Method, apparatus and system for accessing server to terminal by authentication, server and computer readable storage medium
A technology for accessing terminals and servers, applied in the field of communications, can solve the problems of data leakage, easy to read and modify, low reliability, etc., and achieve the effect of avoiding access, high reliability, and avoiding data leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
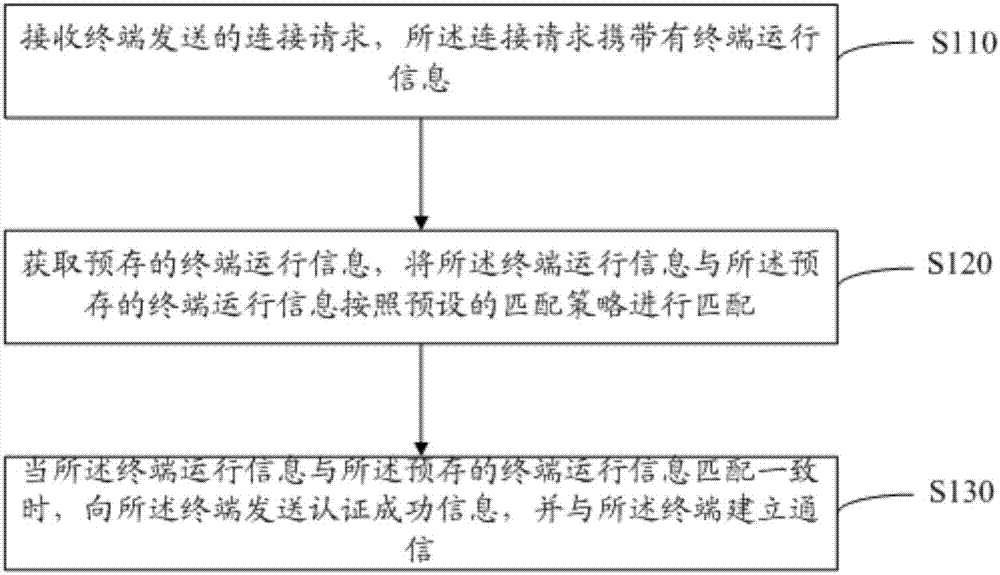
[0043] figure 2 It shows the implementation flow of a method for authenticating an access terminal provided by a server in Embodiment 1 of the present invention, which is applied to a server, and is described in detail as follows:
[0044] In step S110, a connection request sent by the terminal is received, and the connection request carries terminal operation information.
[0045] In the embodiment of the present invention, the terminal running information includes terminal running information including one or any combination of process information, code segment hash, stack feature information, or application signature information.
[0046]In the embodiment of the present invention, the process information includes but not limited to the creator, authority, debugging information, open file and socket list, process ID, parent process ID, assigned user ID, group ID, user group list, owned Capability, permission (capability), the list of Android permissions applied by the APP....
Embodiment 2
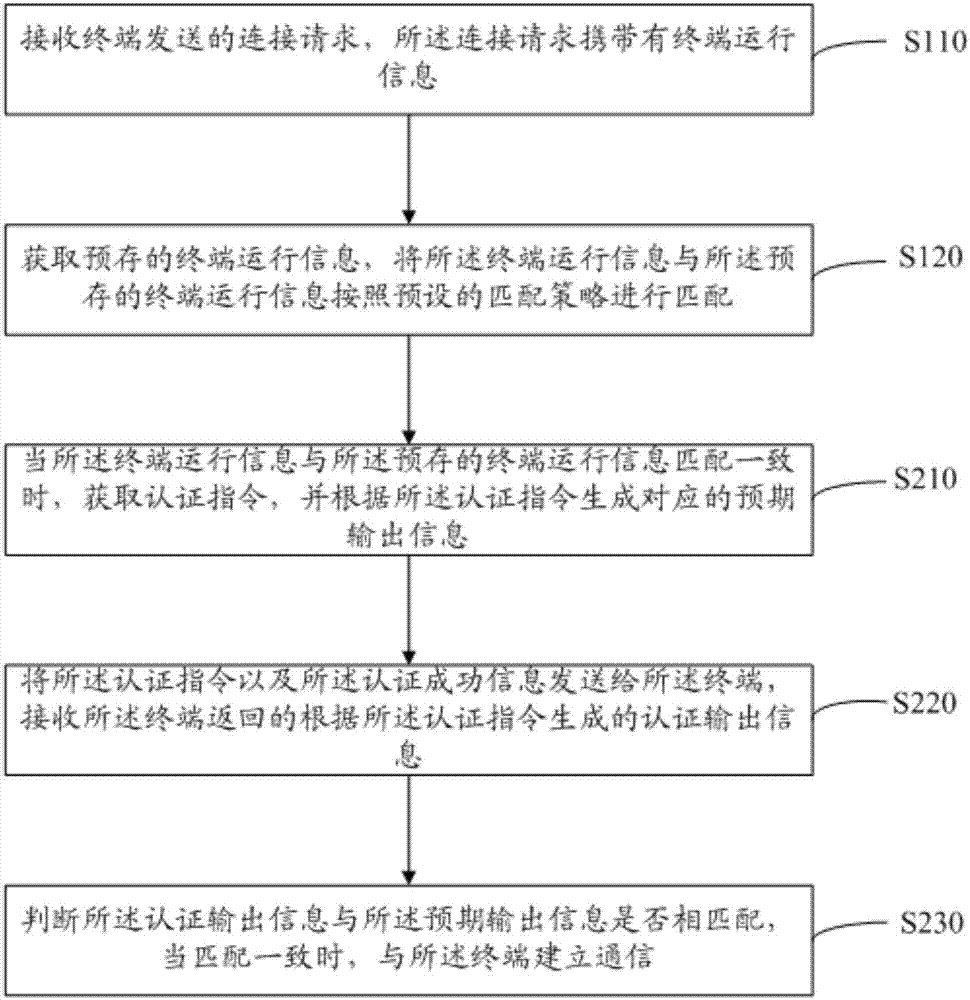
[0060] image 3 It shows the implementation process of a method for authenticating an access terminal provided by a server in Embodiment 2 of the present invention, which is similar to Embodiment 1, except that the Dangdang terminal operation information is the same as the pre-stored terminal When the running information matches the same, send the detection result information to the terminal, and establish communication with the terminal, including:
[0061] In step S210, when the terminal operation information matches the pre-stored terminal operation information, an authentication instruction is obtained, and corresponding expected output information is generated according to the authentication instruction.
[0062] In the embodiment of the present invention, after the terminal operation information sent by the terminal is successfully matched with the pre-stored terminal operation information, the authentication instruction is obtained, and the corresponding expected output...
Embodiment 3
[0070] Figure 4 It shows the implementation process of a method for authenticating an access terminal provided by a server in Embodiment 3 of the present invention, which is similar to Embodiment 1, except that the connection request sent by the terminal is received, and the connection request carries terminal operation information , which previously also included:
[0071] In step S310, a session request sent by the terminal is received.
[0072] In step S320, a random number is generated and sent to the terminal, so that the terminal generates a corresponding negotiation key according to the random number.
[0073] In the embodiment of the present invention, when the server receives the session request sent by the terminal, the server triggers the server to generate a corresponding random number according to the random number generation algorithm, and sends it to the terminal to generate the negotiation key, wherein the random number generation algorithm It can include mu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com