User behavior privacy protection method aiming at CSI time frequency domain information attacks
An information attack and privacy protection technology, applied in the field of information security, can solve problems such as acquisition and company economic loss
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
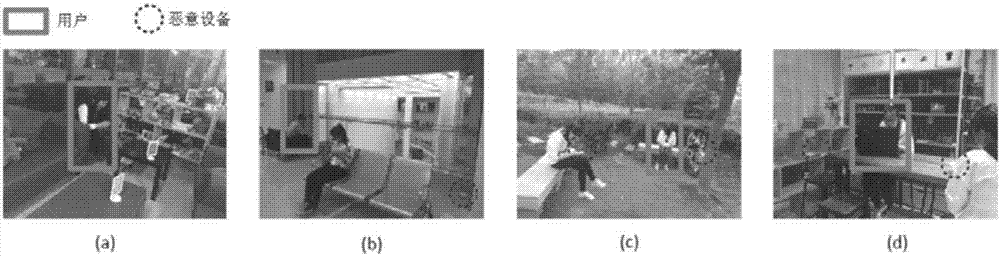
[0049] Such as figure 1 As shown, when the user arrives in a certain area, if there is a WIFI transmitter and receiver in the area, when the user is located relatively close to the device deployed by the attacker, the attacker can use the receiver to obtain The CSI value when the user enters the private information, and then combined with its attack knowledge base, the attacker can easily crack the user's private information, such as the unlock password, Alipay payment password, and WeChat payment password. At this time, the user has the risk of privacy leakage. The present invention provides a privacy behavior protection method that can detect whether the current area is safe, and guide the user to a safe area if it is not safe, specifically as follows:
[0050] A method for protecting user behavior privacy against CSI time-frequency domain information attacks, comprising the following steps:
[0051] Step 1: Determine whether the current location is a safe area
[0052] Inst...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com