Patents
Literature
41 results about "Privacy rights" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
The right to privacy often means the right to personal autonomy, or the right to choose whether or not to engage in certain acts or have certain experiences. Several amendments to the U.S. Constitution have been used in varying degrees of success in determining a right to personal autonomy: The First Amendment protects the privacy of beliefs.
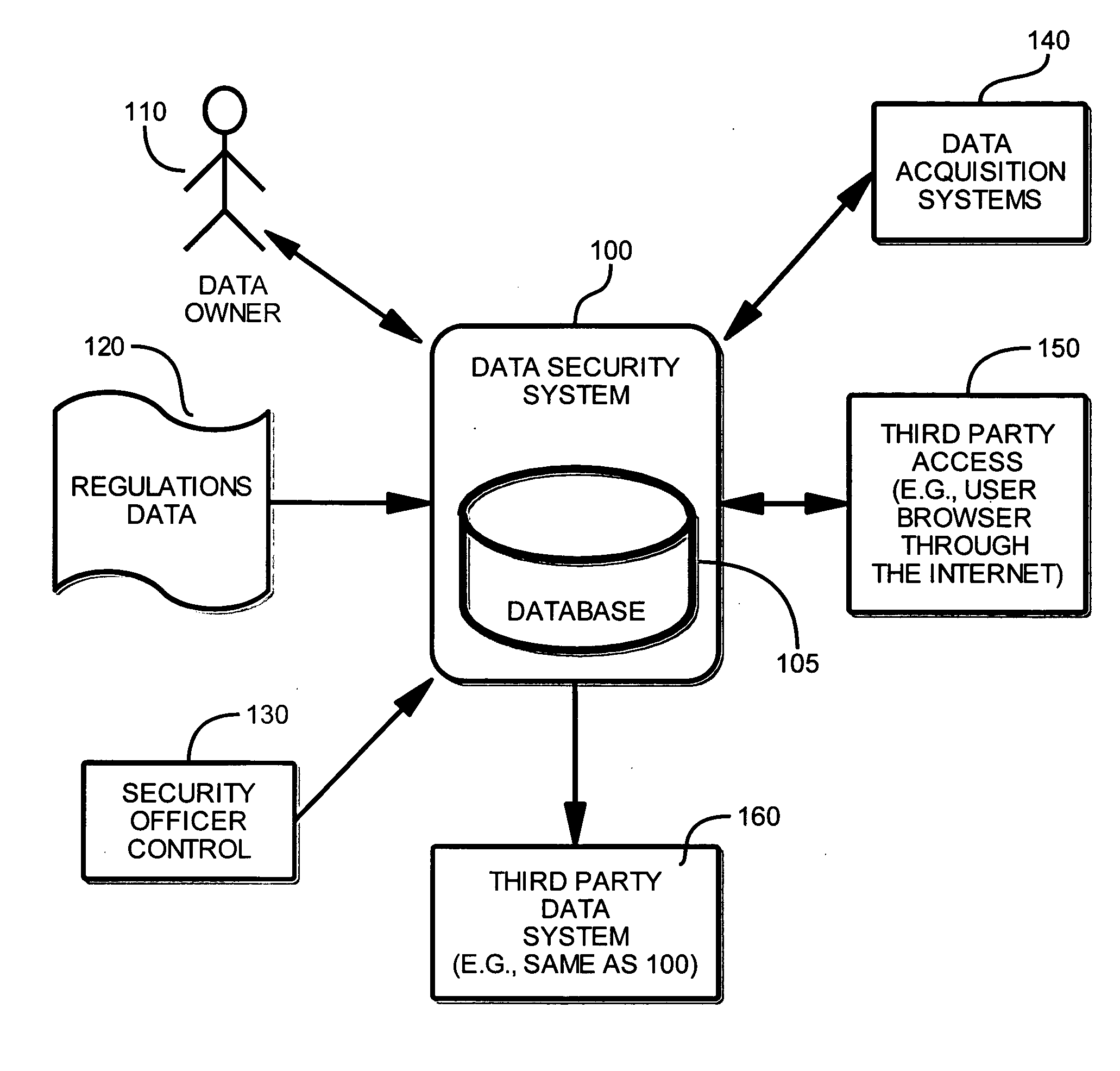
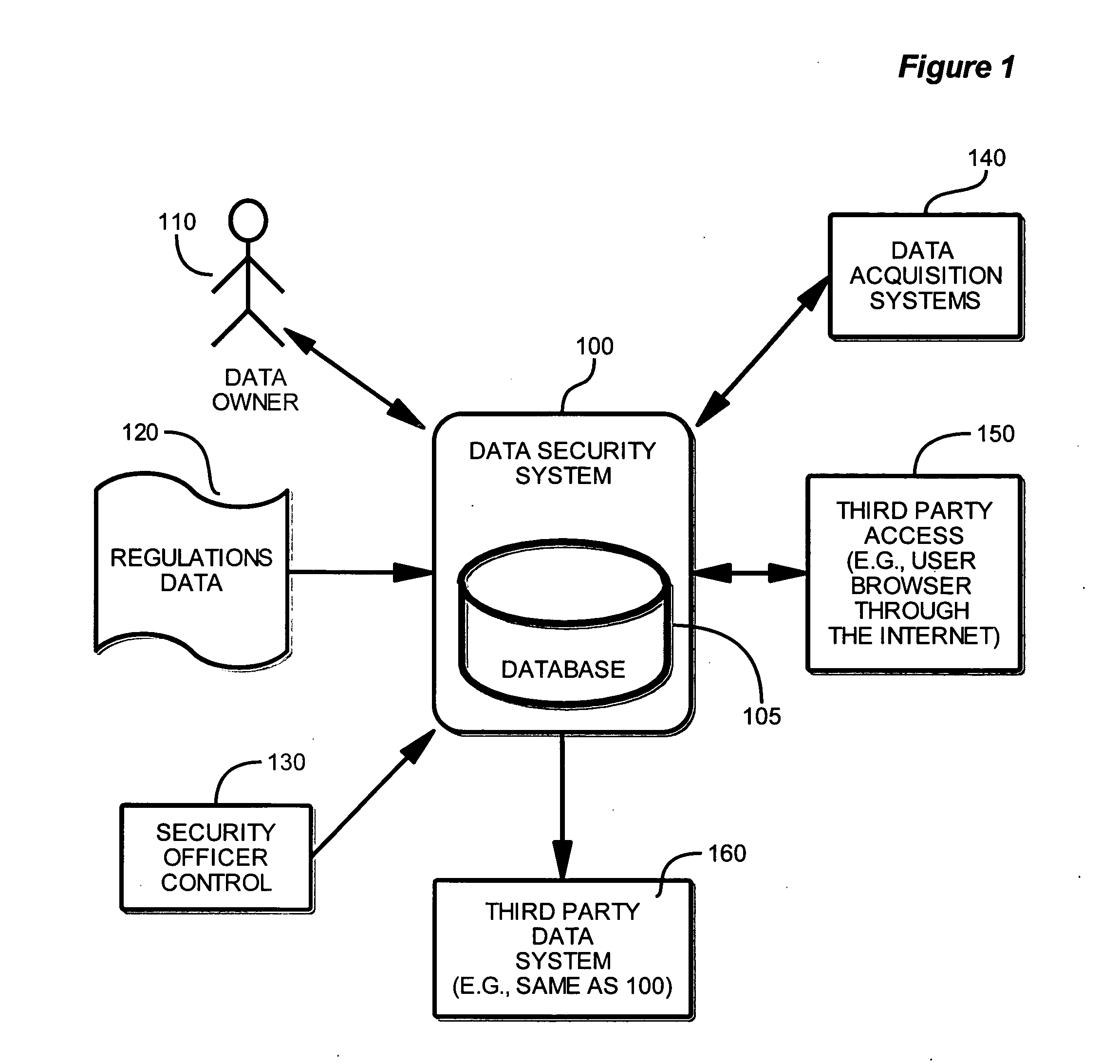
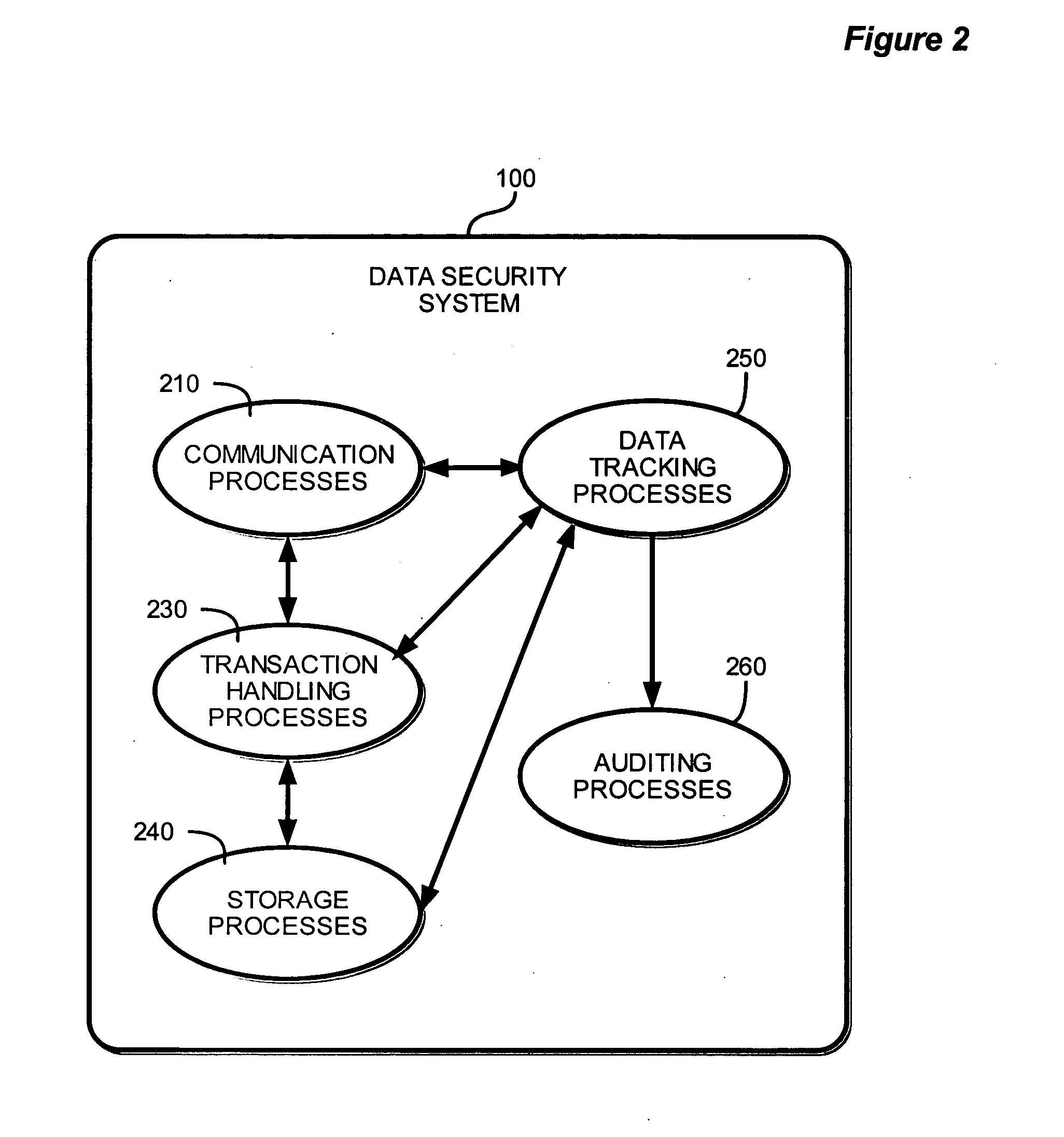
Method and system for obtaining, maintaining and distributing data
InactiveUS20060004588A1Avoid accessPayment architectureSpecial data processing applicationsPrivacy rightsSecurity level
A method and apparatus for storing and distributing protected information, while complying with regulations regarding privacy rights, are described. The system receives multiple configuration settings from individuals and from a security officer. Those configuration settings are used to determine access level attributes, which allow others to access the data. Furthermore, the system implements workflow configuration, which allows the system to manage the protected data within a framework of operational procedures. One or more authentication and encryption methods are implemented to assure that data is transmitted and stored with the highest level of security.
Owner:ANANDA MOHAN
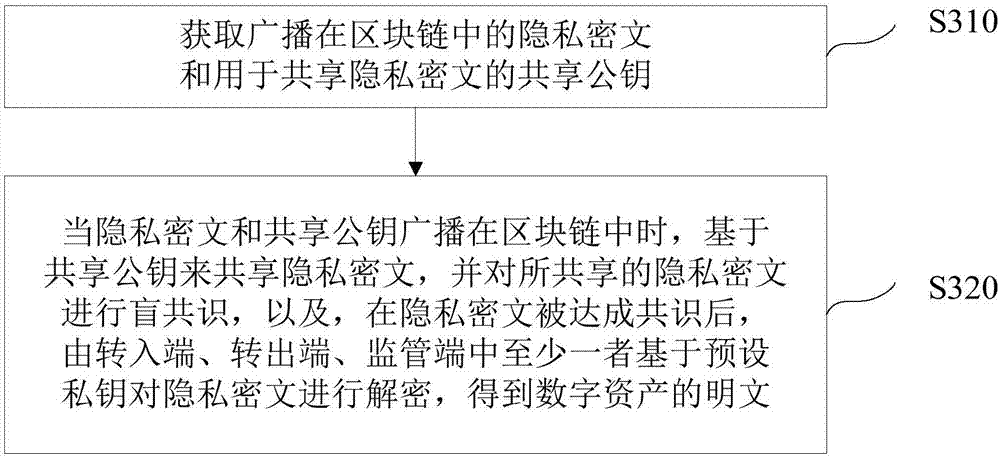
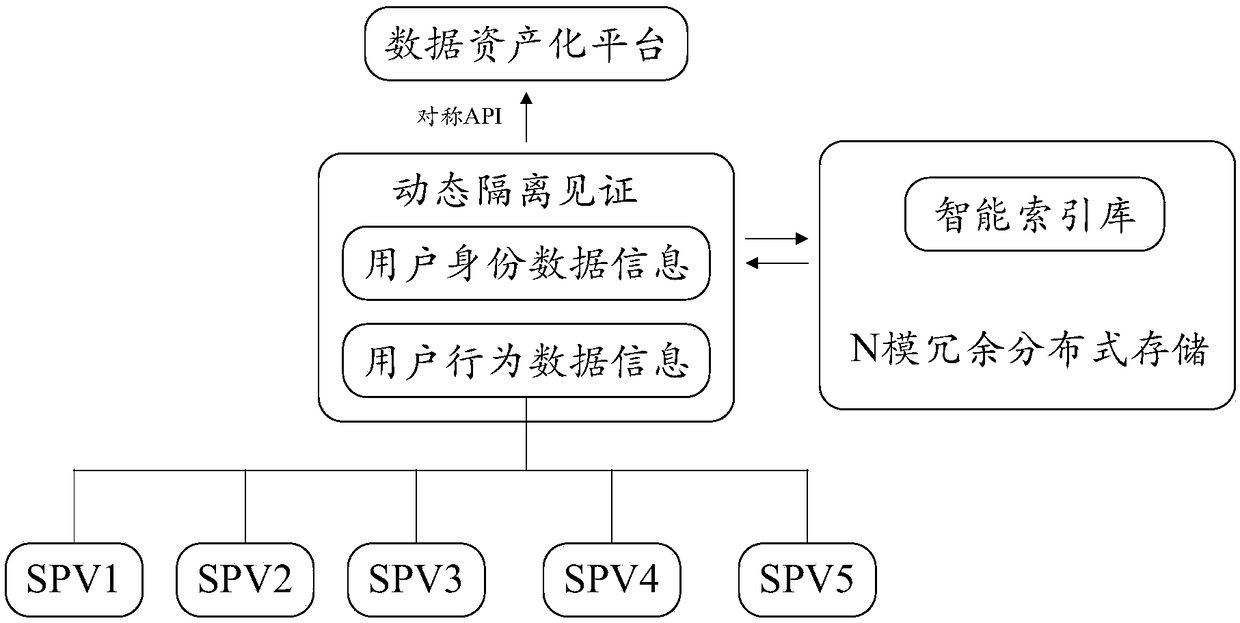
Blockchain-based digital asset processing method and device
ActiveCN106982205AProtection of privacySmooth circulationKey distribution for secure communicationDigital data protectionPlaintextCiphertext
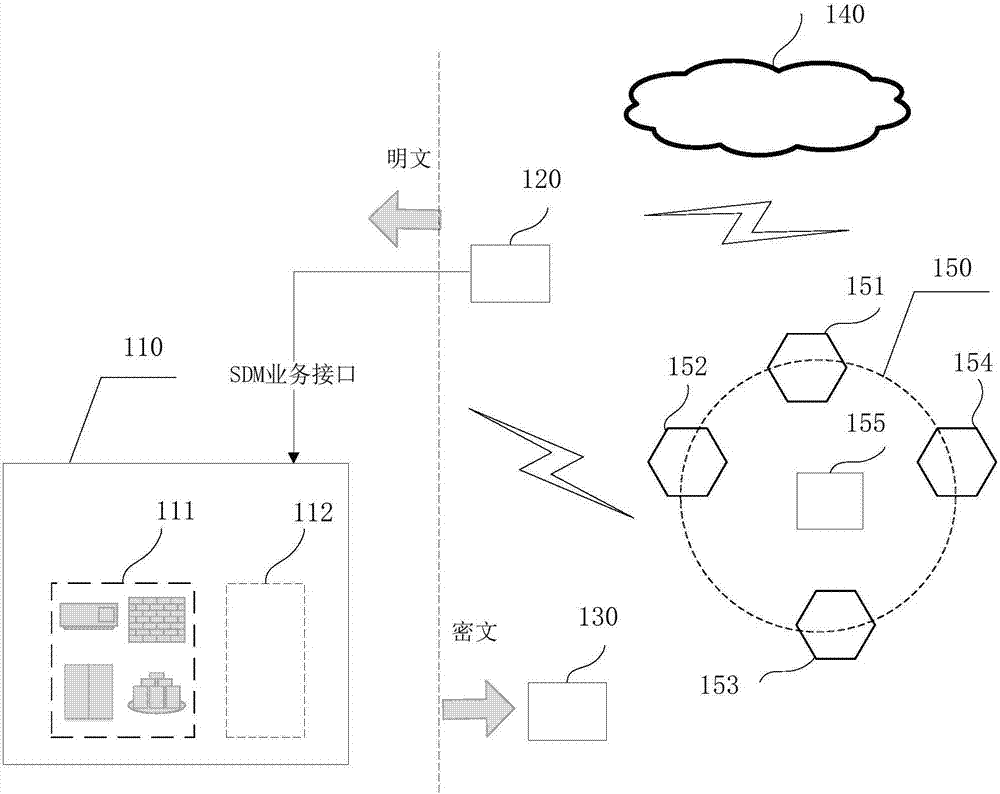
The invention discloses a blockchain-based digital asset processing method and device. The method comprises the following steps: receiving private ciphertext for a digital asset circulated from a sending end to a receiving end through a blockchain, and a preset public key; and obtaining a sharing public key for sharing the private ciphertext based on the preset public key, so that when the private ciphertext and the sharing public key are broadcast in the blockchain, blockchain nodes on the blockchain can share the private ciphertext based on the sharing public key and reach a blind consensus on the shared private ciphertext, and after the consensus on the private ciphertext is reached, the private ciphertext can be decrypted by at least one of three parties, i.e., the sending end, the receiving end and a monitoring end, based on a preset private key to obtain plaintext of the digital asset. The method and device provided by the embodiment of the invention has the advantages that the privacy right of a user is protected; under the premise of privacy protection, the single general digital asset can be smoothly circulated within one blockchain or among multiple blockchains, and a total currency amount remains unchanged; and a monitoring party other than the transaction parties can monitor transaction information at any time.
Owner:中钞信用卡产业发展有限公司杭州区块链技术研究院 +1
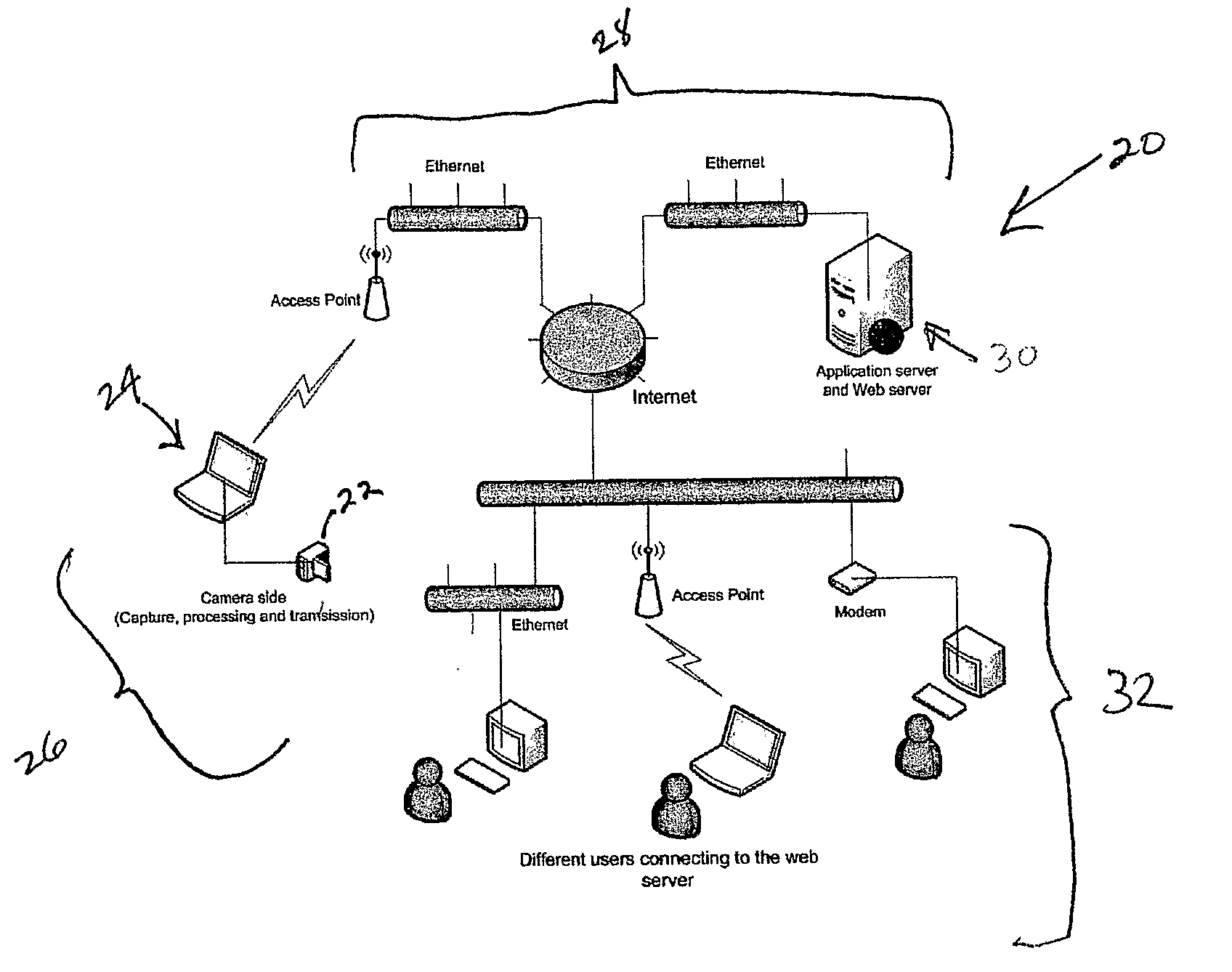
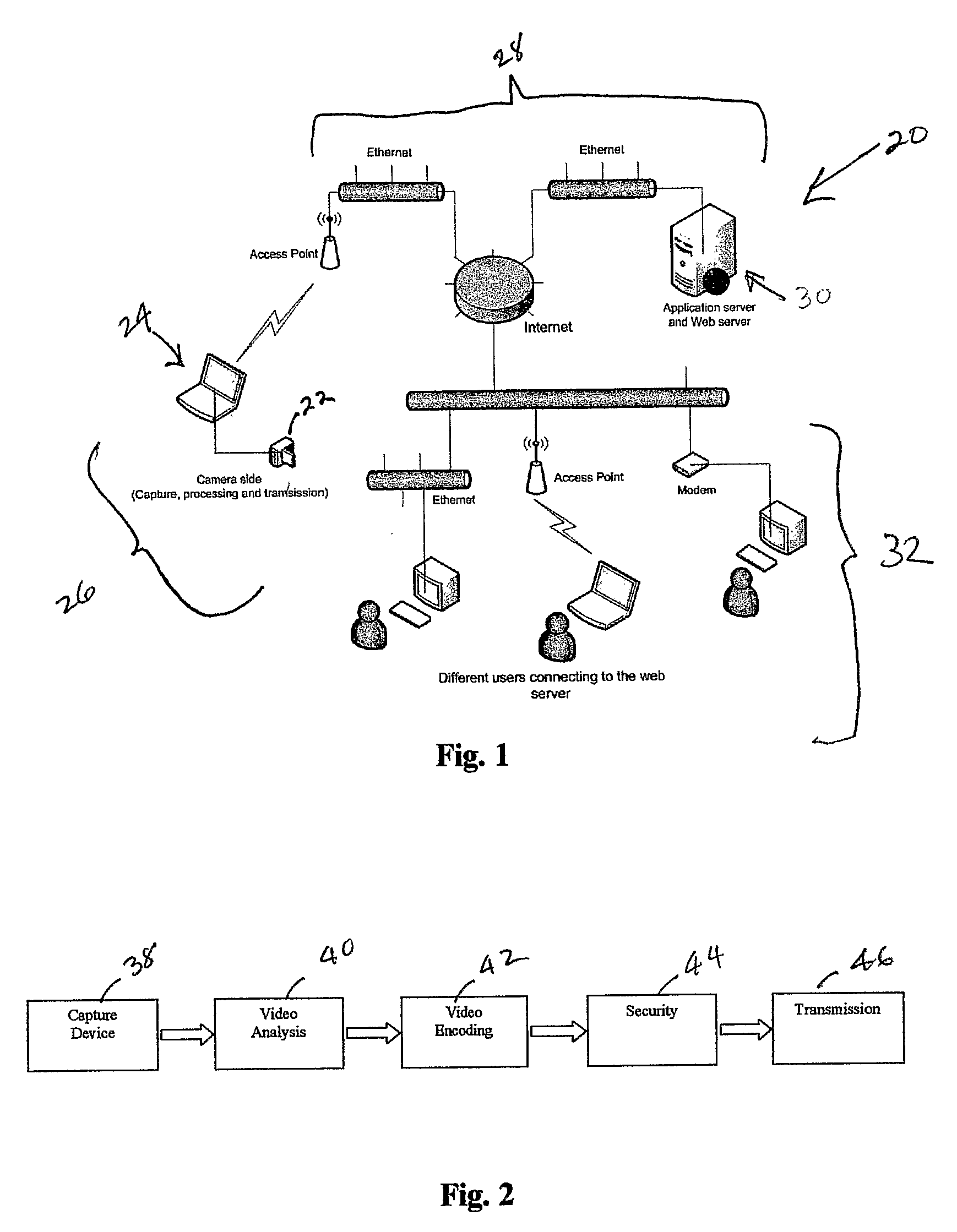
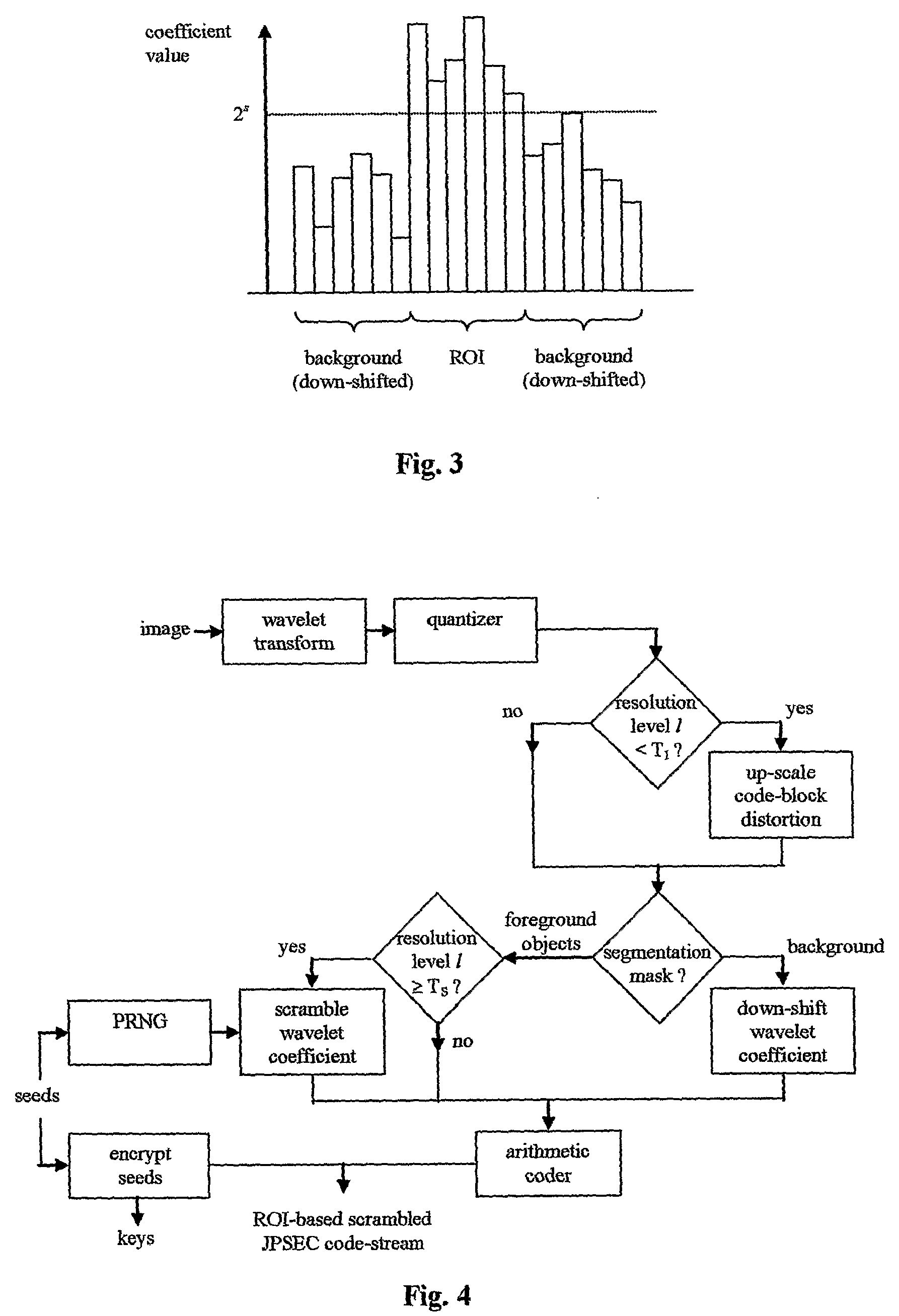
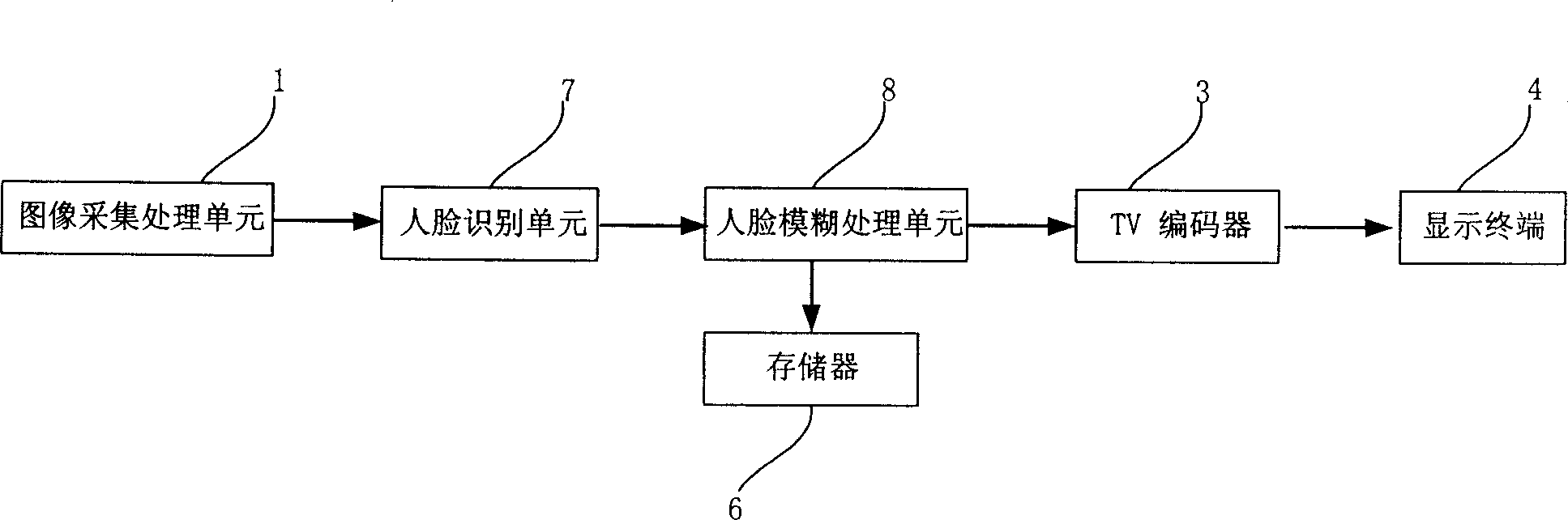
Efficient Scrambling Of Regions Of Interest In An Image Or Video To Preserve Privacy
InactiveUS20080117295A1Drawbacks of known code block scrambling techniques are avoidedLimited degreeCharacter and pattern recognitionColor television detailsFace detectionCoding block
A video surveillance system is disclosed which addresses the issue of privacy rights and scrambles regions of interest in a scene in a video scene to protect the privacy of human faces and objects captured by the system. The video surveillance system is configured to identify persons and or objects captured in a region of interest of a video scene by various techniques, such as detecting changes in a scene or by face detection. In accordance with an important aspect of the invention regions of interest are automatically scrambled, for example, by way of a private encryption key, while the balance of the video scene is left in tact and is thus recognizable. Such region of interest scrambling provides distinct advantages over known code block scrambling techniques. The entire video scenes are then compressed, by one or more compression standards, such as JPEG 2000. In accordance with one aspect of the invention, the degree of scrambling can be controlled.
Owner:EMITALL SURVEILLANCE
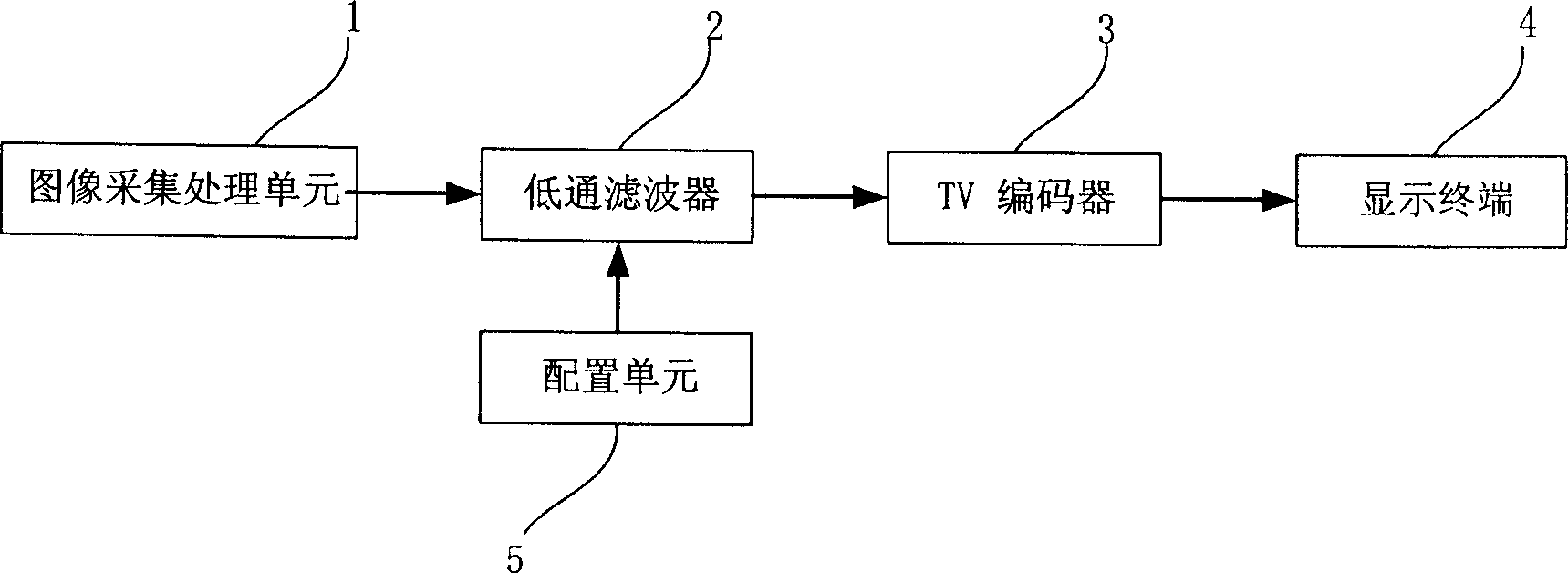
Visible image monitoring method for protecting privacy right and its system
ActiveCN1767638AImplement Motion BlurSolve protection problemsAnalogue secracy/subscription systemsClosed circuit television systemsPrivacy rightsFuzzy process
This invention discloses a visual image monitor method for protecting private right including the following steps: a, collecting images, b, carrying out fuzzy process to the collected images, c, displaying or storing the fuzz images at the display terminal. A system for realizing the method is also disclosed.
Owner:中星智能系统技术有限公司
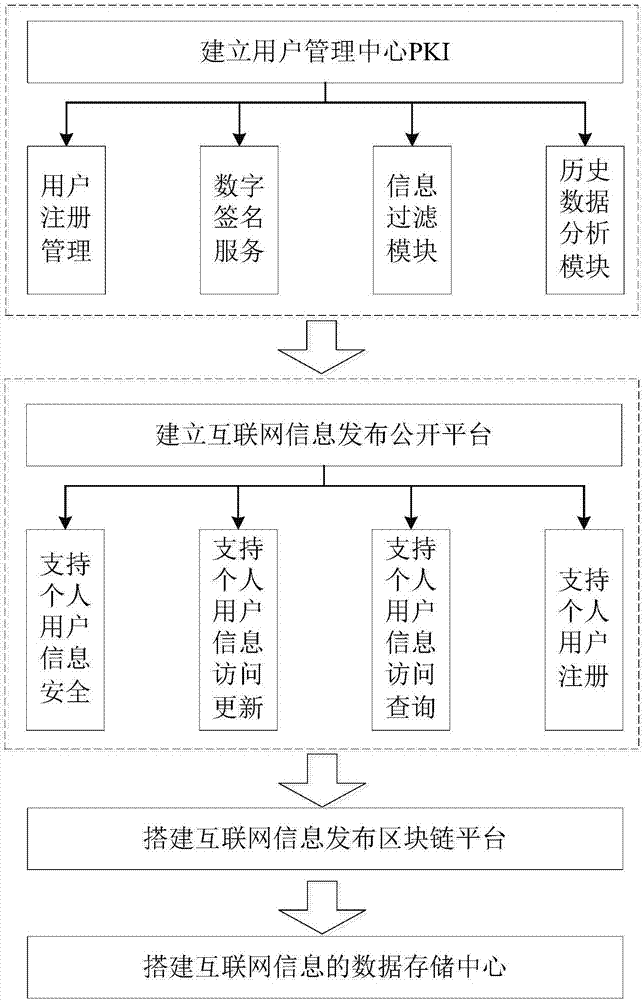
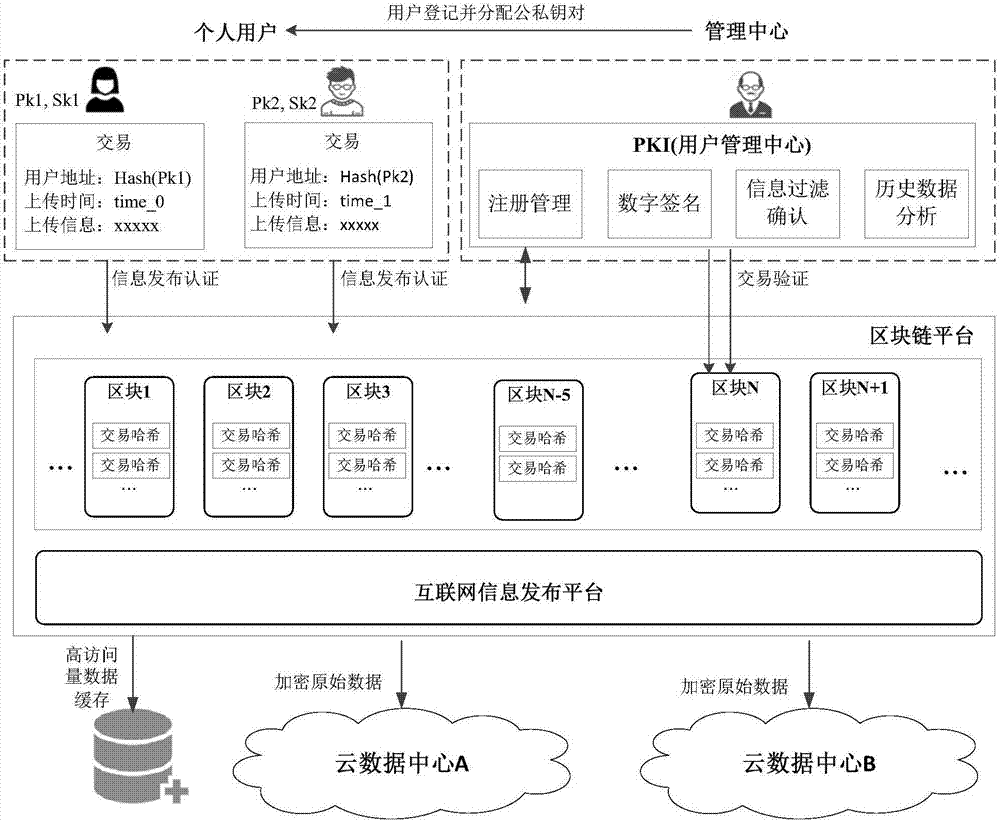
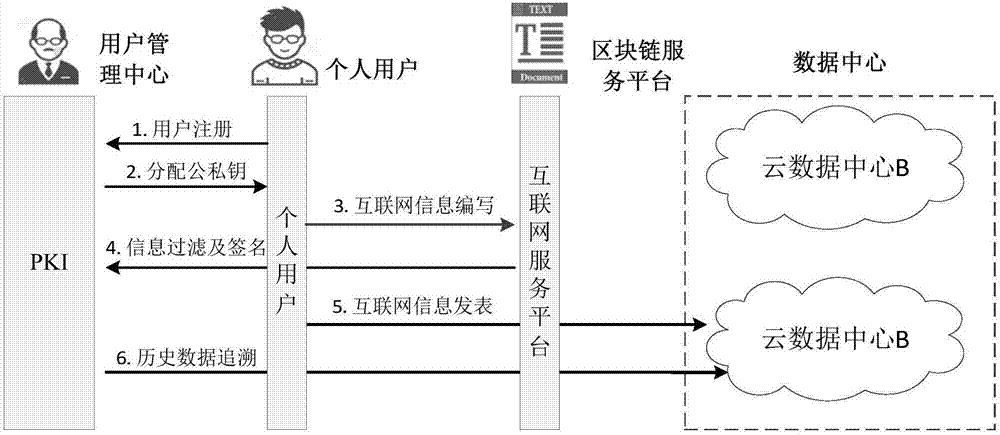
Public opinion detection platform construction method based on block chain technology
InactiveCN107018146AGuaranteed freedom of speechPersonality rights are not violatedUser identity/authority verificationIntellectual propertyOriginal data
The invention discloses a public opinion detection platform construction method based on a block chain technology. The public opinion detection platform construction method comprises the steps of: establishing a user public opinion monitoring centre at first, distributing public and private key pairs to personal users, and providing digital signature service, filtering and historical analysis for internet information; establishing a personal user comment publishing infrastructure platform; setting up a block chain foundation platform published to the internet information; establishing an internet information writing mechanism based on a block chain; and, setting up an internet data storage centre based on a cloud storage platform, and storing original data in a remote cloud data centre after encrypting the original data through the public key of a user. The public opinion detection platform construction method disclosed by the invention has very important significance in the aspects as follows: the public opinion detection is standardized; the personality right, the portrait right, the privacy right and the intellectual property of the personal users can not be infringed, etc.
Owner:JINAN UNIVERSITY
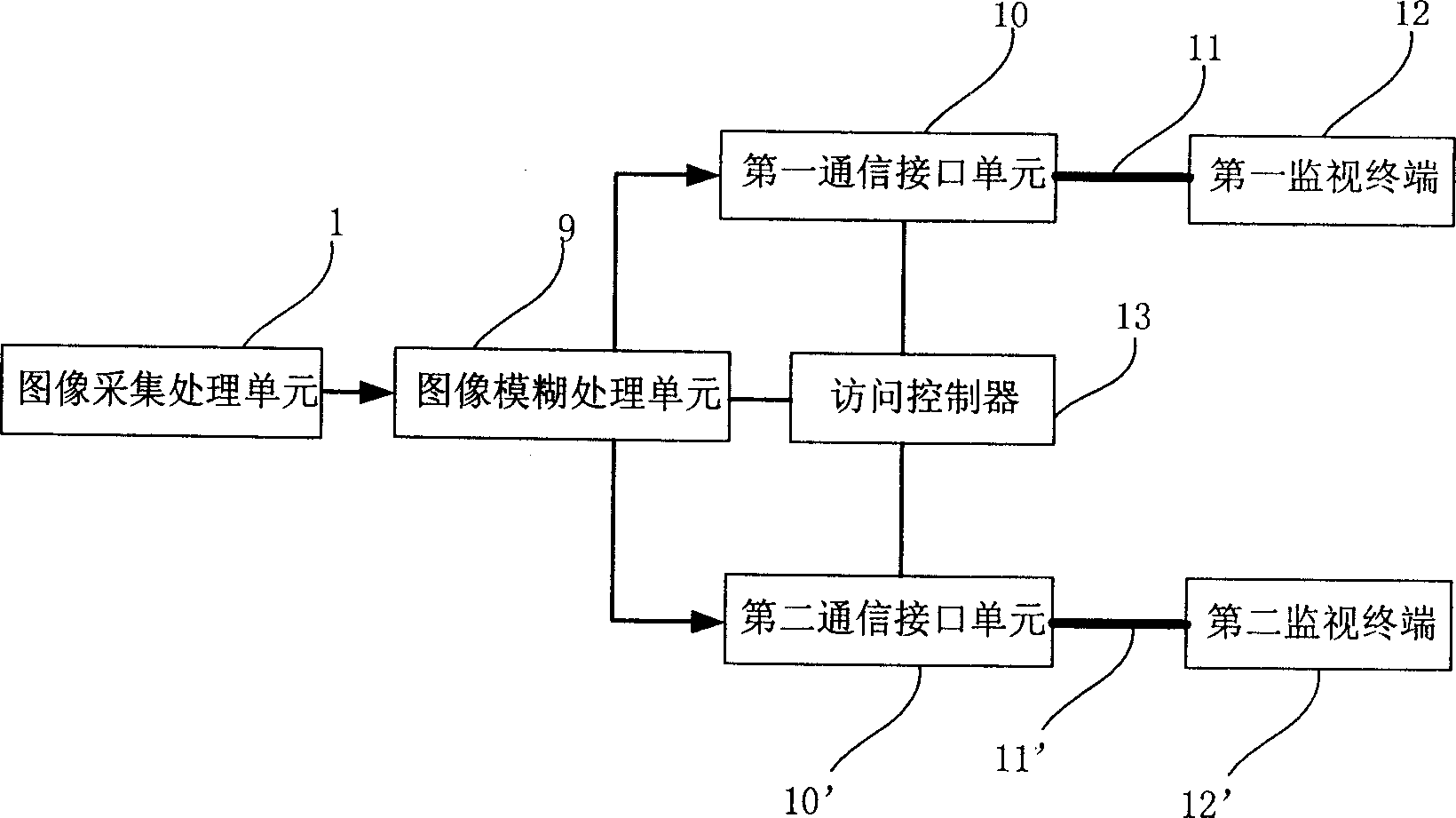
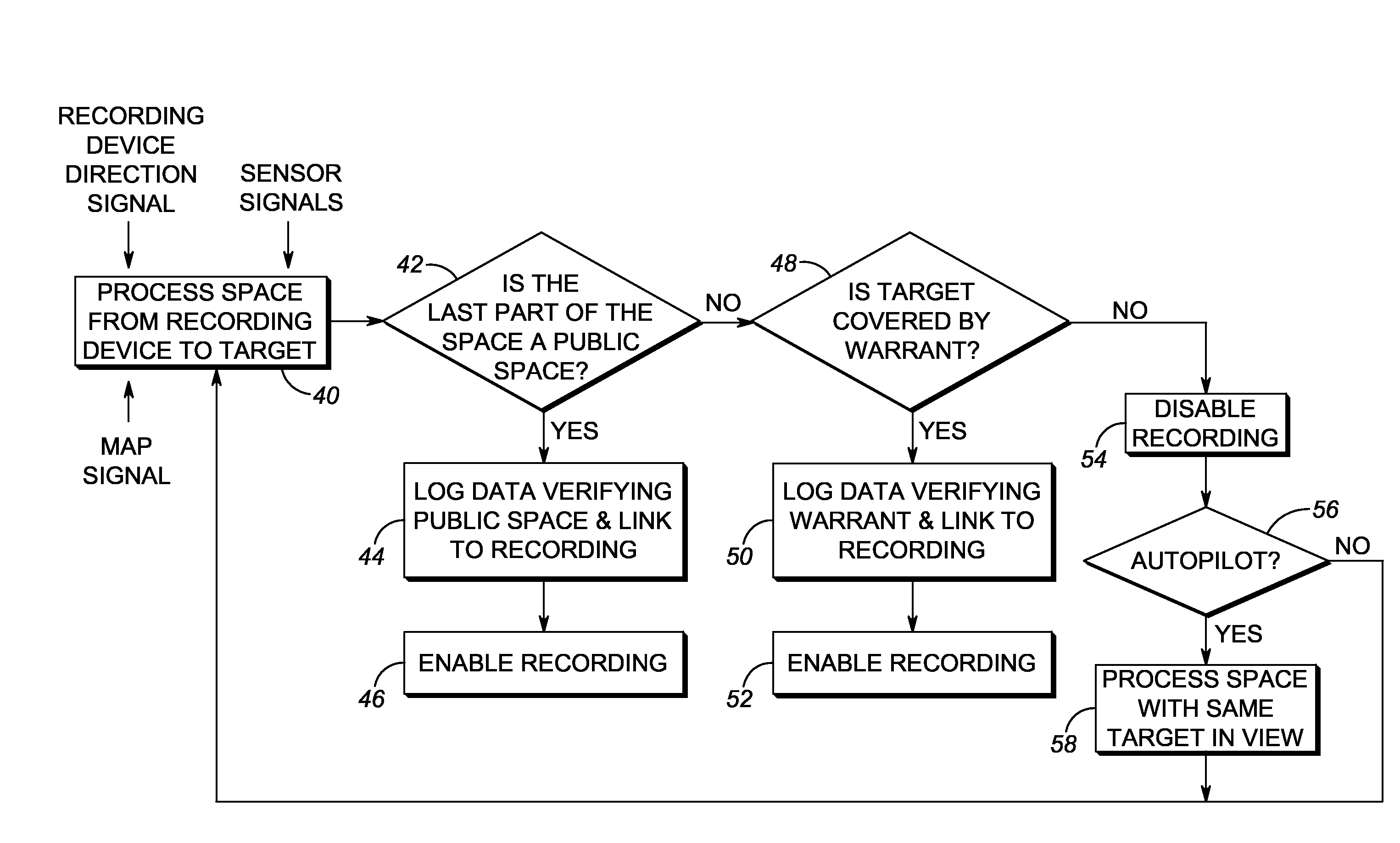
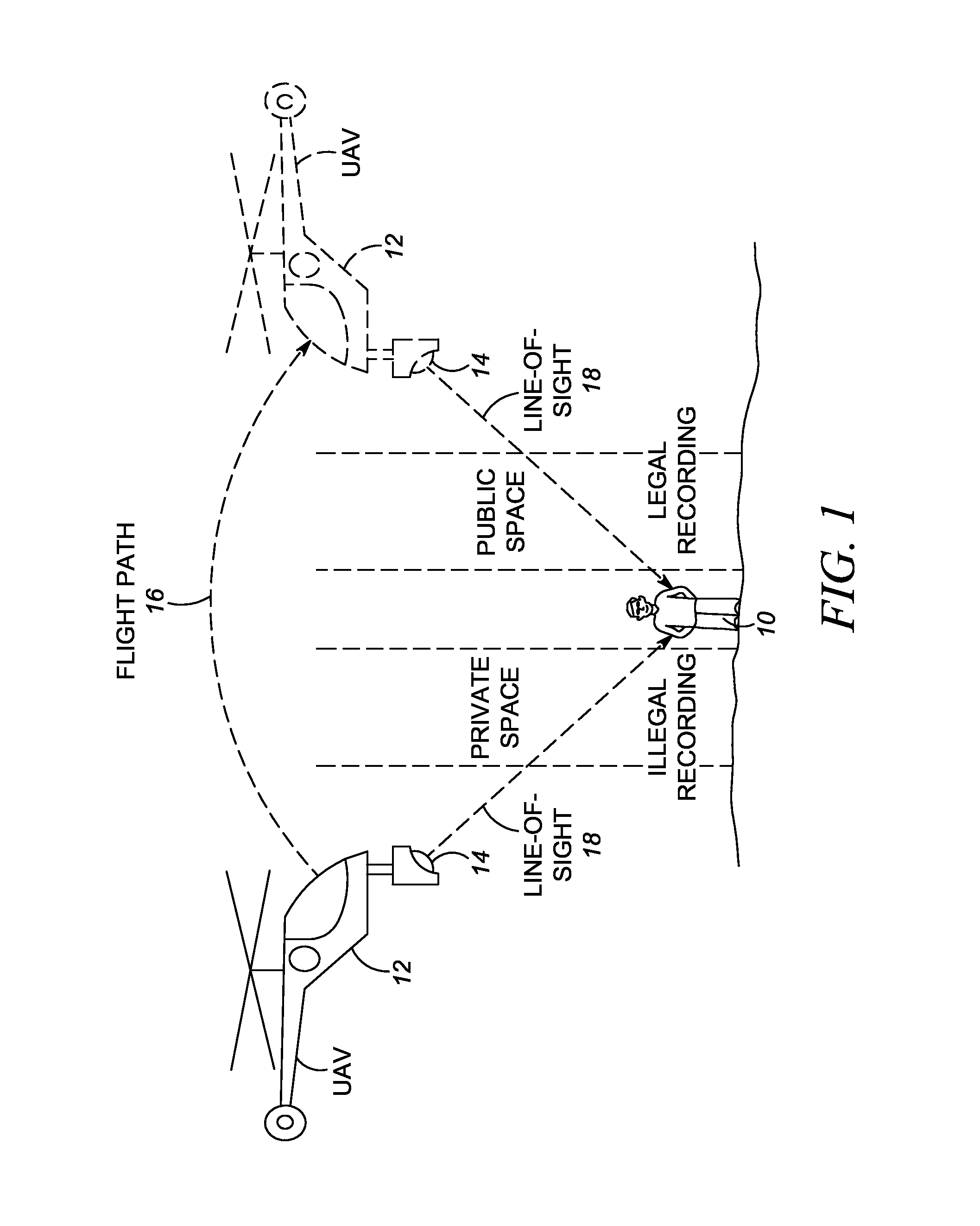
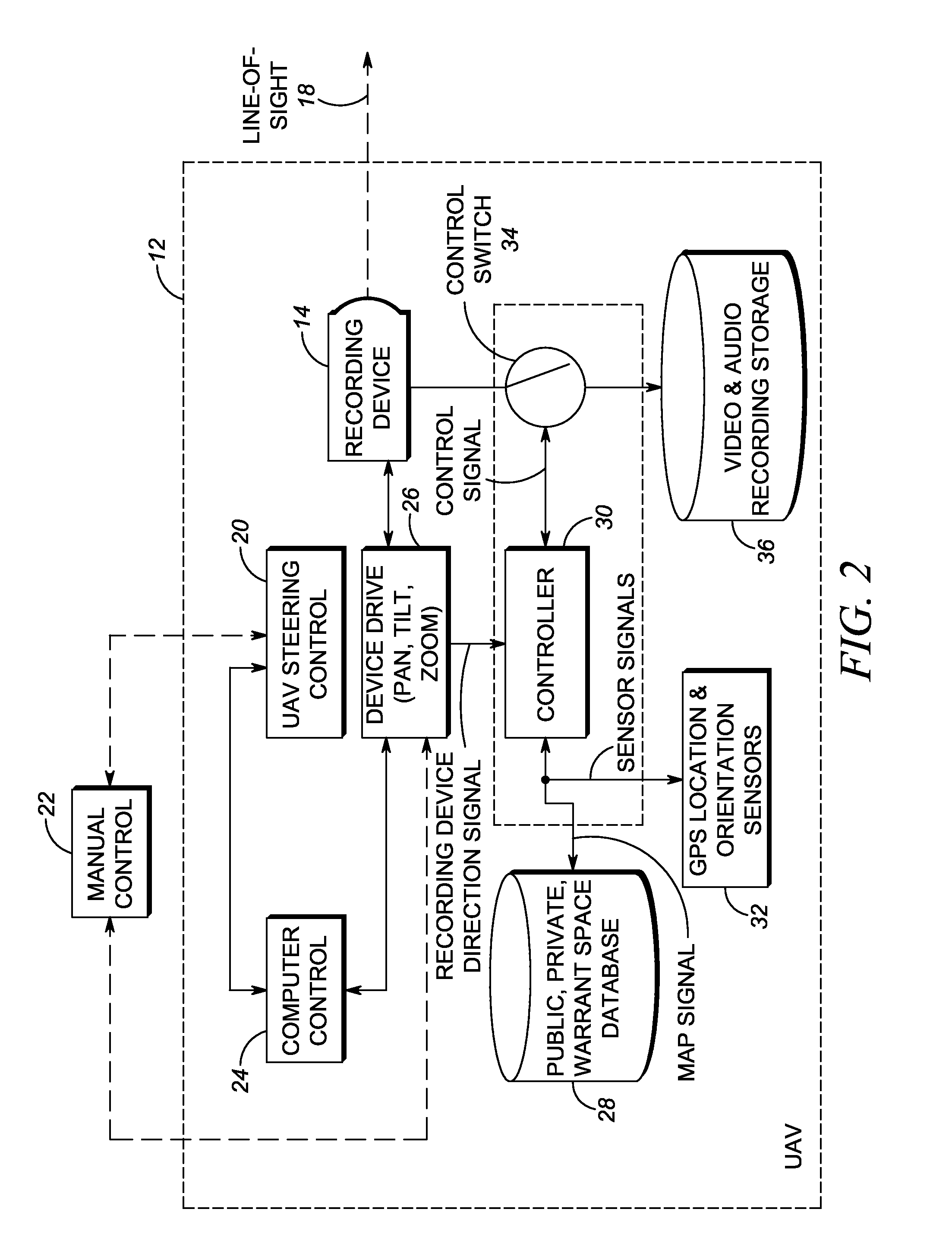
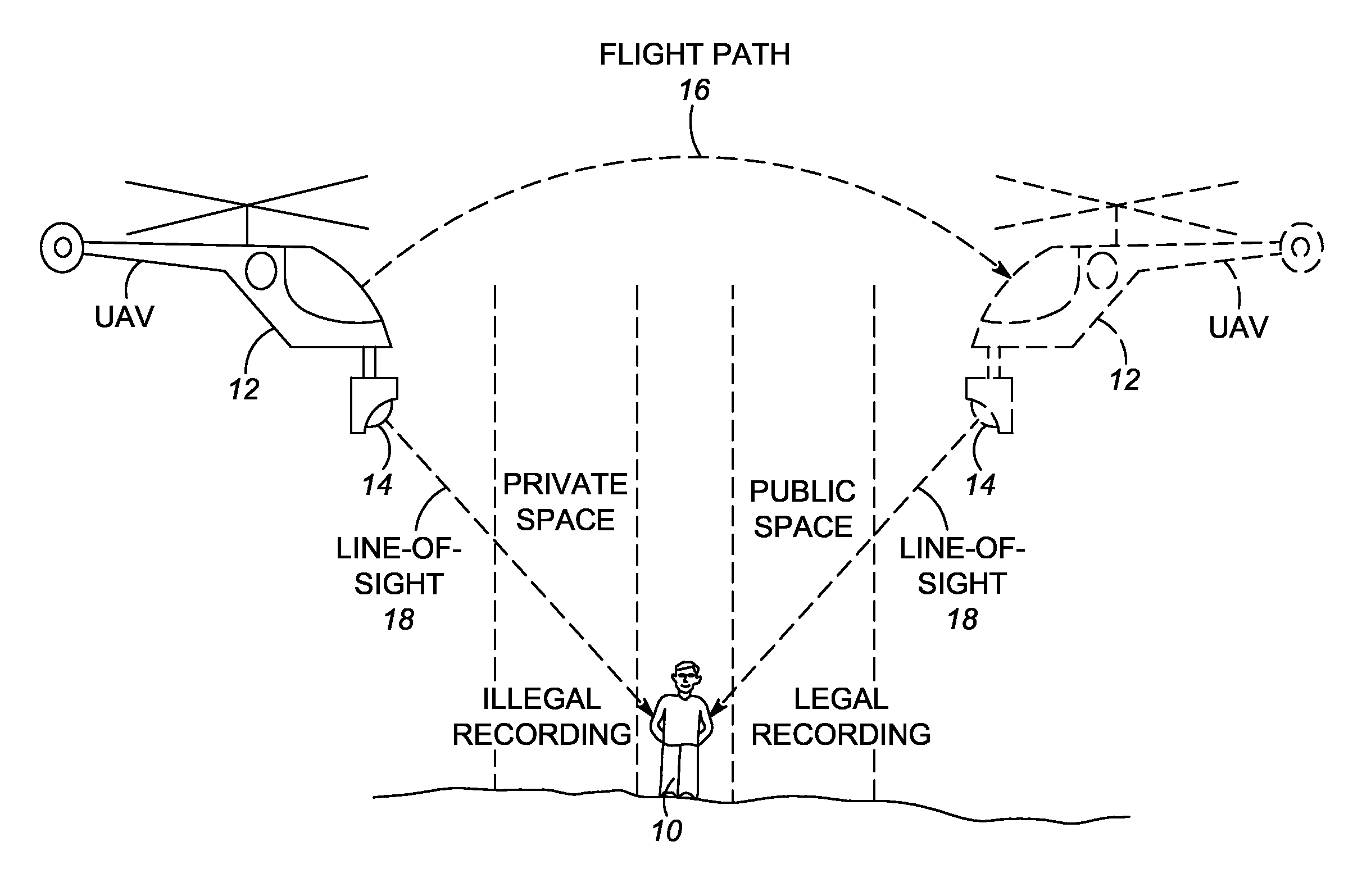
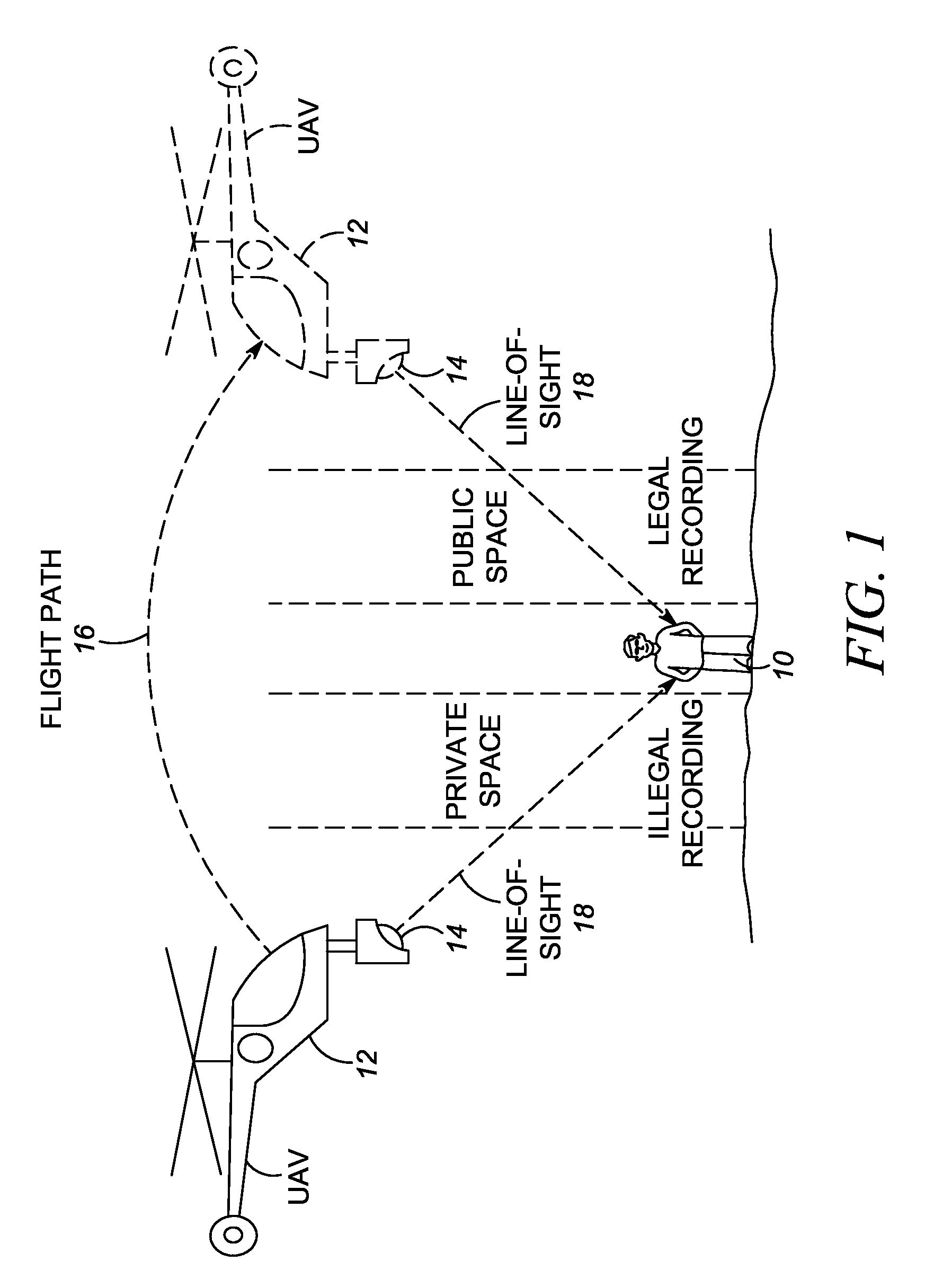
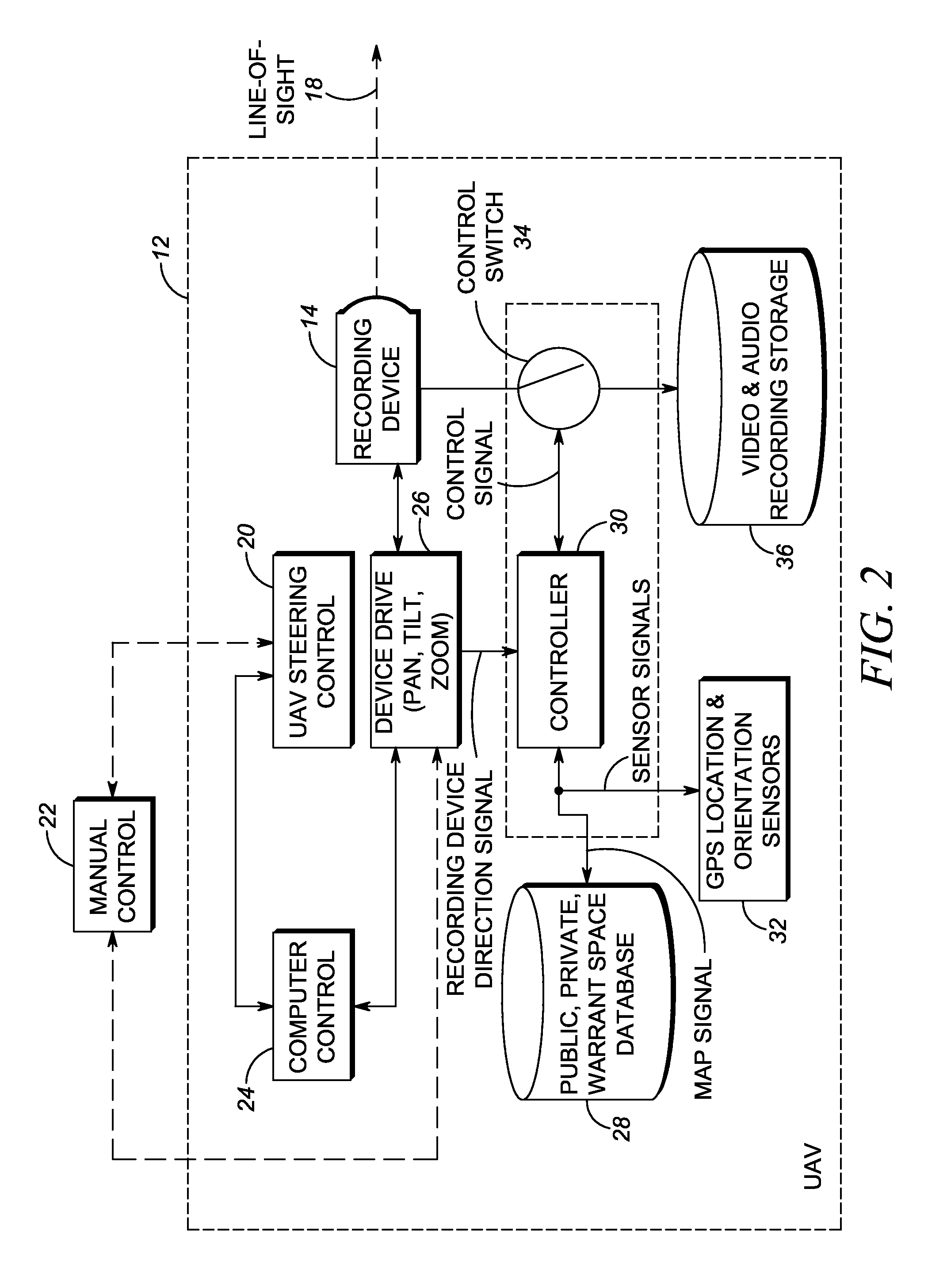
Method of and system for conducting mobile video/audio surveillance in compliance with privacy rights
A video / audio recording device is mounted on a mobile support for recording surveillance information. The recording device is movable relative to the mobile support to adjustably position the recording device to face the target along a line-of-sight during recording. A database stores public map spaces, private map spaces, and warrant spaces that exist in a geographic area to be surveilled. A programmed controller accesses the database, determines whether the target is recordable from a public map space along the line-of-sight between the recording device and the target and / or whether the target is covered by a warrant space, and controls the recording device to record the surveillance information upon a successful determination that the target is so recordable or so covered.
Owner:MOTOROLA SOLUTIONS INC
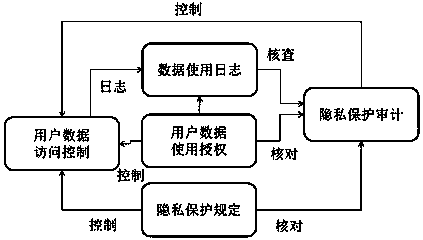
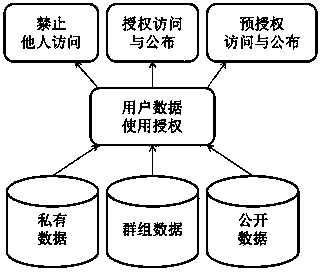
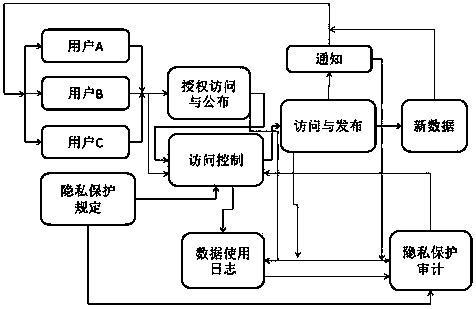
Protecting method for correlated privacy
InactiveCN103488957AGuaranteed Extended RangeEnsure transparencyDigital data protectionData access controlUser privacy
The invention relates to a protecting method for correlated privacy. The protecting method is applied to correlated privacy protection in cloud computing systems, and comprises five modules including data use automation, data use log, privacy protection audit, privacy protection regulation and user data access control. By the protecting method, functions such as authorized access of user data, access control, data use log and privacy protection audit can be completed, and the objectives such as authorized access of user privacy, transparency and reliability of access and publication and guaranteed privacy right are achieved.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Medical information exchange display system
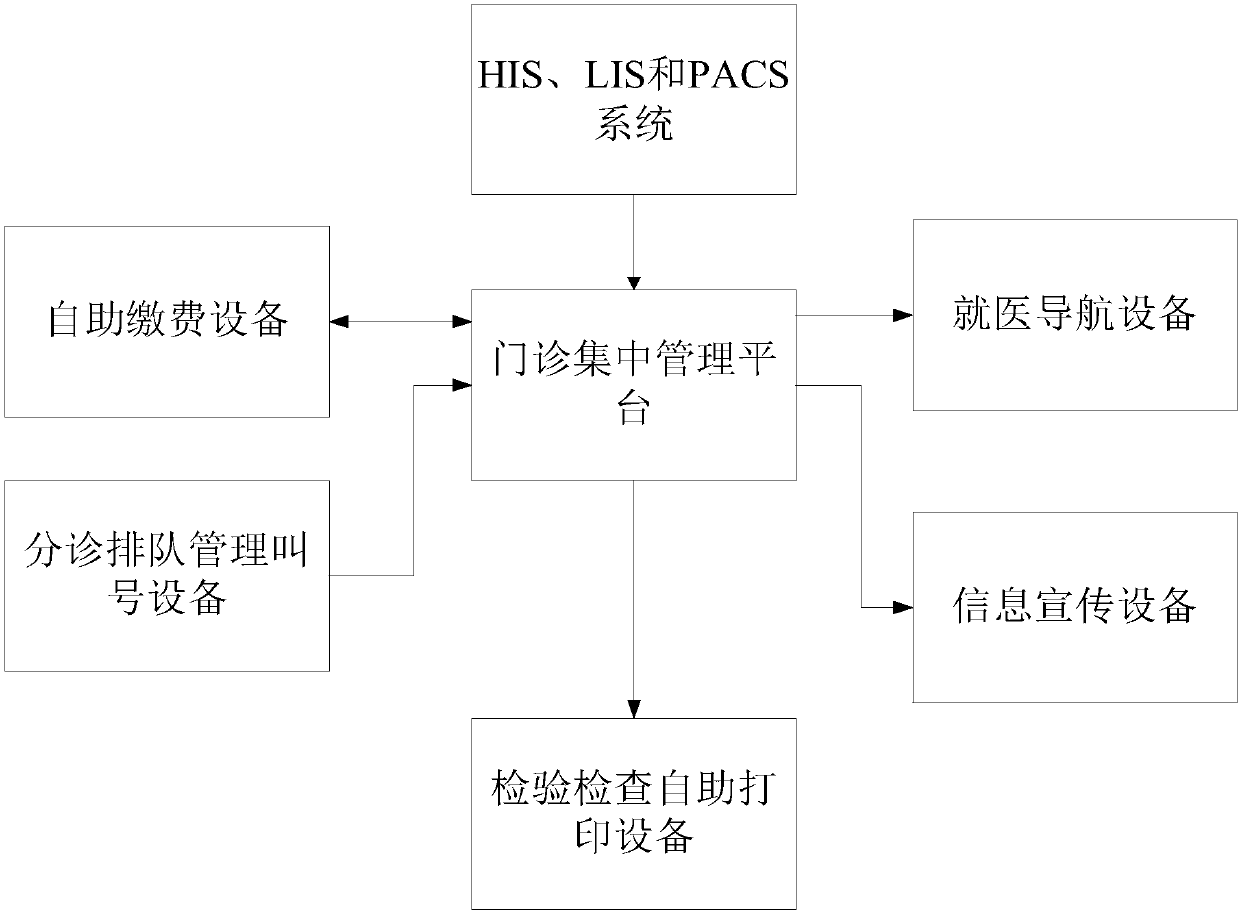
InactiveCN107644675AImprove printing efficiencyImprove service efficiencyMedical equipmentTriageDecision taking
The invention discloses a medical information exchange display system. The system comprises an outpatient centralized management platform, a medical navigation device, an information publicity device,a self-service payment device, a triage queue management calling device and an inspection printing device, wherein the medical navigation device, the information publicity device, the self-service payment device, the triage queue management calling device and the test printing device are connected with the outpatient centralized management platform. According to the invention, the triage queue management calling device carries out triage management and queue calling, so as to avoid wrong arranging, queue-cutting, confusion, noise and the like and reduce many unnecessary disputes; an equal, reasonable, ordered and good environment is created; the unique identification function of a fingerprint identifier arranged on a triage station protects the privacy right of a patient, which enhances the image of a hospital; the efficiency of registration, payment and inspection report printing of the hospital can be improved; the service quality is improved; the waiting time of the patient is reduced; chaos in a consulting room is eliminated; the assessment of a doctor is scientific and reasonable; and an effective basis is provided for leadership's decision-making.
Owner:四川聚典新业科技有限公司
Advertisement propagation method and device based on block chain
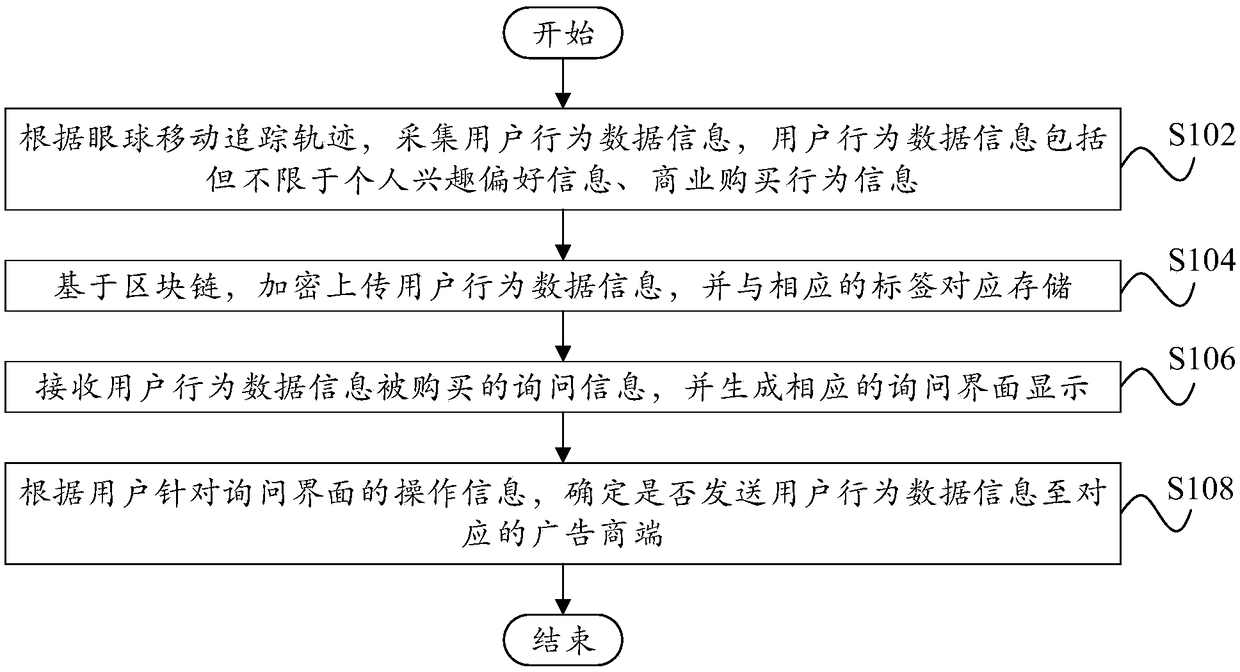
PendingCN108764975ARealize mesh transmissionSolve the expansion problemAdvertisementsDigital data protectionData informationPrivacy rights
The invention provides an advertisement propagation method and a device based on a block chain, wherein, the method comprises: collecting user behavior data information including but not limited to personal interest preference information and commercial purchase behavior information according to an eye movement tracking trajectory; based on the block chain, encrypting and uploading the user behavior data information, and storing the information corresponding to a corresponding tag; receiving inquiry information that the user behavior data information is purchased, and generating correspondinginquiry interface display; and according to the operation information of the user for the inquiry interface, determining whether to send the user behavior data information to a corresponding advertiser terminal. Through the technical scheme of the invention, the collection of the user behavior data information is more comprehensive and multi-dimensional, the channel of advertisement propagation ismore accurate, the privacy right of the user is protected, and the advertisement cost of the advertiser is saved.
Owner:深圳纬目信息技术有限公司
Pressure-sensor-based system and method for monitoring motions of going to bed or getting out of bed
InactiveCN107028718AAvoid exposureEasy to monitorNursing bedsAmbulance serviceControl signalComputer module
The invention relates to a pressure-sensor-based system and method for monitoring motions of going to bed or getting out of bed. A plurality of pressure sensors are arranged on corresponding pressure sensitive areas when a user goes to bed or gets out of bed, the pressure sensors are correspondingly distributed and arrayed according to characteristics of the pressure sensitive areas, so that the pressure sensors are adopted to detect pressure changes of the pressure sensitive areas in real time, then, the pressure changes detected by the pressure sensors are sent to a processor through a communication module, finally, the processor is adopted to generate control signals according to the pressure changes, and therefore the motions of going to bed or getting out of bed are monitored in real time according to the control signals. In this way, by the adoption of the pressure-sensor-based system and method for monitoring the motions of going to bed or getting out of bed, the situation is avoided that the daily life of the user is exposed to a camera, the privacy right of the user is protected, the defect of lacking of inspectors can be solved, further damage to the user can be avoided, and optimal monitoring on the user is achieved with relatively low cost.
Owner:SHENZHEN INST OF ADVANCED TECH
Unmanned detector for guest room
The invention relates to a human body detector, and belongs to the technical field of human body detecting instruments. The human body detector is used for guesthouses and hostels, fixed at a certain position of a guest room and used for detecting whether accommodation staff is in the guest room or not, so that the guesthouses and the hostels are conveniently managed. Existing pyroelectric infrared sensor technology is only suitable for detecting moving objects and used for detecting infrared rays emitted by the moving objects, so that the moving objects can be perceived. A guest possibly sleeps in the guest room and does not move for a long time, so that the human body detector cannot correctly judge whether a person is in the guest room or not. By the aid of the human body detector, a pyroelectric infrared sensor head can be designed in uniform circular motion, the person serving as a detected target can be correctly detected even if the person is fixed, fixed heat sources in the guest room can transmit false information that the person is in the guest room, and the false information is shielded by the aid of corresponding technical measures. The human body detector is low in cost, and the privacy right of the guest cannot be violated.
Owner:SHENZHEN FUMEITONG TECH DEV
Access control method for protecting access privacy of user in mobile value-added service system
InactiveCN102665205AProtection precisionSuitable for development requirementsPublic key for secure communicationSecurity arrangementSurrogate keyRole management
The invention relates to the technical field of mobile value-added services, in particular to an access control method for protecting access privacy of a user in a mobile value-added service system. The method comprises system initialization, role-based authorization, certification and secret key consultation, tracking of the user and revocation of a user role. A role management center is required to implement honestly the authorization of the agent key and the opening of the anonymity, in particular, the role management center can not forge request information of the mobile user and protects interest of the user, and besides, a service provider does not know personal preferences of legal users to the mobile value-added service, so that the requirement of the system is reduced, the legitimate interests of users are safeguarded, the privacy right of users is protected and the method is suitable for development requirements of existing value added services.
Owner:JINAN UNIVERSITY
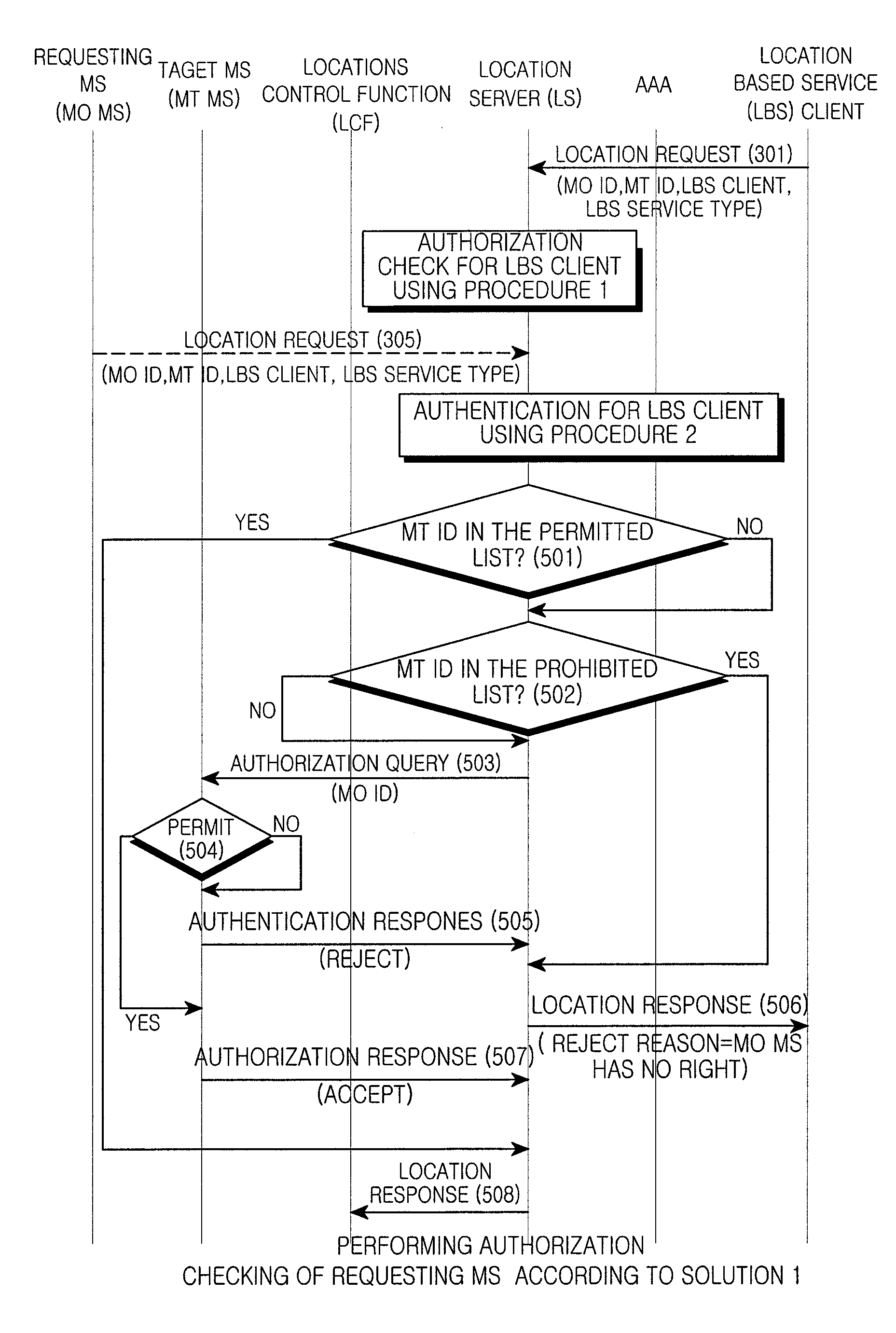
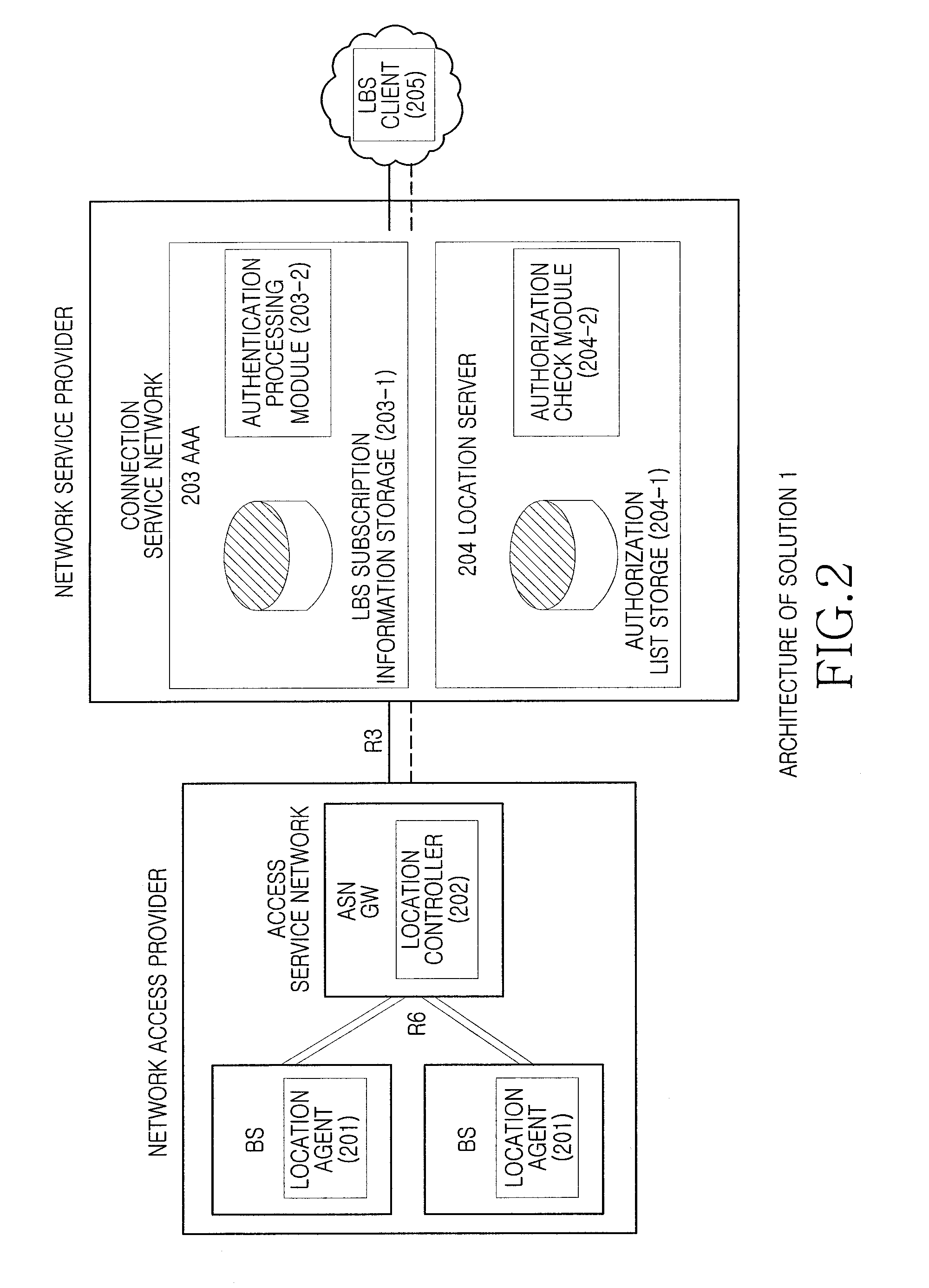
Method for reinforcing security and protecting privacy right of positioning service in Wimax network
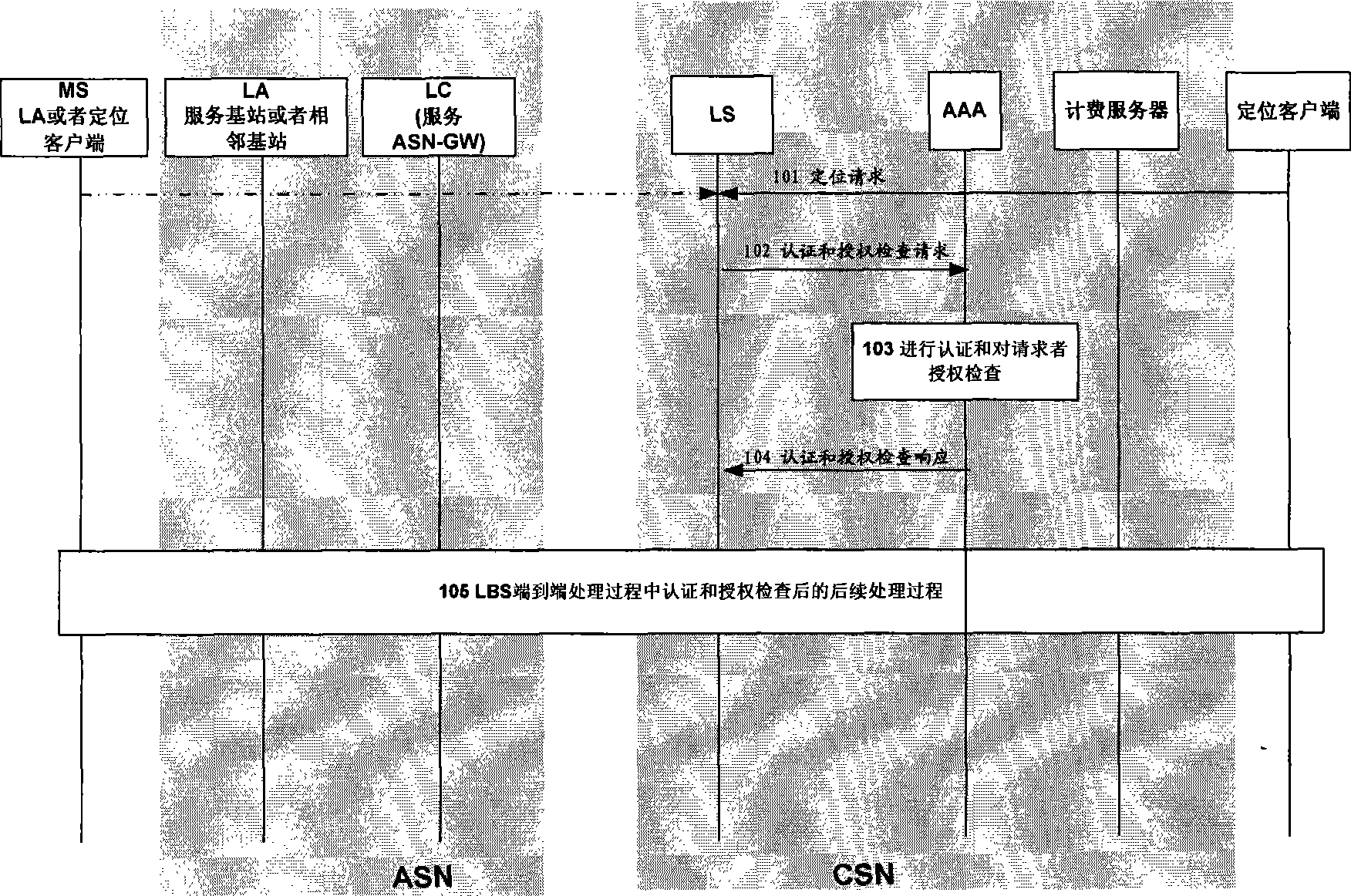
InactiveCN101370007AImprove securityProtection of privacySpecial service provision for substationData switching by path configurationPrivacy rightsUser privacy
A method for enhancing safety and protecting user privacy for positioning service in Wimax network comprises LBS client authentication, for keeping accessible LBS client list at LS, or accomplished by adopting TLS, LLS safety protocol etc; LBS service authentication, for checking if requested LBS service and its QoS matching with signed LBS service; and authorized checking of LBS requester, for LS performing authorized checking, or AAA performing authorized checking. LBS service is prevented to be acquired by illegal LBS client terminal or unsigned LBS service or unauthorized MS, thereby enhancing positioning service safety in Wimax network and protecting user privacy, making up for corresponding blank of present Wimax standard.
Owner:BEIJING SAMSUNG TELECOM R&D CENT +1
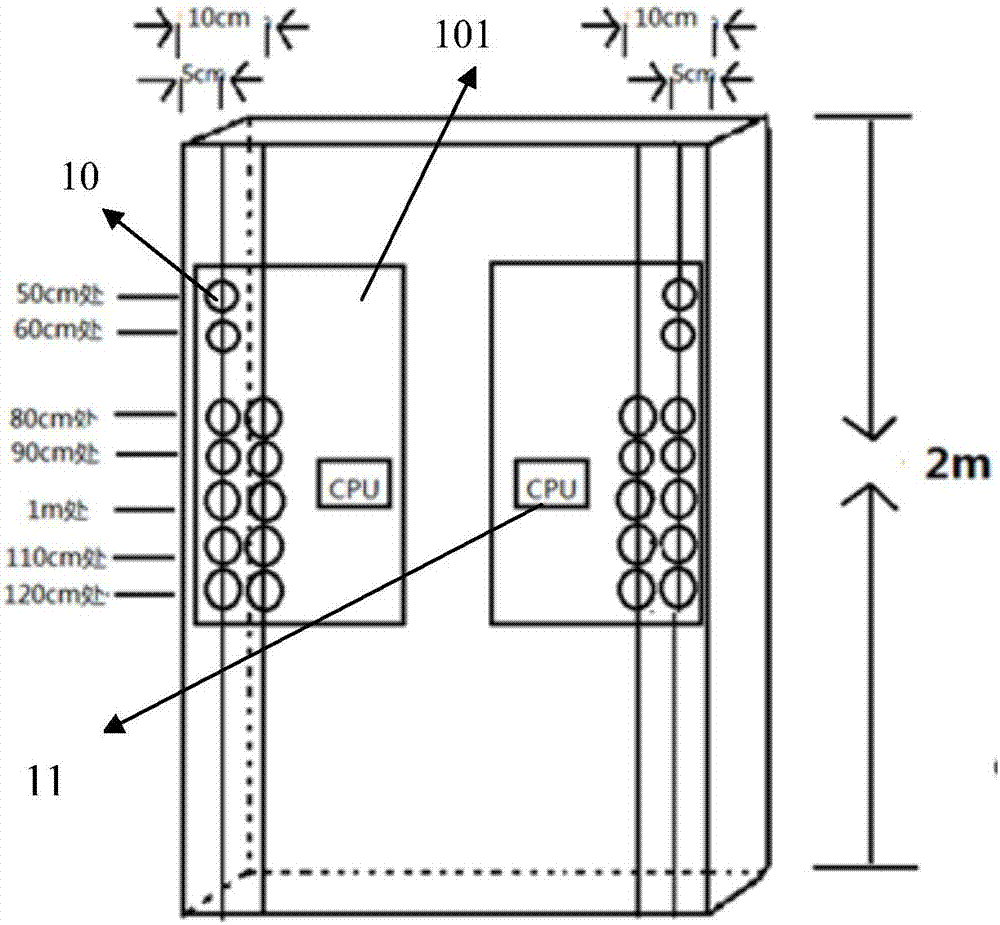
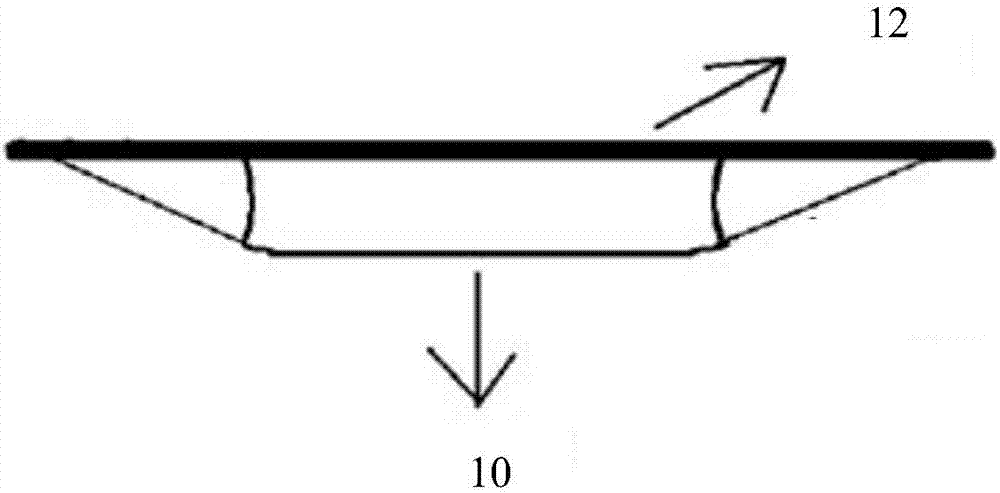
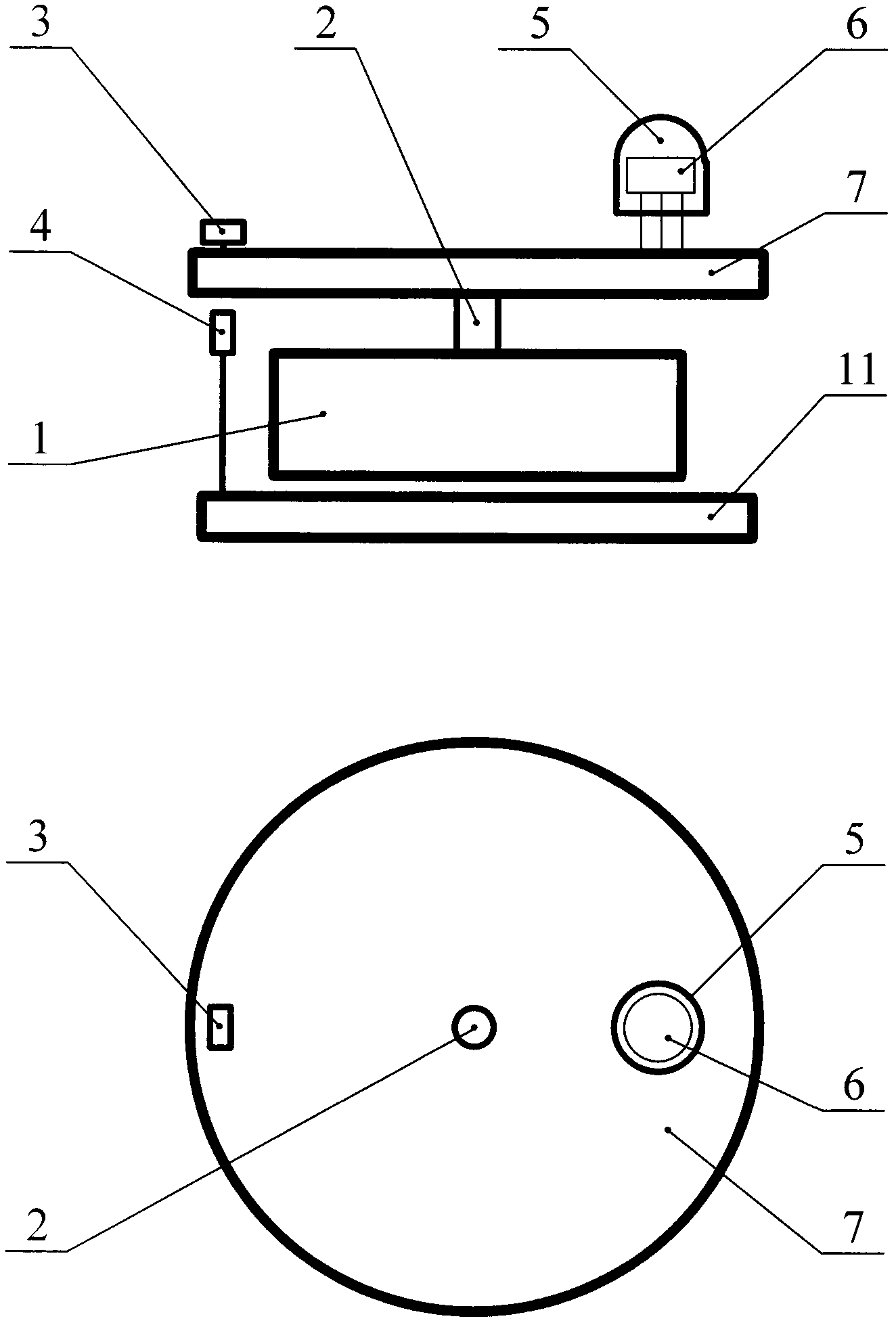
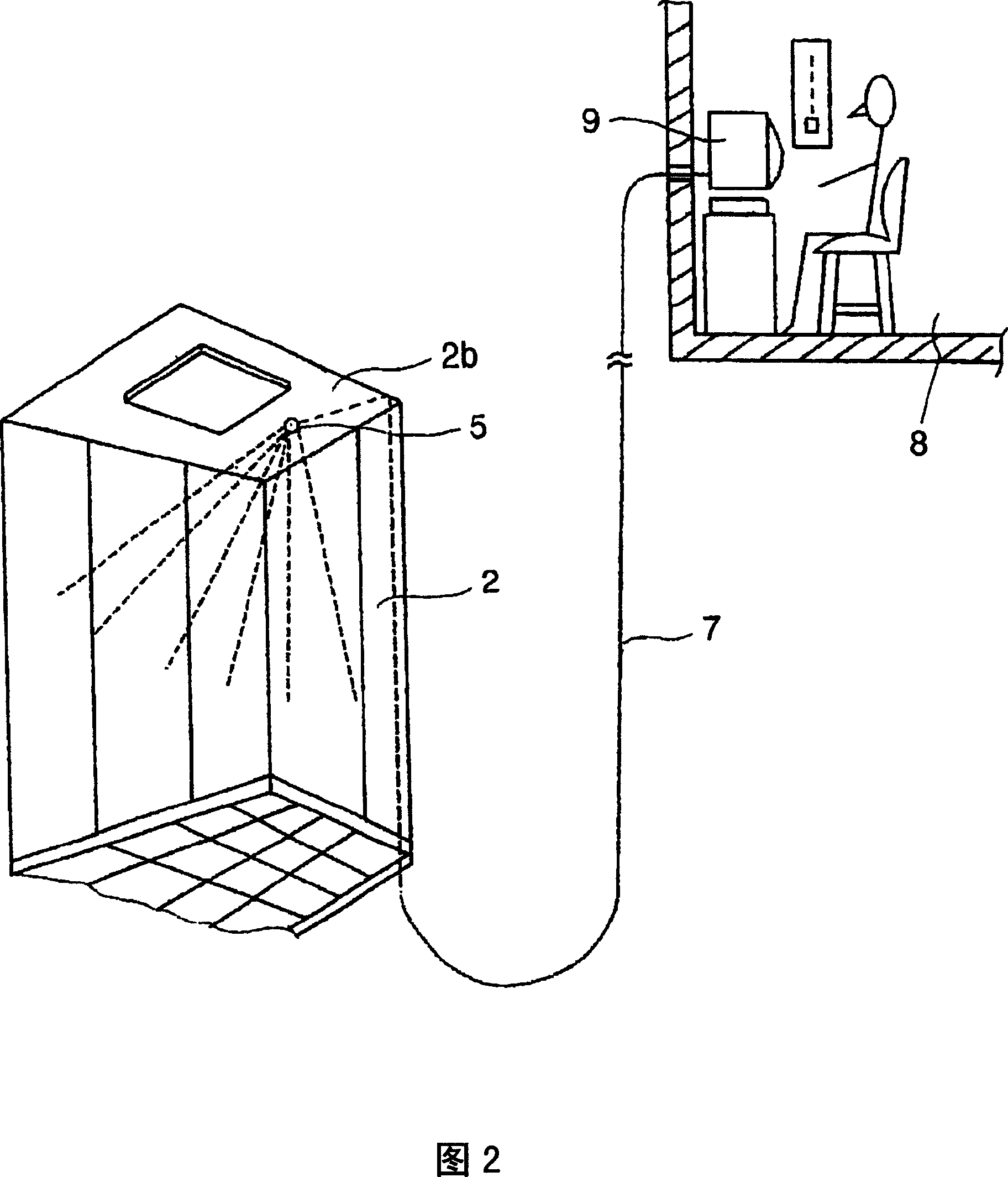
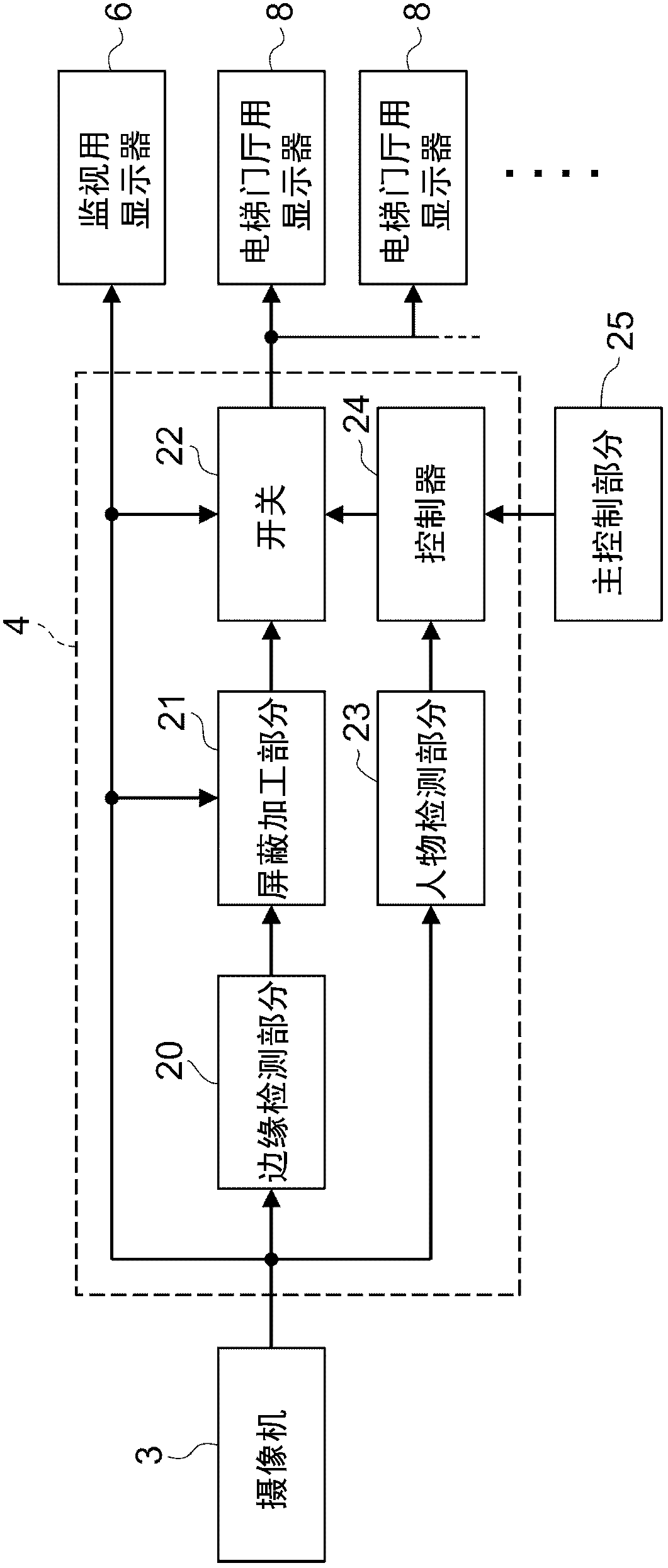
Elevator device
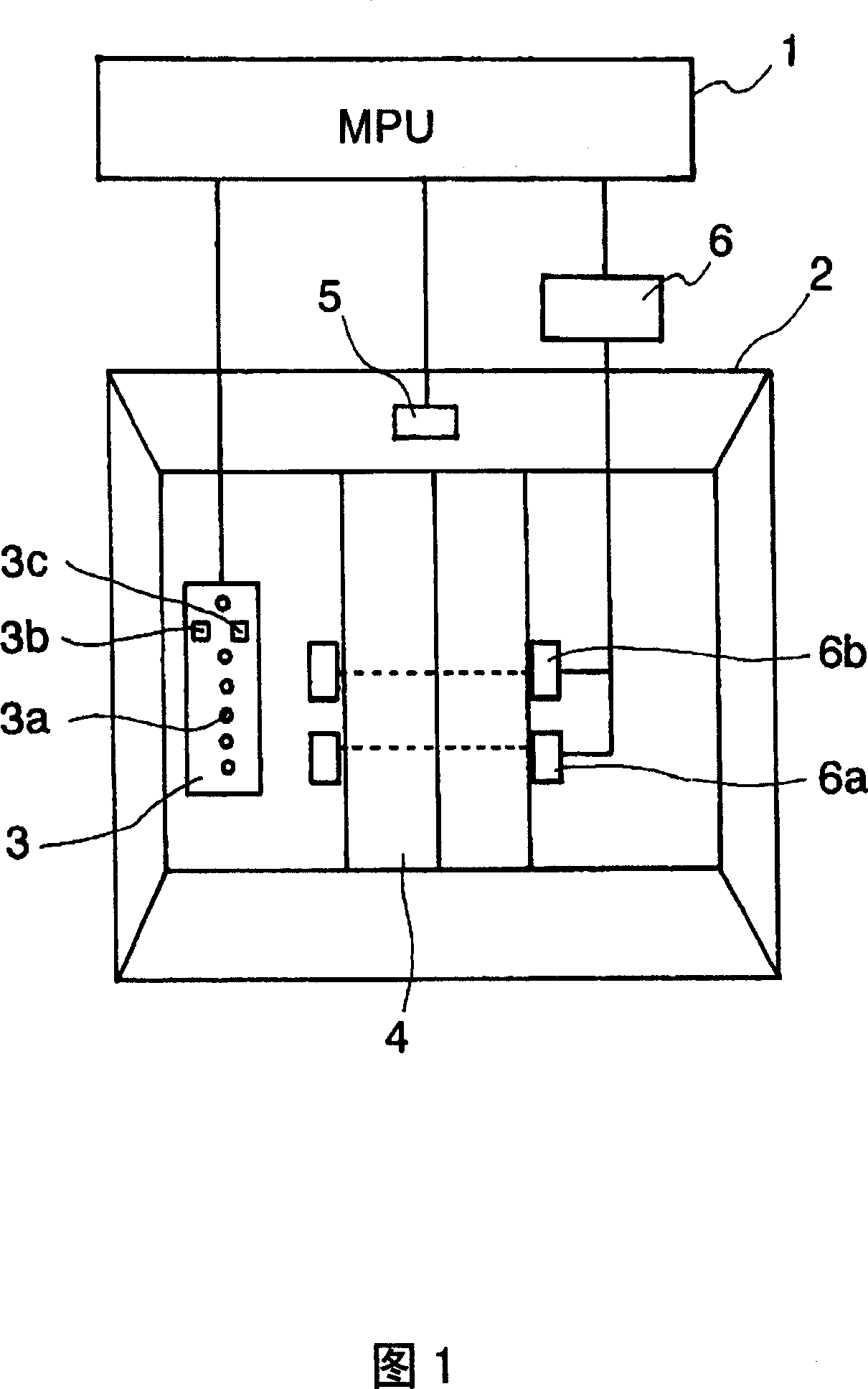
InactiveCN1958424AIncreased sense of securityProtection of privacyElevatorsPrivacy rightsEngineering
Provided is an elevator device by which security function for preventing crimes is ensured, security sense of passengers when taking the elevator alone is improved, and privacy right of passengers can be further protected. When the passenger number in elevator is determined only one by a passenger determining device (6), a driving device is driven by a control device (1) so as to make an antitheft camera head (5) retract to the accommodating component and close the covering component to cover the opening part, and when the passenger number in elevator is determined more than one by the passenger determining device (6), the driving device is driven by a control device (1) to open the covering component so as to make the antitheft camera head (5) extend inwards to the elevator car. Thereby, when the passenger number in elevator is one, the feeling of being monitored possibly occurred of passengers can be eliminated by making the antitheft camera head (5) in an inoperative state. The other aspect, when multiple persons are taking the elevator at the same time, security function for preventing crimes is ensured by making the antitheft camera head (5) operate.
Owner:HITACHI LTD
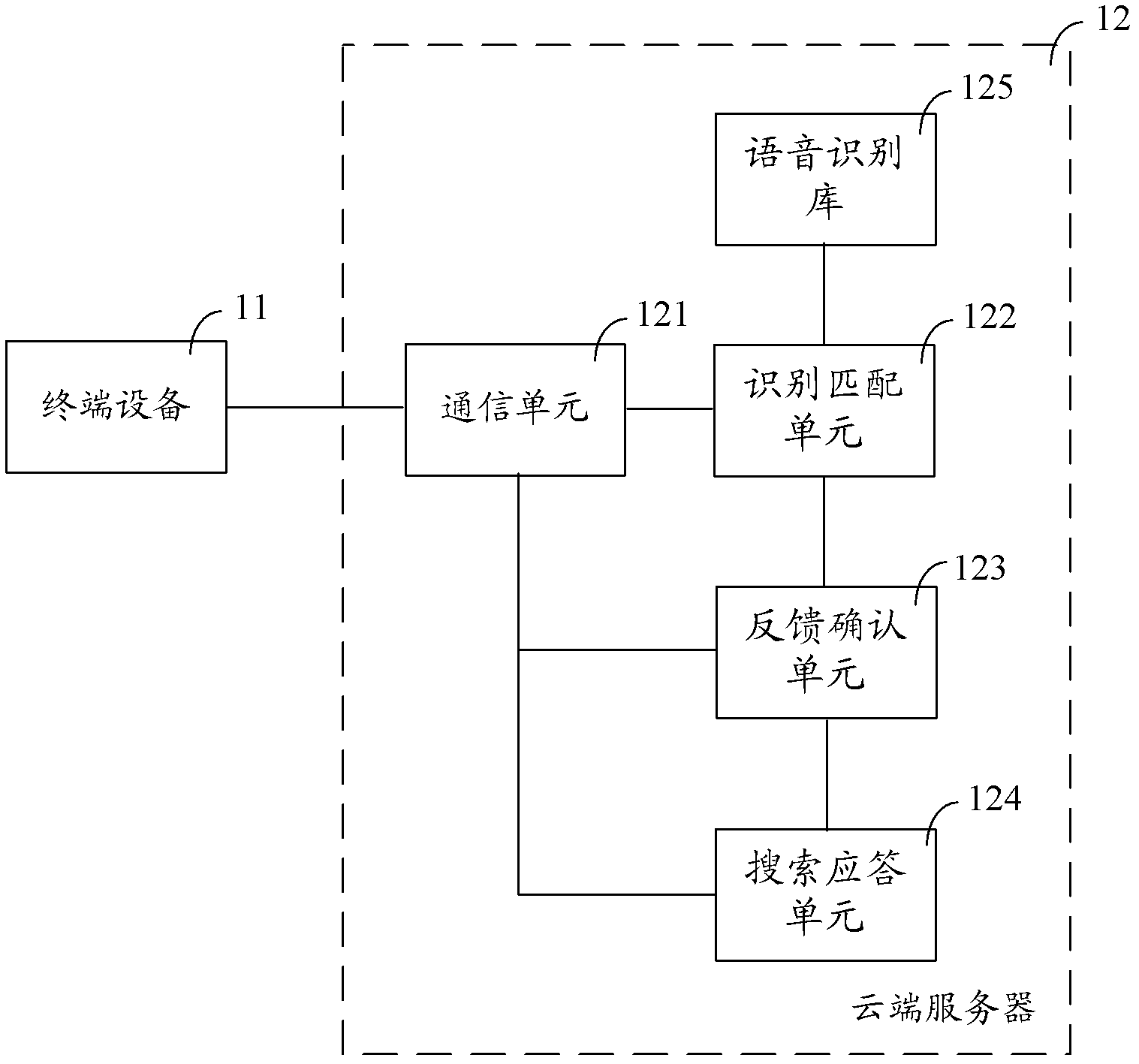
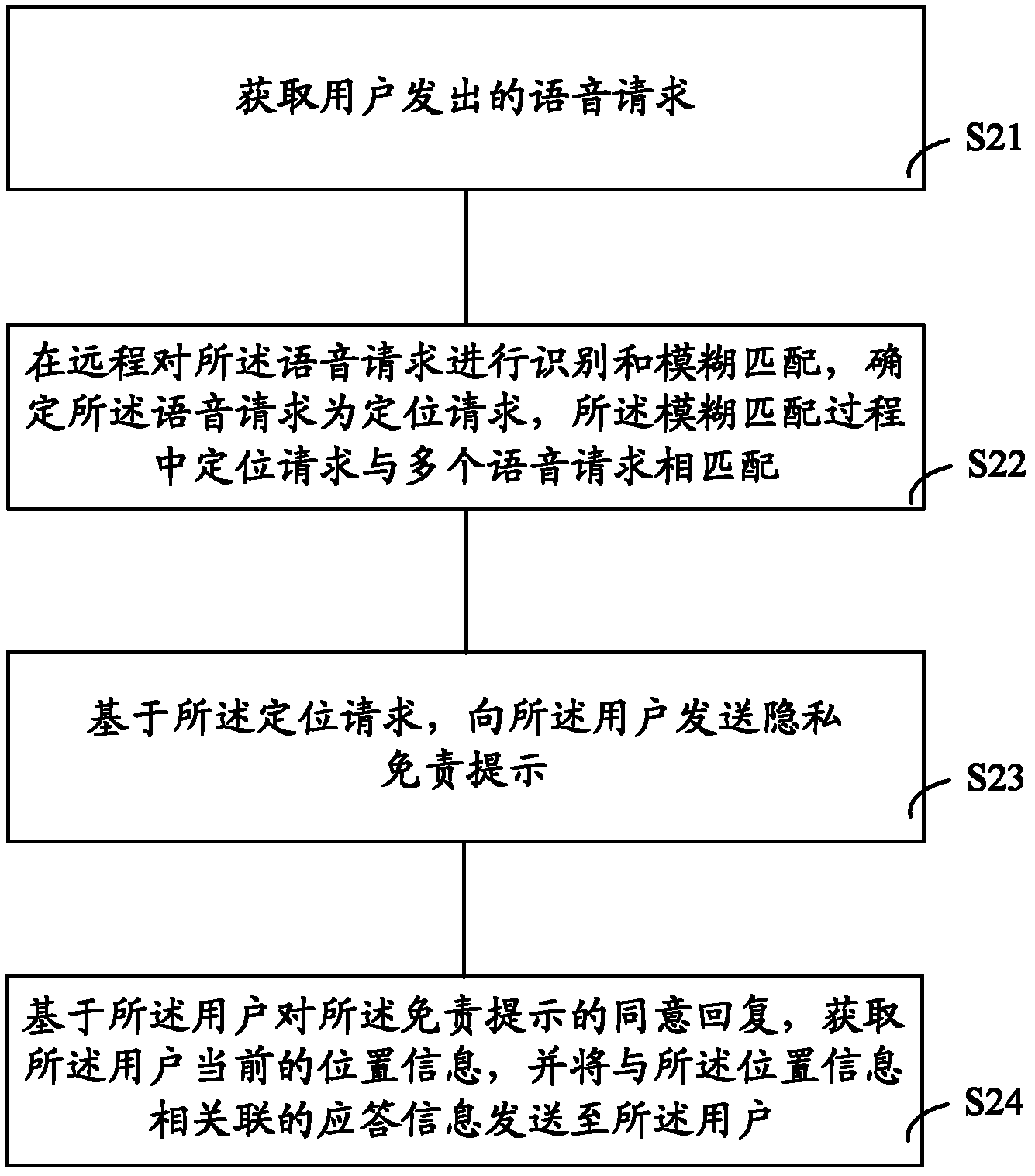
Voice auto-answer cloud server, voice auto-answer system and voice auto-answer method
The invention provides a voice auto-answer cloud server, a voice auto-answer system and a voice auto-answer method. The voice auto-answer cloud server comprises a communication unit, a recognizing and matching unit, a feedback confirming unit and a search and response unit. The communication unit is used for receiving a voice request sent by a user. The recognizing and matching unit conducts recognition and fuzzy matching on the voice request and confirms the voice request to be a locating request, wherein the locating request in the fuzzy matching process matches with a plurality of voice requests. The feedback confirming unit is triggered by the locating request and sends privacy relief prompt to the user. The search and response unit obtains current position information of the user based on an agreed reply of the user to the privacy relief prompt, and sends response information which is relevant to the position information to the user. The voice auto-answer cloud server, the voice auto-answer system and the voice auto-answer method are suitable for various different voice instructions, convenient to use and capable of preventing the privacy right of the user from being violated.
Owner:SHANGHAI PATEO ELECTRONIC EQUIPMENT MANUFACTURING CO LTD
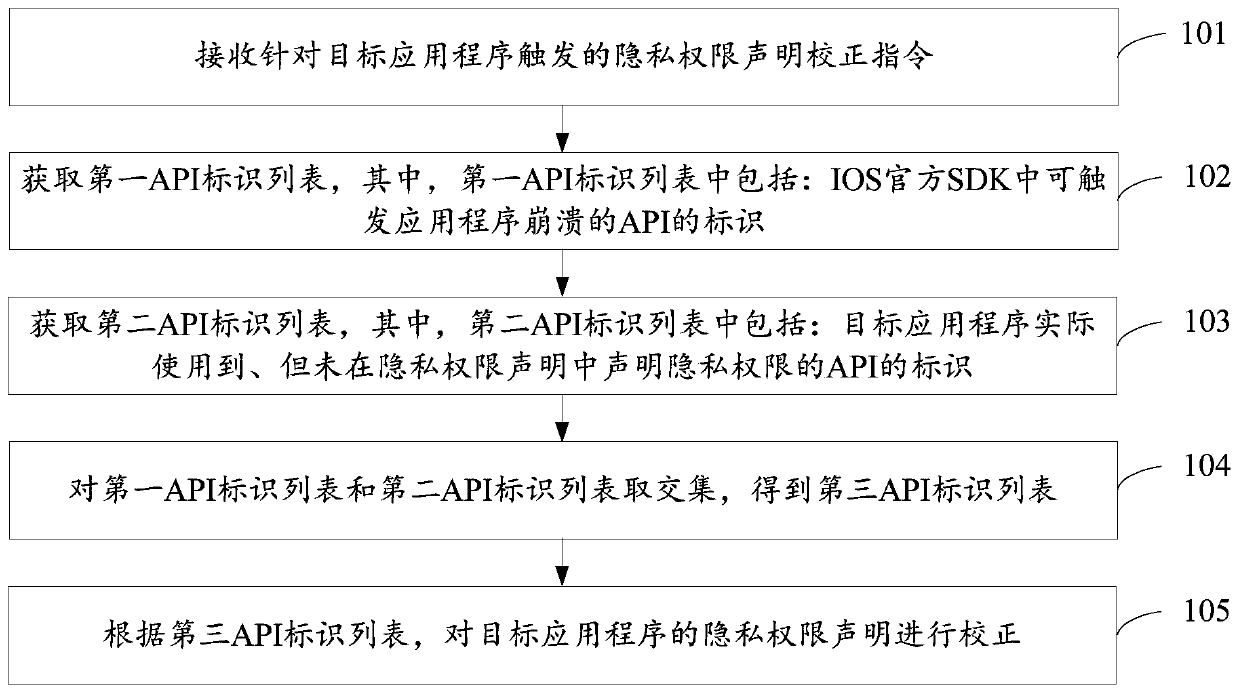
Application privacy authority declaration correction method and device, and electronic equipment
ActiveCN110414215AImprove the approval rateGuaranteed shelf lifeDigital data protectionCrash ratePrivacy rights
The invention discloses an application privacy authority declaration correction method and a device, and electronic equipment. The method comprises the steps of receiving a privacy authority declaration correction instruction; obtaining a first API identifier list, wherein the first API identifier list comprises identifiers of APIs capable of triggering the application program to crash in the IOSofficial SDK; obtaining a second API identifier list, wherein the second API identifier list comprises identifiers of APIs which are actually used by the target application program but do not declarethe privacy permission in the privacy permission declaration; taking an intersection of the first API identifier list and the second API identifier list to obtain a third API identifier list; and correcting the privacy right declaration of the target application program according to the third API identifier list. Visibly, in the embodiment of the invention, a basis can be provided for correcting the privacy authority declaration of the target application program, so that the crash rate of the target application program is reduced, the application program auditing passing rate is improved, andthe development cost is further reduced.
Owner:BEIJING QIYI CENTURY SCI & TECH CO LTD
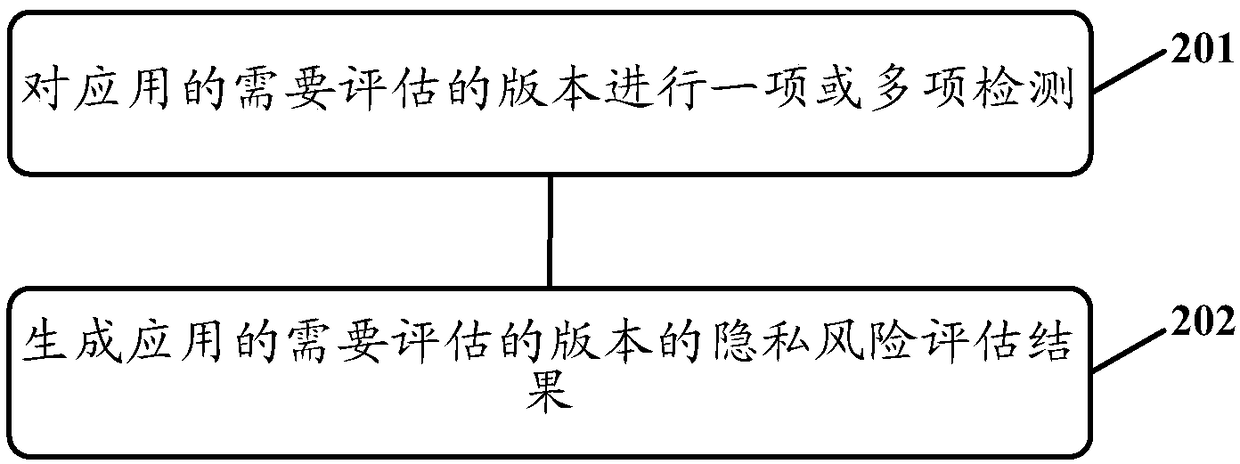
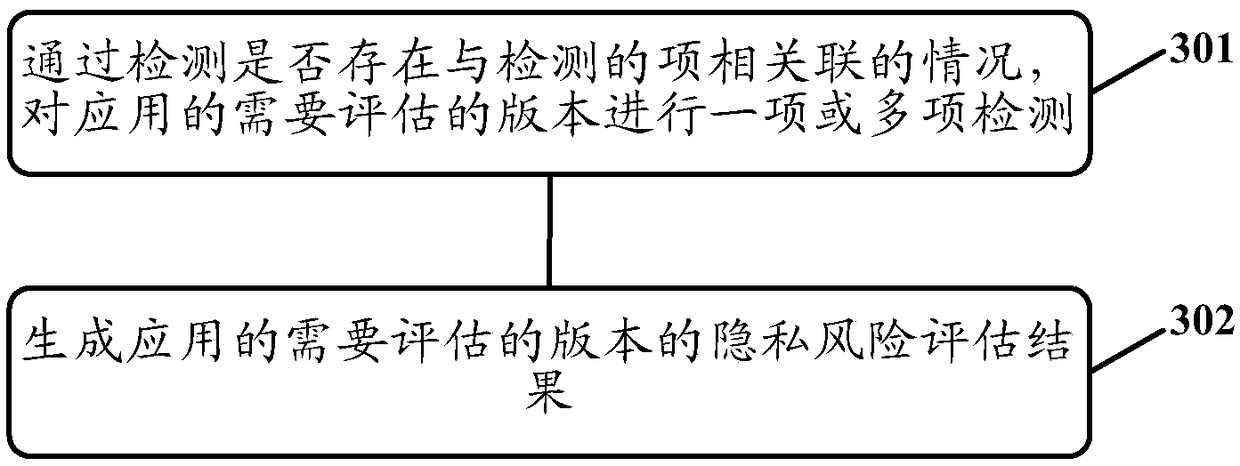
Privacy risk assessment method and apparatus
the emdoiment of the invention provides a Privacy risk assessment method and apparatus. One embodiment of the method includes: Performing one or more of the following checks on the version of the application that needs to be evaluated, obtaining a privacy risk detection result of an applied need-evaluated version: performing consistency of a privacy right requirement situation and a privacy rightapplication situation, legitimacy of a privacy right used by the applied need-evaluated version, and legitimacy of a plug-in use privacy right associated with the applied need-evaluated version; Basedon the privacy risk detection result of the version to be evaluated of the application, generating a privacy risk evaluation result of the version to be evaluated of the application. The invention realizes the detection of multiple privacy risk situations of multiple versions of an application, evaluates the security of the multiple versions of the application in the privacy data of a user, and obtains the privacy risk evaluation results of the multiple versions of the application, so that the security of the multiple versions of the application in the privacy data of a user can be known.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
A method and apparatus for remotely assisted control of a cloud desktop
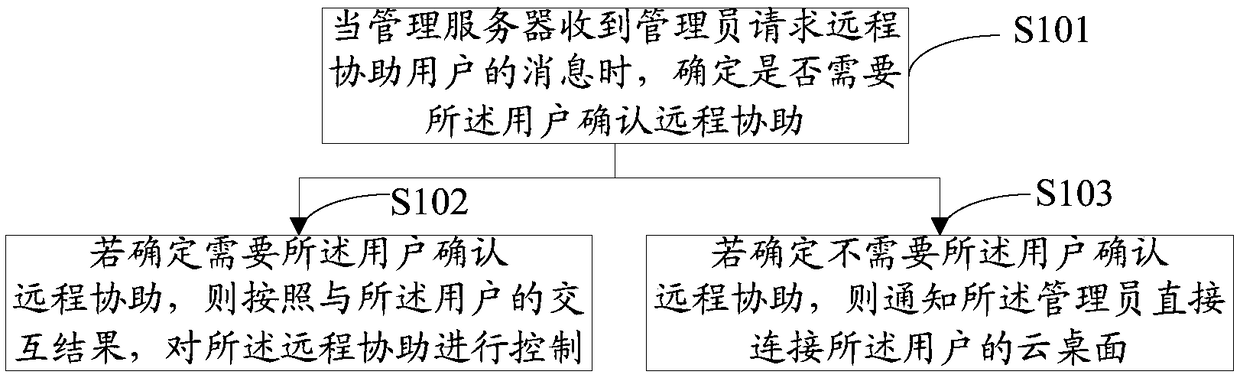
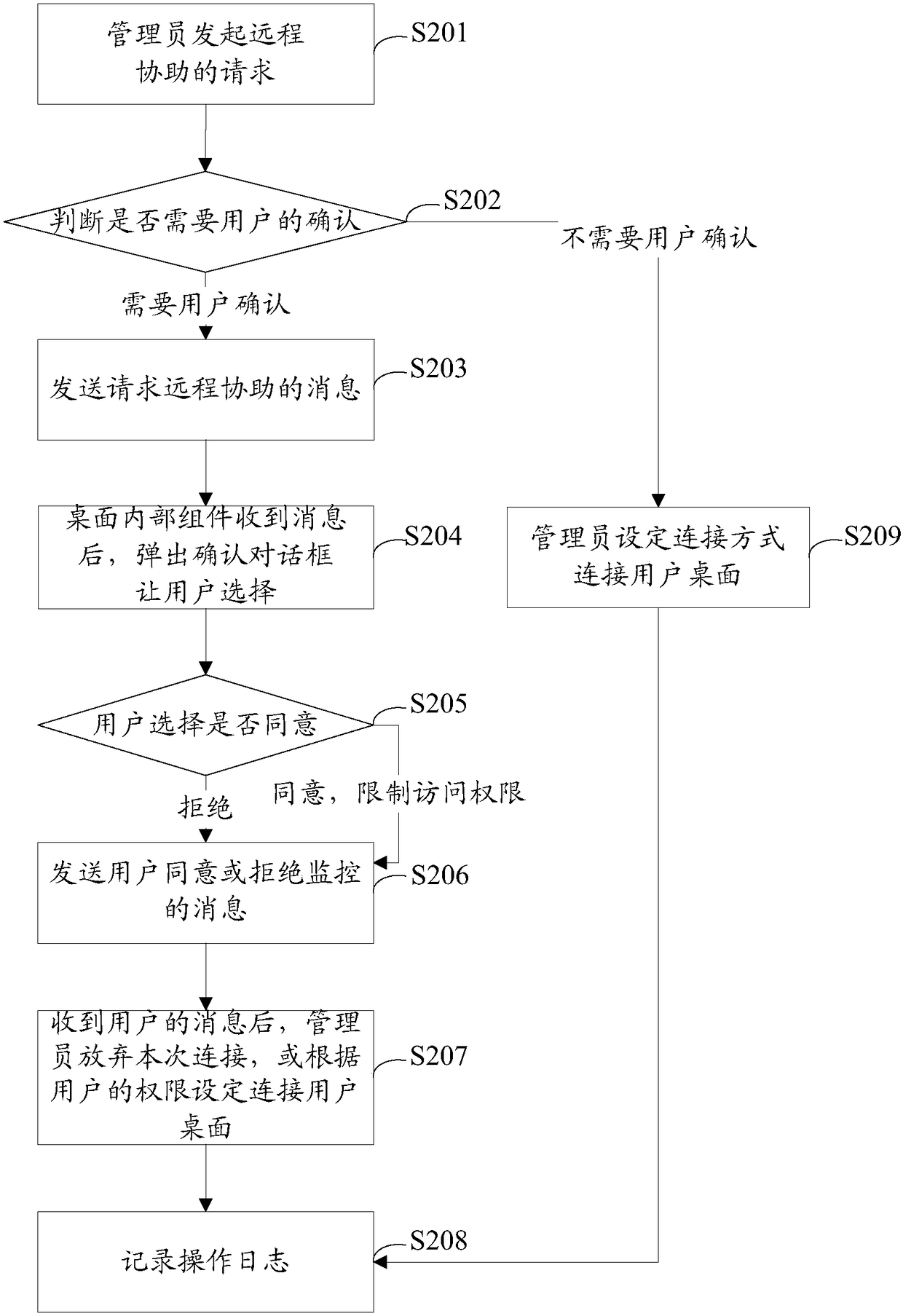
InactiveCN108989073AAvoid infringementInvasion of privacyData switching networksVirtualizationPrivacy rights
The invention discloses a method and a device for remote assistance control of a cloud desktop, which relate to the technical field of virtualization. The method comprises the following steps: when the management server receives a message requesting the remote assistance user, the management server determines whether the remote assistance is required. if the management server determines the remoteassistance confirmed by the user is required, controlling the remote assistance according to an interaction result with the user; If the management server determines the the user confirmation remoteassistance is not required, the administrator is notified to directly connect to the cloud desktop of the user. The embodiment of the invention limits the access authority of the administrator by setting the remote assistance mode, controls the operation authority of the administrator, is flexible and matchable, and supports interaction, so the the administrator can have sufficient authority to provide remote assistance, and can prevent the administrator from abusing the authority to encroach on the privacy right of the user.
Owner:ZTE CORP
Safe privacy control method for mobile phone during non-calling period
InactiveCN103441998AAvoid illegal manipulationProtect personal privacySubstation equipmentTransmissionPrivacy rightsEngineering
The invention relates to a safe privacy control method for a mobile phone during a non-calling period. The safe privacy control method is characterized in that a physical master switch for controlling a wifi circuit, a bluetooth circuit and a data link is arranged on a mainboard of the mobile phone, and meanwhile physical switches for respectively controlling the wifi circuit, the bluetooth circuit and the data link are arranged; a physical switch for controlling a microphone circuit of the mobile phone is arranged on the mainboard of the mobile phone; real-time detection is carried out on the physical switches for controlling the wifi circuit, the bluetooth circuit and the data link and carried out on the physical switch for controlling a microphone circuit of the mobile phone through a processor on the mainboard of the mobile phone. The safe privacy control method has the advantages that various communication networks or mobile phone microphones can be disconnected through the physical switches, a physical link effectively prevents mobile phone hardware from being illegally operated by software, and the personal privacy right is protected to a large extent.
Owner:李少杰
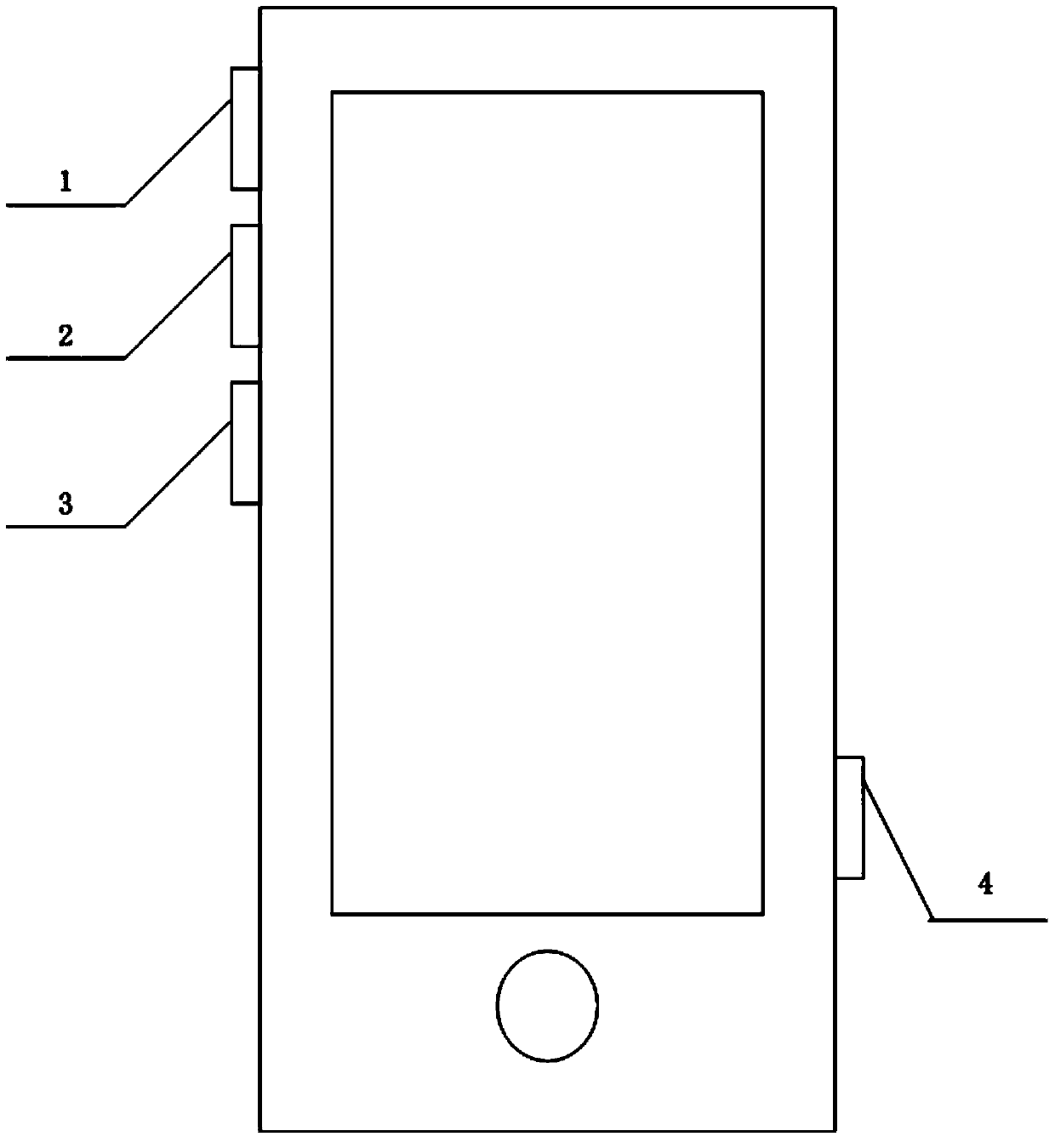
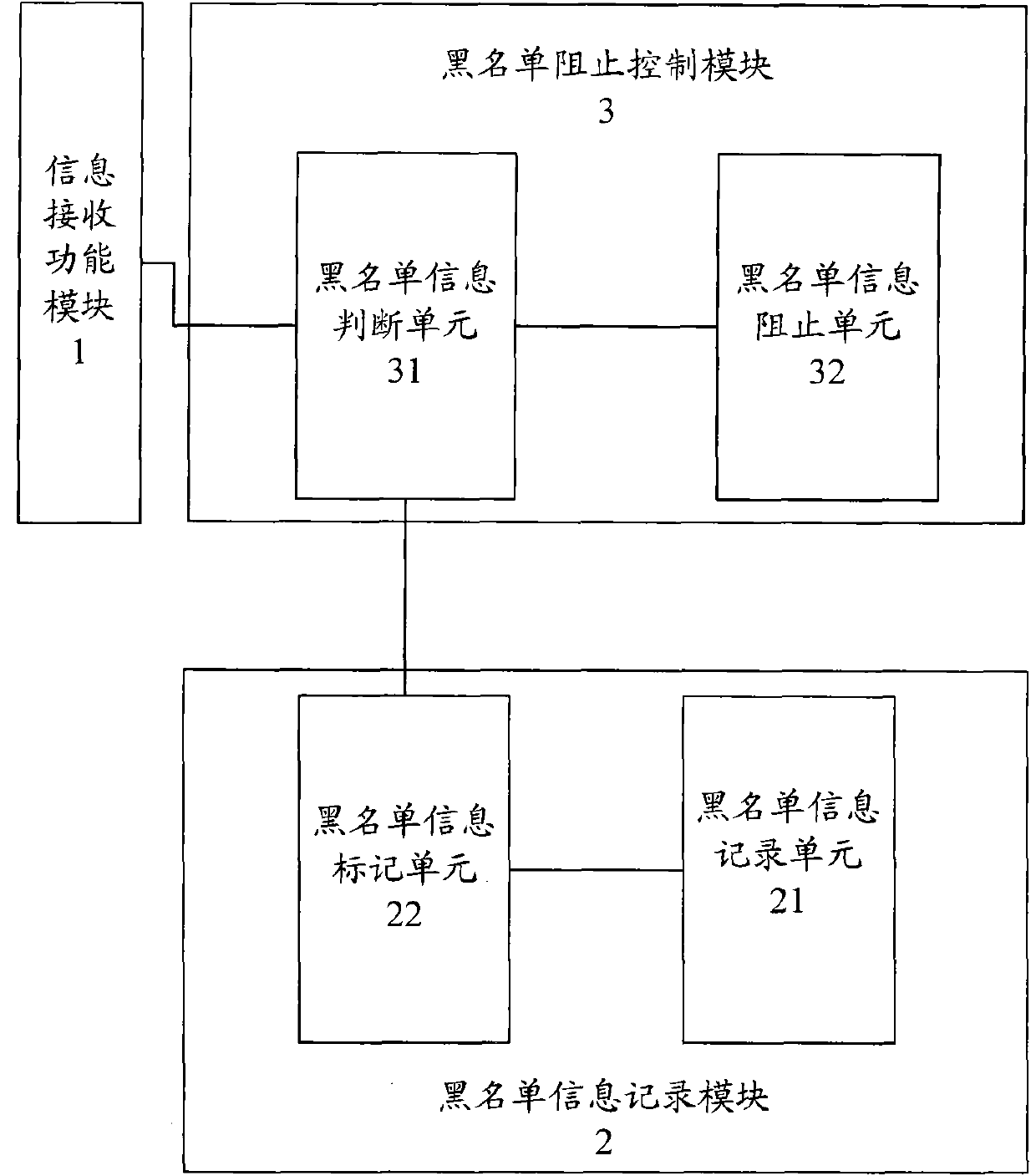
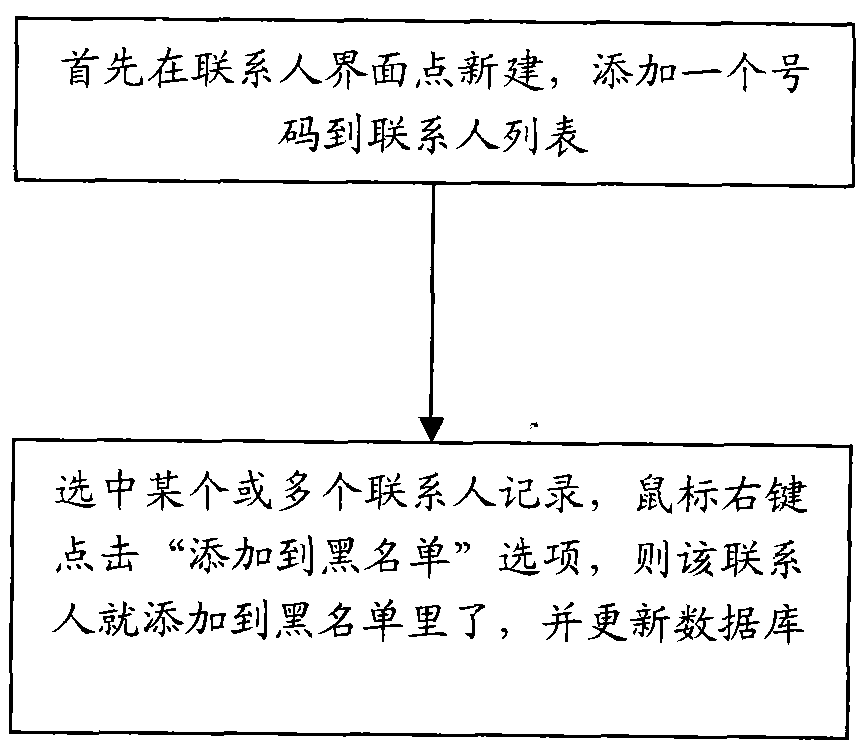
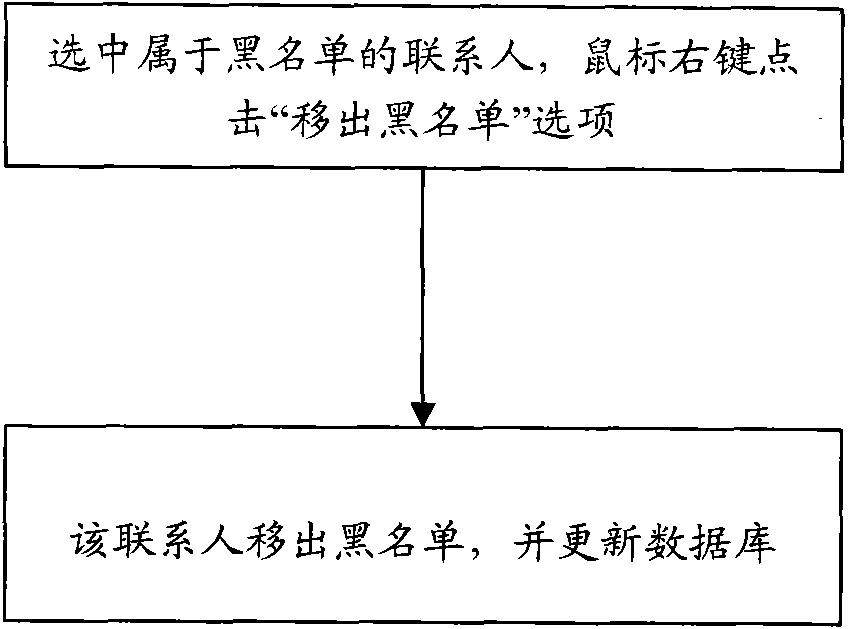
Device and method for stopping harassment short messages and harassment phone calls in wireless broadband client system
InactiveCN101771753ASimple structureEasy to useSubstation equipmentMessaging/mailboxes/announcementsPrivacy rightsBroadband
The invention relates to a device for realizing functions of stopping spam messages and harassment phone calls in a wireless broadband client system. The device comprises an information receiving functional module, a blacklist information logging module and a blacklist stop control module, wherein the blacklist stop control module is connected with the blacklist information logging module and the information receiving functional model respectively. The invention also relates to a method for realizing the functions of stopping the spam messages and the harassment phone calls in the wireless broadband client system by utilizing the device, which comprises the addition operation of blacklist information, the removal operation of the blacklist information and the stop operation of information receiving. The device and the method for realizing the functions of stopping the spam messages and the harassment phone calls in the wireless broadband client system can effectively stop the spam messages and harassment phone calls which users do not need, has the advantages of simple and practical structure, quick and convenient use, stable and reliable operating performance and extensive applicable scopes, and effectively ensures the privacy right and information safety of people.
Owner:SHANGHAI GONGJIN COMM TECH
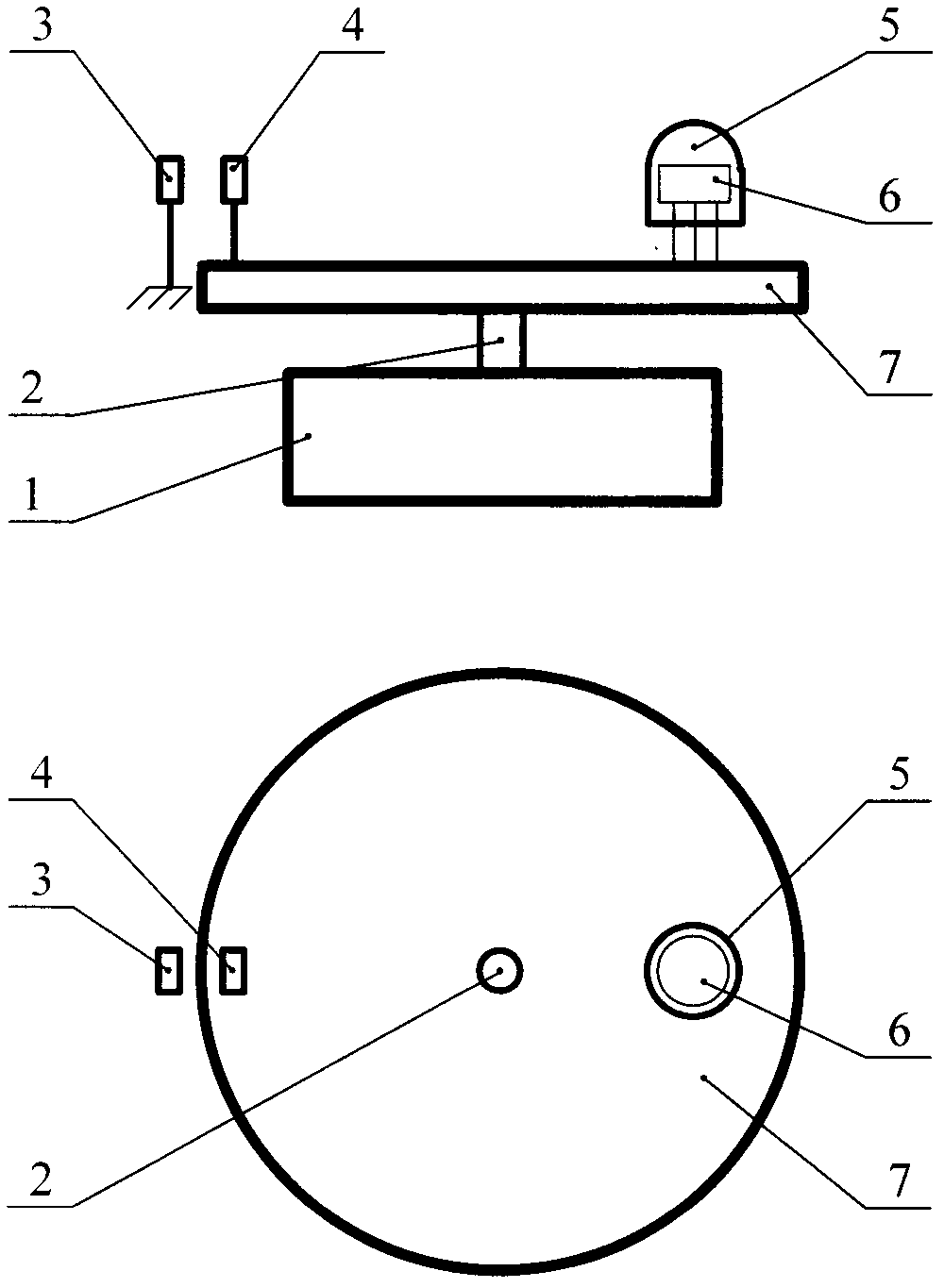
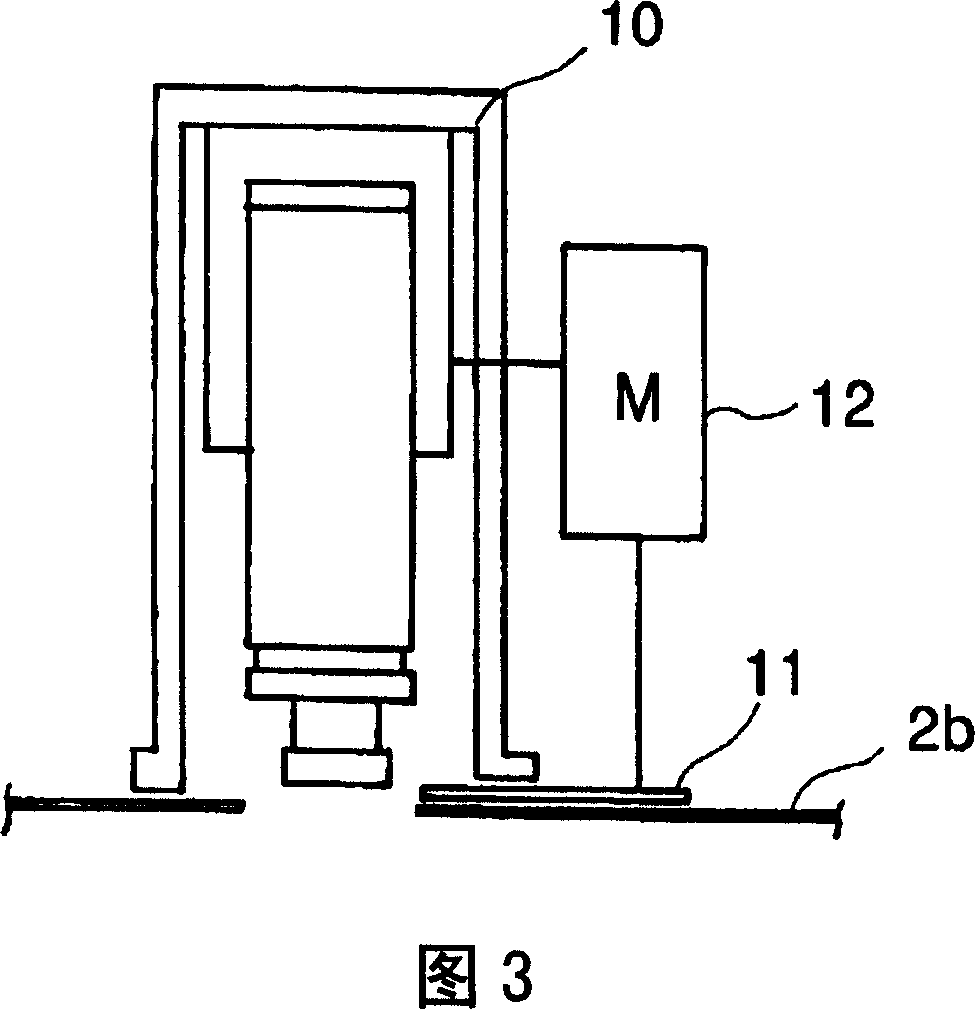
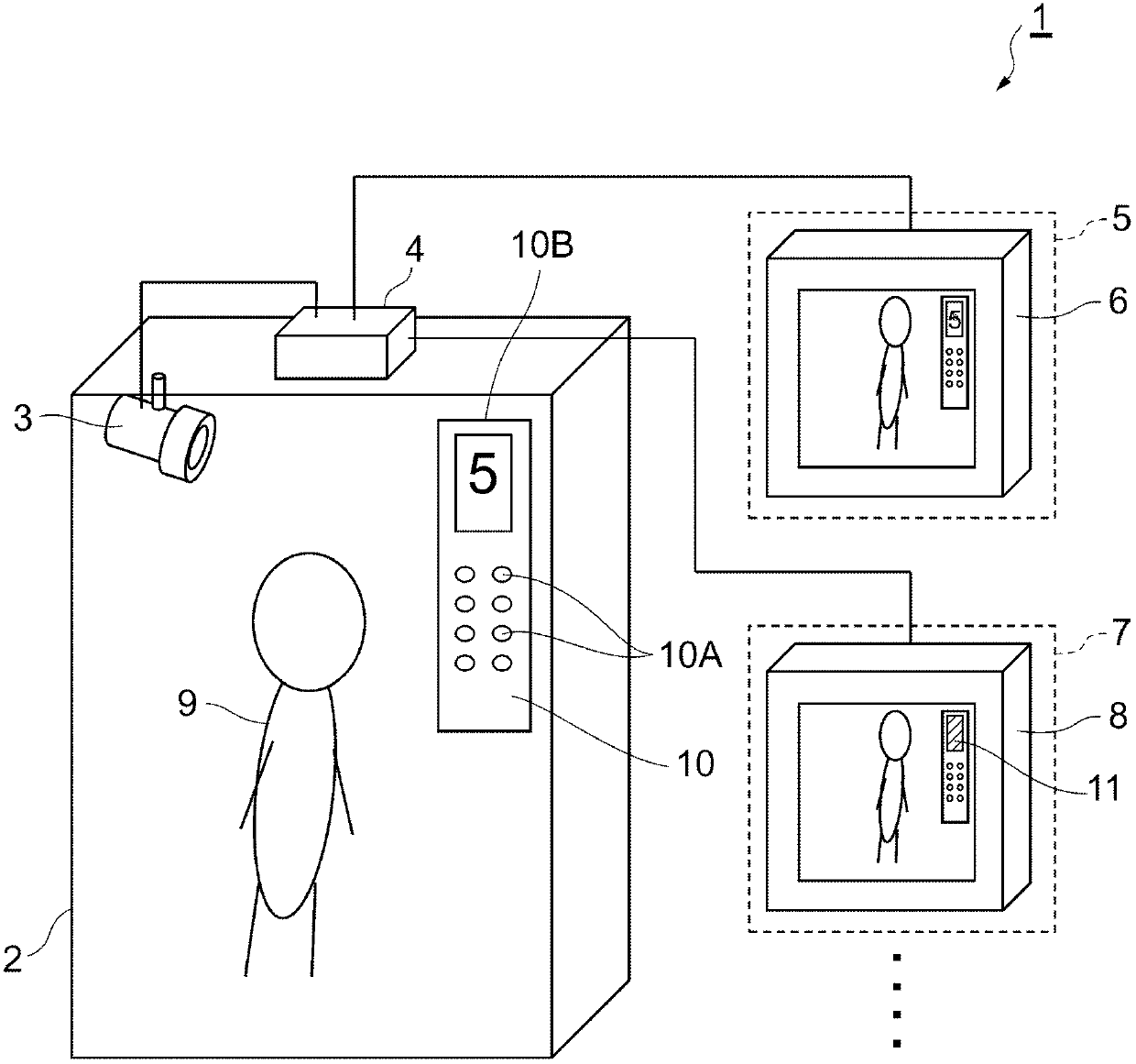
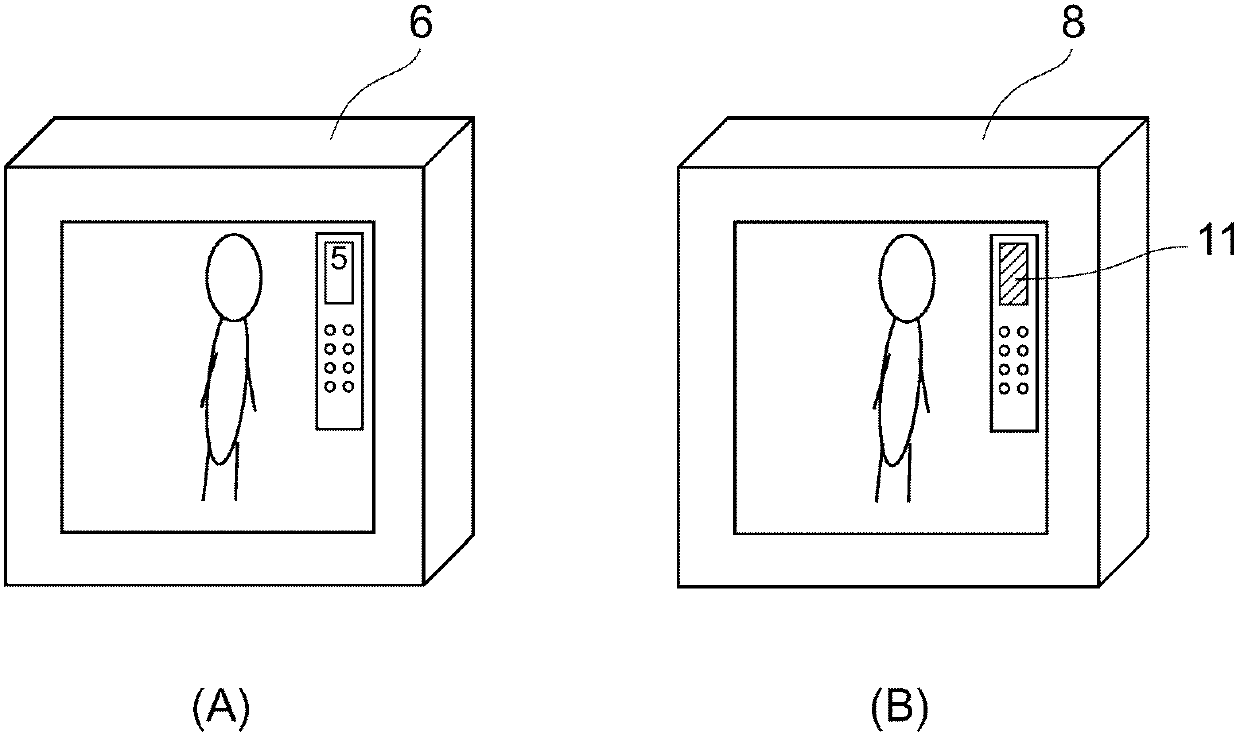
Prevention device and prevention method
The present invention provides a prevention device and a prevention method, which can protect the privacy rights of passengers in an elevator while providing a prevention service conveniently. A camera is arranged in the lift car of the elevator to shoot the interior of the lift car of the elevator, a specific image editing processing is implemented on an image signal outputted by the camera according to demands, and the images of the image signal, which is implemented the image editing processing according to the demands, are displayed in a display in a hallway of the elevator. On the other hand, a floor display part used for displaying the floor, at which the lift car of the elevator is located, is arranged in the lift car of the elevator, and according to the demands, the image signal is implemented the image editing processing to shield the floor number displayed in the floor display part and contained in the images of the image signal.
Owner:HITACHI LTD
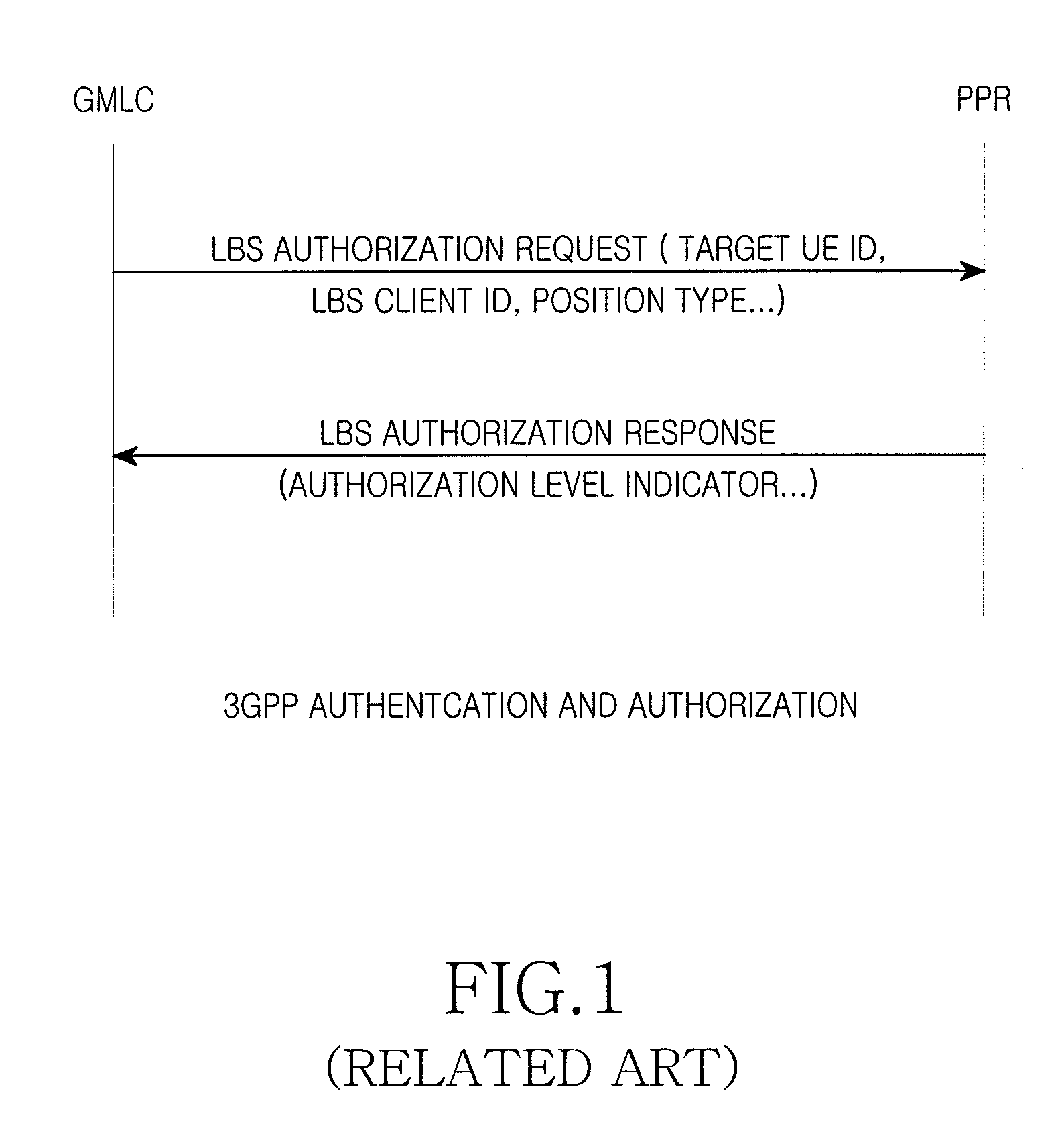
Method and device for authentication and authorization checking on LBS in Wimax network
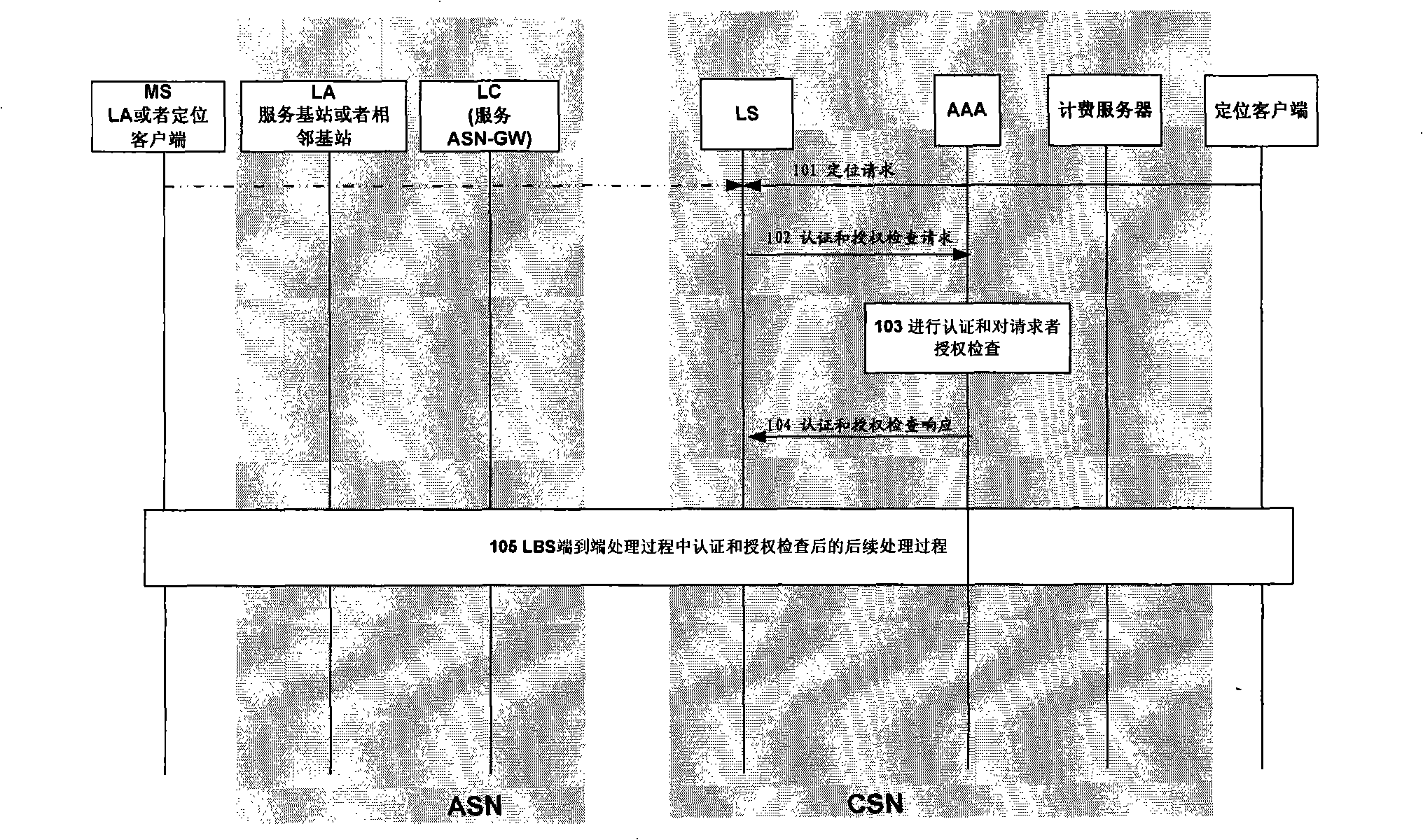
InactiveUS8442551B2Raise security concernsProtection of privacyUnauthorised/fraudulent call preventionEavesdropping prevention circuitsPrivacy rightsClient-side
A device for performing authentication and authorization checking on Location-Based Service (LBS) in a WiMAX network is provided. This device strengthens security for LBS in a WiMAX network, and protects privacy right of subscribers to LBS. The device includes a Location Assessment module (LA) for performing the location assessment, a Location Coordination and control module (LC) for controlling LBS assessment and calculation of a location of a mobile terminal. The device also includes an Authentication / Authorization / Accounting module (AAA) that includes a memory storing authentication and authorization information. The AAA also includes an authentication processing module for authenticating an LBS, and an authorization checking processing module for checking whether an LBS client and a Mobile Station (MS) requesting services from the LBS are authorized to request the location of a target MS.
Owner:SAMSUNG ELECTRONICS CO LTD
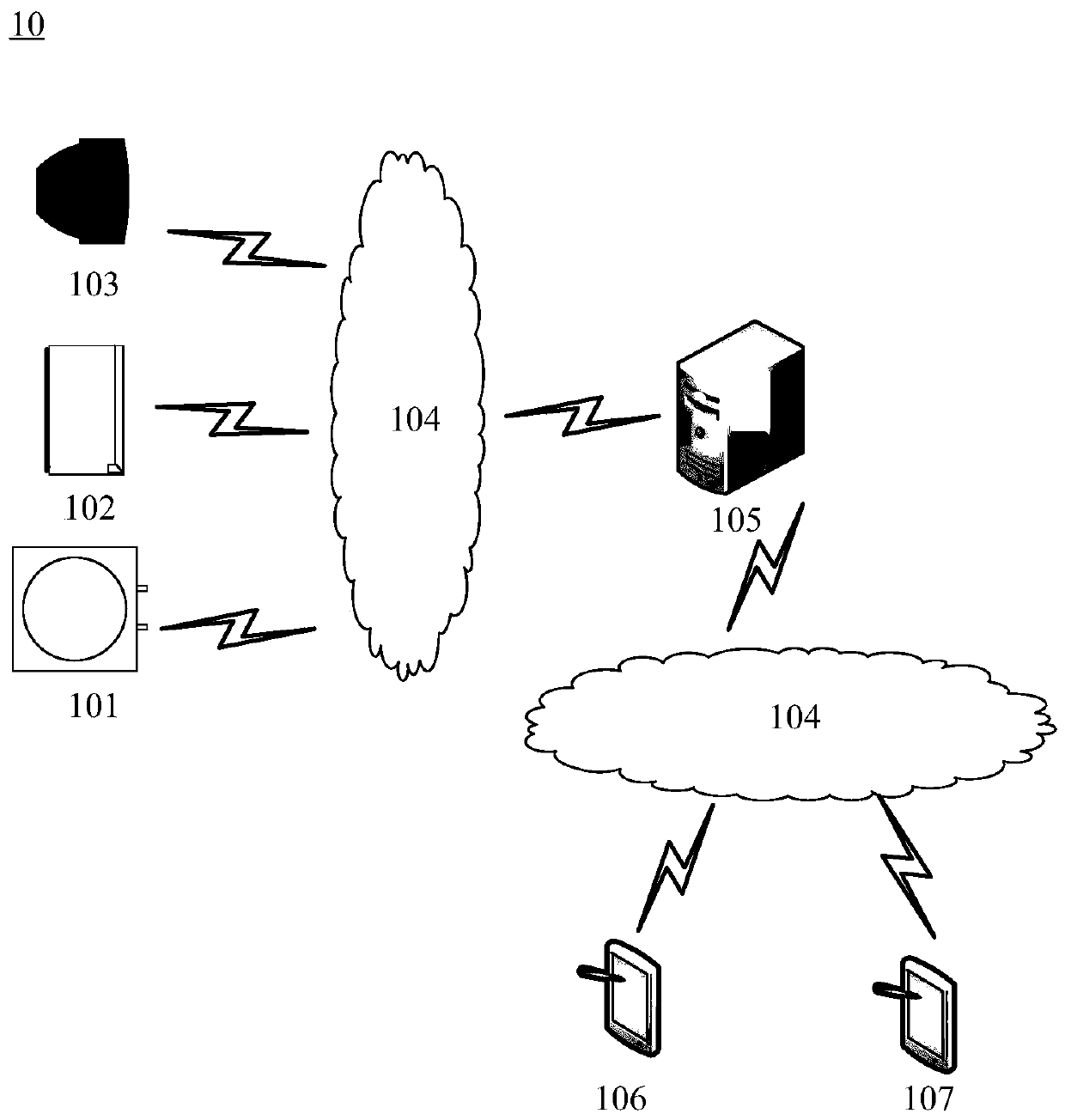
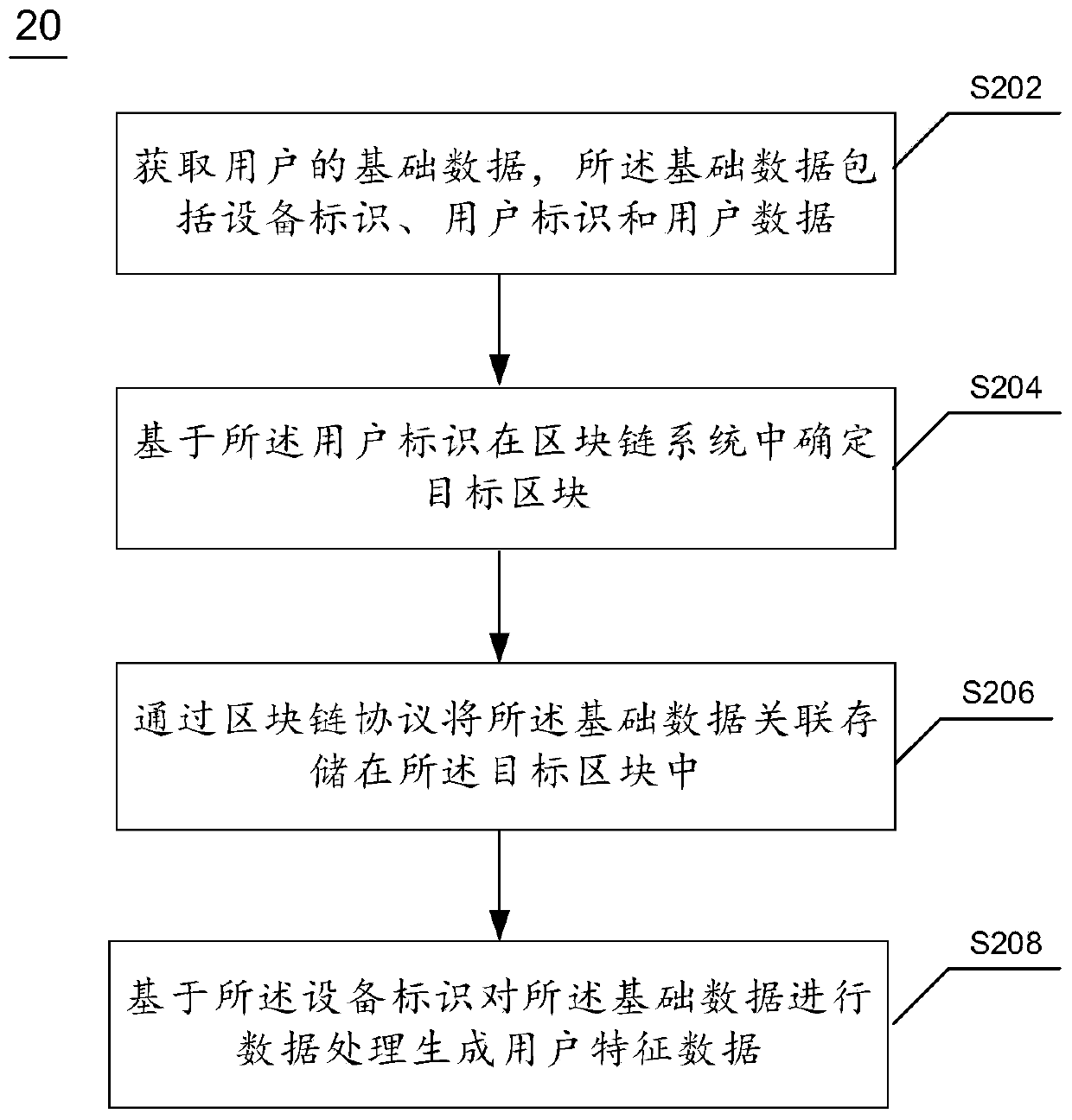
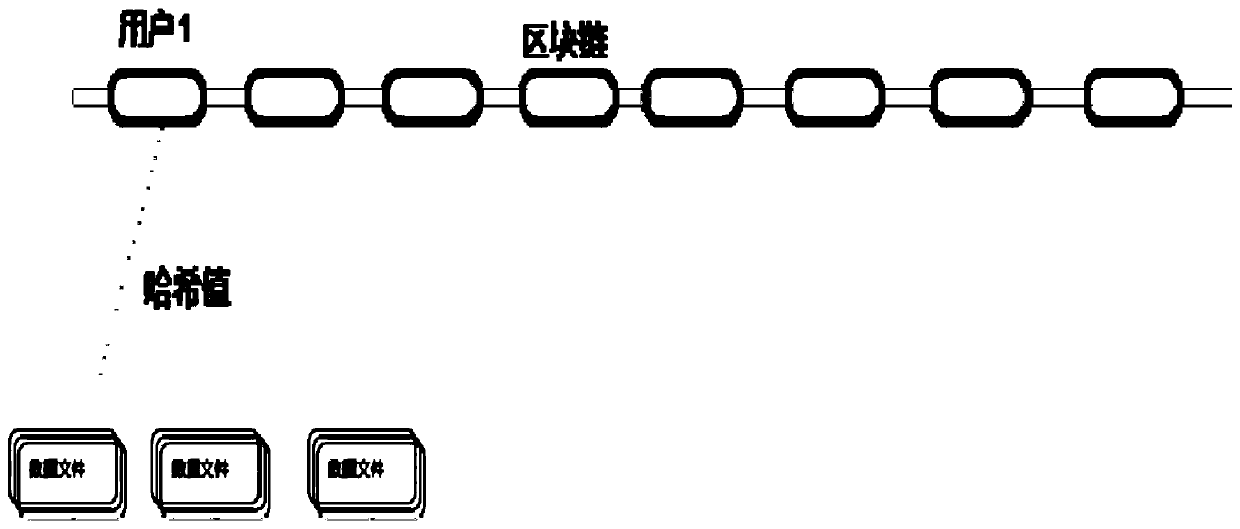
User feature data generation method, equipment and system based on block chain
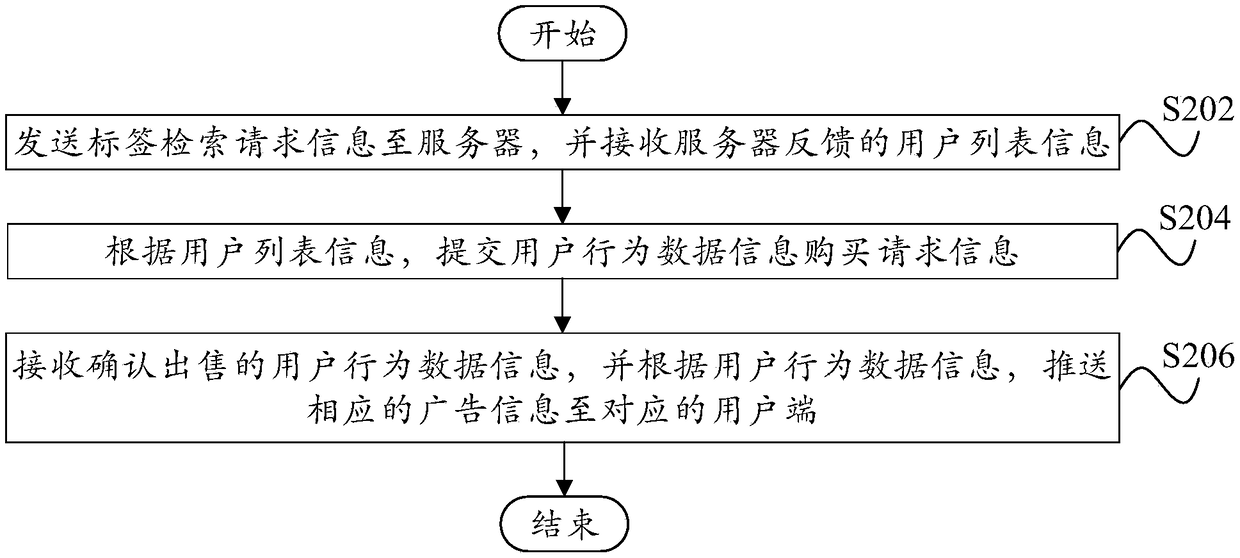
InactiveCN110519342AEffective transferEffective circulationDigital data protectionDigital data authenticationInformation processingCollection system
The invention relates to a user characteristic data generation method and system based on a block chain, intelligent equipment, a cloud server, a merchant terminal and a computer readable medium. Themethod relates to the field of computer information processing, and comprises the steps of obtaining basic data of a user, the basic data comprising a equipment identifier, a user identifier and userdata; determining a target block in a block chain system based on the user identifier; associatively storing the basic data in the target block through a block chain protocol; and performing data processing on the basic data based on the equipment identifier to generate user feature data. The invention relates to a blockchain-based user feature data generation method and system, intelligent equipment, a cloud server, a merchant terminal and a computer readable medium. A safe collection system of daily user data is established, the privacy right and the proprietary right of the user data are protected through a block chain technology, and effective transfer and circulation of the user data can be realized.
Owner:上海域乎信息技术有限公司
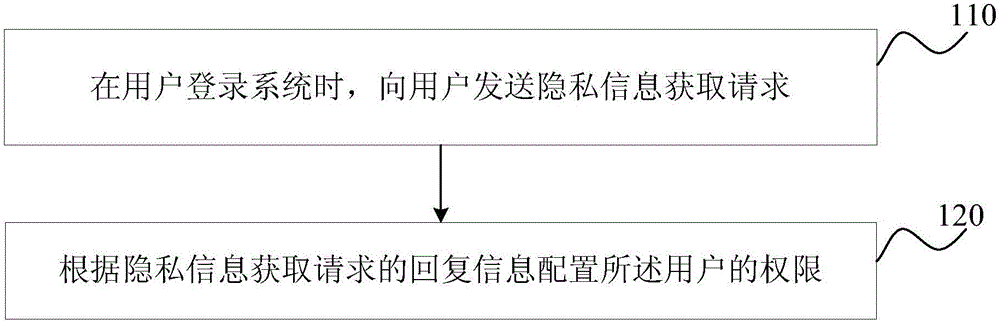
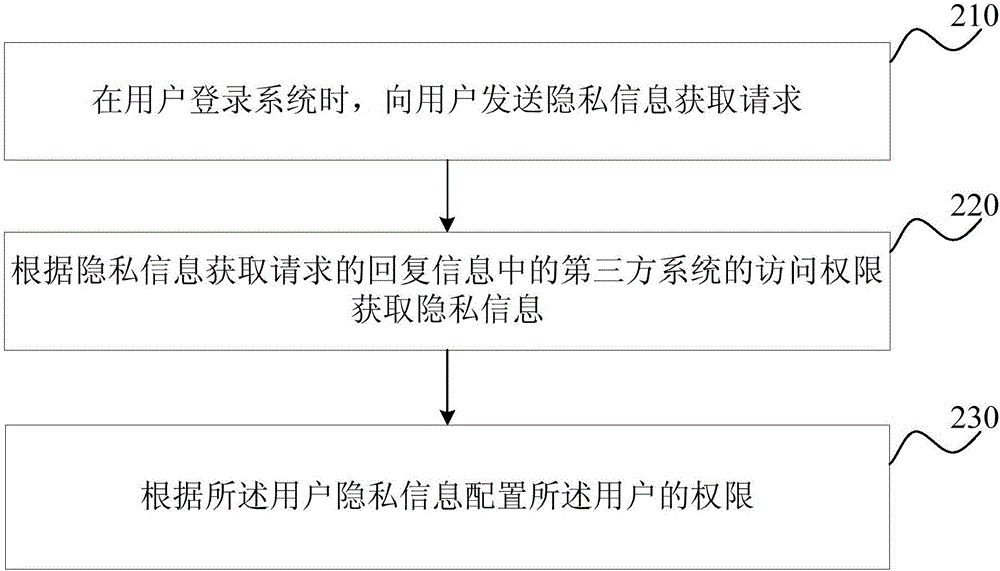
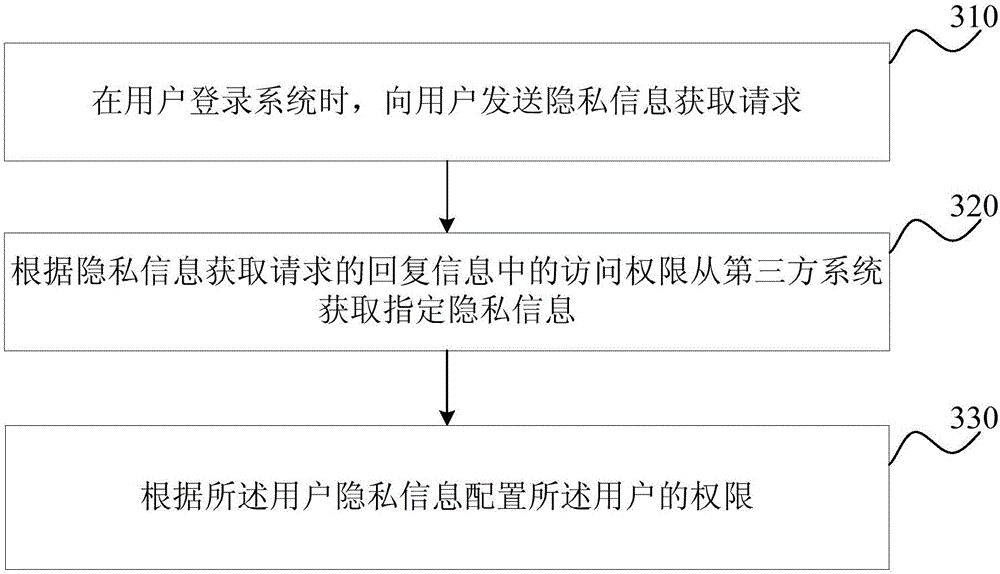
Permission configuration method and device
The embodiment of the invention discloses a permission configuration method and device. The permission configuration method comprises the steps that when a user logs in a system, privacy information is sent to the user to obtain a request; reply information of the request is obtained according to the privacy information to configure a permission of the user; before the privacy information of the user is obtained, the user makes a choice for permitting a system to collect the privacy information of the user or not, and the permission of the user is configured according to the privacy information permitted by the user. While the corresponding operation permission is provided for the user, the privacy right of the user can be protected against invasion, and the privacy of the user can be also prevented from being leaked.
Owner:GREE ELECTRIC APPLIANCES INC
Method of and system for conducting mobile video/audio surveillance in compliance with privacy rights
A video / audio recording device is mounted on a mobile support for recording surveillance information. The recording device is movable relative to the mobile support to adjustably position the recording device to face the target along a line-of-sight during recording. A database stores public map spaces, private map spaces, and warrant spaces that exist in a geographic area to be surveilled. A programmed controller accesses the database, determines whether the target is recordable from a public map space along the line-of-sight between the recording device and the target and / or whether the target is covered by a warrant space, and controls the recording device to record the surveillance information upon a successful determination that the target is so recordable or so covered.
Owner:MOTOROLA SOLUTIONS INC
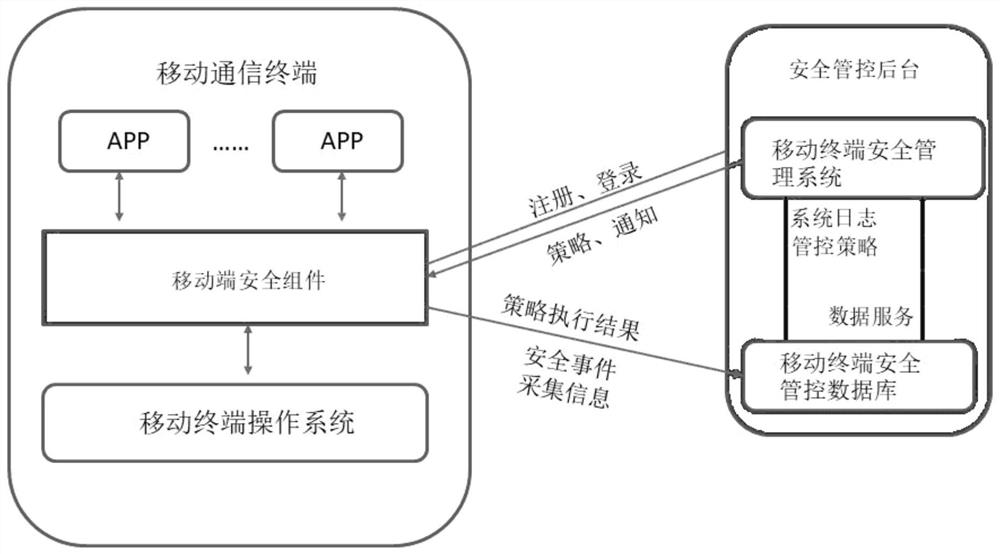
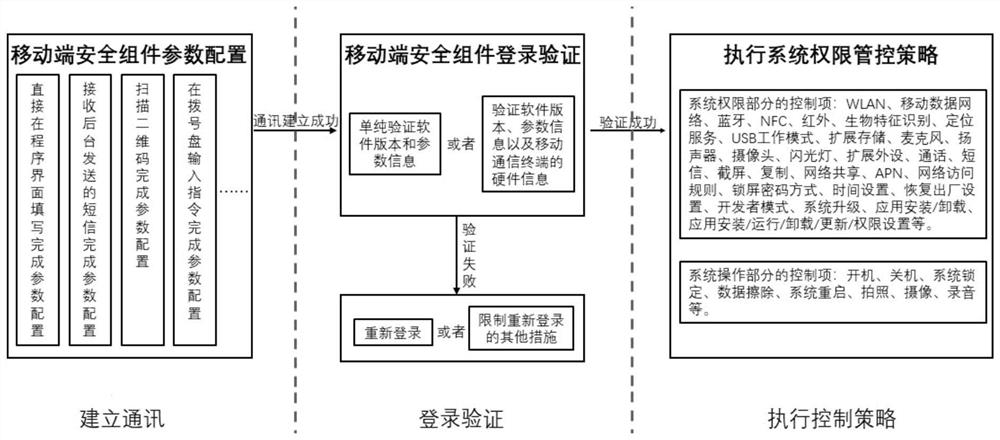
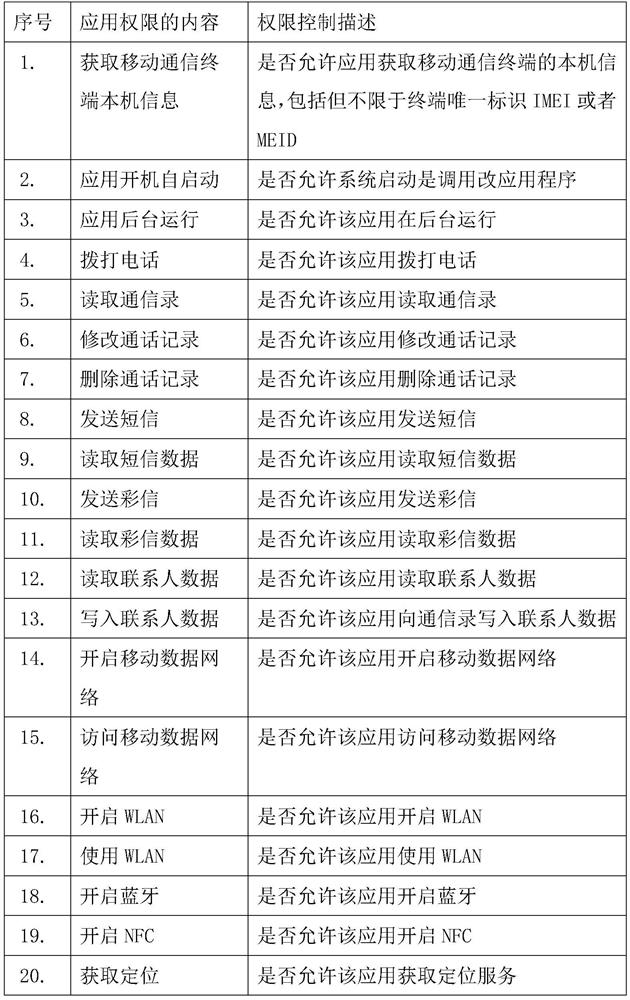
Mobile communication terminal system permission background management and control method
PendingCN113473474AImprove securityProtection of personal privacy rightsDigital data authenticationSecurity arrangementEnd systemMobile end
The invention provides a mobile communication terminal system permission background management and control method, which comprises the following steps that: a mobile terminal security component obtains the highest permission of a mobile communication device end system, receives an instruction sent by a background server end program and executes the instruction so as to control the opening or closing of the system permission of the mobile communication device end. And the mobile terminal program cannot be deleted or changed by a terminal user. The controlled application program object can be global, can also be one or more specified application program objects, and can also be used for implementing a control strategy according to a specific condition. According to the method, the safety of the mobile application system for the working purpose can be effectively improved, meanwhile, the personal privacy right of the user is effectively protected, and the user experience is improved.
Owner:上海商甲信息科技有限公司
Mobile terminal and method for optimizing its privacy rights
ActiveCN104462961BReduce the chance of leaksImprove experienceDigital data protectionPlatform integrity maintainanceUser inputPrivacy rights
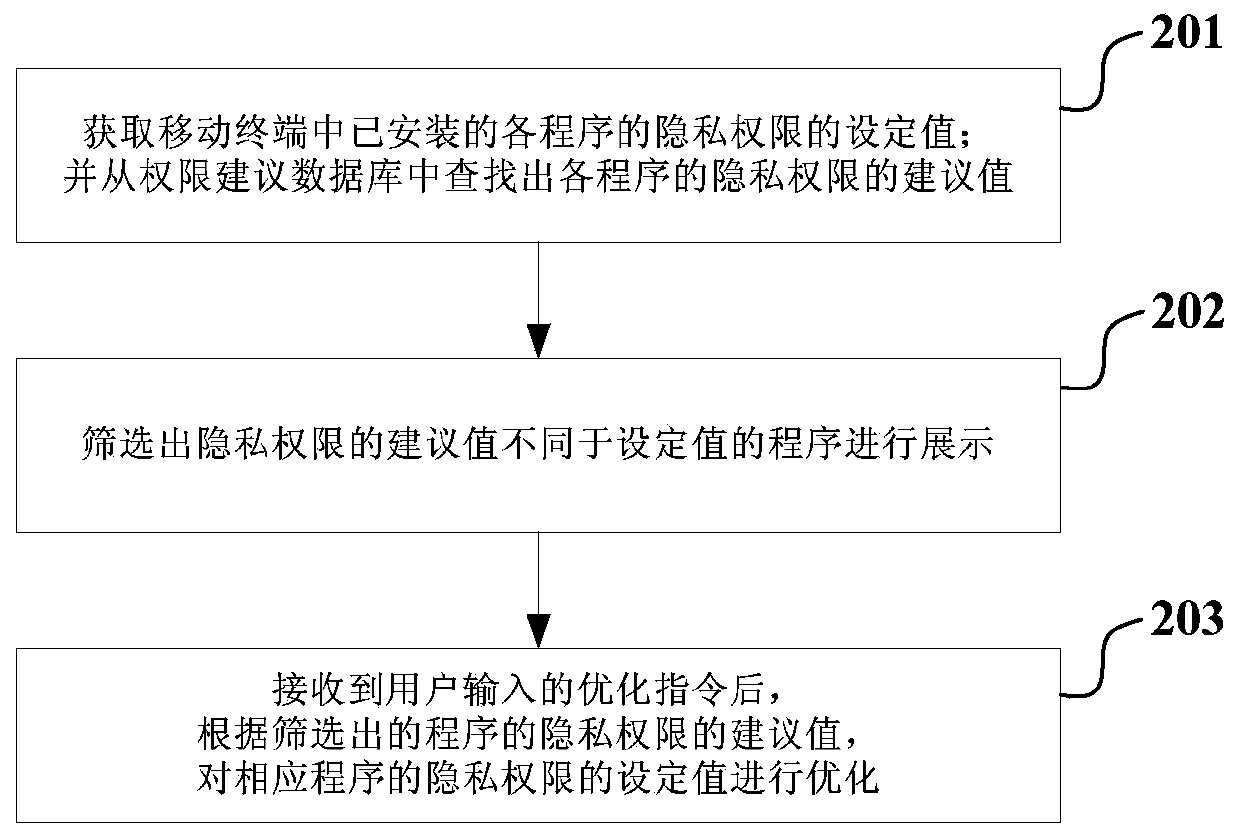
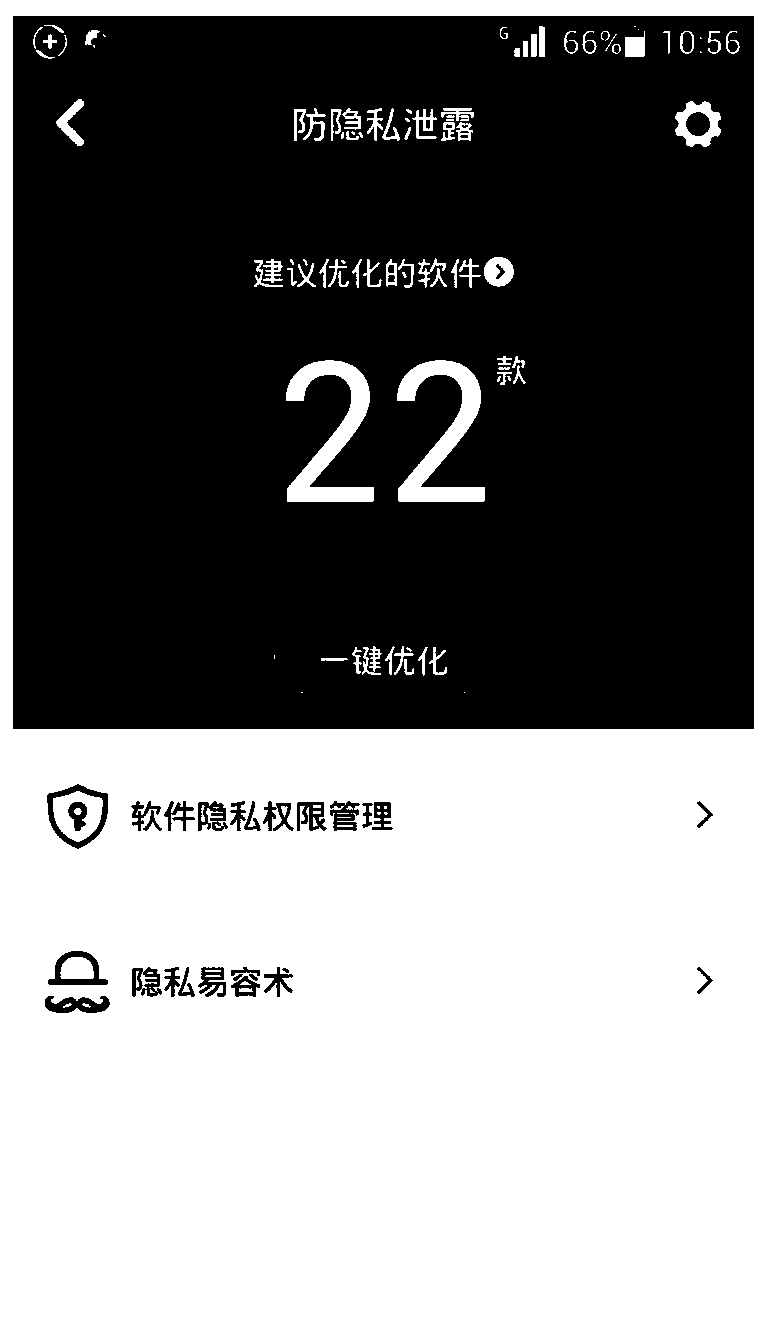
The embodiment of the invention provides a mobile terminal and a privacy permission optimizing method of the mobile terminal. The method comprises the steps that the set values of privacy permission of all programs installed in the mobile terminal are acquired; a permission suggestion database is searched for the suggestive values of the privacy permission of all the programs; the programs with the suggestive values of the privacy permission different from the set values are screened out and shown; after an optimization instruction input by a user is received, the set values of the privacy permission of the corresponding programs are optimized according to the suggestive values of the privacy permission of the screened-out programs. According to the technical scheme, the mobile terminal can optimize the set values of the privacy permission of all the programs installed in the mobile terminal according to the suggestive values, recorded in the permission suggestion database, of the privacy permission of the programs. Therefore, the probability of leaking the private information of the user can be greatly reduced, and the experience of the user can be improved.
Owner:BEIJING QIHOO TECH CO LTD
Method and system for protecting user privacy based on se android
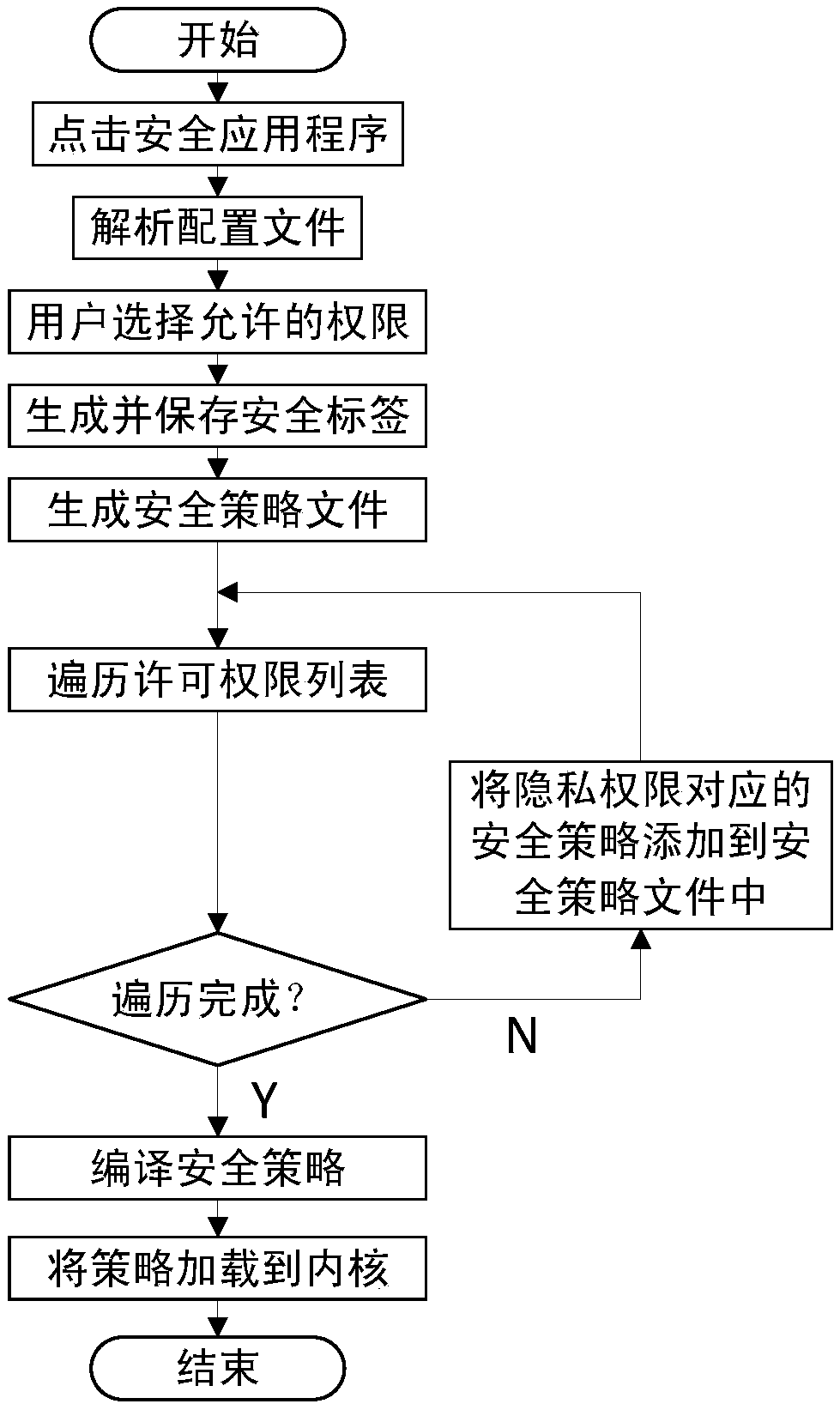
InactiveCN109508550AChange the setup processFlexible and controllable associationDigital data protectionUser privacyPrivacy rights
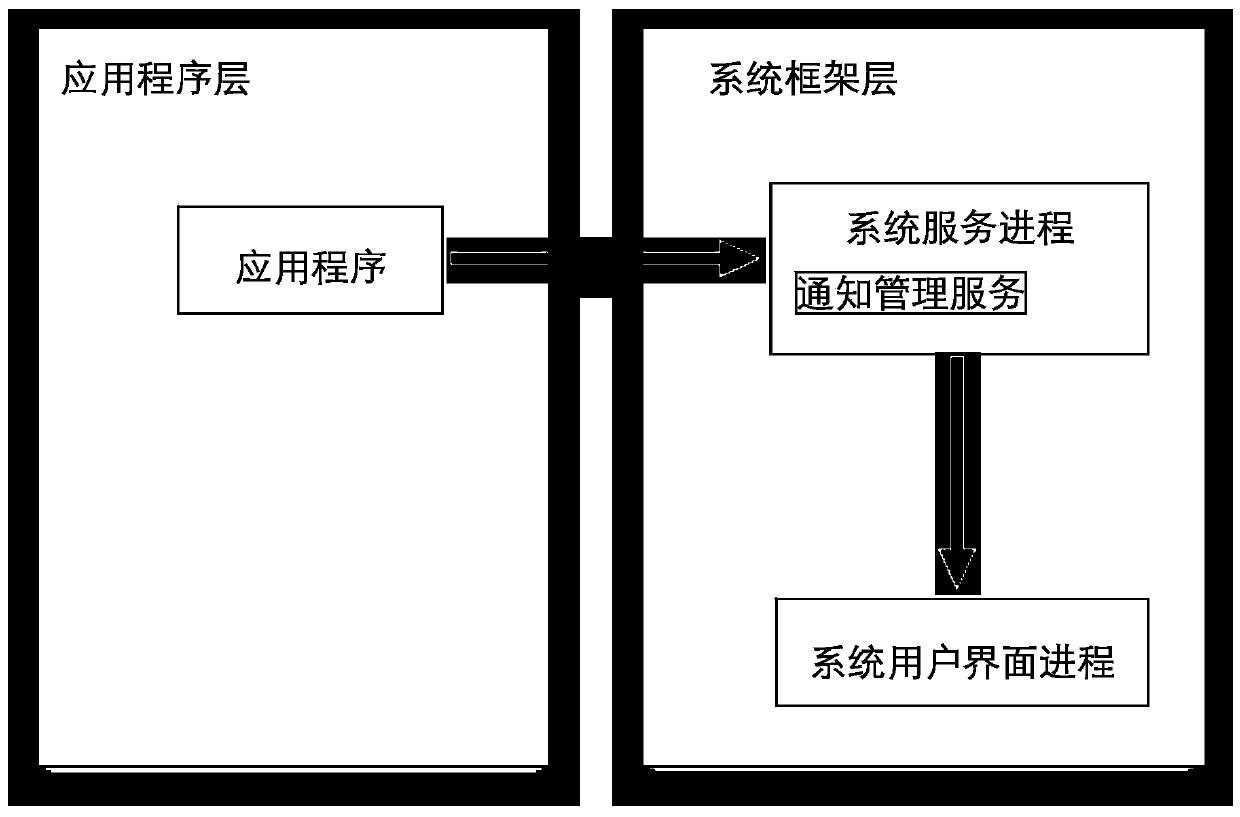
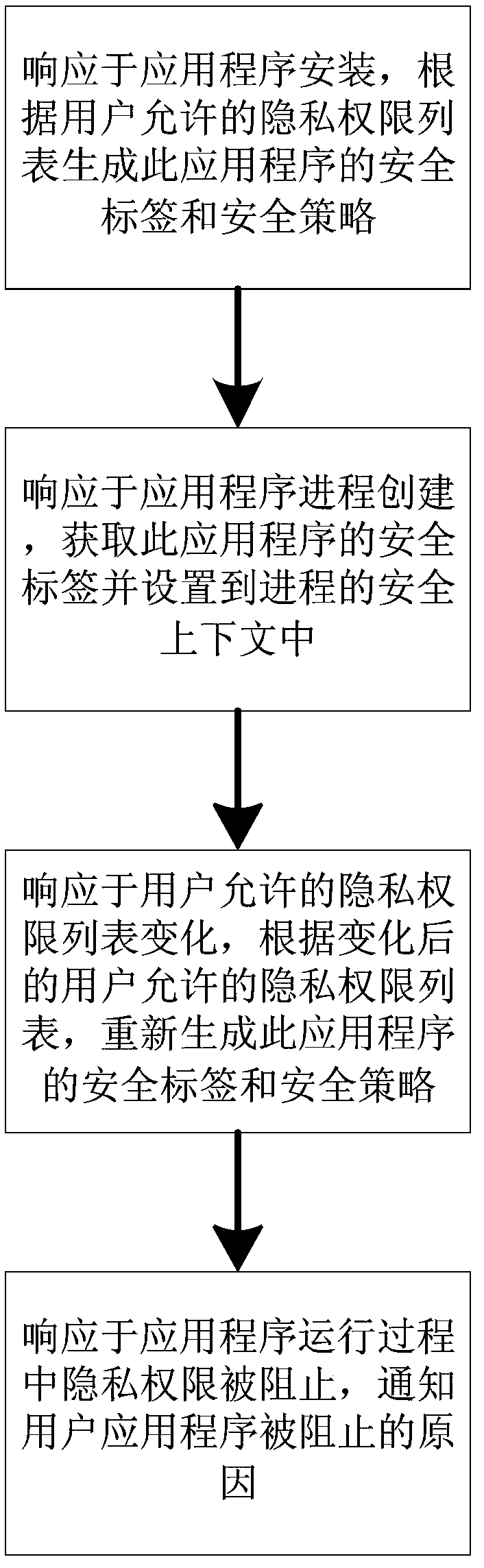
The invention discloses a user privacy protection method based on SE Android. The method comprises: in response to application program installation, generating a security label and a security policy of the application program according to a privacy right list permitted by the user; In response to application process creation, the security label of the application is obtained and set to the security context of the process; In response to the change of the privacy right list allowed by the user, the security label and the security policy of the application are regenerated according to the changed privacy right list allowed by the user. In response to privacy rights being blocked while the application is running, the user is notified of the reason why the application is blocked. At that sametime, a us privacy protection system is also disclosed. The invention improves the disadvantage that the security policy must be predefined by the developer of the SE Android system, makes the association and use of the policy more flexible and controllable, and avoids the trouble and inoperability of repeatedly burning and writing the security policy file of the bottom layer.
Owner:NANJING NARI GROUP CORP +3
Method for reinforcing security and protecting privacy right of positioning service in Wimax network
InactiveCN101370007BImprove securityProtection of privacySpecial service provision for substationData switching by path configurationCryptographic protocolUser privacy
A method for enhancing location-based service security and protecting user privacy in a Wimax network includes three aspects of LBS client authentication, LBS authentication and LBS requester authorization checking. The first method for LBS client authentication is to save the list of LBS clients that are authorized to access in LS. The second method for LBS client authentication is to employ security protocols like TLS, SSL, etc. in authentication process. LBS authentication is realized by checking whether the LBS and related QoS are matched with the subscribed LBS or not. The first method for LBS requester authorization checking is to perform LBS requester authorization checking by LS. The second method for LBS requester authorization checking is to perform LBS requester authorization checking by AAA. Thus, the present invention prevents illegal LBS clients or non-subscribed LBS service or unauthorized MSs from being provided with requested LBS service in virtue of the above three aspects. Therefore, the security can be enhanced for LBS service and user privacy can be protected in a Wimax network, and relevant blank space in current Wimax standard can be made up for.
Owner:BEIJING SAMSUNG TELECOM R&D CENT +1
Social platform information acquisition system
PendingCN114117250AInvasion of privacyImprove collection accuracyData processing applicationsDigital data information retrievalPrivacy rightsInformation presentation
The invention relates to the technical field of social platforms, and discloses a social platform information acquisition system, an information issuing platform is established in a social platform, and trial push is performed according to personal preferences; hot vocabularies in the information are selected, information content labels are formed by the hot vocabularies, voting options are formed by the labels, and then the information is popularized; selecting the labels after the information is browsed by a person, and forming judgment of the person on the information display content by selecting the labels of the information; labels are selected through judgment of individuals on contents, and new labels are formed through popular comments after popularization. According to the method, personal information can be collected through cognition and evaluation on information contents by individuals, the same crowd can be recommended, and meanwhile, the active time is summarized, so that people with the same cognition and the same object thought can be gathered, the information collection accuracy is effectively improved, and the user experience is improved. Meanwhile, the personal privacy right is prevented from being infringed.
Owner:苏州微记信息科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com