A data encryption and decryption scheduling method based on multi-card redundancy check
A technology of redundancy check and scheduling method, applied in the direction of electrical digital data processing, multi-program device, program control design, etc., can solve problems such as task failure, encryption and decryption failure, errors, etc., to reduce data error rate, The effect of improving parallel performance and system availability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
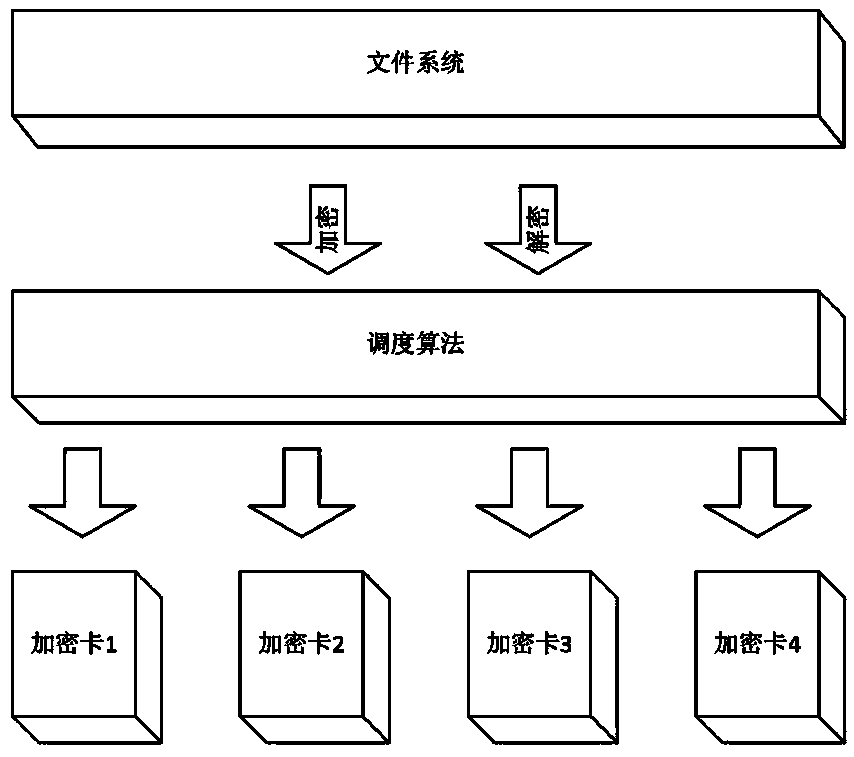
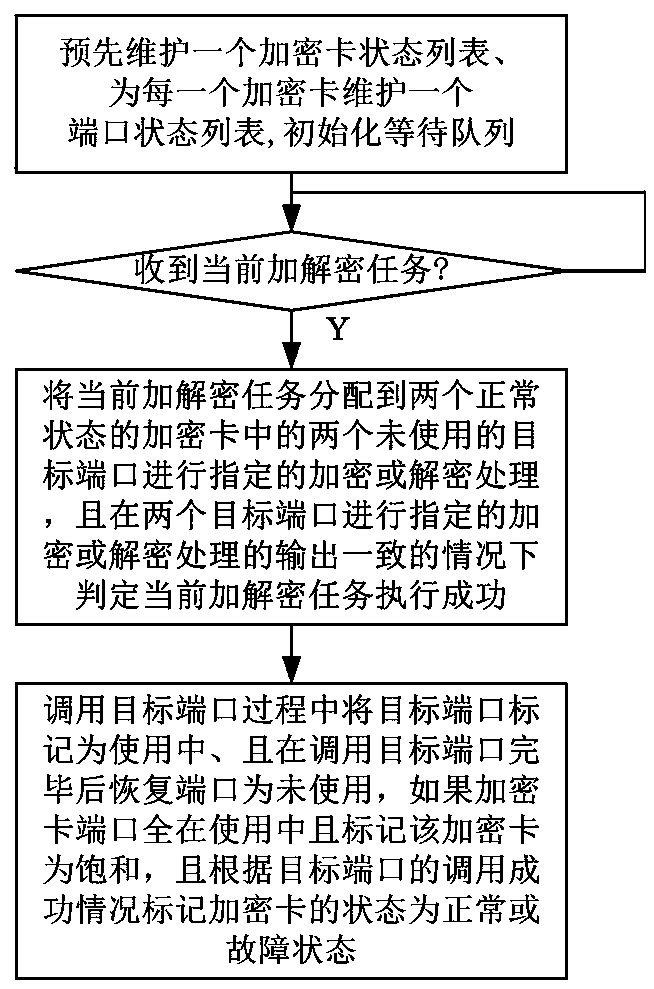
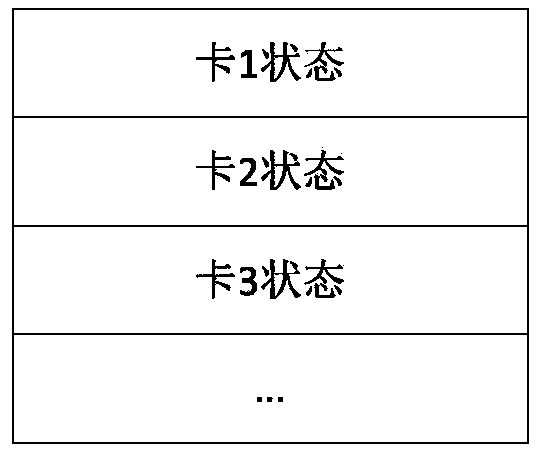
[0026] Such as figure 1 As shown, in this embodiment, the linux operating system including 4 encryption cards is taken as an example, and the data encryption and decryption scheduling method based on the multi-card redundancy check of the present invention is further described in detail. see figure 1 , the linux operating system file system driver scheduling algorithm module containing 4 encryption cards, the file system driver is the caller of the scheduling algorithm module, the scheduling algorithm module is the caller of the encryption card driver, and the encryption card driver is the original encryption card hardware The interface requires the caller to specify the card number and port number. The scheduling algorithm module is an example of using the data encryption and decryption scheduling method based on multi-card redundancy check in this embodiment. It shields the details of the encryption card from the upper layer caller and provides a single Encryption and decry...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com