Method and device for preventing library-hit attacks
A technology with one purpose and the same purpose, applied in electrical components, transmission systems, etc., can solve problems such as misjudgment and missed judgment, and achieve the effect of improving accuracy and avoiding misjudgment.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
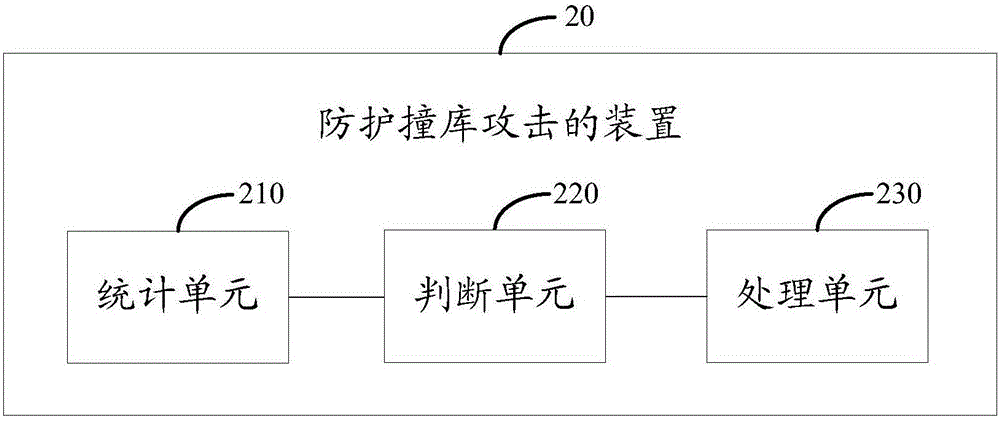
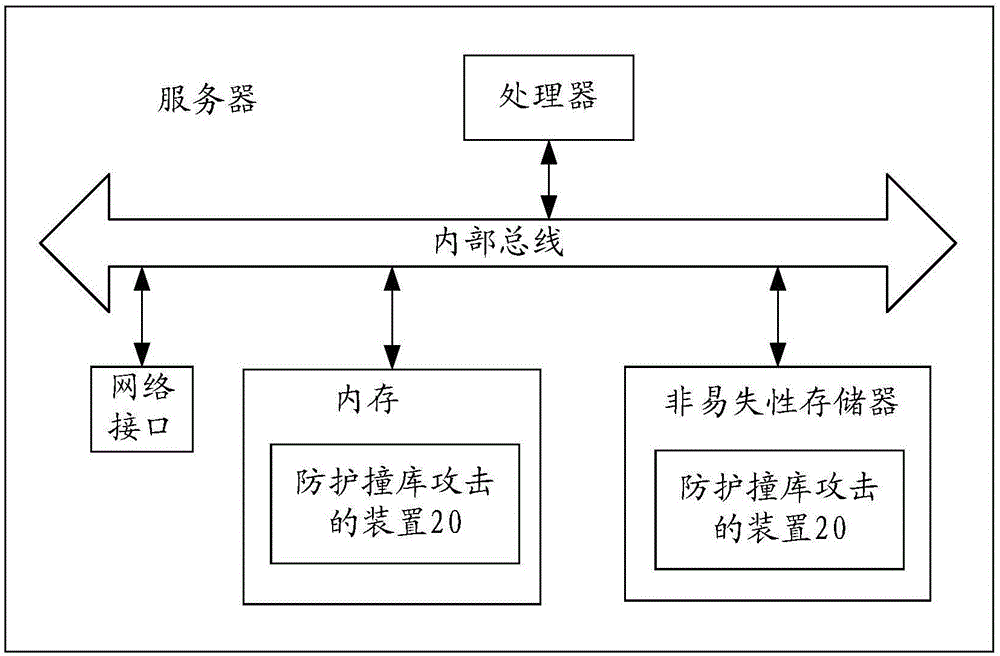
[0048] In order to enable those skilled in the art to better understand the technical solutions in the embodiments of the present invention, and to make the above-mentioned purposes, features and advantages of the embodiments of the present invention more obvious and understandable, the following describes the existing technical solutions and the present invention in conjunction with the accompanying drawings. The technical solutions in the embodiments of the invention are described in further detail.
[0049] At present, many Internet sites use a registration mechanism to manage users, and the registration mechanism is also conducive to the communication between users. When a user registers a personal account on multiple websites, for the convenience of memory, only a few sets of user accounts and passwords are often set up to be used on multiple websites. If the user account and password are leaked, the attacker may collect the leaked user account and password, generate a co...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com