A data anomaly detection method, system and server having the system
A data anomaly and detection method technology, applied in digital data information retrieval, electrical digital data processing, special data processing applications, etc. The effect of practicality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
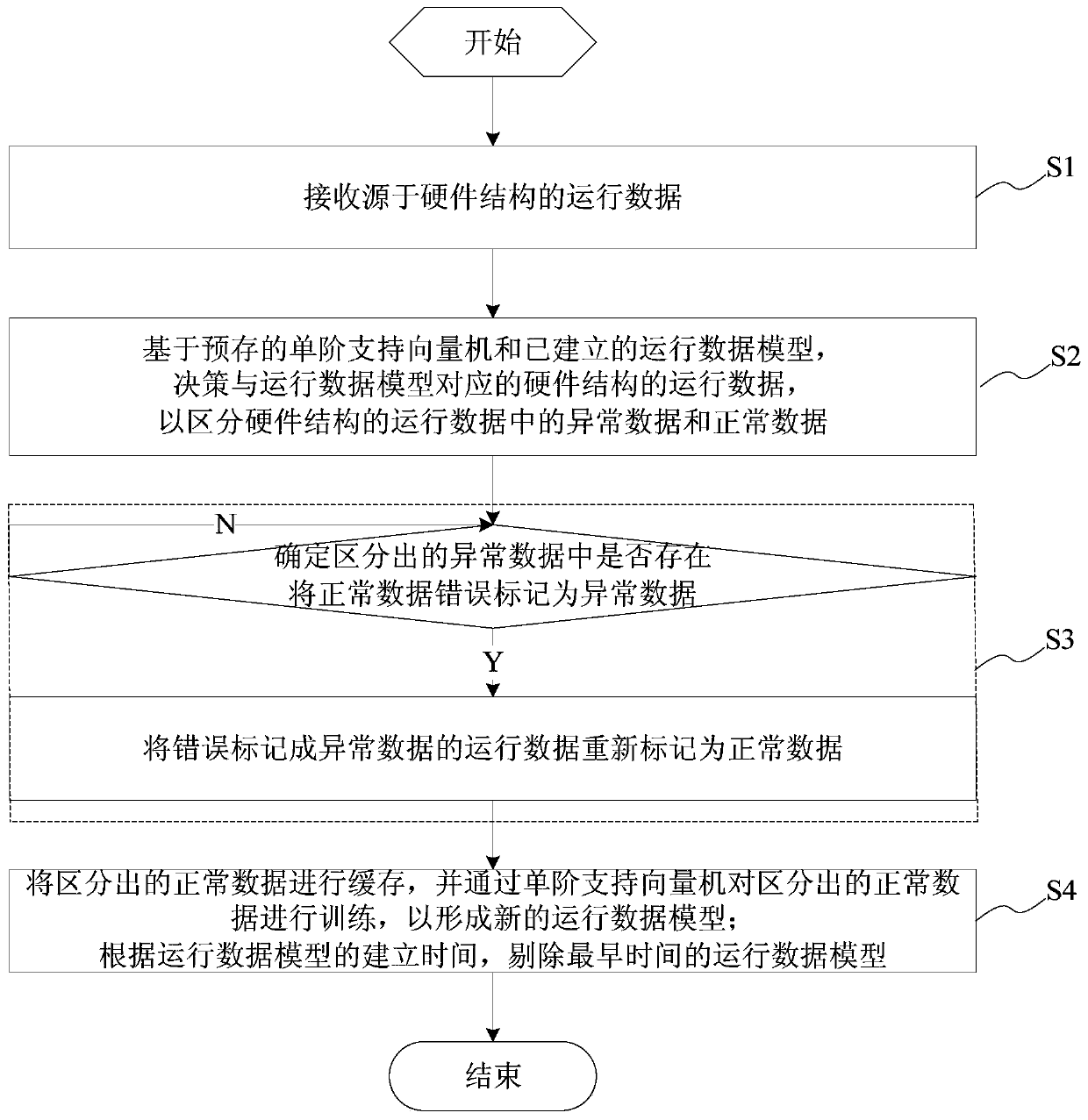
[0043] In this embodiment, a data anomaly detection method is applied to electronic equipment, and the data anomaly detection method includes the following steps:
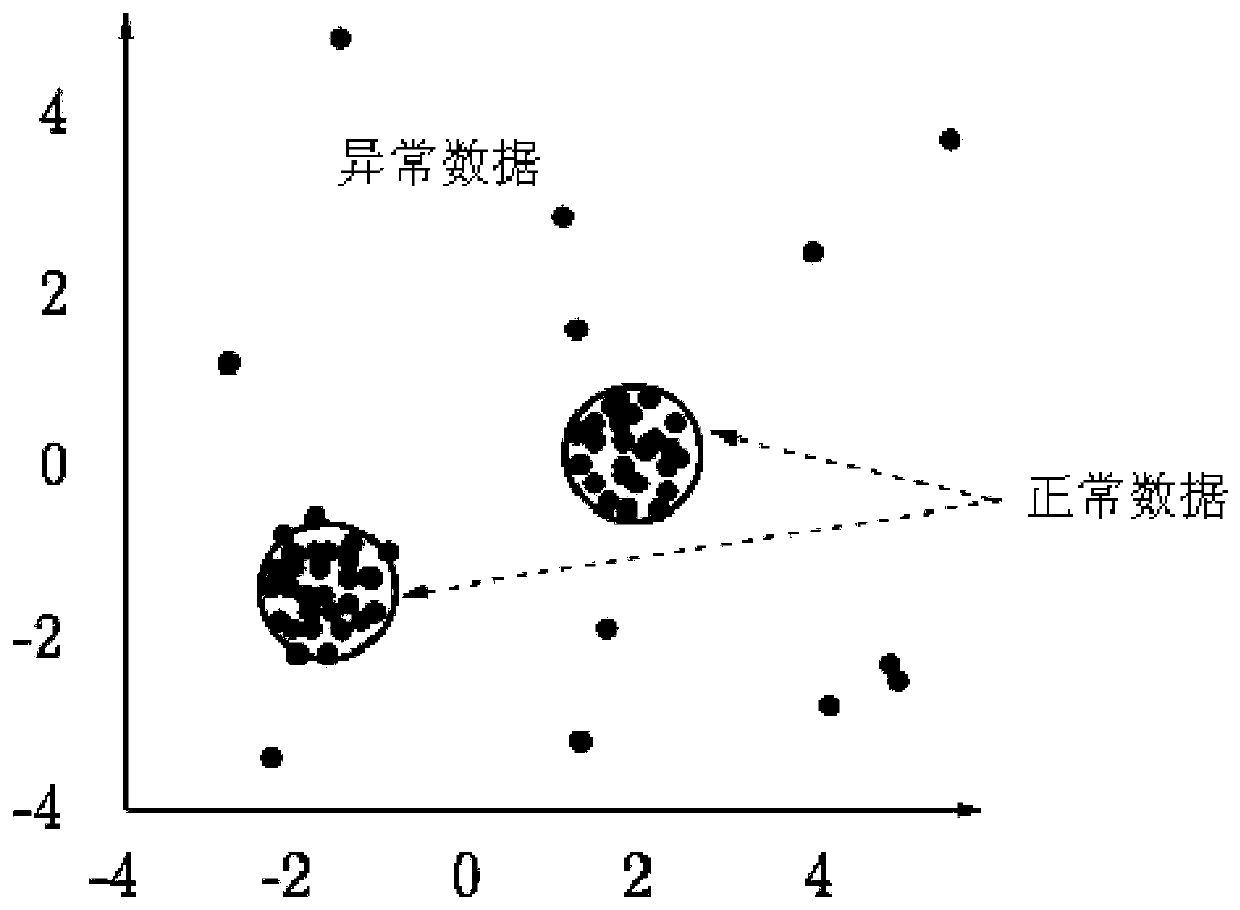
[0044] Step 1, based on the pre-stored single-stage support vector machine and the established operating data model, determine the operating data of the hardware structure corresponding to the operating data model, so as to distinguish abnormal data and normal data in the operating data of the hardware structure;
[0045] Step 2: vote on the identified abnormal data to determine whether normal data is wrongly marked as abnormal data in the identified abnormal data;
[0046] The data anomaly detection method provided by this embodiment will be described in detail below with reference to figures. The data anomaly detection method described in this embodiment is applied to an electronic device. In this embodiment, the electronic device may be an OpenSSL server that uses Heartbleed vulnerability. The data anomaly detec...
Embodiment 2
[0067] This embodiment provides a data anomaly detection system, which is applied to an electronic device. In this embodiment, the electronic device may be an OpenSSL server that uses Heartbleed vulnerability. The data anomaly detection method is used to detect network attacks and detect data models The Heartbleed vulnerability is unknown. see Figure 6 , is shown as a schematic diagram of the principle structure of the data anomaly detection system. Such as Figure 6 As shown, the data anomaly detection system 1 includes a data receiving module 11 , a decision-making module 12 , and a data summarizing module 13 .
[0068] The data receiving module 11 is used for receiving the running data originating from the hardware structure of the OpenSSL server. In this embodiment, the hardware structure is the running data stored in the RAM of the OpenSSL server. The running data stored in RAM comes from off-chip memory.
[0069] The decision-making module 12 connected with the dat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com