Abnormal access detection method and device
A detection method and abnormal technology, applied in the Internet field, can solve the problems of inaccuracy and effectiveness, and insufficient use of data, and achieve the effect of ensuring stability and security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0068] As mentioned in the background technology, further improving the accuracy and effectiveness of outlier detection is a key issue related to the accurate and effective operation of the system in view of the characteristics of time-series application data, and it is also a technical problem to be solved by this application.
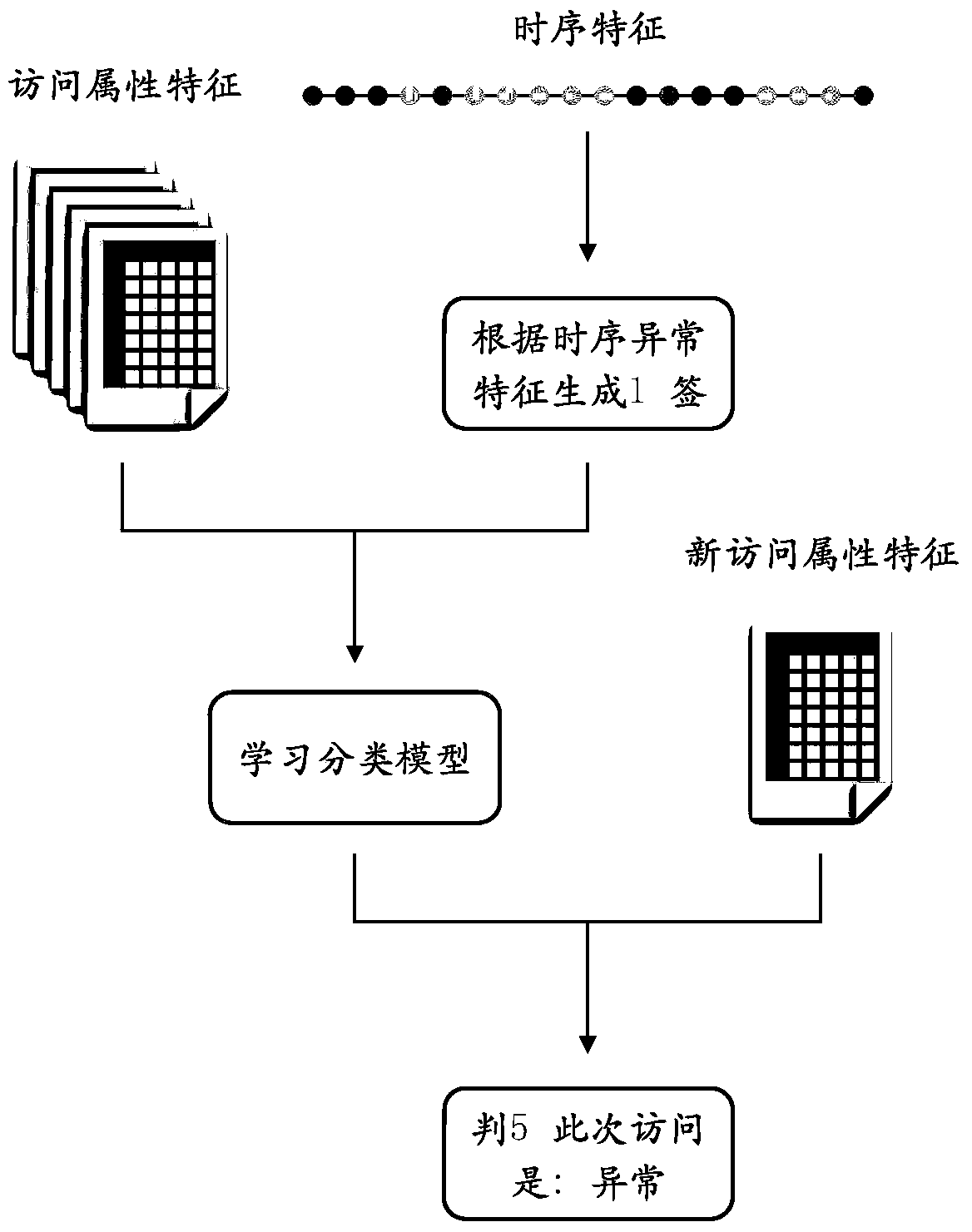
[0069] In order to solve the above technical problems, this application proposes an outlier detection method, which combines user statistical data and time-series access data, gives a preliminary label according to the rules through the time-series data, and adopts the method of logistic regression to analyze the preliminary label and user The attribute is trained to obtain the final result, so that the result of outlier judgment can be further improved.
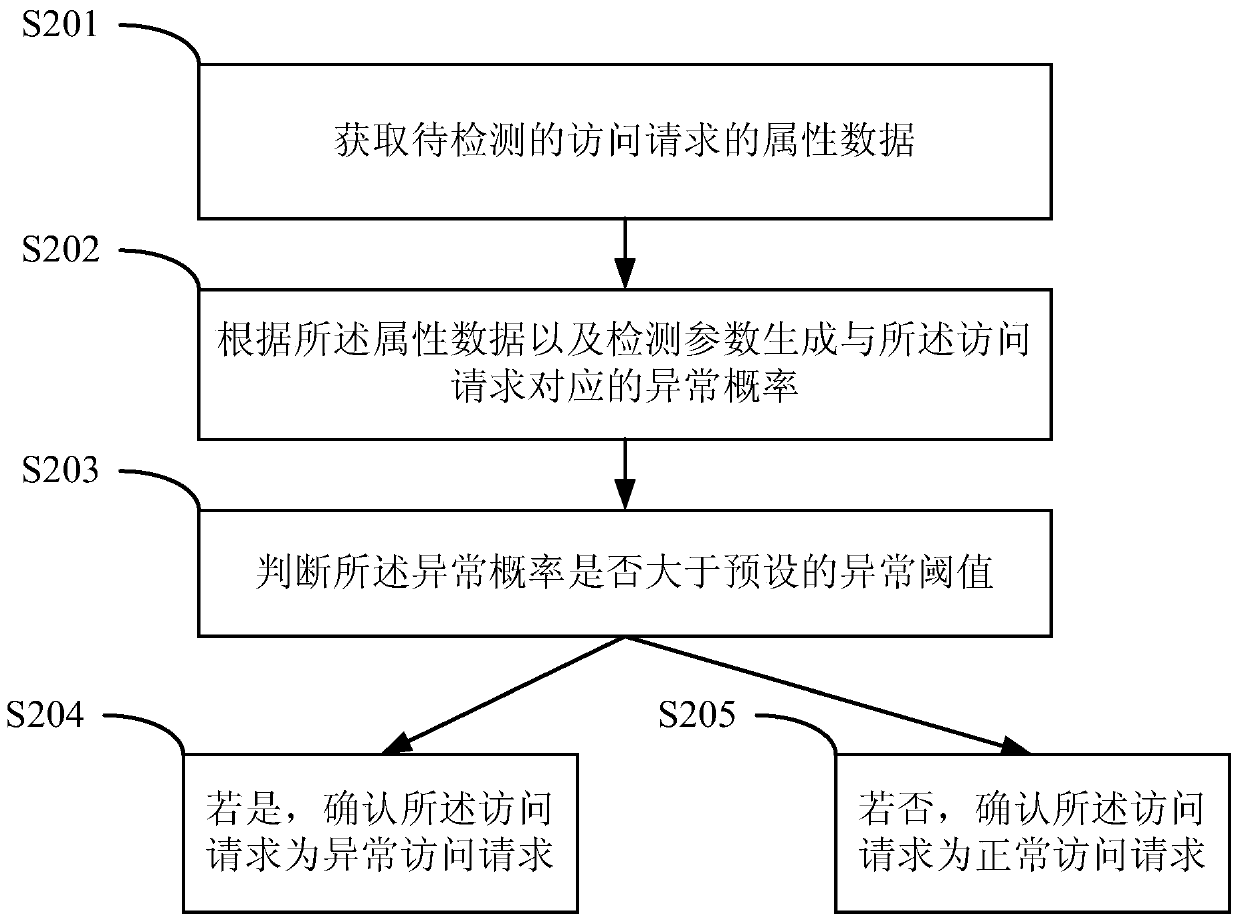
[0070] Such as figure 2 As shown, it is a schematic flow chart of an abnormal point detection method proposed in this application, which includes the following steps:
[0071] S201 Acquire attribu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com