Method for reinforcing security and protecting privacy right of positioning service in Wimax network
A positioning service and positioning server technology, applied in the field of mobile communication, can solve the problems of not complying with Wimax network, the privacy check mechanism is obscure, and the protocol stack cannot transmit and process the message of positioning service authentication and authorization check, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
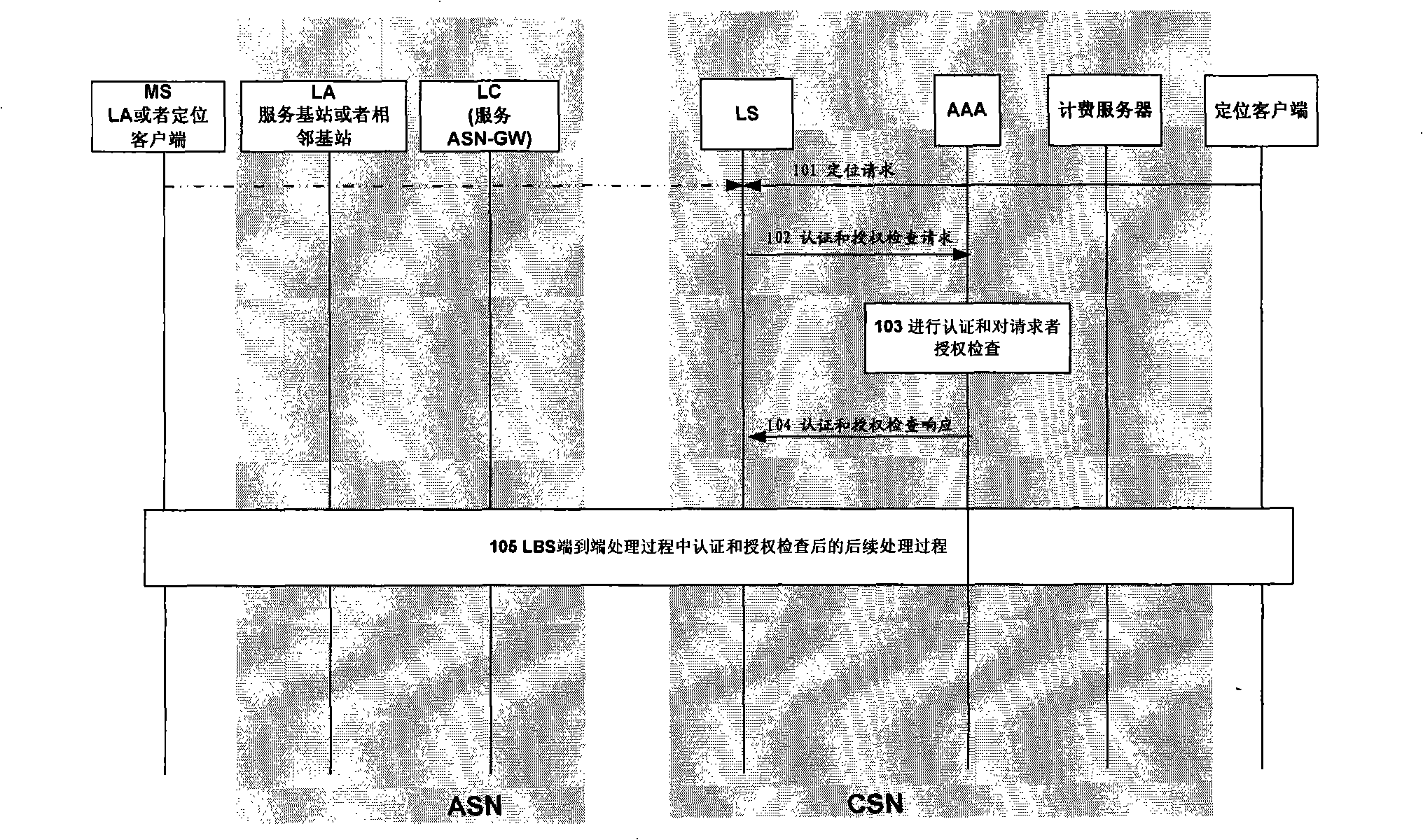
[0085] To achieve the above object, the method for enhancing security and protecting privacy rights for positioning services in the Wimax network according to the present invention will be described from the following three aspects:
[0086] 1. Authentication of LBS clients
[0087] (1) A list of clients allowed to access LBS is stored in LS;
[0088] For specific technical solutions, please refer to Patent Document 1.
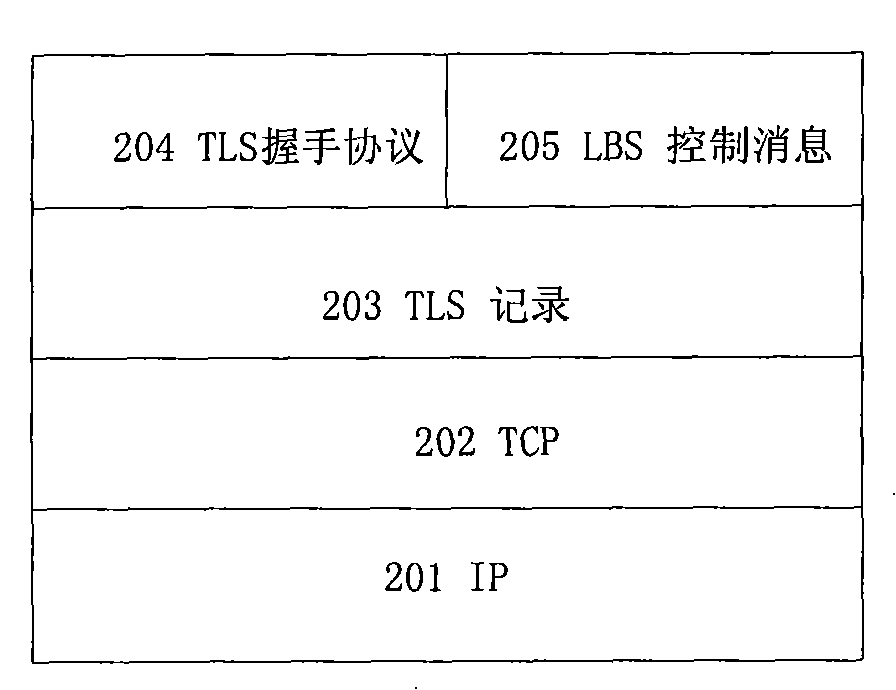
[0089](2) LBS client and LS use existing security protocols such as SSL / TLS
[0090] The interface protocol stack between LBS client and LS includes 201 IP layer, 202 TCP layer, 203 TLS record layer, 204 TLS handshake protocol and 205 LBS control layer.
[0091] The process of LBS client and LS using existing security protocols such as SSL / TLS to authenticate and start LBS services includes the following five steps:
[0092] 1. Establish security capability attributes;
[0093] 2. Server authentication and key exchange; (optional)
[0094] 3. Client authe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com