Safe charging method for bike sharing based on safe position proof
A technology for sharing bicycles and secure locations, applied in secure communication devices and key distribution, can solve the problems that location privacy information cannot be strictly protected and users cannot be obtained.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
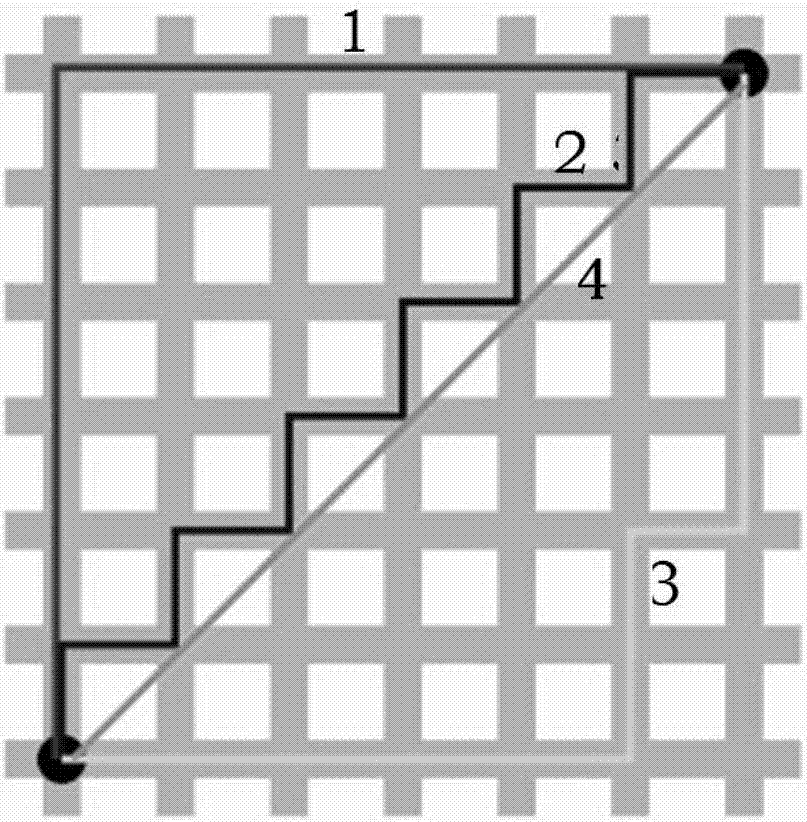
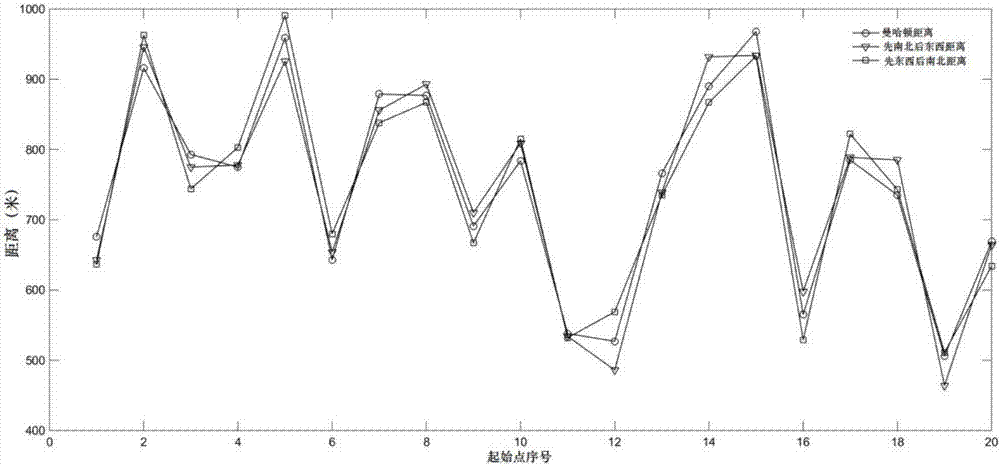
Image
Examples
Embodiment Construction
[0035] A description of the model involved in the present invention, the security goal and the problem to be solved will be given below.
[0036] 1. System model
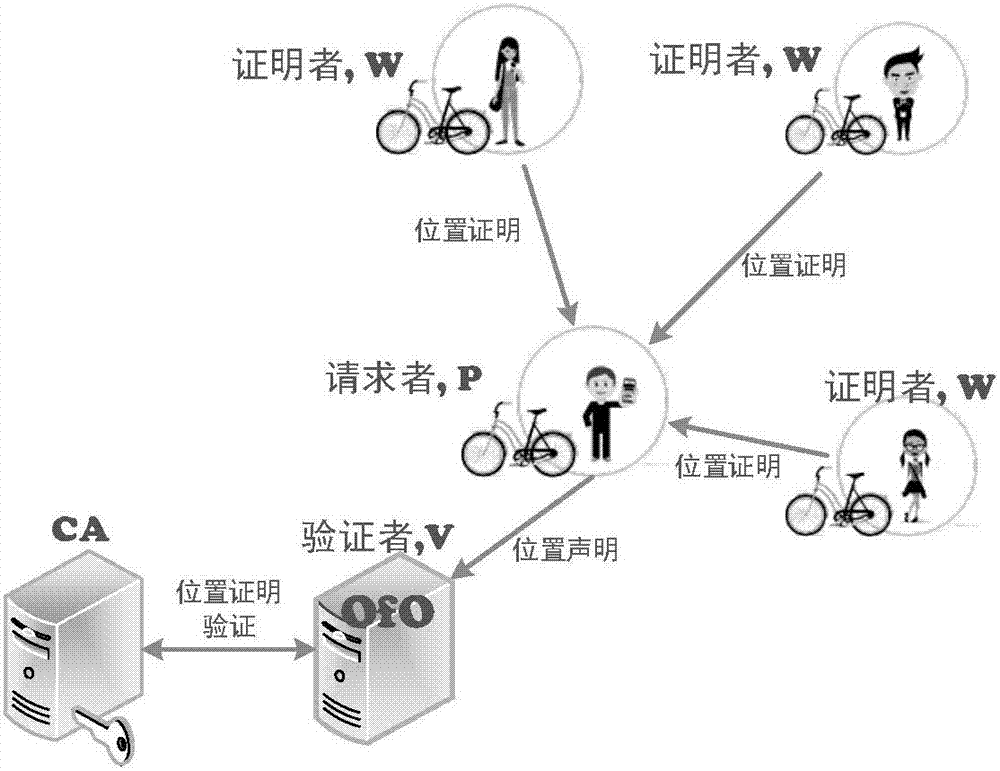
[0037]The structure of the shared bicycle billing system model constructed by the present invention is shown in figure 1 , when the user needs a car, first obtain the location certificate from other users in the surrounding environment when using the car, and then inform the shared bicycle operator of the location certificate, and the shared bicycle operator verifies the authenticity of the location certificate to confirm the user's use track. More specifically, there are four types of entities in the system, which are: (1) users, when they want to generate a location proof, the user is called a location proof (Location Proof, LP) requester (Prover), denoted as a requester P; When generating a location proof for others, the user is called the location proof issuer (Witness), which is denoted as the issuer W; (2) t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com