Distributed human face authentication information generation method, and distributed human face authentication method and apparatus
An authentication information and distributed technology, applied in the field of data processing, can solve problems such as difficulties in the widespread use of face recognition systems or devices, increased complexity of system deployment, and difficulties in collecting face databases
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
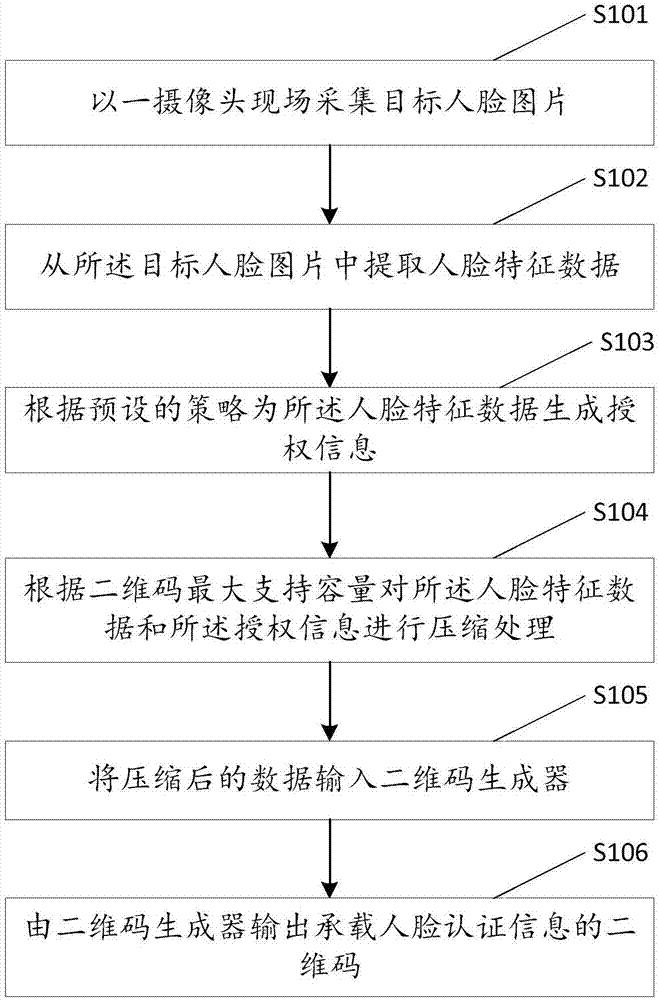
[0075] see figure 1 , the figure shows a method for generating distributed face authentication information, including steps:
[0076] Step S101: collecting target face pictures on-site with a camera;
[0077] Step S102: extracting face feature data from the target face picture;
[0078] Step S103: Generate authorization information for the facial feature data according to a preset policy;
[0079] Step S104: compressing the facial feature data and the authorization information according to the maximum supported capacity of the two-dimensional code;
[0080] Step S105: Input the compressed data into the two-dimensional code generator;
[0081] Step S106: The two-dimensional code generator outputs the two-dimensional code carrying the face authentication information.
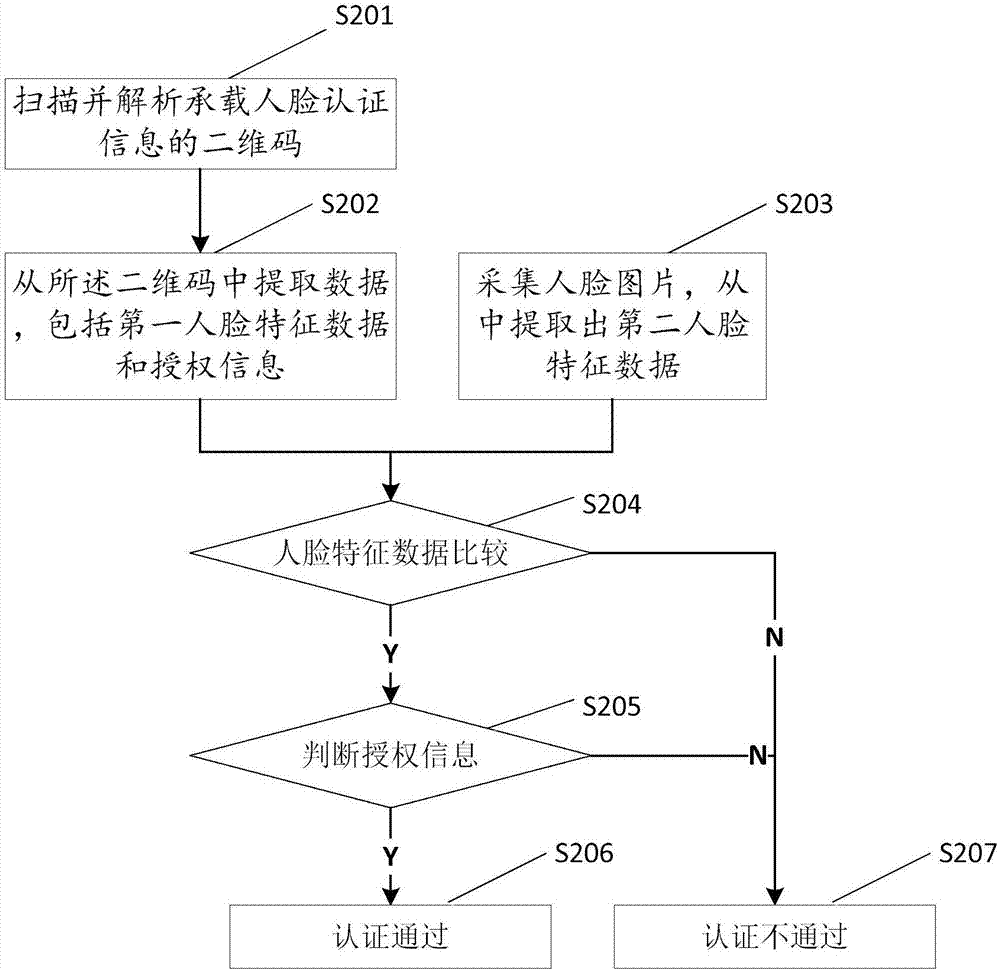
[0082] At present, a large number of mobile terminals are equipped with cameras, such as mobile phones, PADs, computers, etc. When users register through APP or web pages, they can conveniently collect face im...
no. 2 example
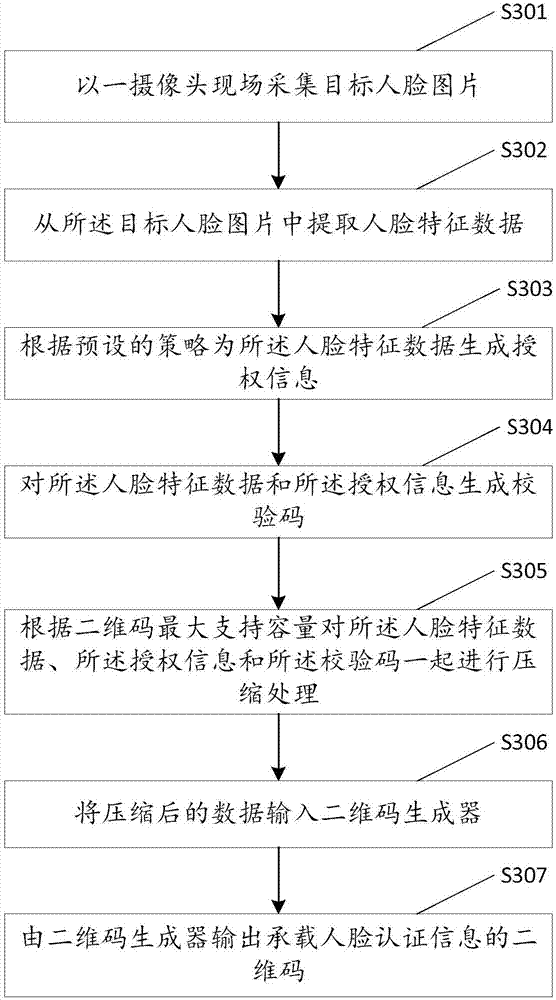
[0105] see image 3 , which shows another method for generating distributed face authentication information, including steps:
[0106] Step S301: collecting target face pictures on the spot with a camera;
[0107] Step S302: extracting face feature data from the target face picture;
[0108] Step S303: Generate authorization information for the facial feature data according to a preset strategy;
[0109] Step S304: generating a verification code for the facial feature data and the authorization information;
[0110] Step S305: Compress the facial feature data, the authorization information and the verification code together according to the maximum supported capacity of the two-dimensional code;
[0111] Step S306: Input the compressed data into the two-dimensional code generator;
[0112] Step S307: The two-dimensional code generator outputs the two-dimensional code carrying the face authentication information.
[0113] At present, a large number of mobile terminals are ...
no. 5 example
[0134] Corresponding to the above method, the embodiment of the present invention also provides a distributed face authentication information generation device, such as Figure 5 shown, including:
[0135] Image processor 501, for extracting face feature data from target face picture;
[0136] An authorization information distributor 502, connected to the image processor 501, configured to generate authorization information for the facial feature data according to a preset strategy;
[0137]A data compressor 503, connected to both the image processor 501 and the authorization information distributor 502, for compressing the facial feature data and the authorization information according to the maximum supported capacity of the two-dimensional code;
[0138] The two-dimensional code generator 504 is connected to the data compressor 503, inputs the compressed data, and outputs a two-dimensional code carrying face authentication information.
[0139] In another embodiment, a ch...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com