Safety emergency response method and system based on analytic hierarchy process
An analytic hierarchy process and emergency response technology, applied in the field of information security, can solve problems such as the inability to clearly provide emergency response plans, unclear risk ratings, and complex calculations of risk assessment algorithms
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
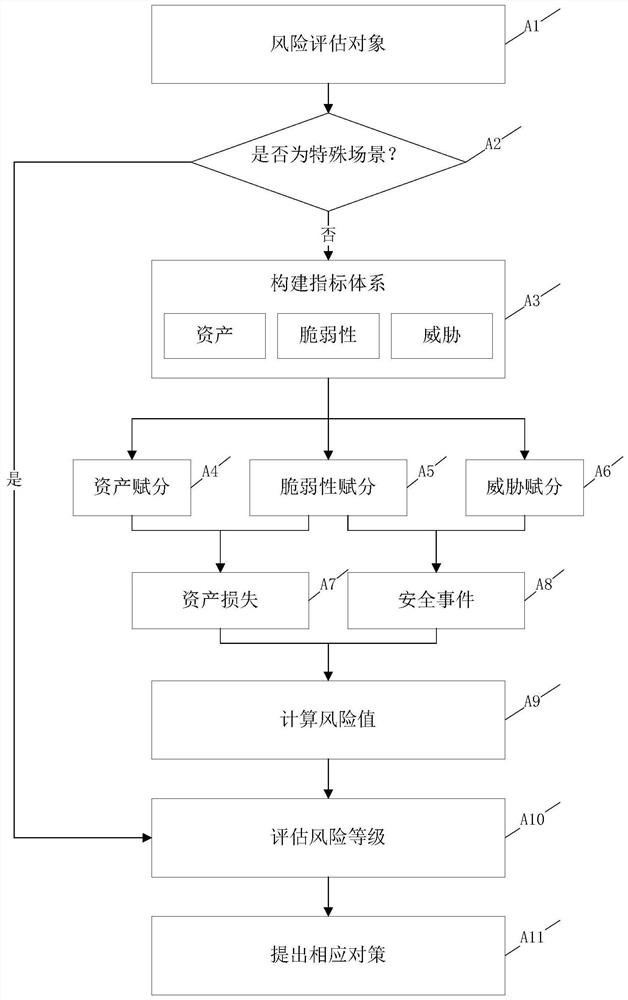
[0079] Such as figure 2 As shown, the safety emergency response method based on the analytic hierarchy process in this embodiment 1 specifically includes the following steps:
[0080] Step A1: Determine the risk assessment object;
[0081] Step A2: Determine whether the risk assessment object is in a special scene, if so, go directly to step A11 for risk level assessment, otherwise go to step A3;
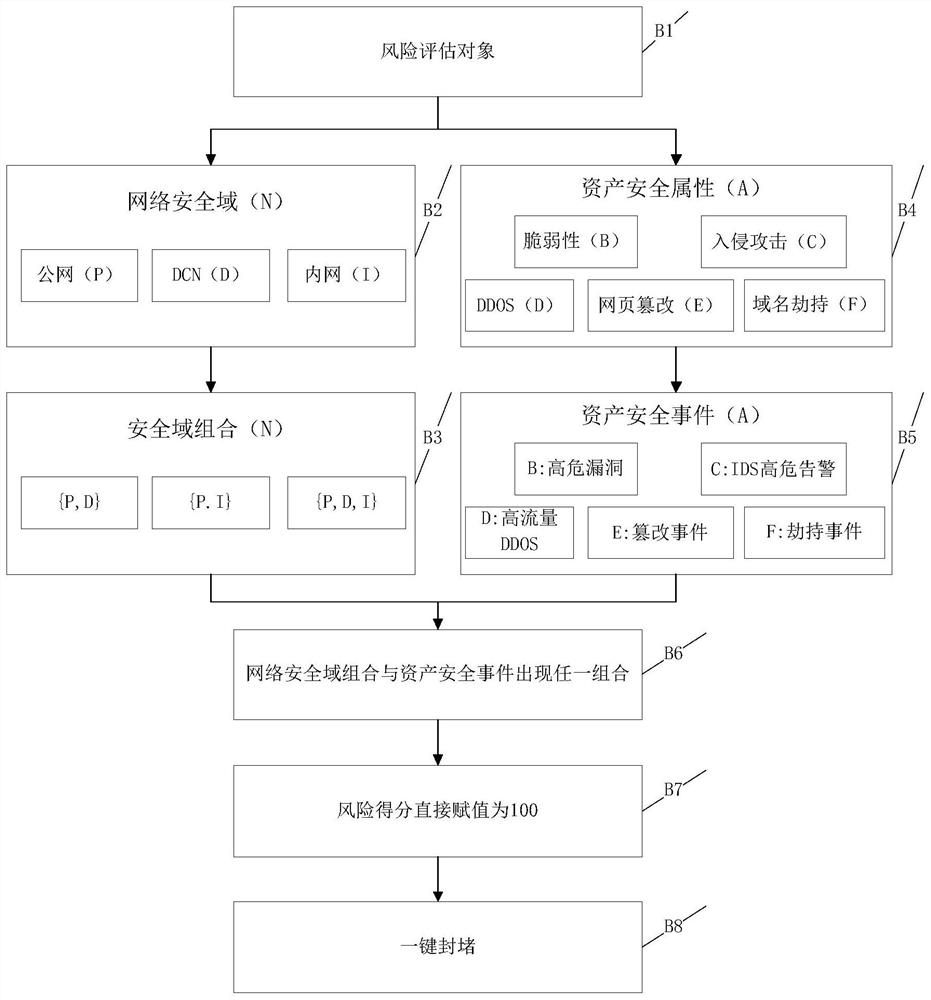
[0082] Among them, referring to Table 1, the judgment indicators for special scenarios include network security domain and asset security attributes. The network security domain includes three secondary indicators of the public network, DCN, and intranet, and its risk portfolio includes three combinations of {public network, DCN}, {public network, intranet}, and {public network, DCN, intranet}. The combination mainly considers the impact on intranet assets after being attacked in the direction of the public network; asset security attributes include five secondary indicators of v...
Embodiment 2
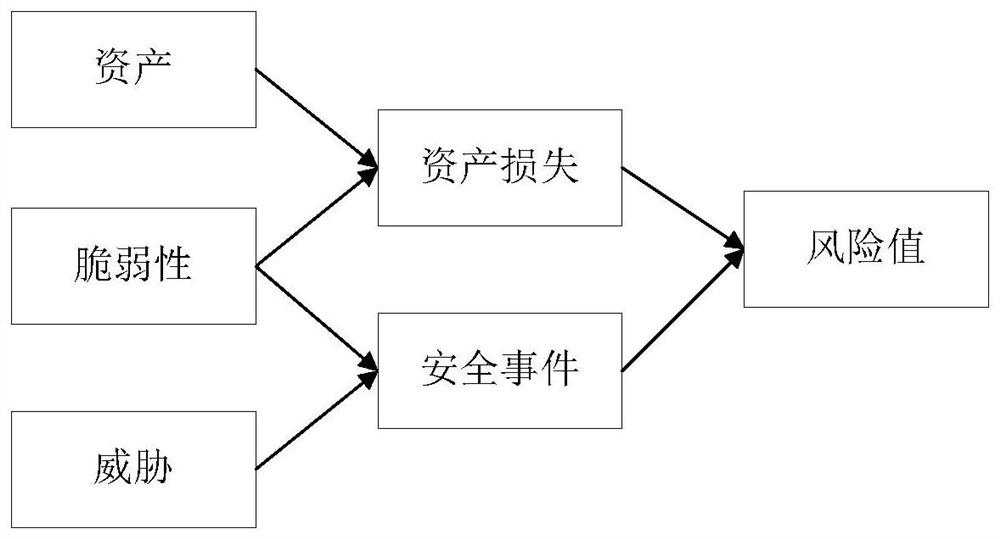
[0181] Such as Figure 7 As shown, the present invention is based on the AHP-based security emergency response method, and also designs a security emergency response system based on the AHP, including a judgment module, an index construction module, an index assignment module, a calculation module, an evaluation module and a disposal module. The judgment module is used to judge whether the risk assessment object is in a special scene; the index construction module is used to construct the index system of assets, vulnerabilities and threats for the risk assessment object; The calculation module is used to calculate the scores of asset losses and safety incidents and obtain the corresponding risk value; the evaluation module is used to divide the risk level according to the size of the risk value; the disposal module is used to propose corresponding measures for different risk levels. Disposal countermeasures. The system has a simple structure and can respond to security incide...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com