An android malicious code detection method based on community structure analysis
A malicious code detection and community structure technology, applied in the field of malicious code of a large number of Android application samples, can solve the problems of unfavorable resistance to variant viruses, high time-consuming, high detection rate, improved operating efficiency, and reduced computational complexity. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
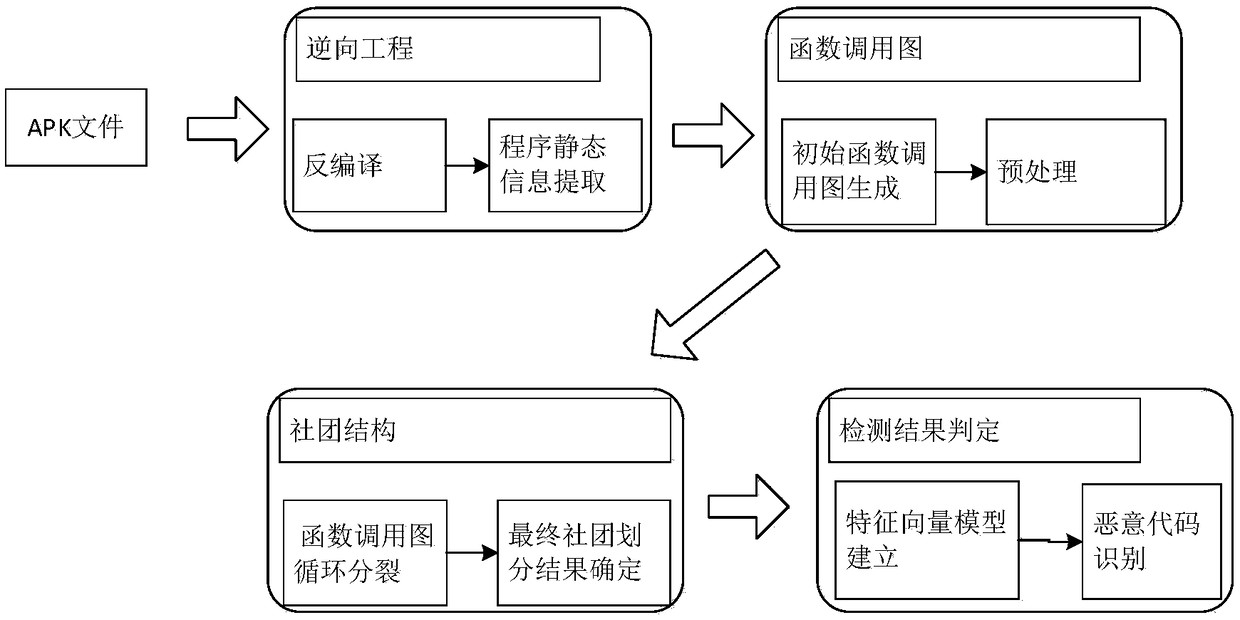
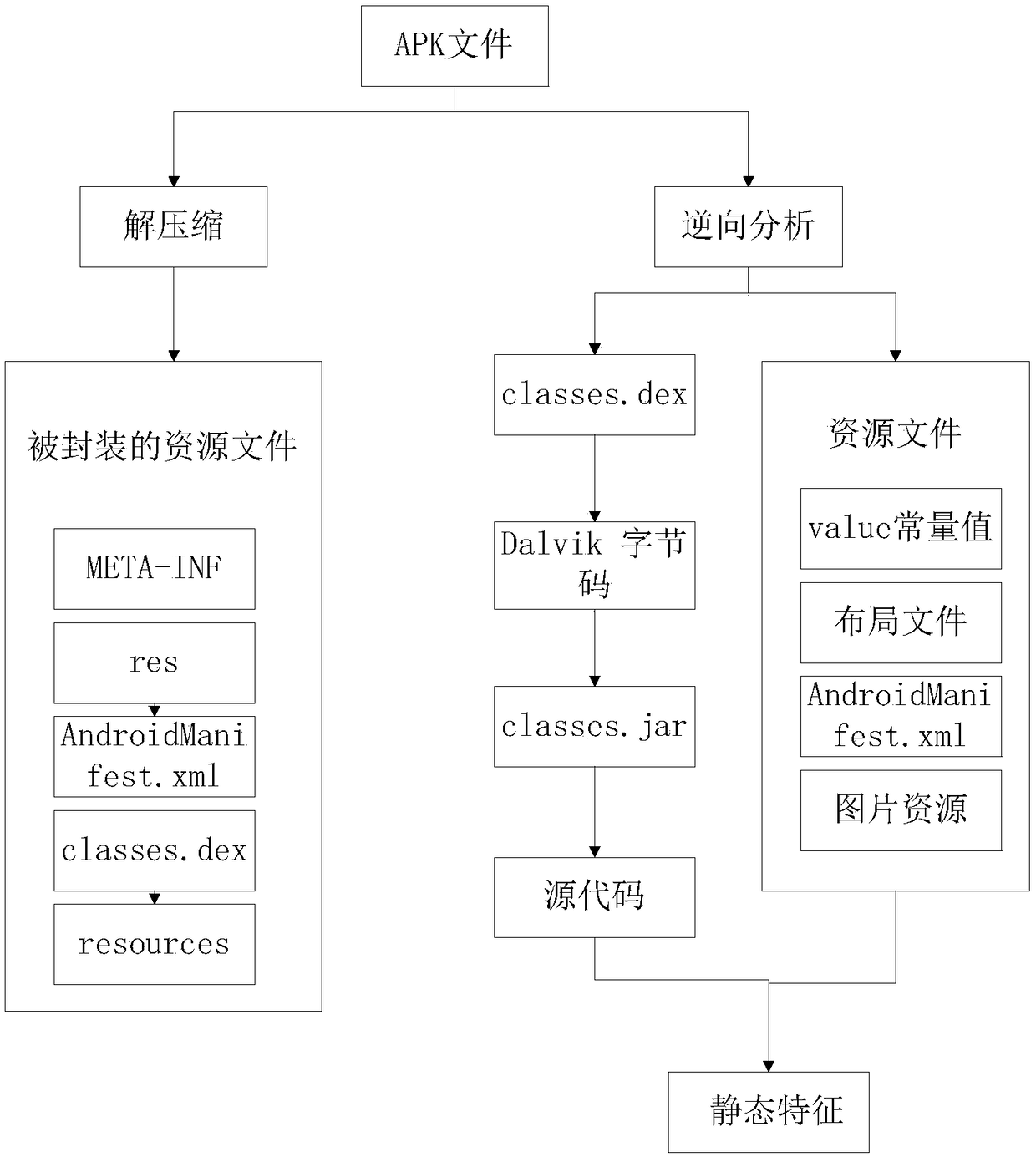
[0041] The present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments. The method of the present invention combines the structural features of the function call graph and the static features of the application program to determine the most ideal community division results, and then extracts the features used for machine learning from the finally divided communities, and puts them into the feature vector for further analysis. Classification learning, so as to achieve the purpose of judging the maliciousness of the application. The method of the present invention improves the division efficiency of graphs by improving the GN method, and uses machine learning technology to judge maliciousness, which also bypasses the complicated calculation caused by graph similarity comparison. Experimental results show that the method can identify malicious codes efficiently.
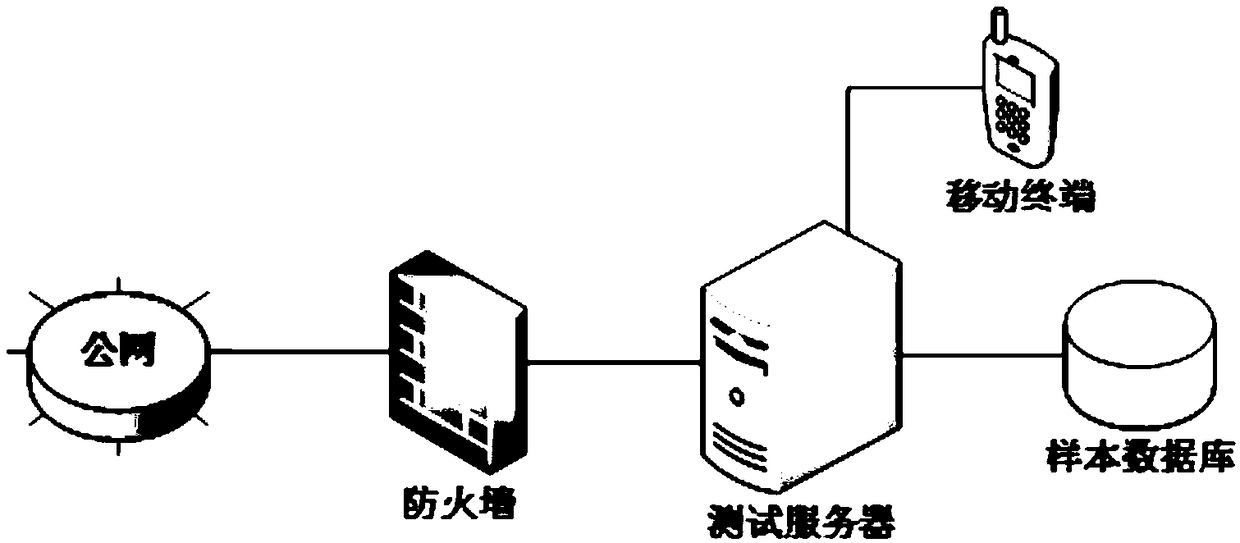
[0042] according to figure 2 The detection ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com