Abnormity detecting algorithm based on random Hash
An anomaly detection and algorithm technology, applied in computing, computing models, machine learning, etc., can solve problems such as failure, achieve high accuracy, solve the effects of long running time, and overcome failure
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
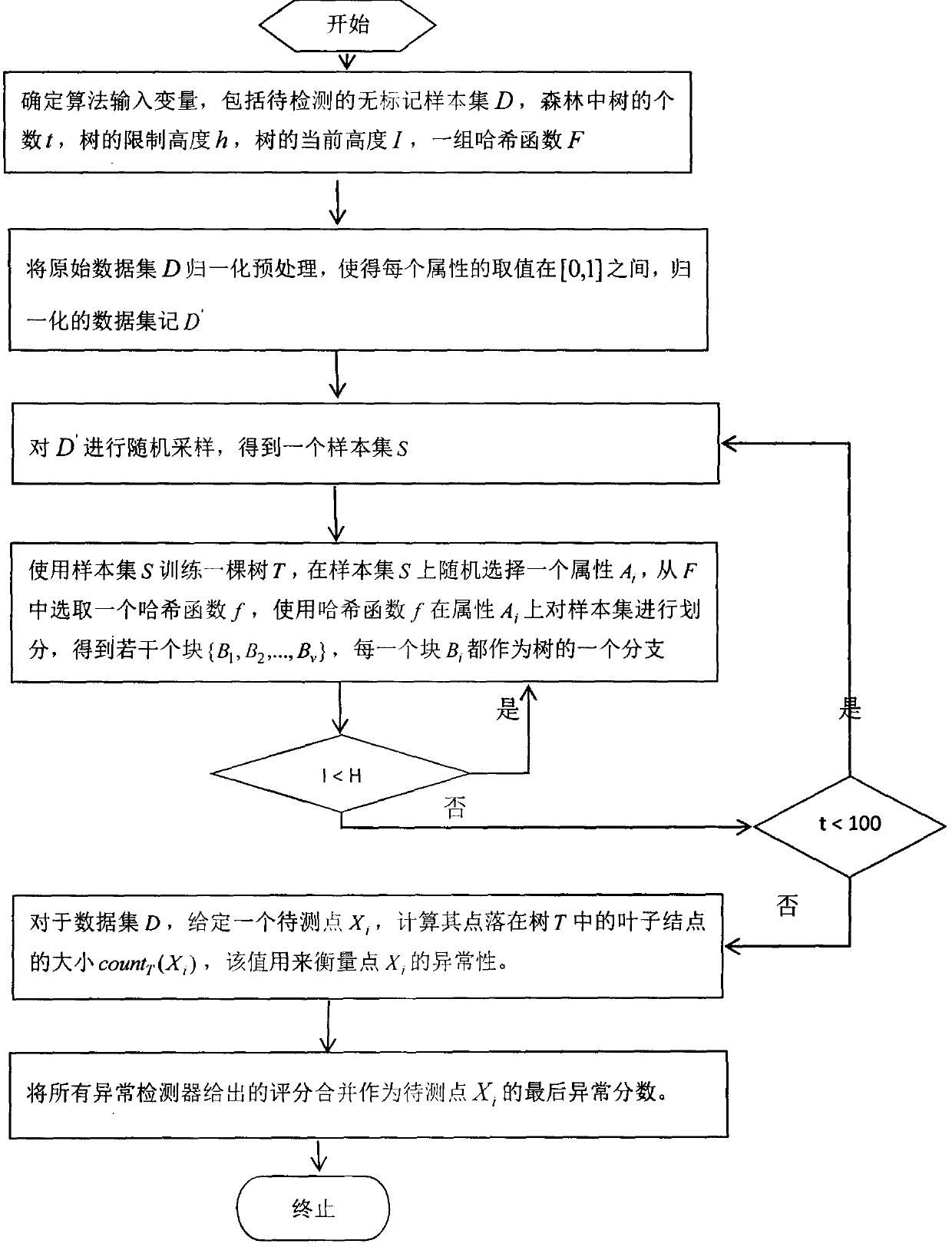
[0029] A random hash-based anomaly detection algorithm proposed by the present invention will be described in detail below in conjunction with the accompanying drawings.
[0030] Such as figure 1 As shown, the anomaly detection algorithm based on random hash proposed in the present invention comprises the following steps:
[0031] Step 1) Determine the algorithm input variables, including the unmarked sample set D to be detected, the number t of trees in the forest, the limited height h of the tree, the current height I of the tree, and a group of hash functions F;
[0032] Step 2) Normalize and preprocess the original data set D so that the value of each attribute is between [0, 1], and the normalized data set is recorded as D';
[0033] Step 3) randomly sampling D' to obtain a sample set S;
[0034] Step 4) Use the sample set S to train a tree T, and randomly select an attribute A on the sample set Si , select a hash function f from F, and use the hash function f in attrib...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com