A network protection method, device and system
A network and network access technology, applied in the transmission system, electrical components, etc., can solve problems such as not being able to meet the pace of rapid business development
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
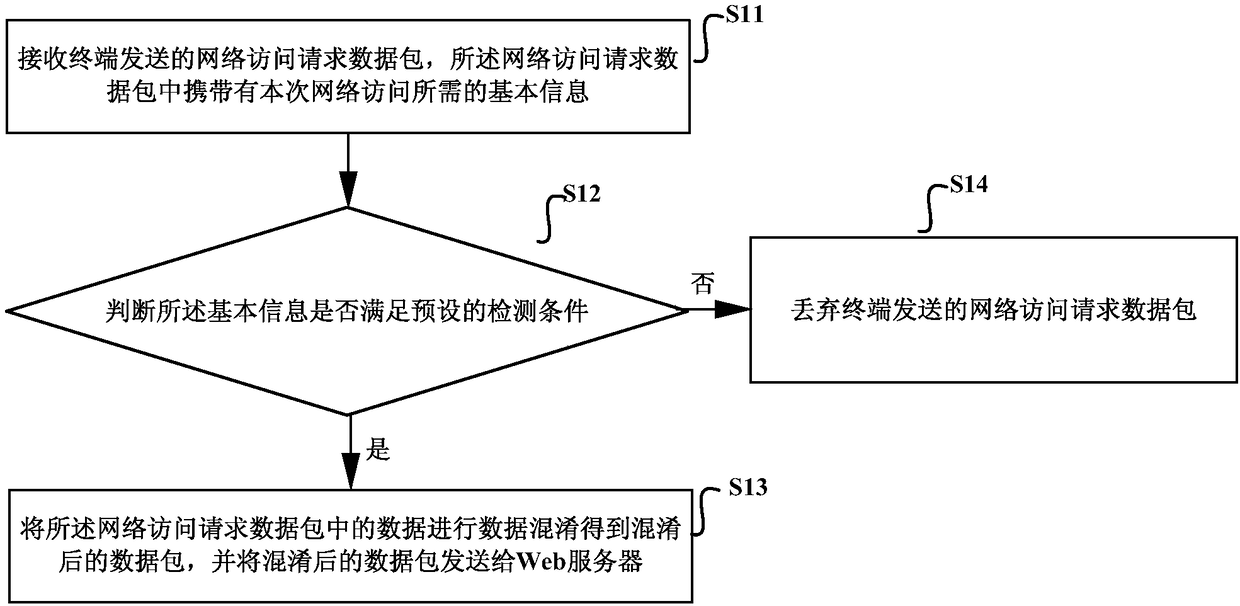
[0089] Such as Figure 1a As shown, it is a schematic diagram of the implementation flow of the network protection method provided by Embodiment 1 of the present invention, which may include the following steps:
[0090] S11. Receive a network access request packet sent by the terminal, where the network access request packet carries basic information required for this network access.
[0091] Specifically, when a user logs in to a browser in a terminal to access any website, the access process in the prior art is to directly send the network access request to the web server, while the embodiment of the present invention sends the network access request data The packet is sent to the network protection server, and the network protection server verifies and processes the network access request data packet. After the verification is passed, the data packet is processed and sent to the web server, which provides active security protection for various services and protects the term...
Embodiment 2
[0155] Based on the same inventive concept, the embodiment of the present invention also provides a network protection device. Since the problem-solving principle of the above-mentioned device is similar to the network protection method, the implementation of the above-mentioned device can refer to the implementation of the method, and the repetition will not be repeated.
[0156] Such as Figure 6 As shown, it is a schematic structural diagram of a network protection device provided in Embodiment 2 of the present invention, including a receiving unit 61, a judging unit 62, and a data obfuscation unit 63, wherein:
[0157] The receiving unit 61 is configured to receive a network access request packet sent by the terminal, the network access request packet carrying basic information required for this network access;
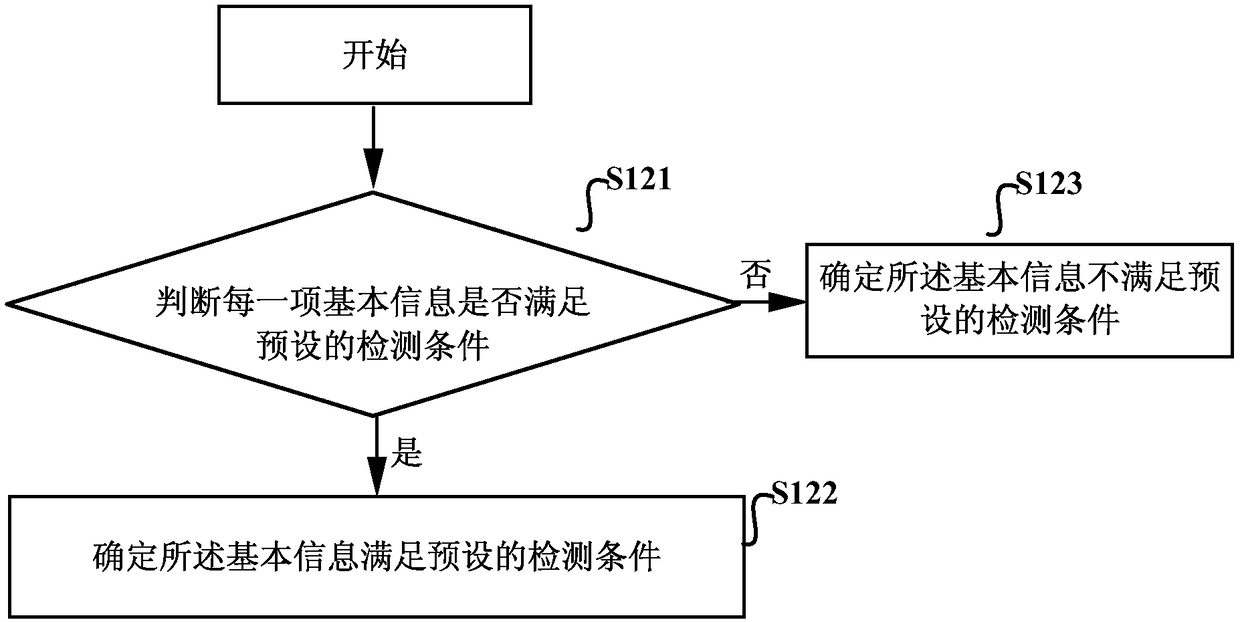
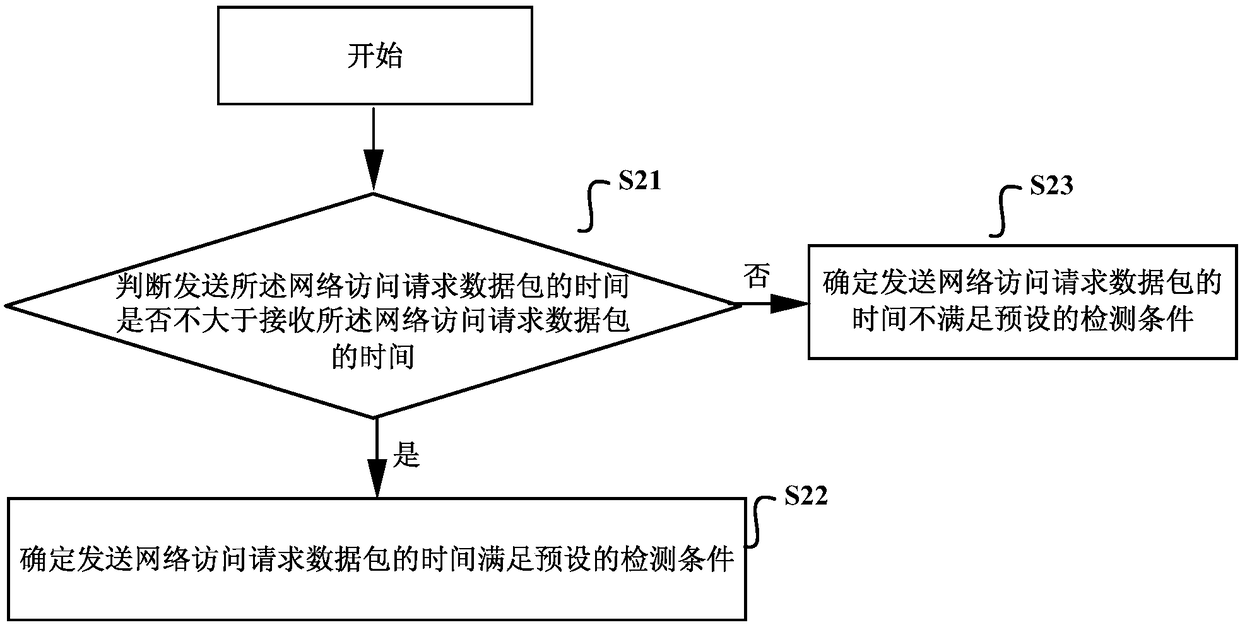
[0158] A judging unit 62, configured to judge whether the basic information satisfies a preset detection condition;
[0159] A data obfuscation unit 63, configured...
Embodiment 3
[0185] Such as Figure 7 As shown, it is a schematic structural diagram of the network protection system provided by Embodiment 3 of the present invention, including at least one terminal 71, a network protection server 72 and a webpage Web server 73, wherein the network protection server is provided with the Network guard. For each terminal, the active defense process is as follows:
[0186] The terminal 71 is used to send the network access request data packet to the network protection server 72. Prior to this, in order to ensure the security of the data packet, the intelligent password key 74 is used to encrypt the network access request data packet. After the encryption is completed, , sending a network access request packet to the network protection server 72.
[0187] The network protection server 72, after receiving the network access request data packet sent by the terminal 71, judges whether the basic information carried in the network access request data packet sat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com