A ssl/tls encrypted malicious service discovery method based on certificate feature generalization and server transition behavior
A service discovery and malicious server technology, applied in the field of SSL/TLS encrypted malicious service discovery, can solve the problems of insufficient real-time performance, insufficient robustness, performance degradation, etc., to avoid the increase of missed detection rate, quickly and effectively extract, improve The effect of robustness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
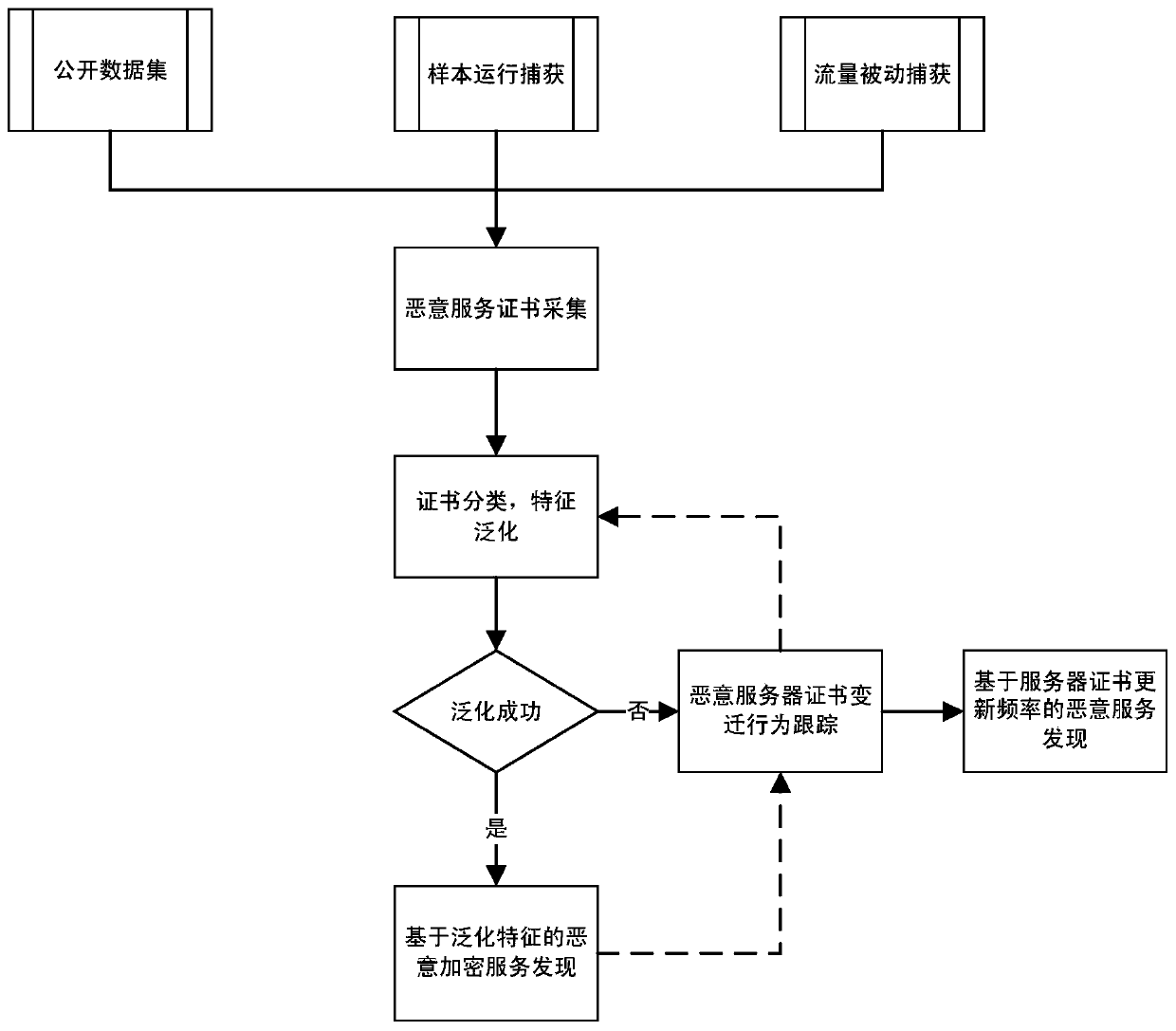
[0044] Example 1 Based on the generalization of certificate features, a new bank stealing Trojan service was found in a scientific research network
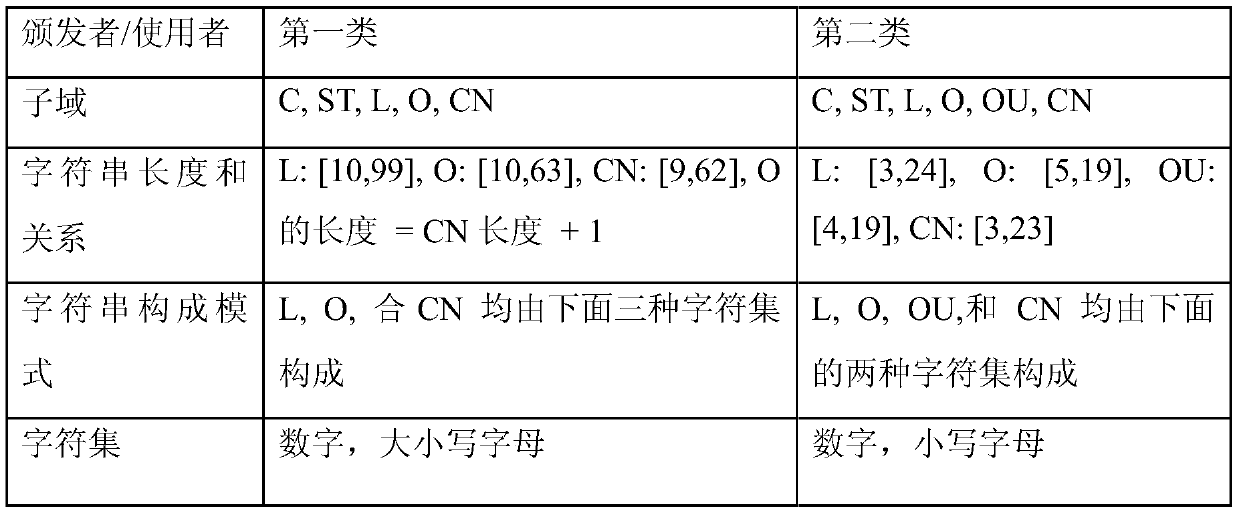
[0045] More similar malicious services were found based on part of the certificate information of the Dyre online banking stealing Trojan horse in SSLBL. On August 31, 2015, 3,127 Dyre certificate brief information and corresponding blacklisted IP ports (653 in total) were collected from the SSLBL website (https: / / sslbl.abuse.ch). With the help of feature generalization, the following two main types of generalized features are obtained:
[0046]
[0047] Obtain certificates from the traffic of a domestic scientific research network, and detect the above two types of characteristics. Within a week, 520 new certificates were found, corresponding to 1741 suspicious servers, of which 1708 were new discoveries, and 33 were in Dyre of SSLBL. in the complete blacklist list. Through the active scanning method, the newly discovered s...
example 2
[0048] Example 2 Based on the generalization of certificate characteristics and the entire network scanning certificate data set, a bank secret-stealing Trojan service is discovered
[0049] More similar malicious services were found based on part of the certificate information of the Dridex online banking stealing Trojan horse in SSLBL. In October 2015, the certificate features adopted by the Dridex Trojan horse in SSLBL were generalized, and then the generalized features were applied to the certificate scanning data set of port 443 of the entire IPv4 network of RAPID7 for experiments (https: / / scans.io ), about 500 suspicious SSL / TLS server IPs were found.
example 3
[0050] Example 3 Discover unknown encrypted malicious remote control services based on coarse-grained features and server certificate update frequency
[0051] Through a month's monitoring of known malicious servers, it was found that the remote server certificate update frequency of a Trojan horse control service was 3 days, but the generalization characteristics were not obvious. Therefore, with the help of certificate renewal frequency screening, 5 unknown remote control servers were successfully found in the 24-hour traffic of an enterprise network egress.
[0052] In addition to the above-mentioned embodiments, the present invention can also adopt other implementation modes, including:
[0053] 1. Step 1) is the collection of certificates for known malicious services. There are various ways to obtain certificates for malicious services. In addition to the methods listed, you can also obtain them from security companies and other channels. In addition, the certificate acq...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com