APT detection method and system based on invasion route
A threat detection and approach technology, applied in the field of APT threat detection, can solve the problems of difficult protection for the attacked, difficult detection of attack methods and methods, etc., and achieve the effect of convenient overall behavior, simple operation and easy use
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
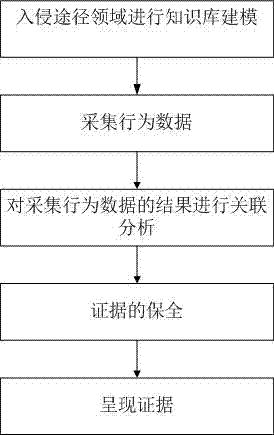
[0053] Such as figure 1 Shown is an APT threat detection method based on intrusion pathways, which includes:
[0054] S1: Carry out knowledge base modeling on the domain of intrusion pathways;
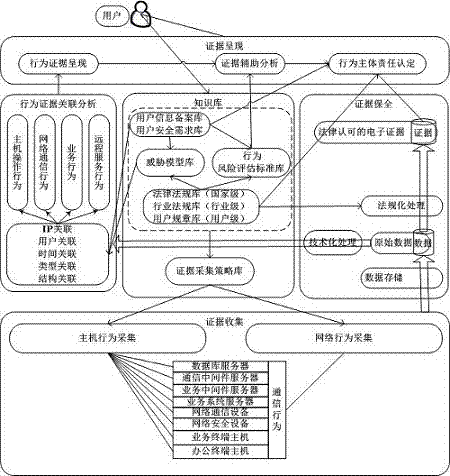
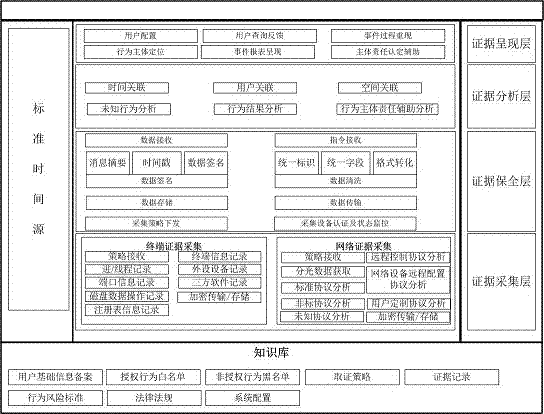
[0055] S2: Collecting behavior data, including collecting host behavior data and collecting network behavior data. The collected host behavior data includes collecting progress / thread information records, port information records, disk data operation records, system registry information change records, terminal System basic information update records, peripheral equipment connection and data transmission records, and third-party application program information records. The collection of network behavior data will first classify and mark the network behavior, and then restore the network behavior data, and record and track The operation and maintenance service information and external connection information of the network system, and finally save the data locally;
[0056] S3: Correla...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com