Method for verifying RFID label group
A RFID tag and tag technology, applied in the field of RFID security communication, can solve the problems of poor scalability and low efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] specific implementation plan
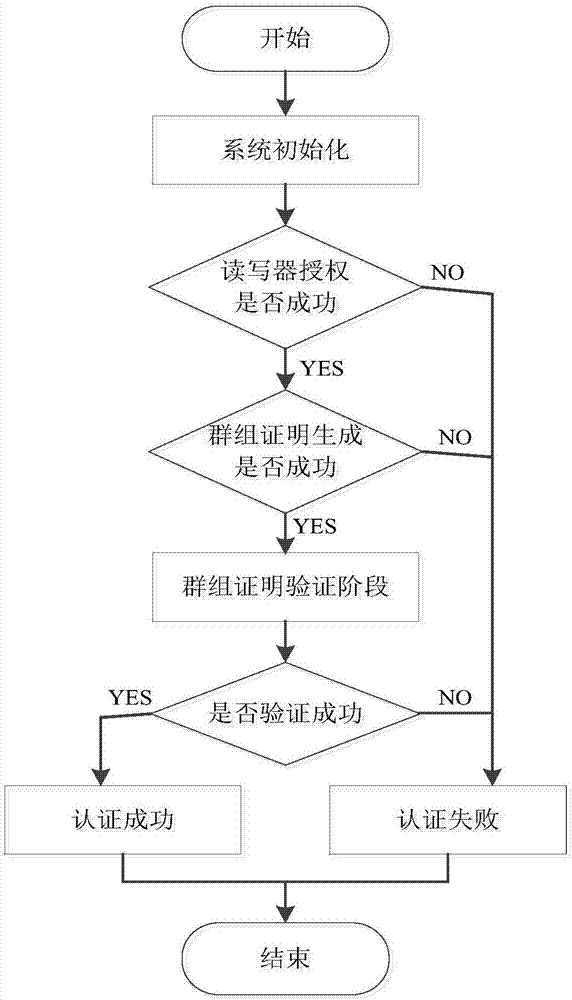
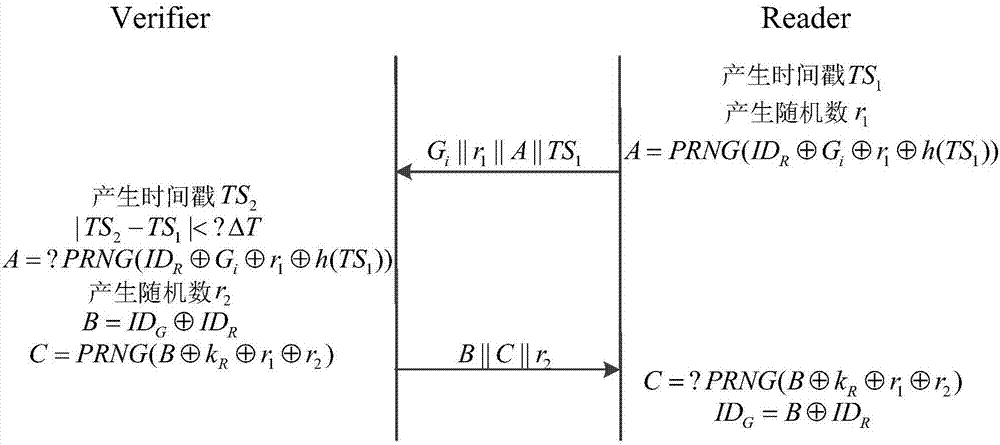
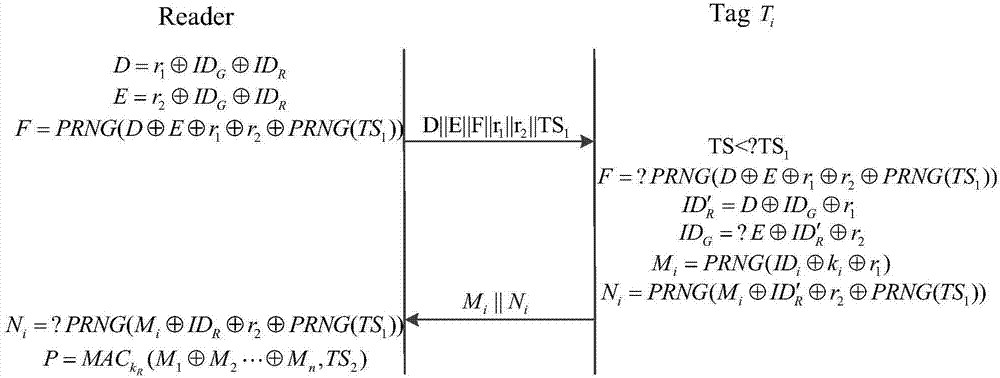
[0021] The invention is aimed at a tag group certification method under the RFID system environment, and the system includes a verifier, a reader-writer and multiple tags. The communication process between entities uses ciphertext to transmit messages, which ensures the security of sensitive information. The invention uses time series TS and threshold ΔT to control a round of communication session period, which can not only effectively resist common attack types, but also prevent the reader from waiting and receiving tag messages without limit. In addition, the group ID sharing technology is used to realize the independence of the tag reading sequence, avoiding the forwarding of communication messages between the reader and multiple tags, thereby improving the system efficiency.
[0022] First, initialize the RFID automatic identification system, the specific steps are as follows:
[0023] Store a set of tuple information (ID G ,ID i ,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com