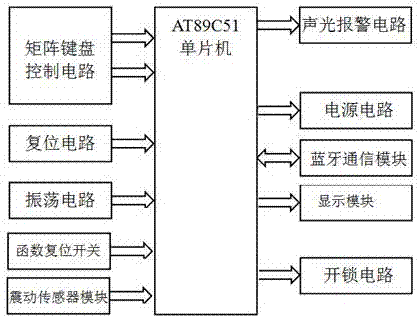
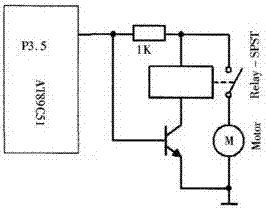
Lock with function of acquiring variable passwords by means of scanning functions corresponding to two-dimensional codes by mobile phones, two-dimensional code identifier and password lock power supply module
A technology of two-dimensional code and password lock, which is applied in the direction of instruments, time registers, single input port/output port registers, etc., which can solve the problems of high development cost and occupation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
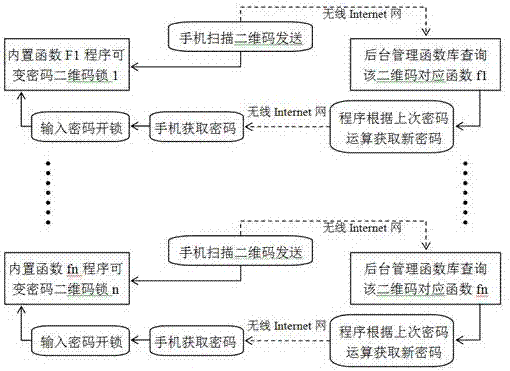
[0076] Embodiment 1: The variable combination lock is in a locked state, and what is seen from the built-in hole (13) of the two-dimensional code is blank, and the variable combination lock is in an open state, and what is seen from the built-in hole (13) of the two-dimensional code is Black, the opening and closing state of the variable combination lock (8) can be judged through the mark in the built-in hole (13) of the two-dimensional code.
[0077] Each two-dimensional code corresponds to one of the independent functions Fn, and this function exists in the memory of the variable password lock (8), which constitutes a password change function subroutine; the exact same function Fn also exists in the management server In the function library, as long as there is the same initial value, there will be the same calculation result; after the mobile phone scans the QR code, send the QR code to the background management function library through the wireless Internet to query the cor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com