Agent-free illegal external-connection monitoring method and system
A monitoring system and outreach technology, applied in the field of information security, can solve problems such as difficulty in monitoring illegal outreach behavior of subnets, monitoring failure, and inaccurate monitoring results.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] The technical solutions of the present invention will be further described below in conjunction with the accompanying drawings and through specific implementation methods.
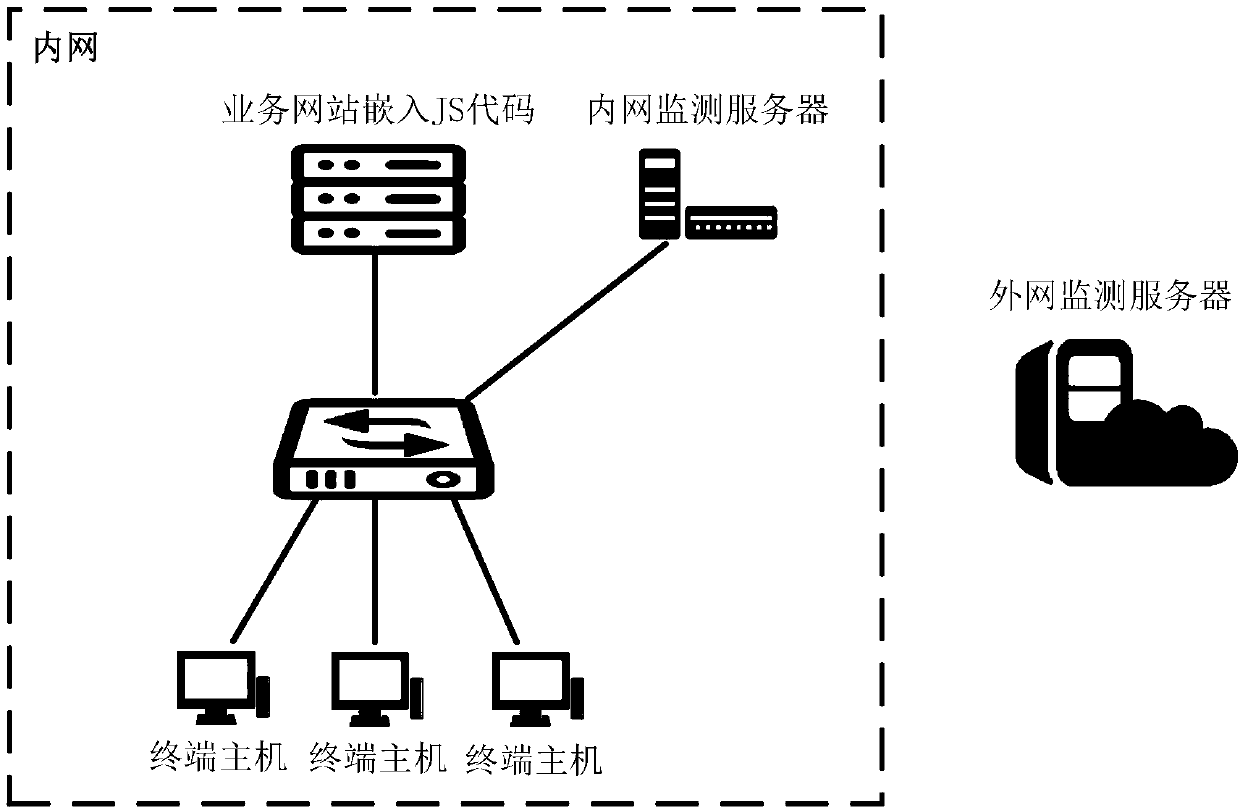
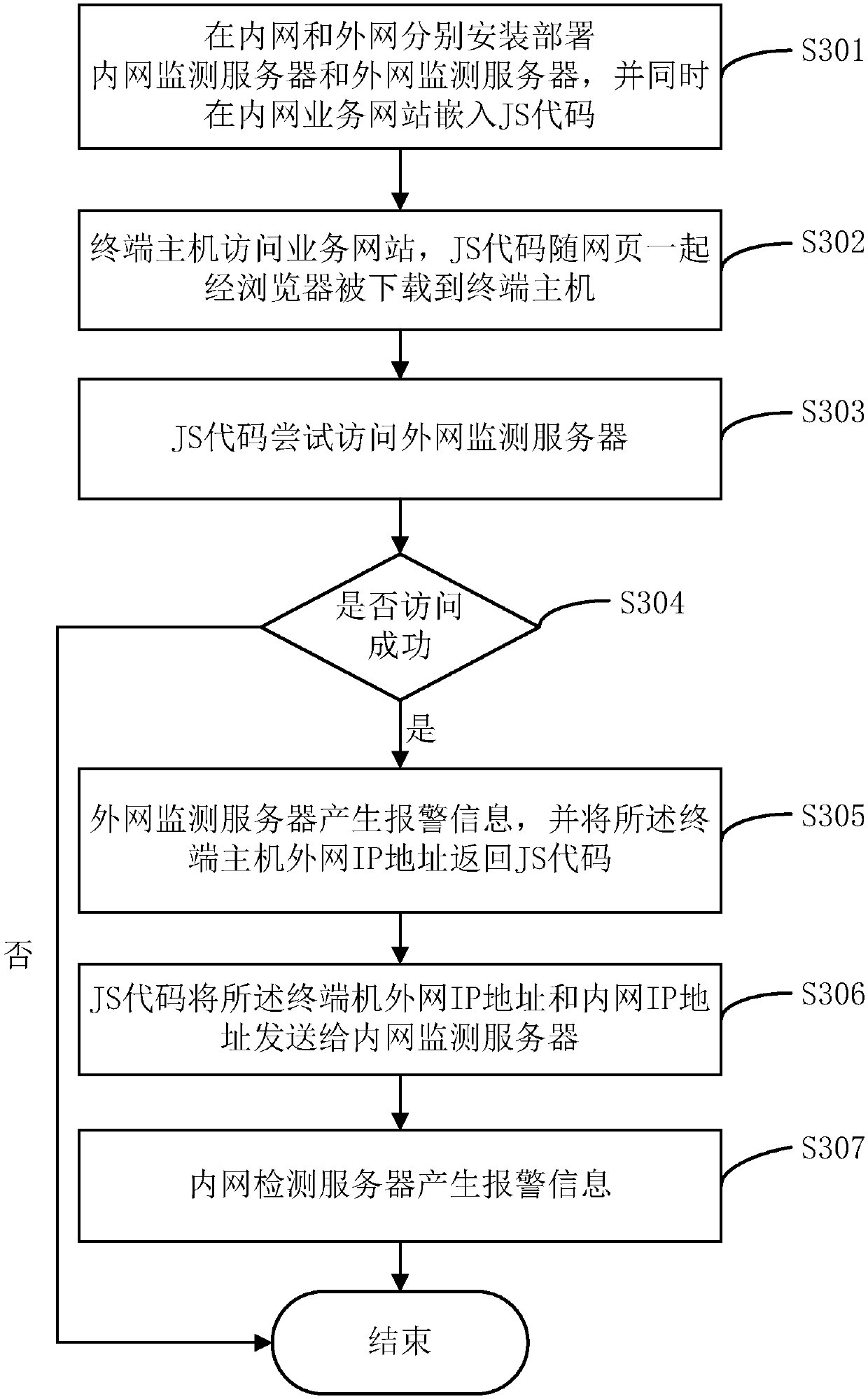
[0029] figure 1 It is an application deployment diagram of a preferred non-agent violation monitoring system of the present invention. Such as figure 1 As shown, the application model of the present invention is shown. Install and deploy the intranet monitoring server on the intranet, install and deploy the extranet monitoring server on the extranet, and embed JS code on the intranet business website.
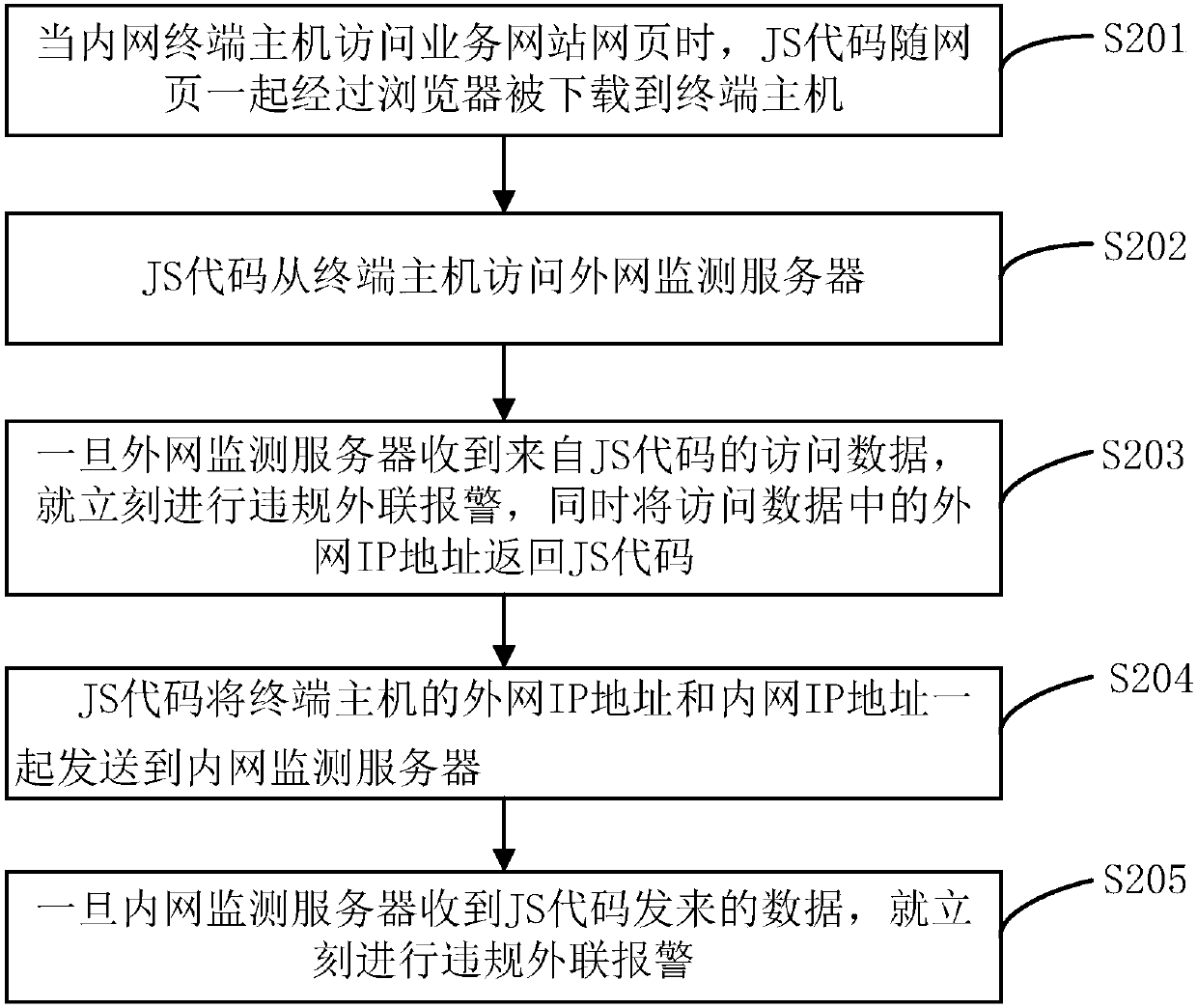
[0030] figure 2 It is a flow chart of an agentless outreach monitoring method for violations of the present invention, such as figure 2 As shown, the method flowchart includes the following steps:
[0031] Step S201, when the intranet terminal host visits the webpage of the business website, the JS code is downloaded to the terminal host through the browser along with the webpage;
[0032] St...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com