Secret level marking and checking method and device thereof
A verification method and a technology of a verification device, which are applied in the field of information security and can solve problems such as large watermark capacity requirements
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
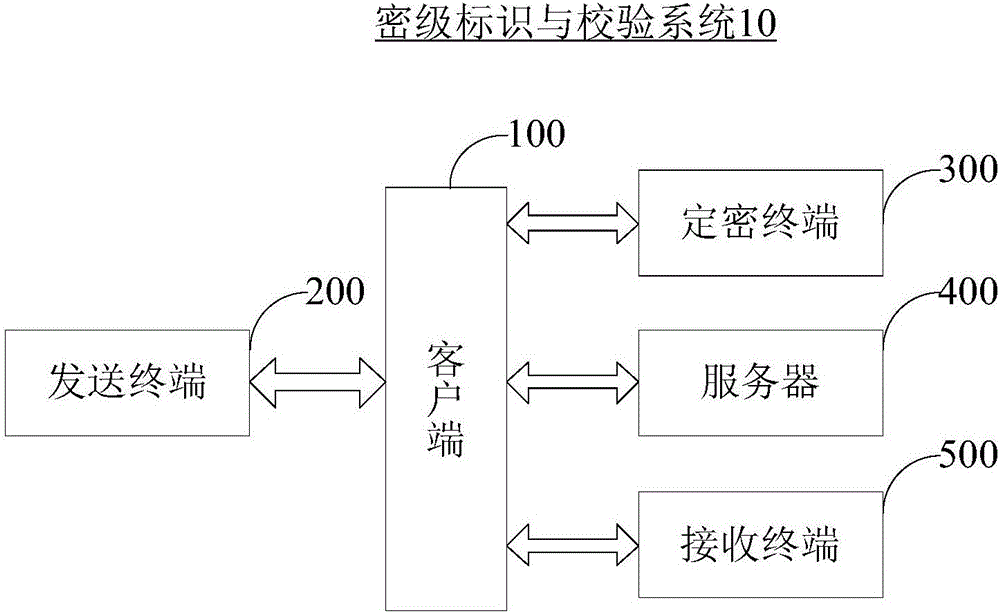
[0055] Please refer to Figure 7 , Figure 7 It is a flow chart of the secret level identification and verification method provided by the first embodiment of the present invention, and the method is applied to the secret level identification and verification system 10 . The specific flow of the confidentiality level identification and verification method will be described in detail below.
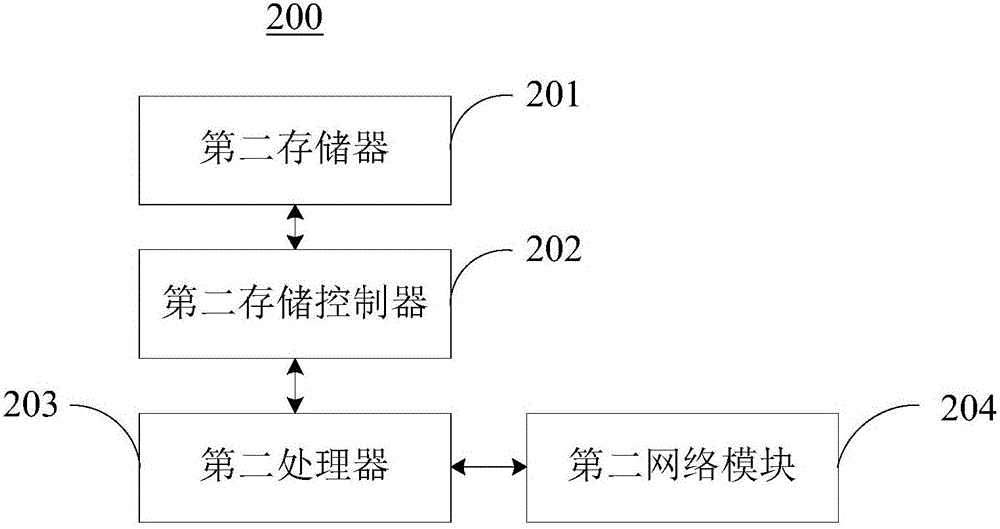
[0056] Step S110 , the sending terminal 200 responds to the file selection operation, and sends the selected file to the client 100 .
[0057] In this embodiment, the sending terminal 200 may include an input device (such as a mouse), and may also include an interactive interface for receiving a file selection operation. In the implementation of this embodiment, the interactive interface may be a touch screen. Wherein, the touch display screen may be a capacitive touch screen or a resistive touch screen supporting single-point and multi-touch operations. Supporting single-point and mul...
no. 2 example
[0081] Please refer to Figure 8 , Figure 8 It is a schematic flow chart of the confidentiality level identification and verification method provided by the second embodiment of the present invention. The method is applied to the client 100 communicating with the sending terminal 200 , the encryption terminal 300 and the server 400 . The specific flow of the confidentiality level identification and verification method is described below.
[0082] Step S210, receiving the file sent by the sending terminal 200 in response to the file selection operation, and judging whether the file has been encrypted.
[0083] Please refer to Figure 9 , Figure 9 for Figure 8 A schematic flowchart of the sub-steps included in step S210. The step S210 includes sub-steps S212 and S214.
[0084] The sub-step S212 is to calculate the hash digest of the file through a hash algorithm, and send the hash digest to the server 400 .
[0085] In the sub-step S214, the server 400 compares the re...
no. 3 example
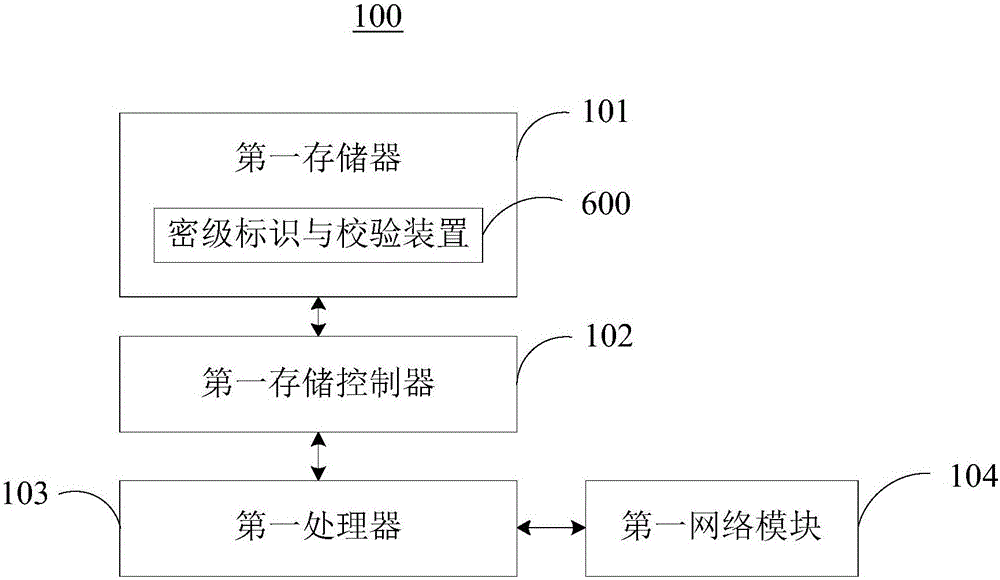
[0108] Please refer to Figure 14 , Figure 14 It is a schematic block diagram of the confidentiality identification and verification device 600 provided by the third embodiment of the present invention. The confidentiality identification and verification device 600 includes:
[0109] A receiving query module 610, configured to receive the file sent by the sending terminal 200 in response to the file selection operation, and query the encryption status of the file;
[0110] An encryption module 620, configured to encrypt the file through the encryption terminal 300 when the file is not encrypted;
[0111] The verification module 630 is configured to obtain the file encryption level of the file through the server 400 when the file has been encrypted, and verify the file according to the file encryption level.
[0112] In this embodiment, the receiving query module 610 receives the file sent by the sending terminal 200 in response to the file selection operation, and the way ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com