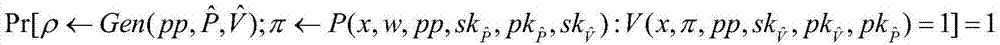Realization method of perfect forward security deniable key exchange protocol of online bidding system
A key exchange protocol and forward security technology, which is applied in the online bidding system to improve the field of forward security deniable key exchange protocol implementation, and can solve the problems of increasing protocol burden, losing deniability, and not knowing the construction method. Improve the effect of forward security and strong security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
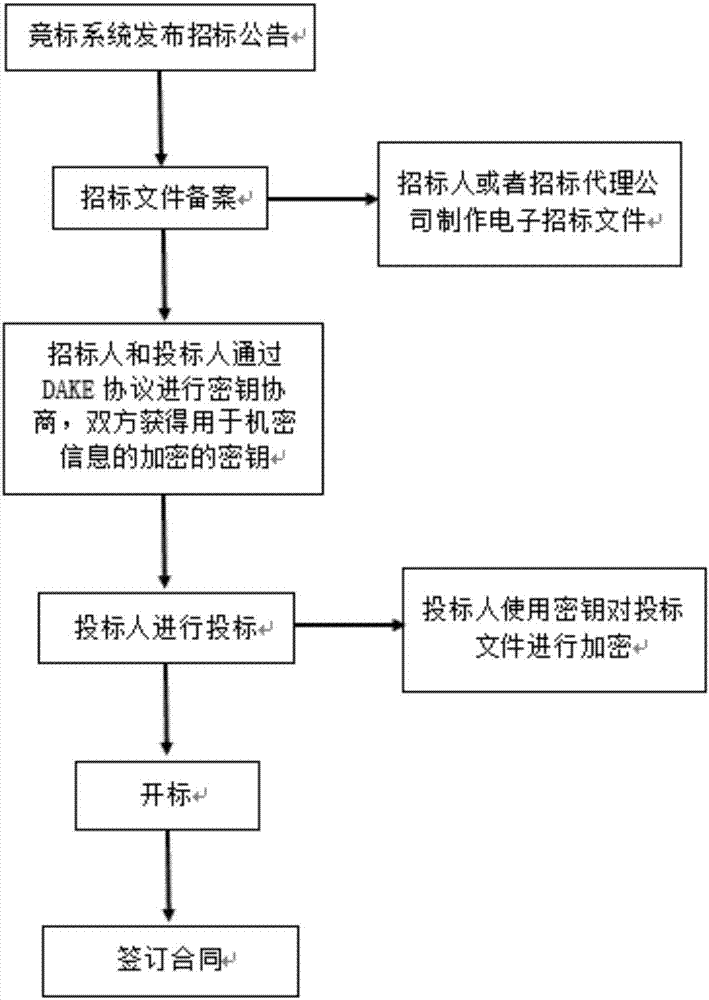
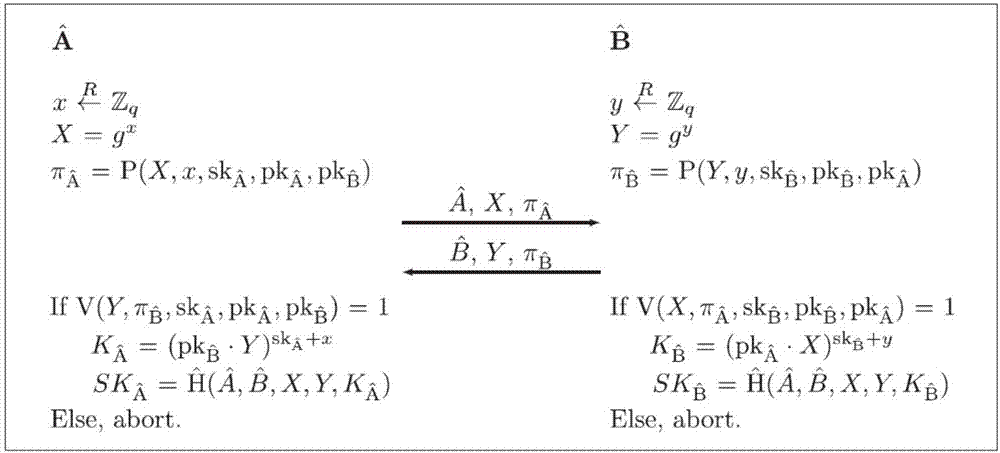
[0071] The present invention defines the non-interactive Designated Verifier Proof of Knowledge (DV-PoK) and proposes an efficient non-interactive Designated Verifier Proof of Knowledge scheme, and then combines the non-interactive Designated Verifier Proof of Knowledge (DV-PoK) scheme and Diffie-Hellman protocol to construct a round of deniable authenticated key exchange protocol (DAKE protocol), which has both perfect forward security and complete deniability. Such as figure 1 As shown, it specifically includes the following steps:
[0072] Non-interactive Designated Verifier Proof of Knowledge (DV-PoK) definition:
[0073] The present invention formally defines the concept of non-interactive designated authenticator's knowledge proof, which has completeness, special reliability, adaptive zero-knowledge, unforgeability and symmetry. The unforgeability and symmetry make the protocol constructed by the present invention have perfect forward security and complete denia...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com