Folder space monitoring and maintenance system and method for Unix-like system server
A system server, space monitoring technology, applied in the field of folder space monitoring and maintenance system, can solve problems such as single function, lack of FTP data transmission path, lack of compression/decompression operation path, etc., to achieve the effect of convenient use
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0062] A folder space monitoring and maintenance system for Unix-like system servers, including:
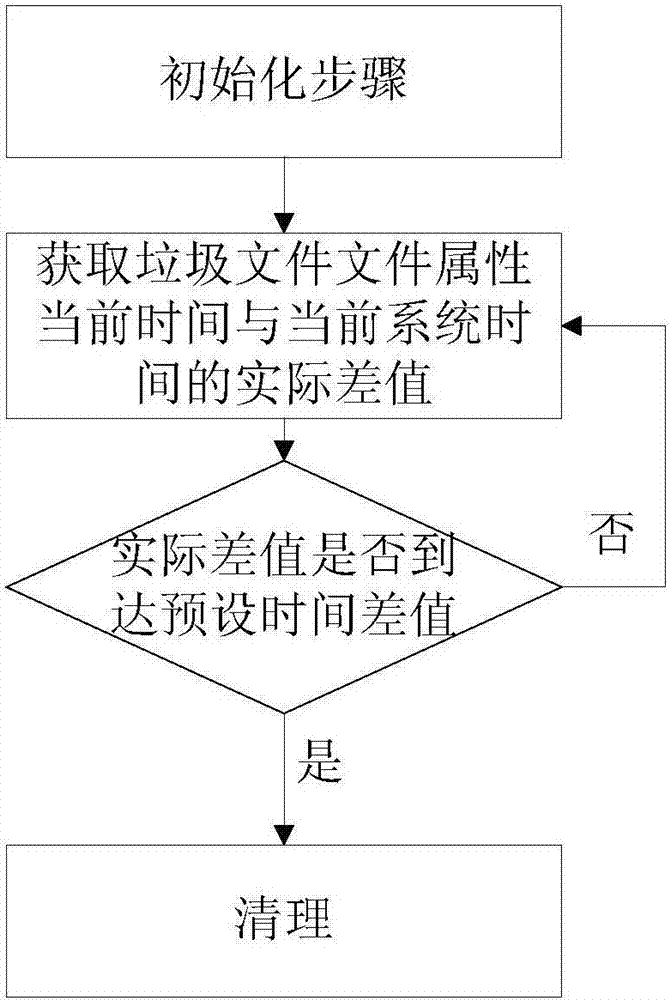
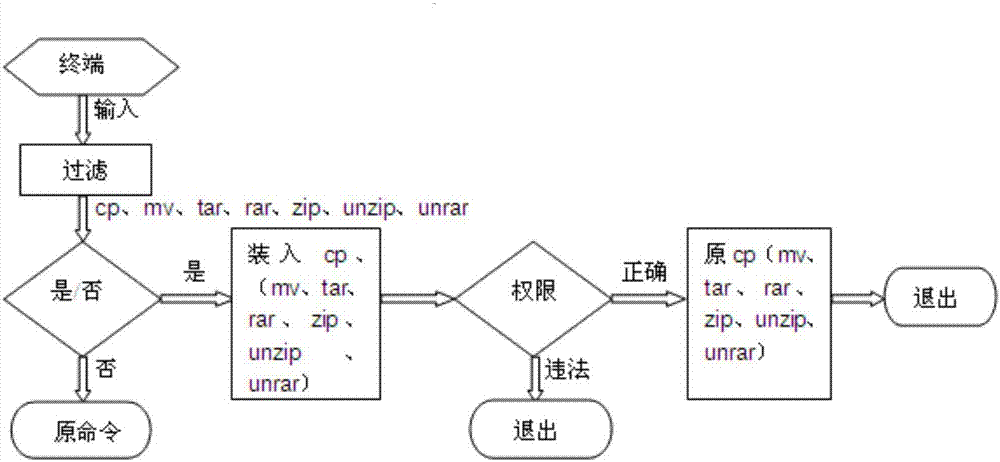
[0063] The authority management module is used to obtain the actual operation instruction input by the user, and when the actual operation instruction belongs to the restriction instruction, restrict the operation path of the actual operation instruction; the restriction instruction includes copy command, move command, compression command and decompression command. The cleaning module takes the set file type input by the user as a junk file, and cleans up the junk files in the folder with the path set by the user according to the time interval set by the user.
[0064] In this embodiment, the authority management module includes:
[0065] an instruction acquisition unit, configured to acquire the actual operation instruction input by the user;
[0066] an instruction screening unit, configured to send actual operation instructions belonging to restricted instructions to the judg...
Embodiment 2
[0152] A method for monitoring and maintaining a Unix-like system server, comprising: acquiring an actual operation instruction input by a user, and restricting the operation path of the actual operation instruction when the actual operation instruction is a restricted instruction; and using the set file type input by the user as a junk file , clean up the junk files in the folder with the path set by the user according to the time interval set by the user.
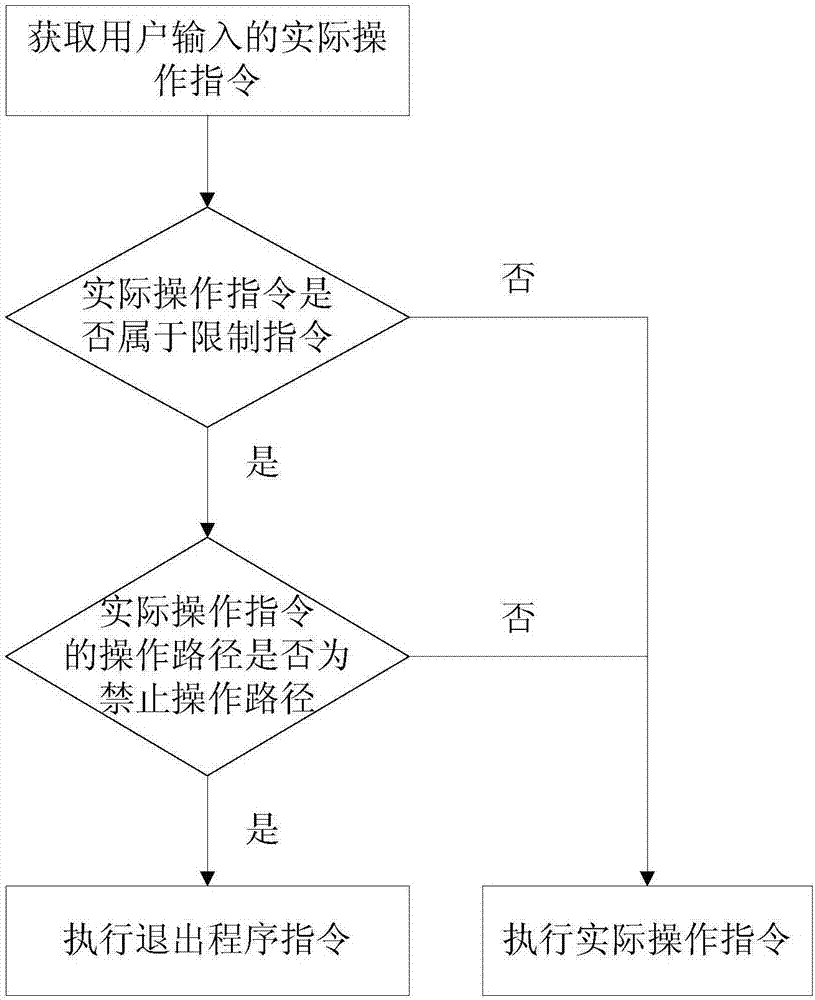
[0153] Obtain the actual operation instruction input by the user, and when the actual operation instruction belongs to the restriction instruction, restrict the operation path of the actual operation instruction, such as figure 1 shown, including:
[0154] Step S11, obtaining the actual operation instruction input by the user;
[0155] Step S12, judging whether the actual operation command is a restricted command, if yes, go to step S13, if not, go to step S14; the restricted commands include copy command, move command, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com