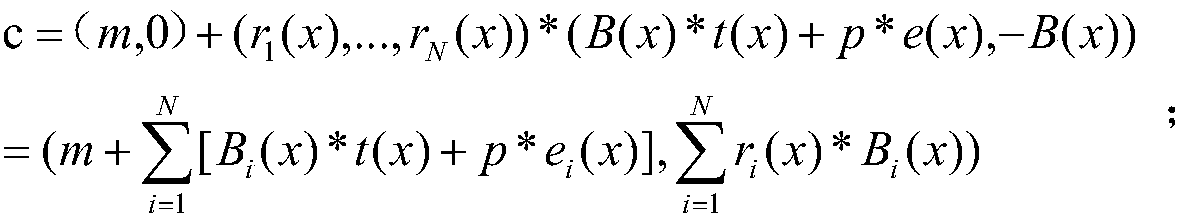Polynomial point expressed low expansion ratio anti-quantum-attack file encryption and decryption method
An anti-quantum attack, low expansion rate technology, applied in the computer field, can solve the problems of high ciphertext expansion rate and low efficiency, and achieve the effect of low ciphertext expansion rate and high encryption efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
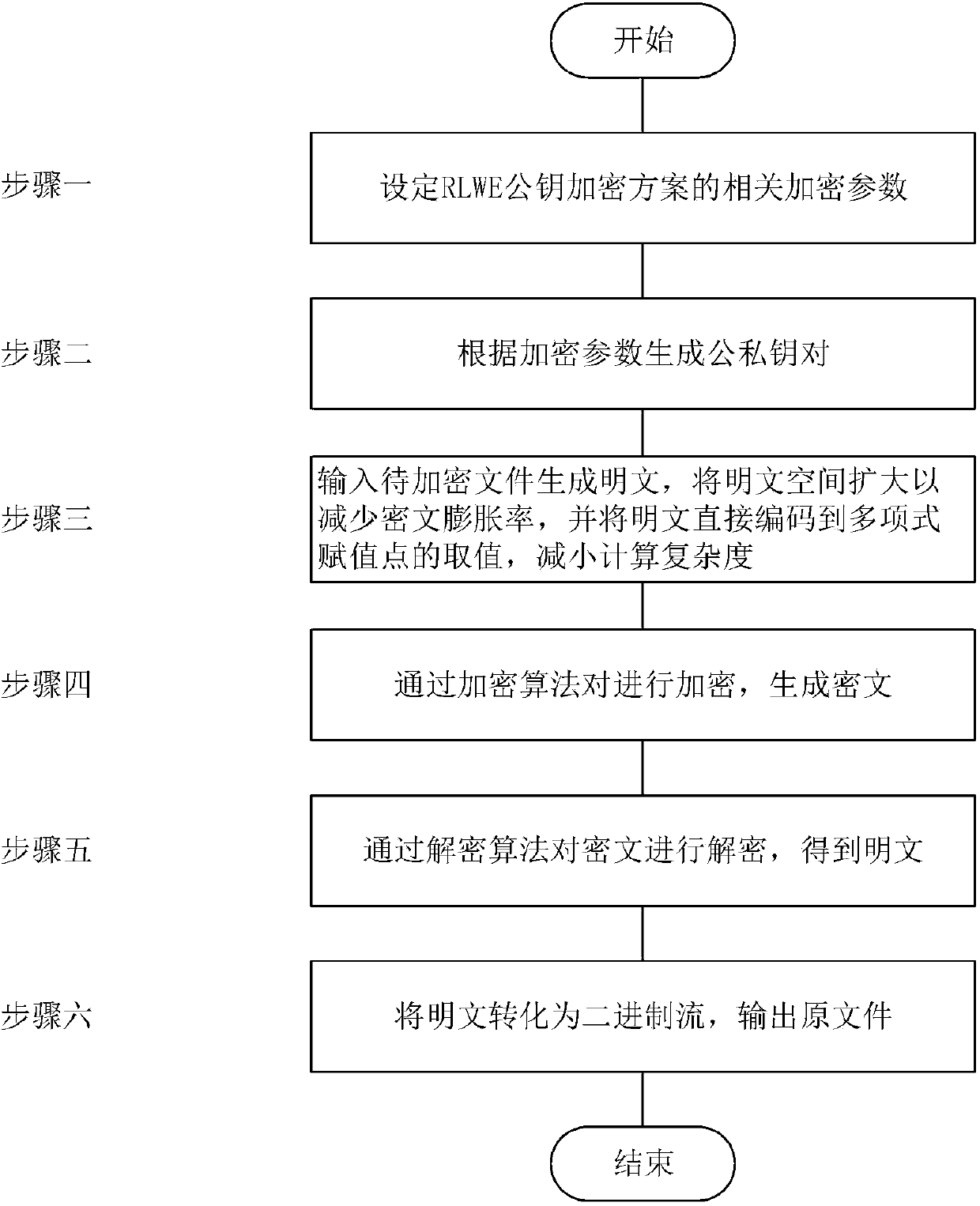
[0042] The preferred embodiments of the present invention will be described in detail below with reference to the accompanying drawings.
[0043] like figure 1 Shown, the steps of the present invention are as follows:
[0044] step one:
[0045] 1) Modulo q polynomial residue class ring Rq = Z q [x] / φ n (x) is the ciphertext space, where Z q [x] indicates that the coefficient is a finite field Z q A set of polynomials of elements in , take a fixed parameter q=1618027507.
[0046] 2) Take the fixed parameter n=809 as the number of times of the loop.
[0047] 3) N is the dimension of elements in the ring, and a fixed parameter N=92 is taken.
[0048] 4) Modulo p polynomial residue class ring R p = Z p [x] / φ n (x) is the plaintext space, where Z p [x] indicates that the coefficient is a finite field Z p A set of polynomials of elements in , take a fixed parameter p=65535.
[0049] 5) χ is R q The noise distribution on , with an expectation of 0 and a variance of 3.2...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com