Permission configuration method and device
A permission configuration and permission technology, applied in the communication field, can solve problems such as infringement of user privacy information, and achieve the effect of preventing leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
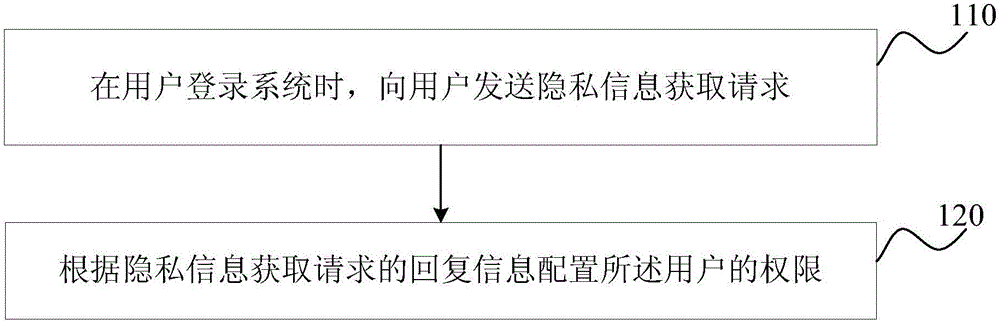
[0018] figure 1 It is a schematic flow chart of the permission configuration method provided in Embodiment 1 of the present invention. The method in this embodiment is applicable to the situation where an online business hall configures user permissions. It can be executed by a device for configuring rights, which can be implemented in the form of hardware and / or software, and can generally be applied to an operator's server.
[0019] see figure 1 , the permission configuration method includes:
[0020] S110, when the user logs in to the system, send a private information acquisition request to the user.
[0021] Exemplarily, in the user login system, the system will send a request to the user to obtain the user's private information. So that the user can choose appropriate private information to provide to the system according to the degree of correlation between the private information and the system. The private information may be: user historical operation data and / or ...
Embodiment 2
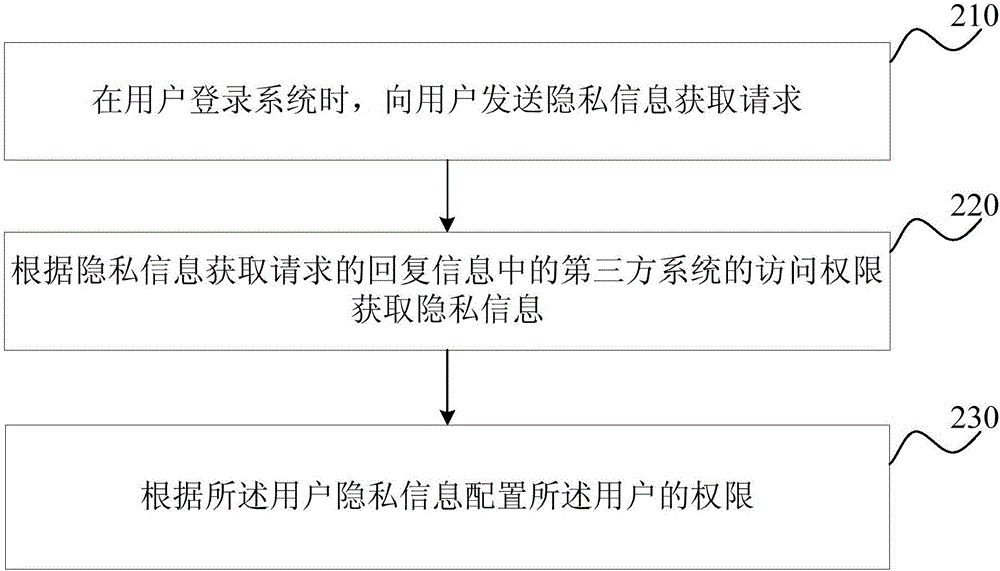
[0028] figure 2 It is a schematic flow chart of the permission configuration method provided in Embodiment 2 of the present invention. This embodiment is optimized on the basis of the above embodiments. In this embodiment, the reply information is specifically optimized as: the access authority of the third-party system, and correspondingly, the private information will be obtained according to the access authority of the third-party system , the specific optimization is: configure the user's authority according to the user's privacy information.
[0029] Correspondingly, the permission configuration method provided in this embodiment includes:
[0030] S210, when the user logs in to the system, send a private information acquisition request to the user.
[0031] S220. Acquire the private information according to the access authority of the third-party system in the reply information of the private information obtaining request.
[0032] At present, some privacy data chang...
Embodiment 3
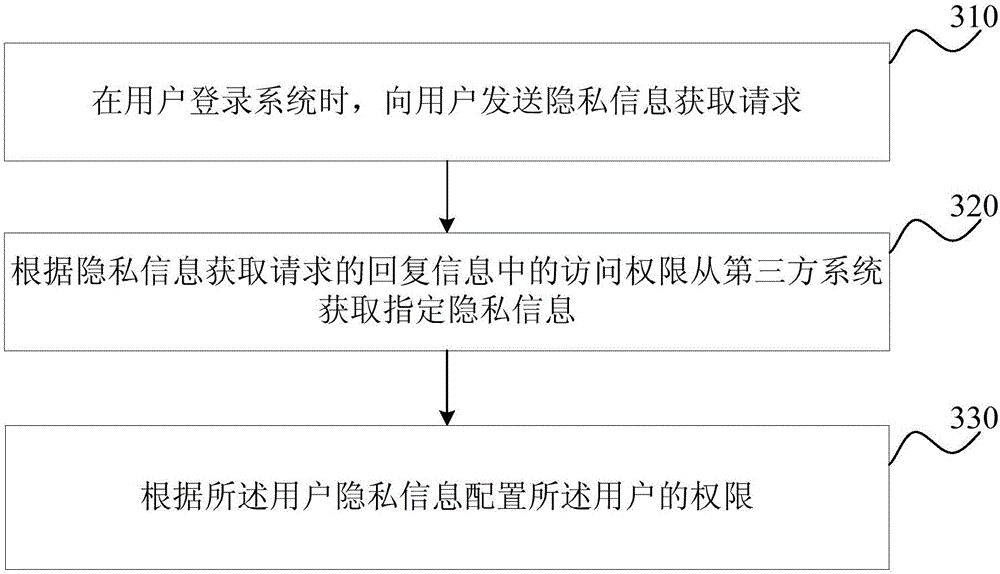
[0036] image 3 It is a schematic flow chart of the permission configuration method provided by Embodiment 3 of the present invention. This embodiment is optimized on the basis of the above-mentioned embodiments. In this embodiment, the reply information is specifically optimized as: the access authority of the third-party system and the designated privacy information. Correspondingly, the The permission to obtain the user's private information is specifically optimized as: obtaining specified private information from a third-party system according to the access permission.
[0037] Correspondingly, the permission configuration method provided in this embodiment includes:
[0038] S310, when the user logs into the system, send a private information acquisition request to the user.
[0039] S320. Acquire designated private information from a third-party system according to the access authority in the reply information of the private information obtaining request.
[0040] Sinc...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com