File encryption and decryption method and device
A file encryption and encryption password technology, applied in the field of data security, can solve problems such as unsatisfactory requirements
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
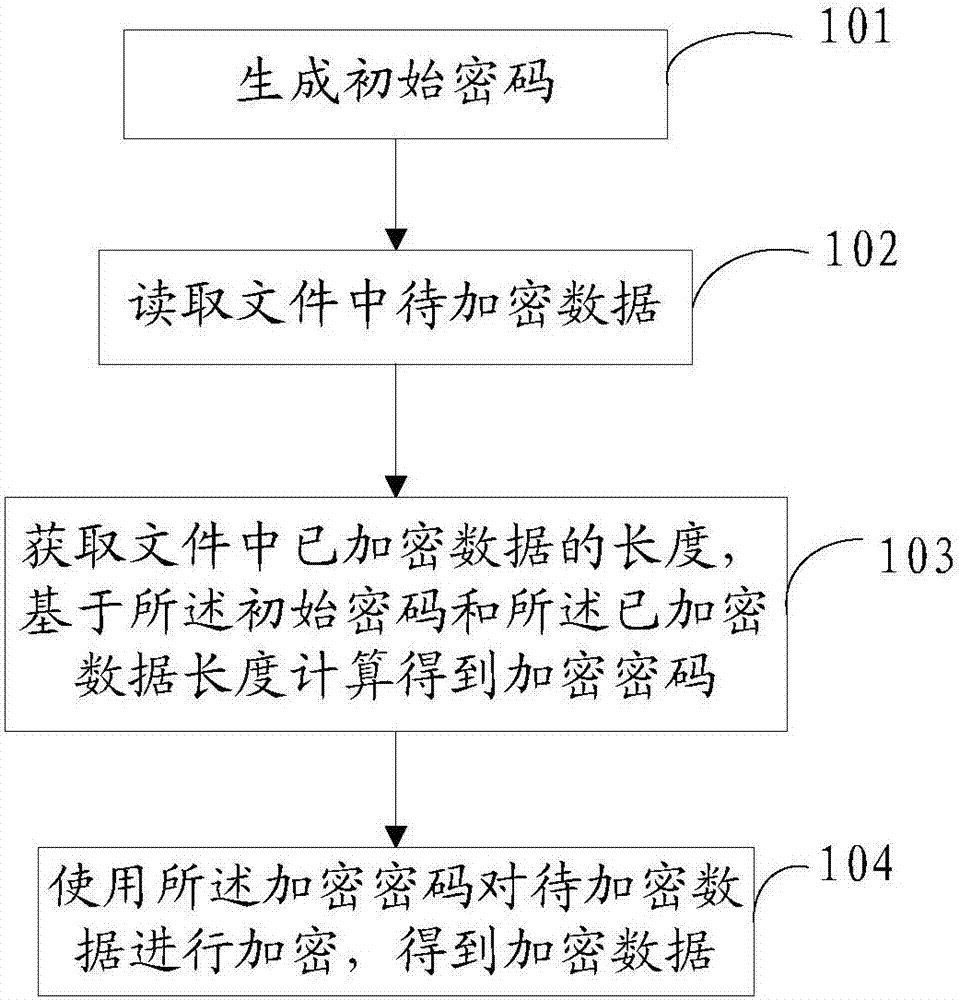
[0066] see figure 1 As shown, the first embodiment of the present invention provides a file encryption method, including steps 101 to 104, which are described in detail as follows.
[0067] Step 101: Generate an initial password.
[0068]The initial password is used to generate an encrypted password. In the embodiments of the present invention, the initial password can be a single number or an array, which can be random or fixed. In some preferred embodiments, in order to improve security , the initial password can be generated with the help of a random function. Further, in order to increase the difficulty of password cracking, the initial password is an array containing multiple elements generated with the help of a random function.
[0069] Furthermore, for subsequent decryption operations, the initial password needs to be saved.
[0070] Step 102: Read the data to be encrypted in the file.
[0071] In the embodiment of the present invention, when reading the data to be ...
no. 2 example
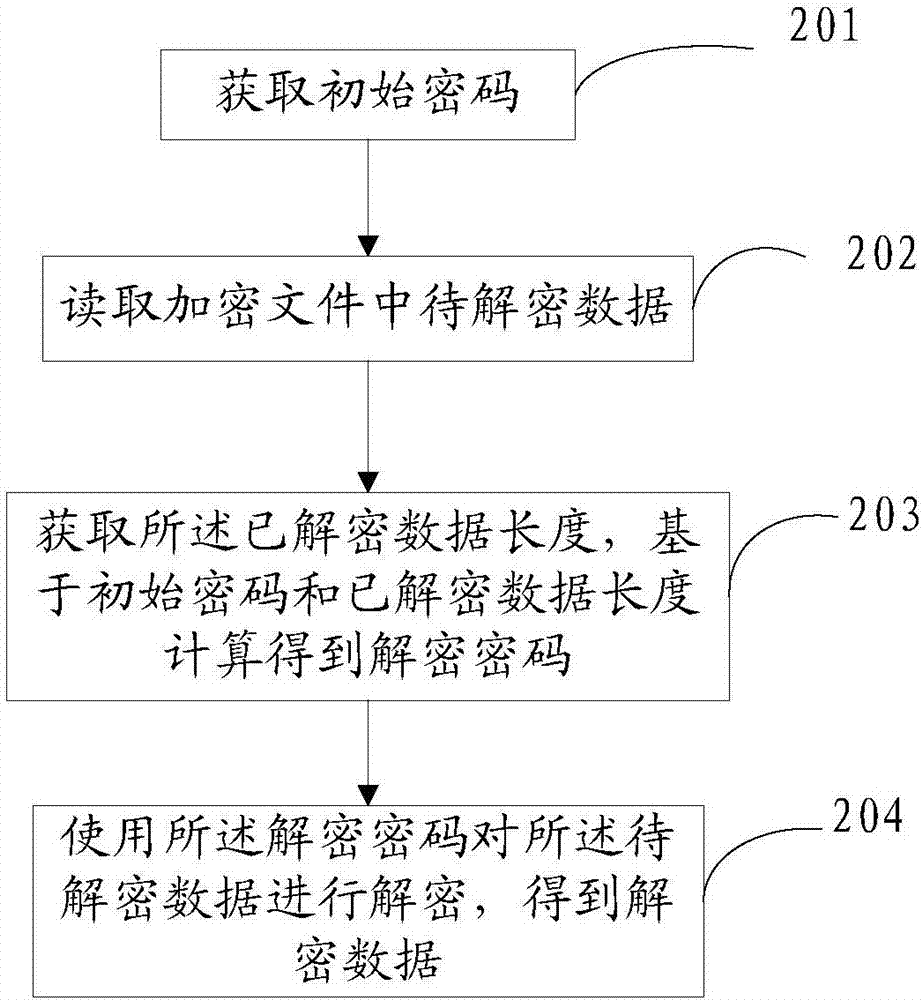
[0091] see figure 2 As shown, the second embodiment of the present invention provides a method for decrypting an encrypted file, including steps 201 to 204, which are described in detail as follows.
[0092] Step 201: Obtain an initial password.
[0093] Specifically, the same initial password used for encryption needs to be used for decryption. In this step, the initial password can be obtained by reading from the storage path of the initial password for encryption. The initial password can be obtained by other means. The technical means used are: It is well known to those skilled in the art, so it will not be repeated here.
[0094] Step 202: Read the data to be decrypted in the encrypted file.
[0095] Since the way of reading the data to be decrypted will affect the generation of the decryption password, in this embodiment, the way of reading the data to be decrypted is the same as the way of reading the data to be encrypted when encrypting the file.
[0096] Step 203:...
no. 3 example
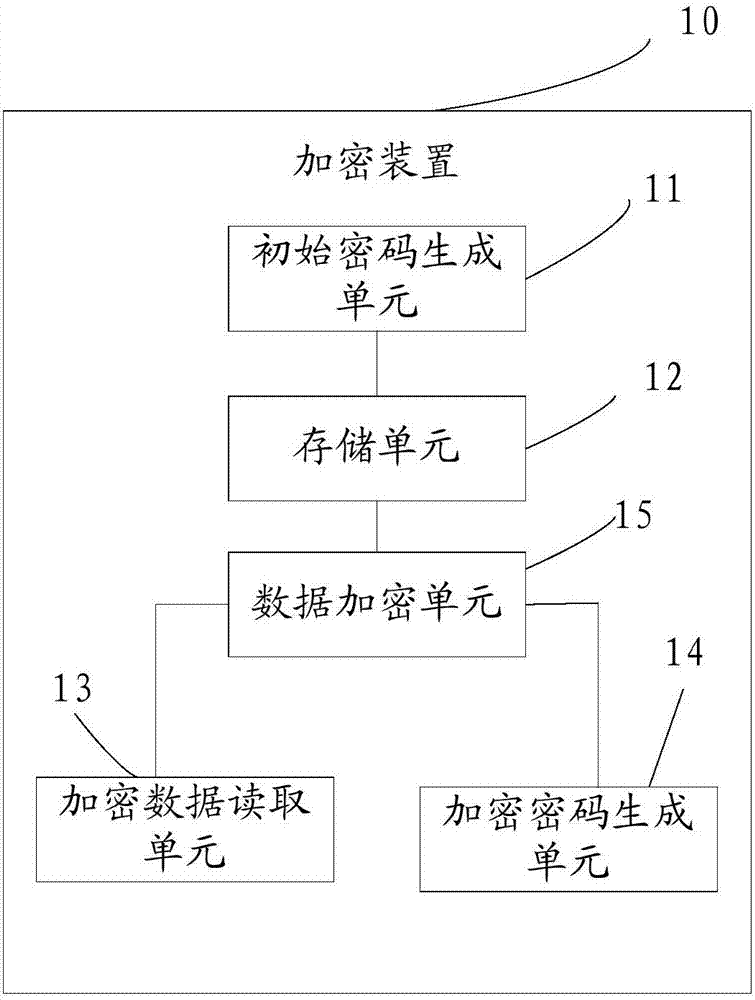
[0104] see image 3 As shown, the third embodiment of the present invention provides a file encryption device, and figure 1 The file encryption method shown corresponds to the details of the file encryption method in the first embodiment, and achieves the same effect. Described file encryption device 10 comprises initial password generating unit 11, storage unit 12, encrypted data reading unit 13, encrypted password generating unit 14, data encryption unit 15, wherein initial password generating unit 11 is connected to storage unit 12, encrypted password generation The unit 14 is connected to a data encryption unit 15 , and the data encryption unit 15 is connected to the storage unit 12 and the encrypted data reading unit 13 .
[0105]Specifically, the initial password generating unit 11 is configured to generate an initial password and store the initial password in the storage unit 12 .
[0106] In the embodiment of the present invention, the initial password can be a singl...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com