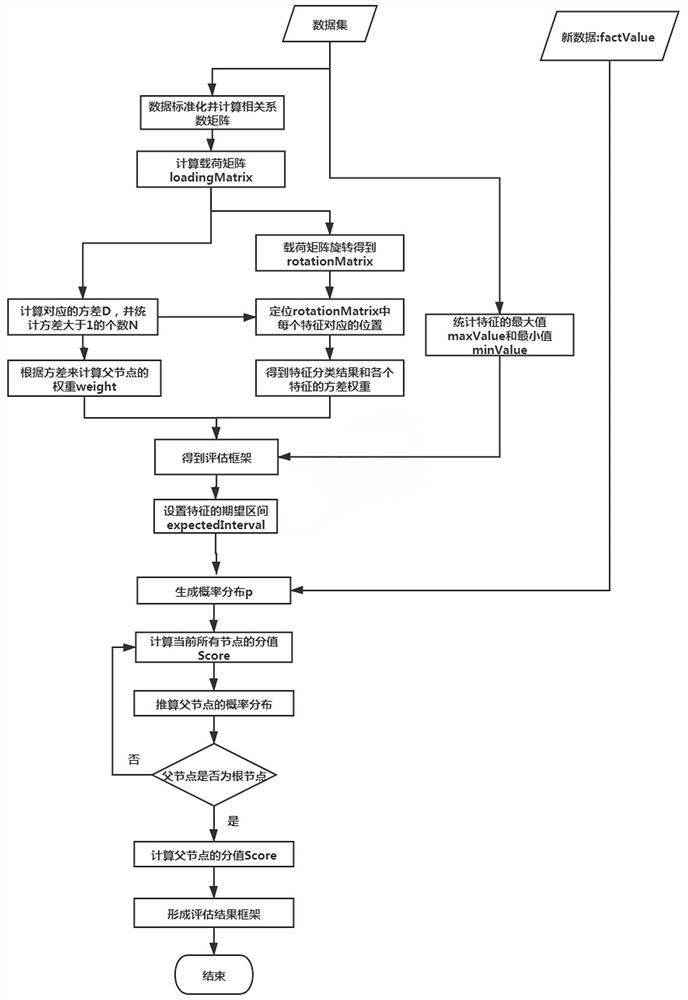
PendingCN114330972ASave spaceSave storage spaceResourcesComplex mathematical operationsData profilingIndustrial engineering
The invention discloses a facility and equipment evaluation method and device based on probability distribution, and mainly solves the problems that in the prior art, an existing equipment and facility evaluation method evaluates correlation and independence between framework loss features and does not have expansibility. The facility equipment evaluation method based on probability distribution comprises the following steps: analyzing a correlation production evaluation framework according to historical data of facility equipment by an analyzer, and then scoring new data of the facility equipment according to the evaluation framework and outputting a result. By means of the scheme, the purposes of automatically establishing an evaluation framework, reserving correlation and independence between feature patterns, calculating scores and weights in an information distribution mode so as to prevent information loss and achieving multi-dimensional evaluation are achieved.
Owner:CHENGDU SEFON SOFTWARE CO LTD
Sleep physiological signal feature extraction method and system based on tensor complexity
ActiveCN111539472BRetain relevanceAccurate internal featuresCharacter and pattern recognitionDiagnostic recording/measuringSleep stagingFeature extraction
The invention discloses a sleep physiological signal feature extraction method and system based on tensor complexity, comprising: collecting the sleep physiological signal and converting the polyconductive time series of the sleep physiological signal into a tensor representation; the sleep physiological signal is expressed as an N-order tensor , the N-order tensor is composed of N-order sub-tensors; judge the difference between the elements in each sub-tensor and each element in the global sub-tensor to determine the size of the N-order tensor approximate entropy, and use the tensor approximate entropy as sleep physiology The features of the signal extraction, the extracted features can accurately reflect the internal features of the sleep physiological signal data, and then achieve more accurate sleep staging in the subsequent classification processing.
Owner:SHANDONG UNIV
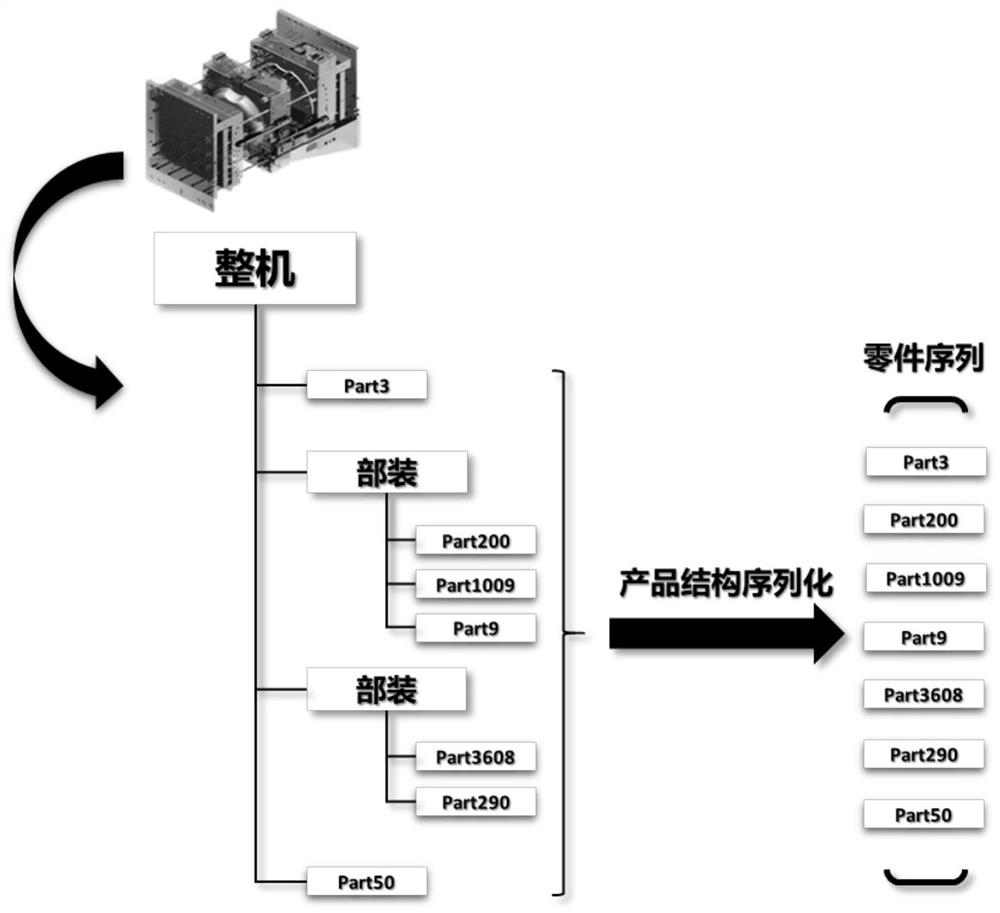
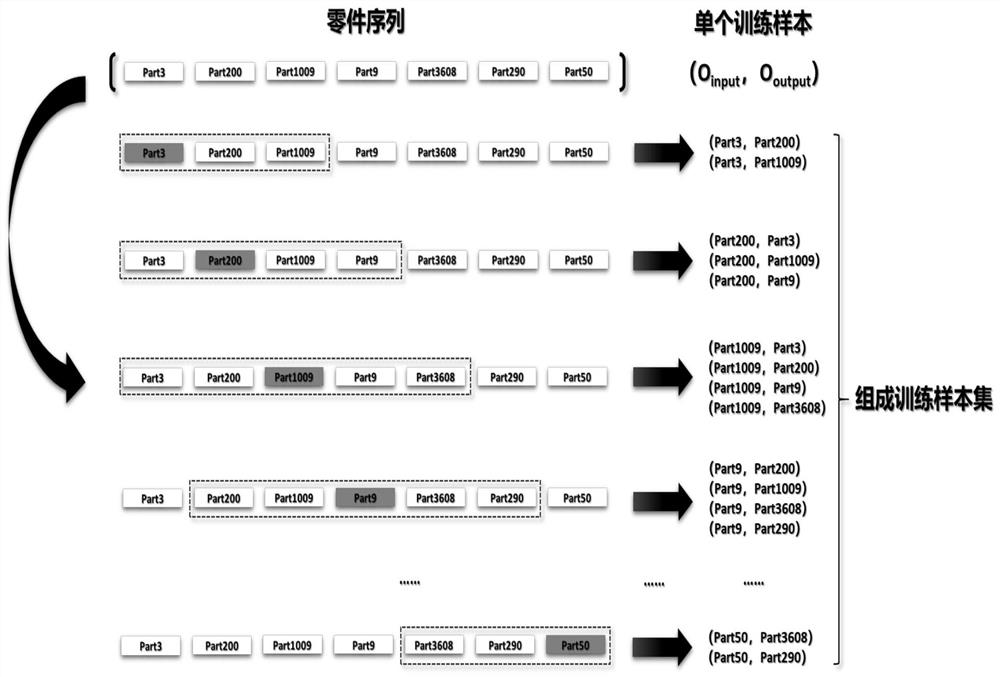
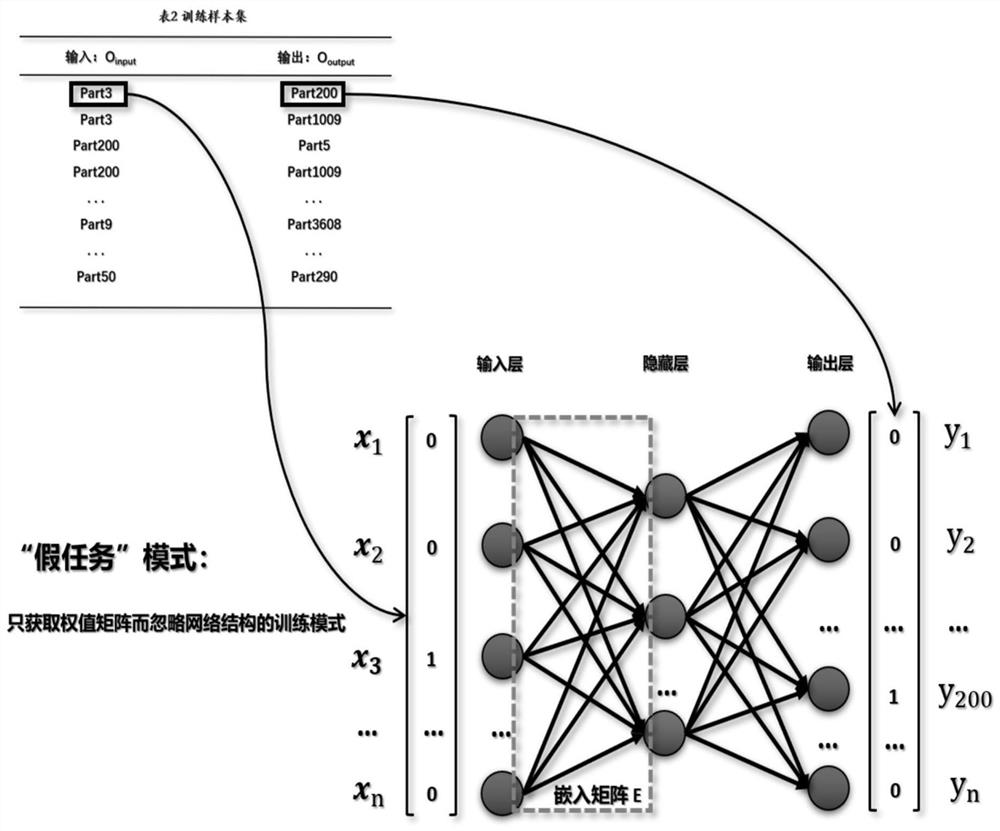
Part2Vec part vectorization processing method based on deep learning
PendingCN112232423AAchieve unique representationRetain relevanceCharacter and pattern recognitionNeural architecturesPattern recognitionHidden layer
The invention discloses a part vectorization processing method based on deep learning, namely Part2Vec, which mainly comprises the following steps of preprocessing an existing product structure, creating a part dictionary, and establishing a part dictionary based on a constraint relationship among parts; constructing a training sample and a sample set, determining a neural network structure, training obtained sample set data, obtaining a weight matrix between an input layer and a hidden layer, converting the weight matrix into an embedded matrix, wherein the creation sequence and the description sequence are the same. According to the method, vectorized representation can be quickly carried out on the parts, so that the unique representation of the parts is realized, the correlation between similar parts is reserved, and the dimensionality of the parts during numeralization is reduced.
Owner:深制科技(苏州)有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com