Android malware real-time detection method based on network flow analysis
A malware and network traffic technology, applied in the field of communications, can solve the problems of ineffective detection, single network traffic data characteristics, and insufficient utilization of network traffic, etc., and achieve the effect of good detection accuracy.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
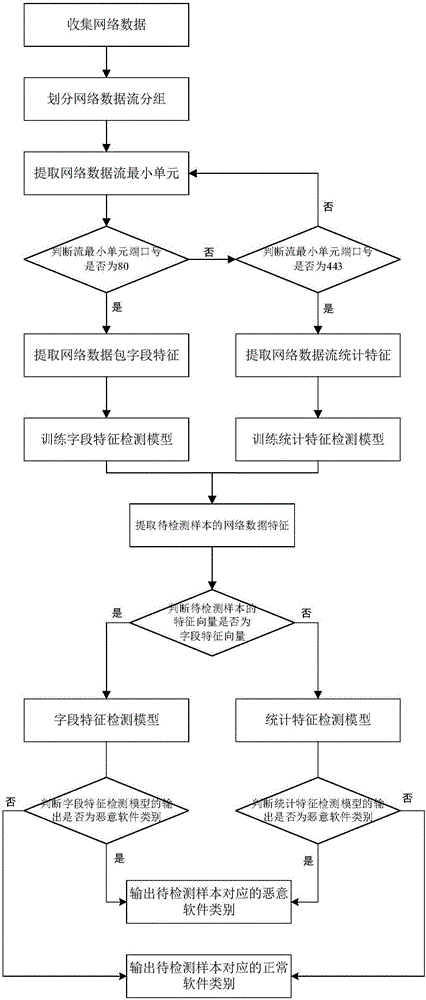
[0050] The present invention will be further described below in conjunction with the accompanying drawings.
[0051] Refer to attached figure 1 , to further describe the implementation method of the present invention.
[0052] Step 1, collect network data.
[0053] Use network packet capture tools to collect network traffic data generated by normal software samples and malware samples respectively, and use the collected network traffic data as the initial data set for training malware detection models.
[0054] Step 2, dividing the network data flow into groups.
[0055] According to the definition rules of network data flow grouping, the initial data set is grouped to obtain multiple different network data flow groups.
[0056] The definition rule of the network data stream grouping is that, for the network data packets in the initial data set, according to the time sequence of the network data packets, the adjacent network data packets with a time interval of less than 4....
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com