Business processing method and device
A business processing and identification algorithm technology, applied in the Internet field, can solve the problems of increased system resource consumption and analysis time, high computational complexity, and many rule models for risk identification, so as to save system resource consumption, ensure accuracy, The effect of improving the recognition efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
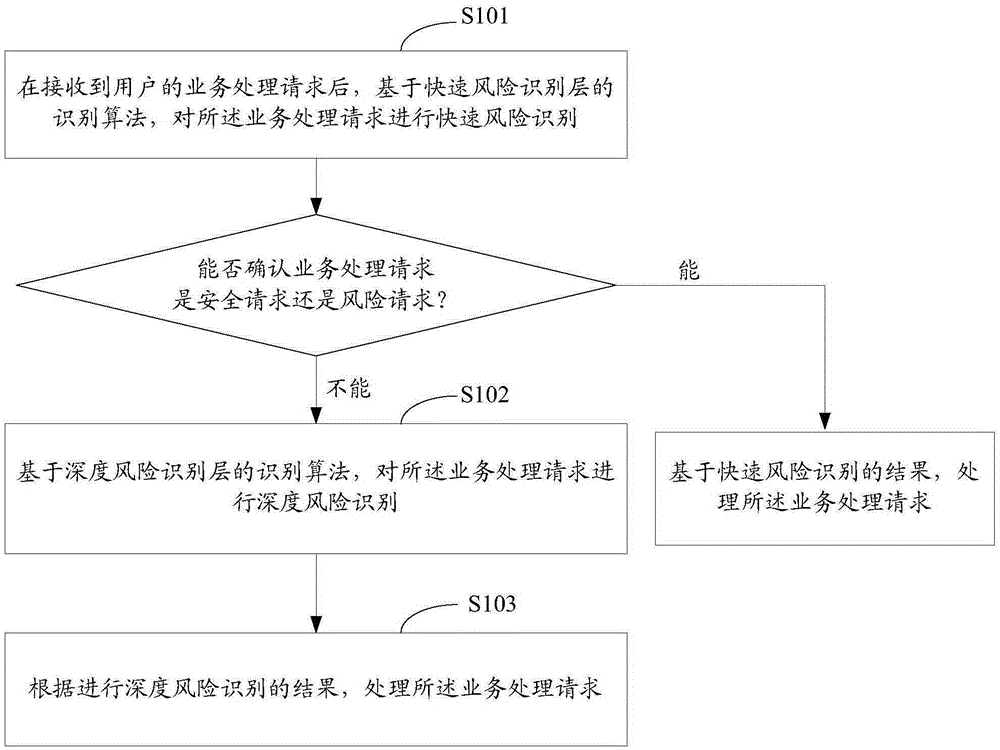
[0039] Such as figure 1 As shown, it is a flow chart of the business processing method provided in Embodiment 1 of the present application, including the following steps:
[0040] S101: After receiving a service processing request from a user, perform rapid risk identification on the service processing request based on the identification algorithm of the rapid risk identification layer.
[0041] In the specific implementation process, first, based on the pre-stored trusted user list and risk user list, rapid risk identification can be performed on the service processing request. The trusted user list here may include the user's trusted Internet Protocol (Internet Protocol, IP) address, trusted Media Access Control (MediaAccess Control, MAC) address, trusted terminal location and other user data; correspondingly, the risk user The list may include user data such as risk application account numbers, risk bank card numbers, and risk IP addresses. If the user data in the busines...
Embodiment 2
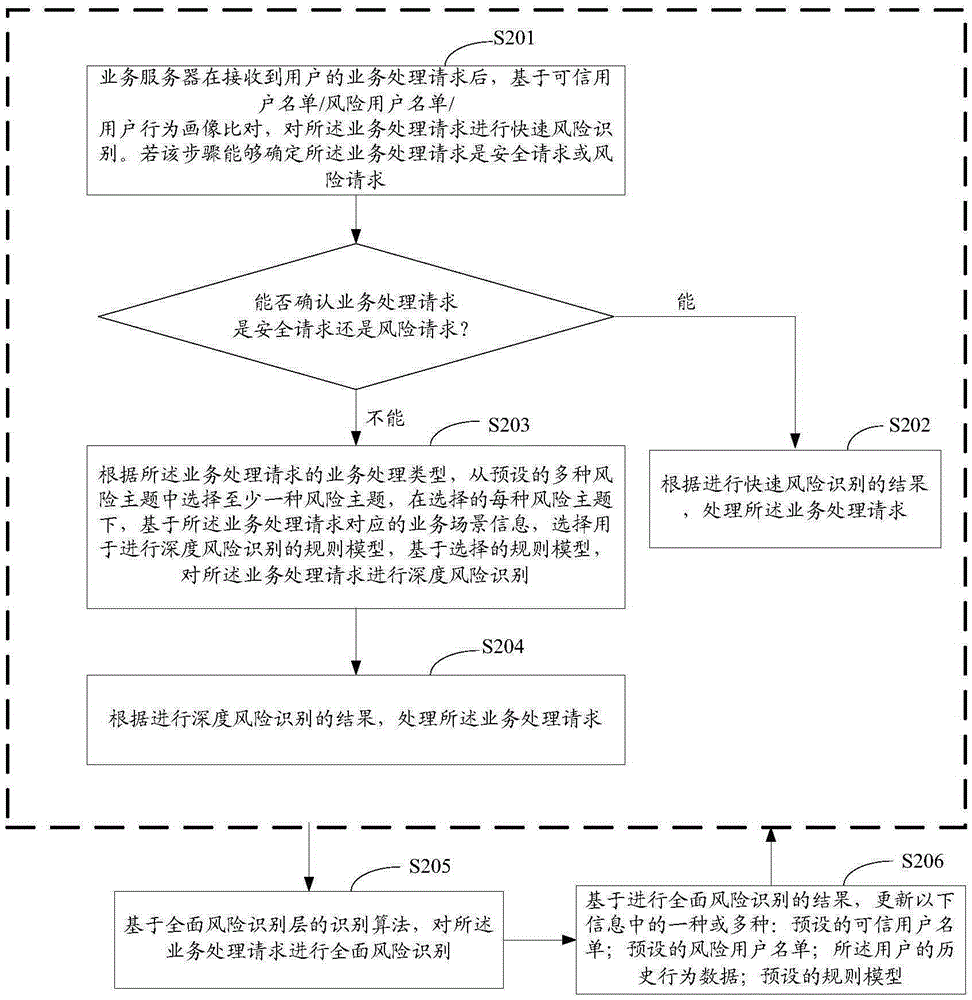
[0057] In the second embodiment of the present application, in order to further improve the accuracy of risk identification, a comprehensive risk identification layer is designed. The risk identification process is performed asynchronously with the rapid risk identification and in-depth risk identification, that is, it does not affect the business processing process. The results of comprehensive risk identification can be used to optimize user data and rule models for rapid risk identification and in-depth risk identification.
[0058] Such as figure 2 As shown, it is a flow chart of the risk identification method provided in Embodiment 2 of the present application, including:
[0059] S201: After receiving the user's business processing request, the business server performs rapid risk identification on the business processing request based on the comparison of trusted user list / risk user list / user behavior profile. If it can be determined in this step that the service proce...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com