An identification method and terminal
An identity recognition and terminal technology, applied in the field of data processing, can solve the problems of cumbersome user operation, poor user experience, inconvenient user information statistics and analysis, etc., to achieve the effect of convenient login, avoid repeated authentication, and good user experience
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
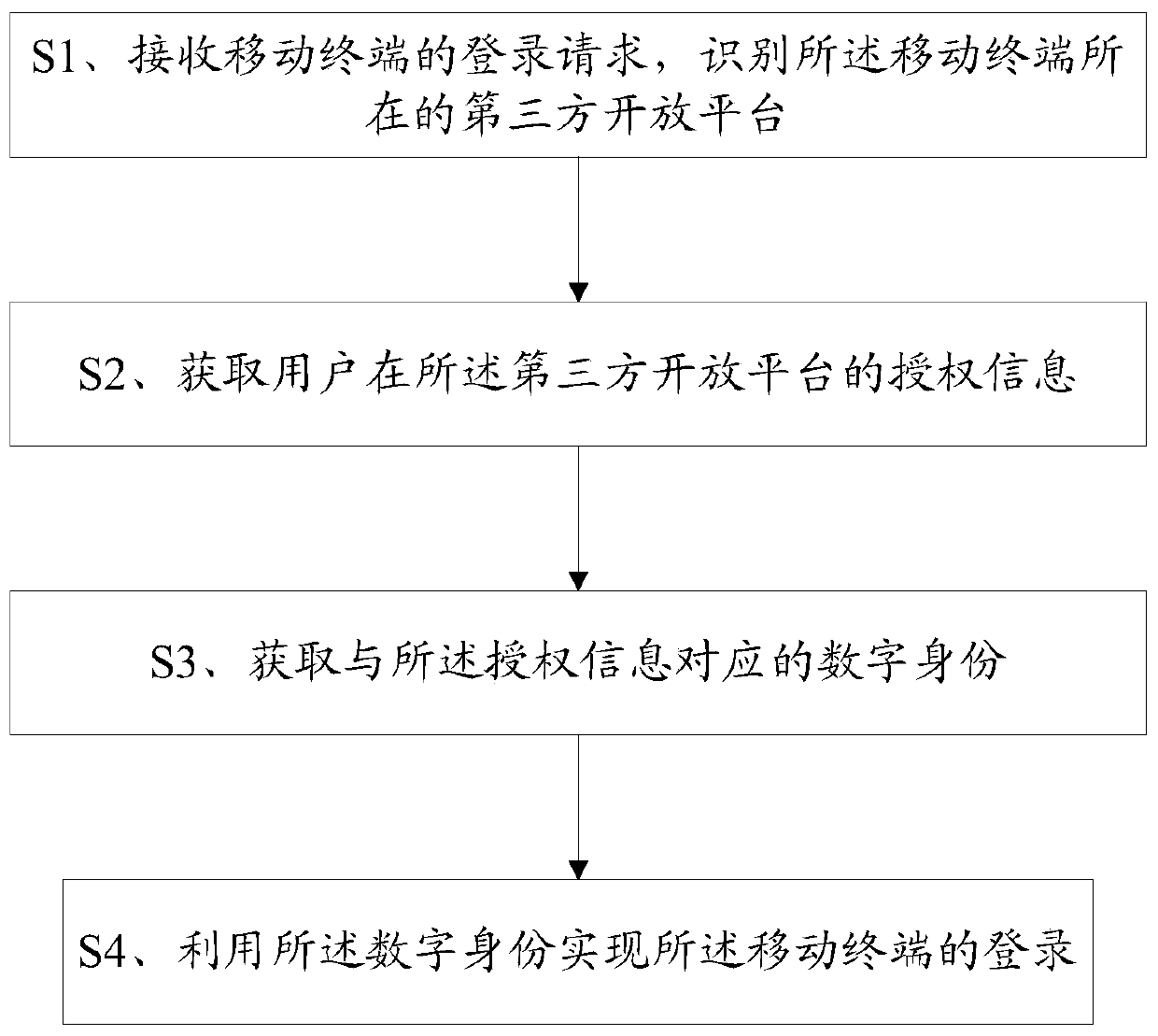
[0068] An identification method, comprising the steps of:
[0069] S1. Receive a login request from a mobile terminal, and identify the third-party open platform where the mobile terminal is located;
[0070] Wherein, the login request is generated after the mobile terminal scans a two-dimensional code;
[0071] S2. Obtain authorization information of the user on the third-party open platform;
[0072] Specifically, the OAuth2.0 authorization mechanism is used to obtain the authorization token of the user on the third-party open platform;
[0073] Obtain the authorization information of the user on the third-party open platform according to the authorization token;
[0074] S3. Obtain a digital identity corresponding to the authorization information;
[0075] Specifically, including steps:
[0076] S31. Determine whether there is a digital identity corresponding to the authorization information, if not, execute step S32, otherwise, execute step S35;
[0077] S32. Extract ...
Embodiment 2
[0084] An identification method, which differs from Embodiment 1 in that it also includes the steps of:
[0085] S5. Receive transaction completion information sent by the mobile terminal, and store user information related to the transaction based on the digital identity;
[0086] Wherein, the user information includes coupons of various third-party open platforms owned by the user, order information of the user, and the like.
Embodiment 3
[0088] Apply the identification method to specific scenarios, for example: after the user enters the restaurant and takes a seat, scan the QR code of the dining table through WeChat to log in to the server used by the restaurant;
[0089] The server recognizes that the third-party open platform where the mobile phone is located is WeChat according to the login request, and then obtains the authorization token of the user on the WeChat platform through an OAuth2.0 authorization mechanism;
[0090] According to the authorization token, obtain the authorization information of the user in WeChat, such as WeChat account;
[0091] Search whether there is a corresponding digital identity in the terminal database based on the WeChat account, if not, extract the user’s mobile phone number from the WeChat account, bind the user’s mobile phone number to the WeChat account, and add the WeChat account to the user In the authorization information pool corresponding to the mobile phone numbe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com