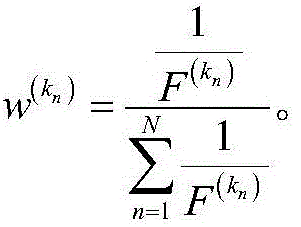Comprehensive vulnerability assessment method based on power communication network structure and state
A power communication network, vulnerability technology, applied in electrical components, data exchange networks, digital transmission systems, etc., can solve problems such as incomplete evaluation and inaccurate evaluation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
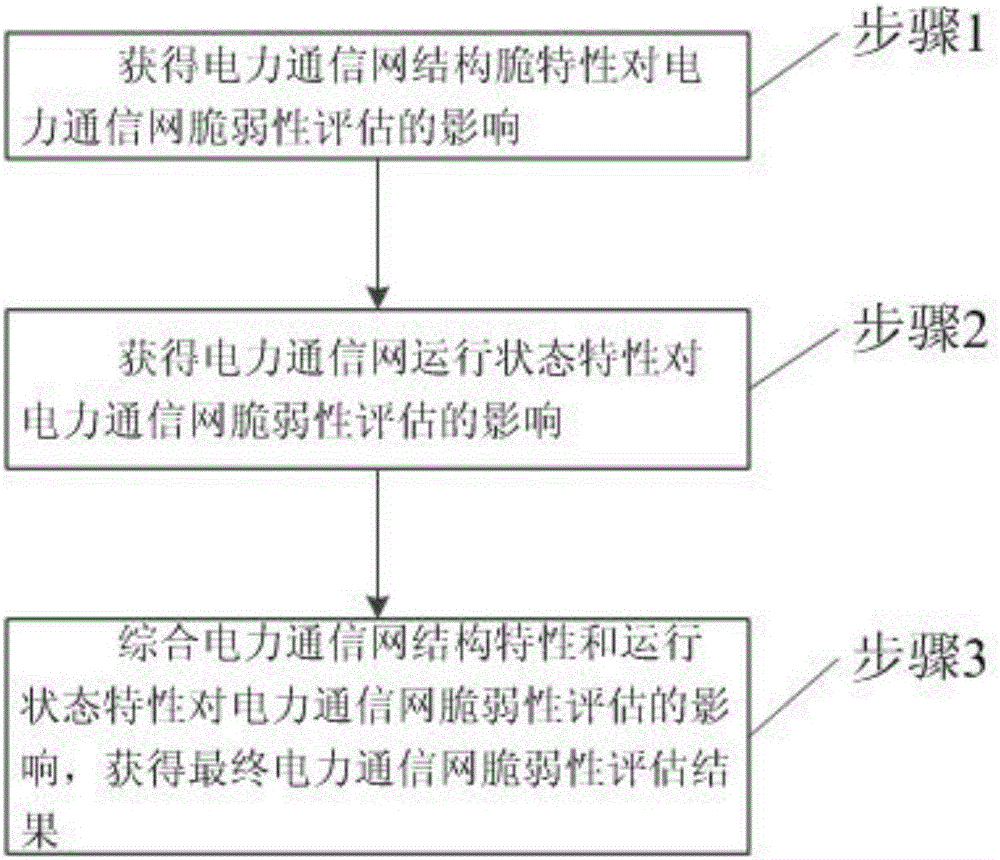
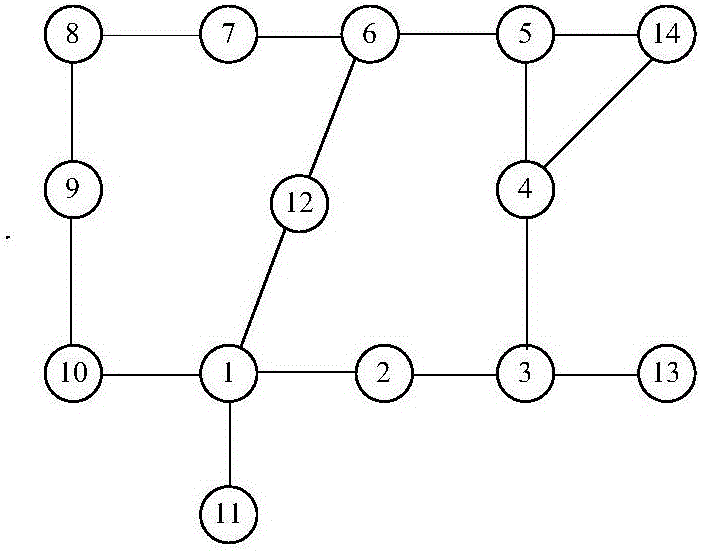
[0040] The invention provides a comprehensive vulnerability assessment method based on the structure and state of the power communication network, which solves the technical problems of incomplete and inaccurate assessment in the existing vulnerability assessment method of the power communication network, and realizes the current operation of the fusion network After the status, the vulnerable links in the network can be located more comprehensively, and the technical effect of vulnerability assessment can be carried out according to different network topologies and operating states.
[0041] In order to understand the above-mentioned purpose, features and advantages of the present invention more clearly, the present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments. It should be noted that, under the condition of not conflicting with each other, the embodiments of the present application and the features ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com