A Double Encryption Method for Reversible Data Hiding of Encrypted Domain Image
A double encryption, data hiding technology, applied in image communication, digital video signal modification, selective content distribution, etc., can solve the problems of complex protocol, low embedding capacity, low distortion, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
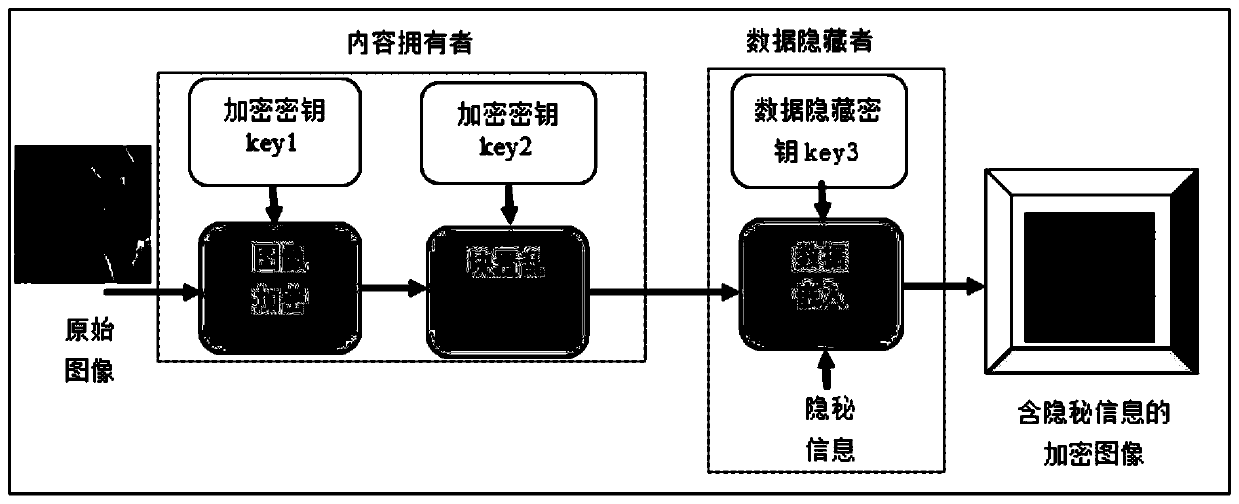
[0068] A double-encrypted encrypted domain image reversible data hiding method proposed in this embodiment includes three parts: image encryption, encrypted domain image reversible data hiding, hidden data extraction and original image lossless restoration; wherein,
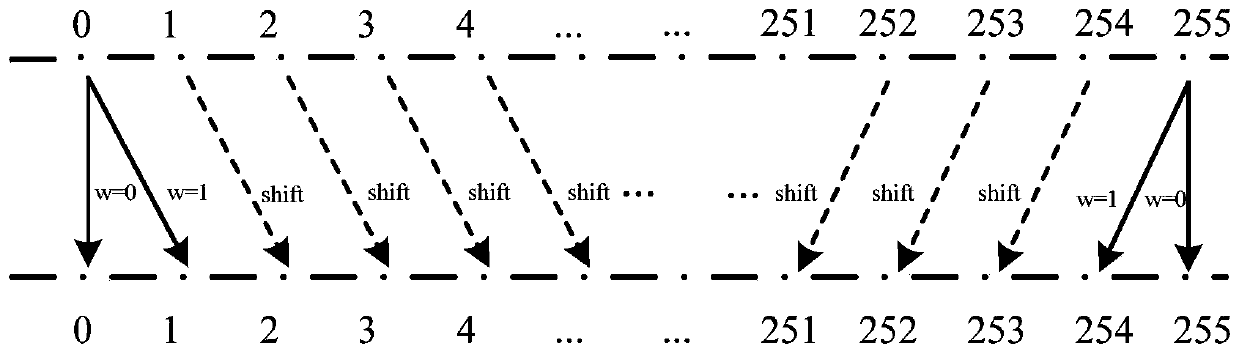
[0069] Such as figure 2 As shown, the processing process of the image encryption part is:
[0070] ①_1. Set the width and height of the original image to be encrypted to correspond to W and H. If W×H can be divisible by g×g, divide the original image to be encrypted into non-overlapping image blocks of size g×g; if W×H cannot be divisible by g×g, the original image to be encrypted is divided into non-overlapping image blocks with a size of g×g, and the blocks to the right and bottom of the original image to be encrypted whose size is not g×g are also used as image blocks. image blocks; among them, the value of g is 2 or 3, and the symbol is the rounding down sign, the sign is the round up symbol.
[00...
Embodiment 2
[0095] This embodiment proposes a double-encryption encryption domain image reversible data hiding method, the image encryption part and the encryption domain image reversible data hiding part are the same as the image encryption part and the encryption domain image reversible data hiding part in Embodiment 1. The focus is only on the part of the secret data extraction and the lossless restoration of the original image. In this embodiment, the receiving end only has the data hiding key, and only extracts the secret information from the encrypted domain image containing the secret information. The specific process is as follows:
[0096] ③_2_1. The width and height of the encrypted domain image containing hidden information correspond to W and H, and the encrypted domain image containing hidden information is divided into non-overlapping image blocks of size g×g; where, the symbol is the rounding down symbol.
[0097] The third key key3 is used as an input parameter of the r...
Embodiment 3
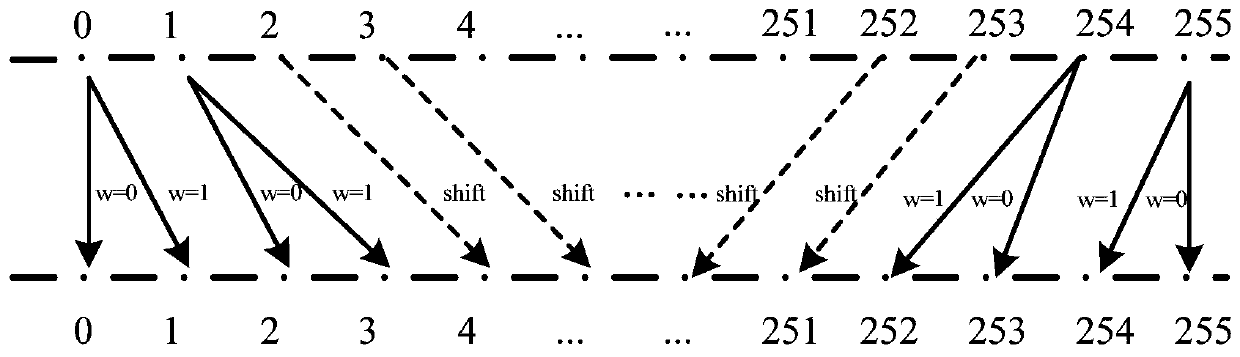
[0105] A double-encryption encryption domain image reversible data hiding method proposed in this embodiment, its image encryption part and encryption domain image reversible data hiding part are the same as the image encryption part and encryption domain image reversible data hiding part in Embodiment 1 or Embodiment 2 The same, the difference is only in the hidden data extraction and lossless restoration of the original image, in this embodiment, such as image 3 As shown, the receiving end has both the data hiding key and the encryption key. First, the secret information is extracted from the encrypted domain image containing hidden information, and then the encrypted domain image after the secret information extraction is decrypted. The specific process is as follows:
[0106] ③_3_1. The width and height of the encrypted domain image containing hidden information correspond to W and H, and the encrypted domain image containing hidden information is divided into non-overla...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com