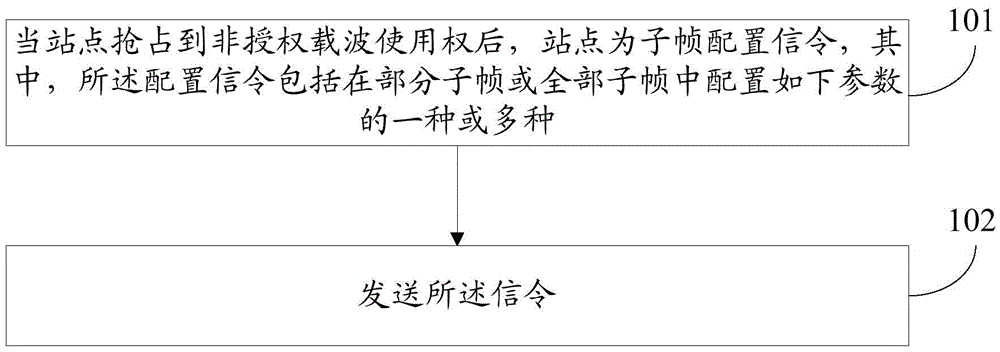
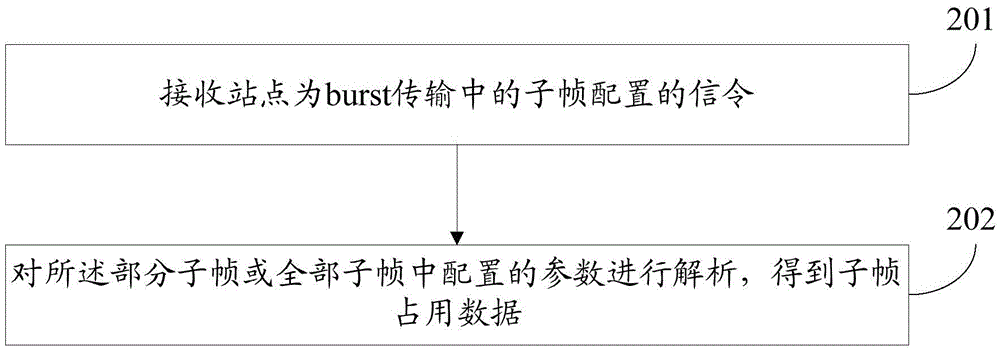
Signaling configuration method and signaling transmission method based on unauthorized carrier, station, and terminal
A configuration method and an unauthorized technology, applied in the field of communication, can solve problems such as difficulty in collaboration, high overhead in centralized management, and transmission of reference signals that take up time.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0142] In embodiment 1, only parameters A and B are used as examples.
[0143] In the current subframe, the station configures parameter A as 0100 and configures parameter B as 0011, then the actual occupied subframe of the station is: 4+1 subframes after the current subframe (including) are downlink, and there are 3+ 1 uplink subframe or subframe for other purposes. The station may also modify (mainly increase) the number of subsequent subframes expected to be occupied by the value of parameter A sent in each downlink subframe. This is beneficial to use fewer bits to describe more consecutively occupied subframes. For example, when 3 bits are used to describe parameter A, and the occupier wants to claim to occupy 10 subframes, the station sets parameter A to 111 in the first occupied subframe, and sets parameter A to 111 in the second occupied subframe. is 111, set the parameter A to 111 in the third occupied subframe, set the parameter A to 110 in the fourth occupied subfr...
Embodiment 2
[0145] Embodiment 2, an example using parameters A, B, and C.
[0146] In the current subframe, the station configures parameter A as 0100, configures parameter B as 0011, and configures parameter C as 10101 (the number of bits of parameter C is the number of downlink subframes described by parameter A), then the actual occupied subframe of the station is: from 4+1 subframes after the start of the current subframe (including) are downlink, and then there are 3+1 uplink subframes or subframes for other purposes, and the station occupies 4+1 downlink MBSFN subframes and non-MBSFN subframes The position order of the frame is: MBSFN subframe, non-MBSFN subframe, MBSFN subframe, non-MBSFN subframe, MBSFN subframe.
[0147] The terminal receives the above duration signaling in the subframe and analyzes it. According to the signaling agreement, the terminal analyzes the bits of parameter A and parameter B and learns that there are still 5 downlink subframes after the current subframe...
Embodiment 3
[0148] Embodiment 3, an example using parameters A, B, and D.
[0149] The station forwards the MBSFN subframe configuration information in the LAA carrier of the UE through the Pcell for the UE, which may be forwarded through a point-to-point UE RRC dedicated message or through a point-to-multipoint broadcast message. For the LAA unlicensed carrier, when the station occupies it, it needs to determine which subframes in the occupied period are MBSFN subframes according to the subframe timing of the corresponding Pcell. Then, the signal / signaling is sent in the corresponding MBSFN subframe according to the configuration requirements of the MBSFN subframe.
[0150] In the current subframe, the station configures parameter A as 0100 and configures parameter B as 0011, then the actual occupied subframe of the station is: 4+1 subframes after the current subframe (including) are downlink, and there are 3+ 1 uplink subframe or subframe for other purposes, and the station occupies 4+...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com