Method for realizing network flow load balancing by utilizing consistency Hash strategy
A network traffic and load balancing technology, applied in the Internet field, can solve problems such as increased costs, restrictions, and cluster-wide jitter
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
[0045] Its specific implementation process of the embodiment of the present invention is as follows:
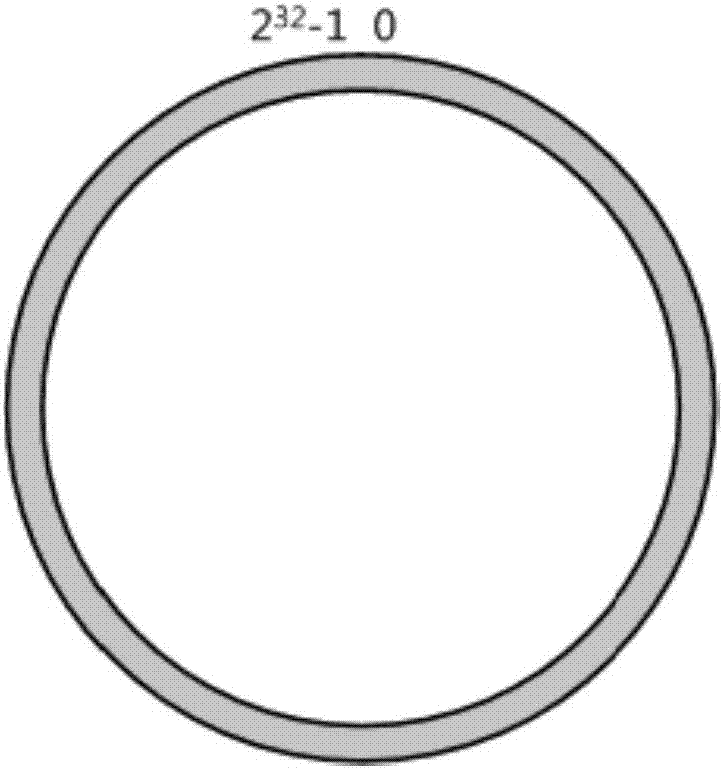
[0046] Such as figure 1 As shown, the consistent hashing strategy organizes the entire hash value space into a virtual ring, such as assuming that the value space of a certain hash function H is 0 to (2 32 -1) (that is, the hash value is a 32-bit unsigned integer):
[0047] The entire space is organized clockwise.
[0048] 0 and 2 32 -1 for direction coincidence in zero point.
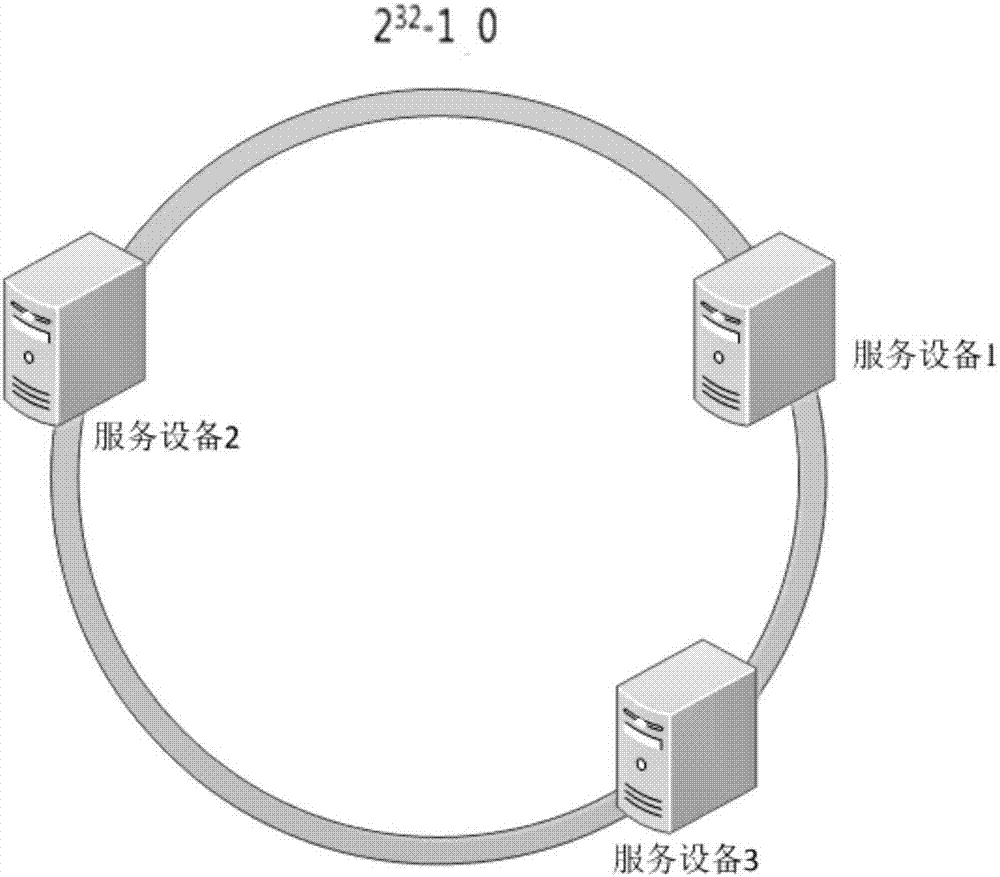
[0049] The next step is to use the Hash algorithm to perform a hash on each server. Specifically, you can choose the server's ip or hostname as a keyword for hashing, so that each machine can determine its position on the hash ring. It is assumed here that there are three service devices, and the positions in the ring space after hashing the ip addresses are as follows: figure 2 shown.
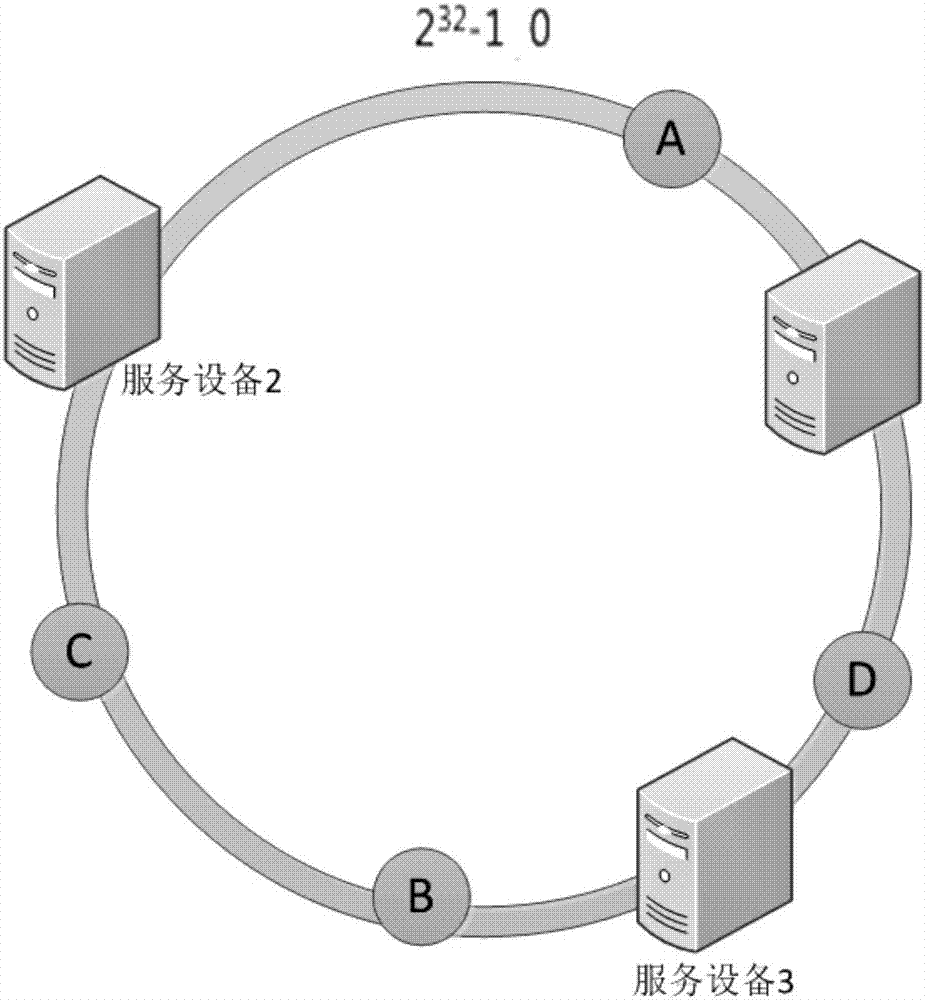
[0050] Next, use the following algorithm to locate the traffic access to the corresponding service device: u...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com