Vulnerability mining method and device
A vulnerability mining and vulnerability technology, applied in the field of application security, can solve the problems of difficult discovery of high-risk vulnerabilities, no solution proposed, difficulty of reverse analysis, etc., and achieve the effect of solving the low efficiency of vulnerability mining
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
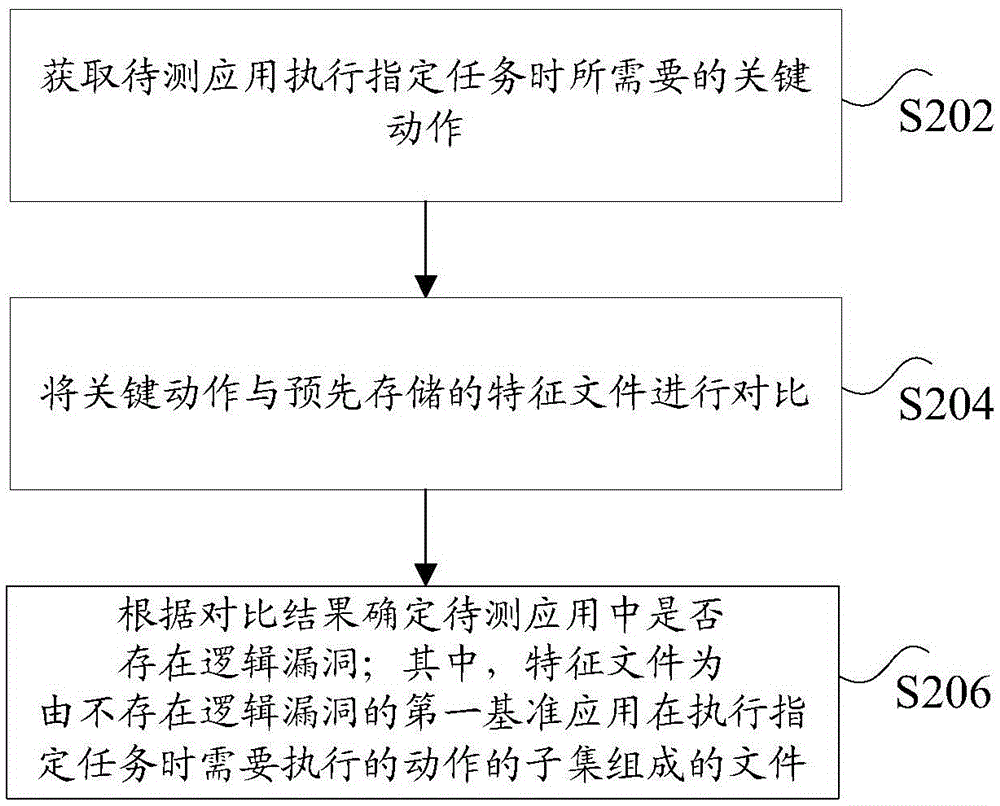
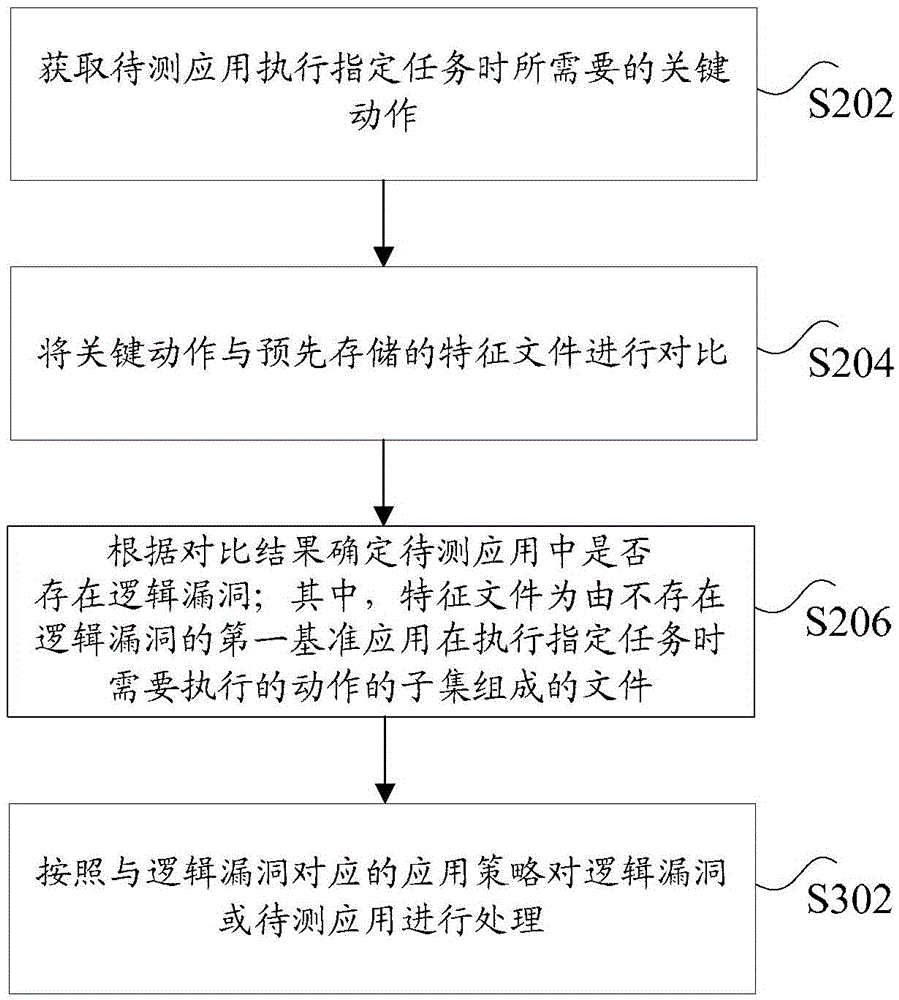
[0020] According to the embodiment of the present application, an embodiment of a vulnerability mining method is also provided. It should be noted that the steps shown in the flow chart of the accompanying drawings can be executed in a computer system such as a set of computer-executable instructions, and, although A logical order is shown in the flowcharts, but in some cases the steps shown or described may be performed in an order different from that shown or described herein.
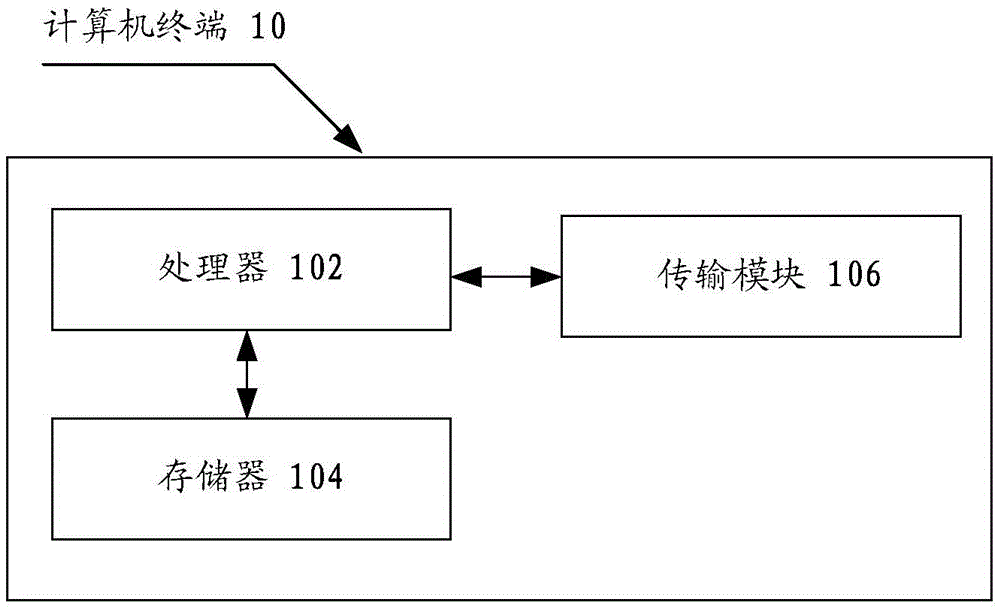
[0021] The method embodiment provided in Embodiment 1 of the present application may be executed in a mobile terminal, a computer terminal, or a similar computing device. Take running on a computer terminal as an example, figure 1 It is a block diagram of the hardware structure of a computer terminal of a vulnerability mining method according to the embodiment of this application. Such as figure 1 As shown, the computer terminal 10 may include one or more (only one is shown in the figure) processor...
Embodiment 2
[0083] According to an embodiment of the present invention, a device for implementing the above-mentioned method for automatically mining logic vulnerabilities of application programs is also provided, Image 6 is the structural frame of the vulnerability mining device according to the embodiment of the present application Figure 1 ,Such as Image 6 As shown, the device includes:
[0084] An acquisition module 62, configured to acquire the key actions required by the application under test to perform specified tasks;
[0085] It should be noted that the above key actions may include: a function called when the application under test executes a specified task, the function may only include system functions, may only include non-system functions, or may include both system functions and non-system functions, The content contained in this function varies according to the specific situation. The above-mentioned system function refers to a function that has nothing to do with th...
Embodiment 3
[0119] Embodiments of the present invention may provide a computer terminal, and the computer terminal may be any computer terminal device in a group of computer terminals. Optionally, in this embodiment, the foregoing computer terminal may also be replaced with a terminal device such as a mobile terminal.
[0120] Optionally, in this embodiment, the foregoing computer terminal may be located in at least one network device among multiple network devices of the computer network.
[0121] In this embodiment, the above-mentioned computer terminal can execute the program code of the following steps in the vulnerability mining method: obtain the key actions required by the application under test to perform the specified task; compare the key actions with the pre-stored feature files; and according to the comparison As a result, it is determined whether there is a logical loophole in the application to be tested; wherein, the feature file is a file composed of a subset of actions th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com