Solution method for coping with information center network malicious content transmission
An information-centric network and solution technology, which is applied in the field of segmented forwarding strategies for content targets, can solve problems such as reducing network service quality, congestion, and reducing user experience, so as to achieve the effect of ensuring service quality and avoiding waste
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
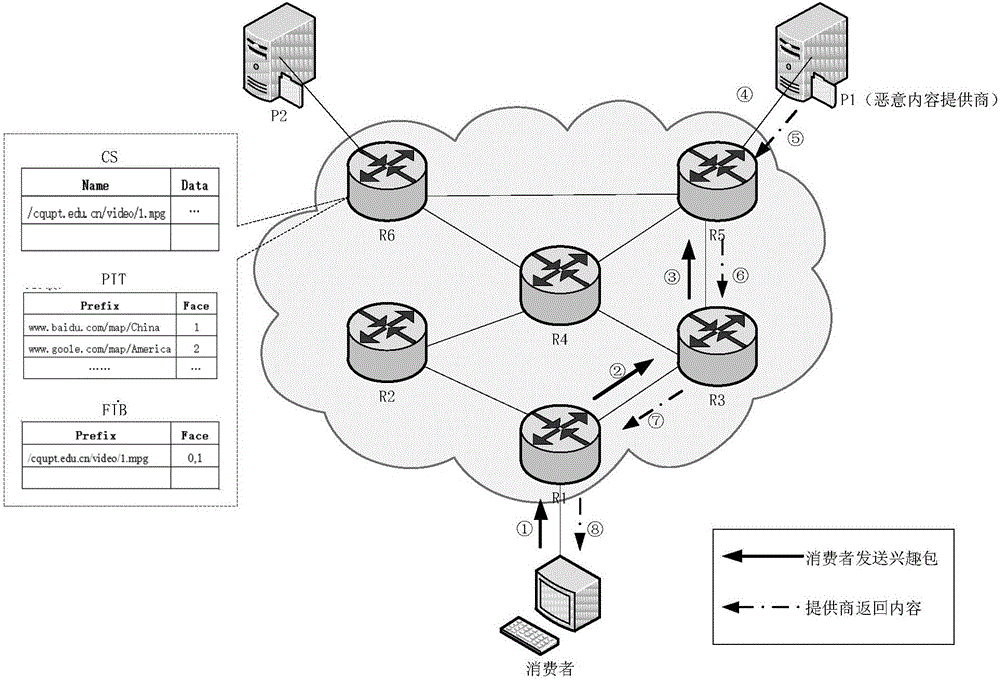
[0051] image 3 Shown is the CCN communication topology. As shown in the figure, the solid line arrow on the link marks the sending process of the user interest packet, the dotted line arrow marks the process of the content provider replying to the content object, and R1, R3, and R5 are intermediate routers on the transmission path.
[0052] Step 301: The consumer sends a request ① to the network and reaches the router R1. R1 adds the request information in the PIT table, and forwards the request interest packet to the upstream node ②→④ according to the FIB.
[0053] Step 302: After receiving the Interest packet, the malicious content provider P1 copies the HopLimit value in the Interest packet, and discards the Interest packet. P1 forges the content object and adds the copied HopLimit value to the content object, then signs it with the correct public key, forwards the signed content object to the next hop ⑤ according to the reverse path of the original route, and the content...
Embodiment 2
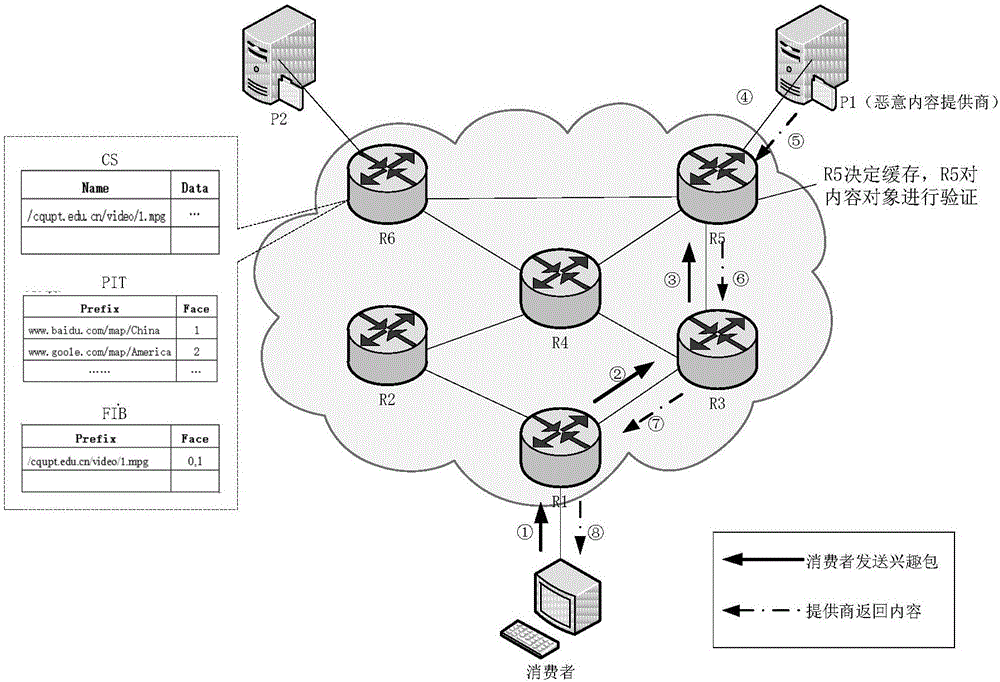
[0060] Figure 4 Another case of network operation.
[0061] Step 401: The consumer sends a request to the network, and the intermediate router forwards the Interest packet to the content provider P1①→④.
[0062] Step 402: After receiving the Interest packet, the malicious content provider P1 copies the HopLimit value in the Interest packet, and discards the Interest packet. P1 forges the content object and adds the copied HopLimit value to the content object, then signs it with the correct public key, and returns the signed content object according to the original route ⑤→⑦.
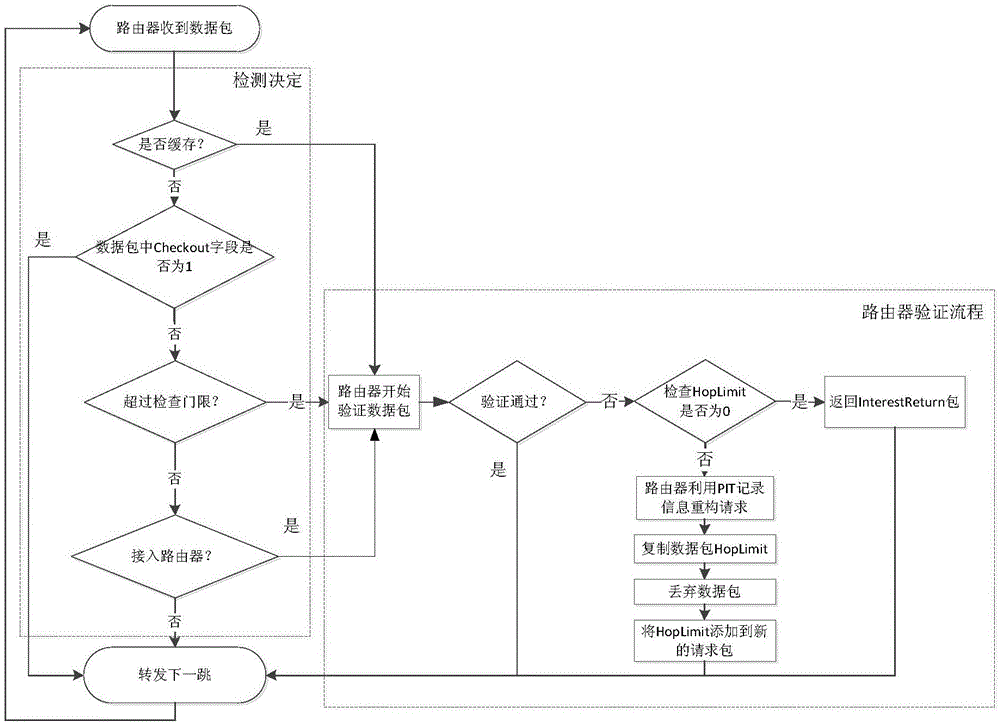
[0063] Step 403: R1 checks the received content object. At this time, the value of the Checkout field is 0, and the consumer access router R1 is responsible for verifying the content object.
[0064] (1) If the signature of R1 is verified as sending the data packet to the user through R1;
[0065] (2) If the signature verification result of R1 fails and the content object HopLimit is 0, R1 discards t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com