K-anonymity privacy protection method for track data in uncertain environment
A trajectory data and privacy protection technology, which is applied in digital data protection, electronic digital data processing, instruments, etc., can solve the problems that affect the effectiveness of privacy protection, data deviation, actual effect and efficiency are difficult to meet the requirements, and achieve effective trajectory anonymity Effects of privacy protection and semantic enhancement
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0043] In order to understand the technical scheme of the present invention more intuitively and completely, the non-limiting feature descriptions are as follows in conjunction with the accompanying drawings of the present invention:
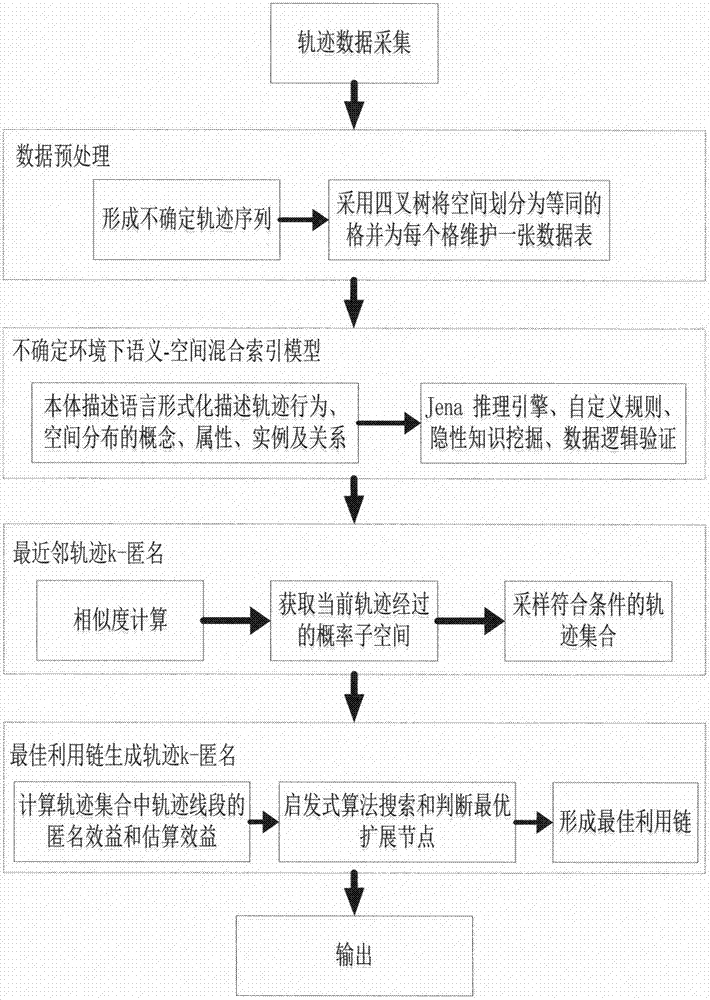
[0044] Such as figure 1 As shown, a trajectory data k-anonymous privacy protection method in an uncertain environment, including the following steps:
[0045] A: Trajectory data collection, the object of data collection is a large amount of mobile trajectory data generated by mobile police equipment, including location data, attribute data, time data and spatial relationship data stored in the spatial database, and the original trajectory in the data space database Decompose data into meaningful sequences and parse data in multivariate formats collected over different time periods;
[0046] B: Trajectory data preprocessing, dynamic data flow analysis is performed on the multi-format trajectory data obtained in different time periods, forming tr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com