Method and system for detecting incredible search path loophole
A search path and detection method technology, applied in the field of data security, can solve problems such as easy to miss, let go of loopholes, untrustworthy search path loopholes, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach
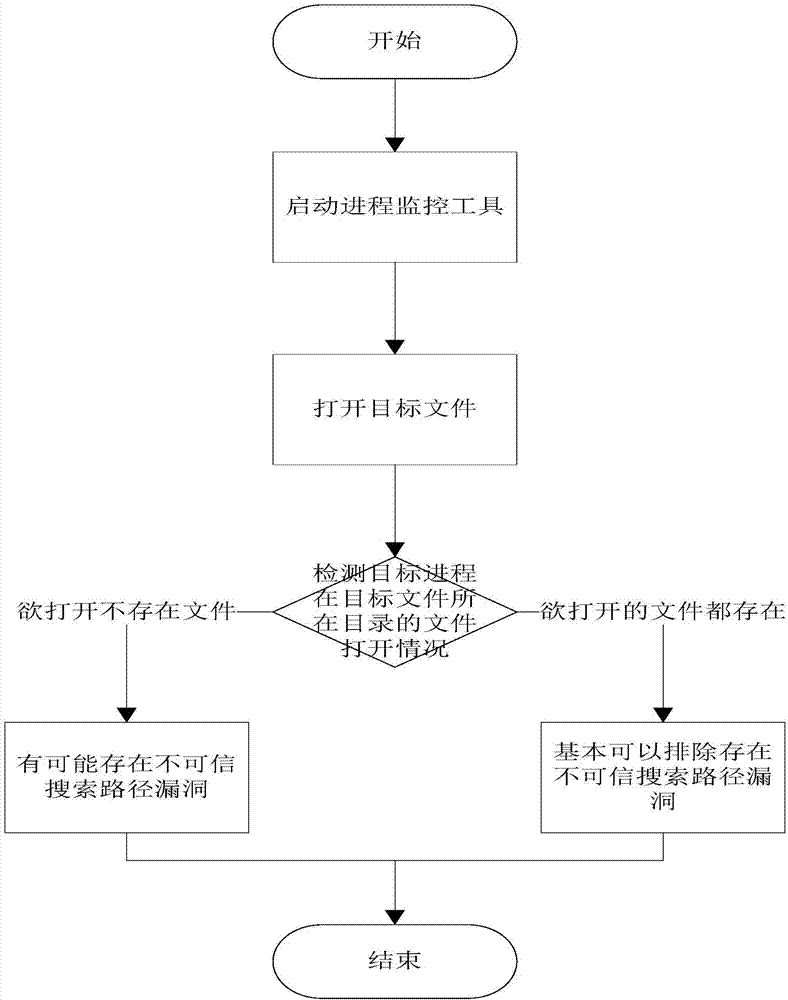
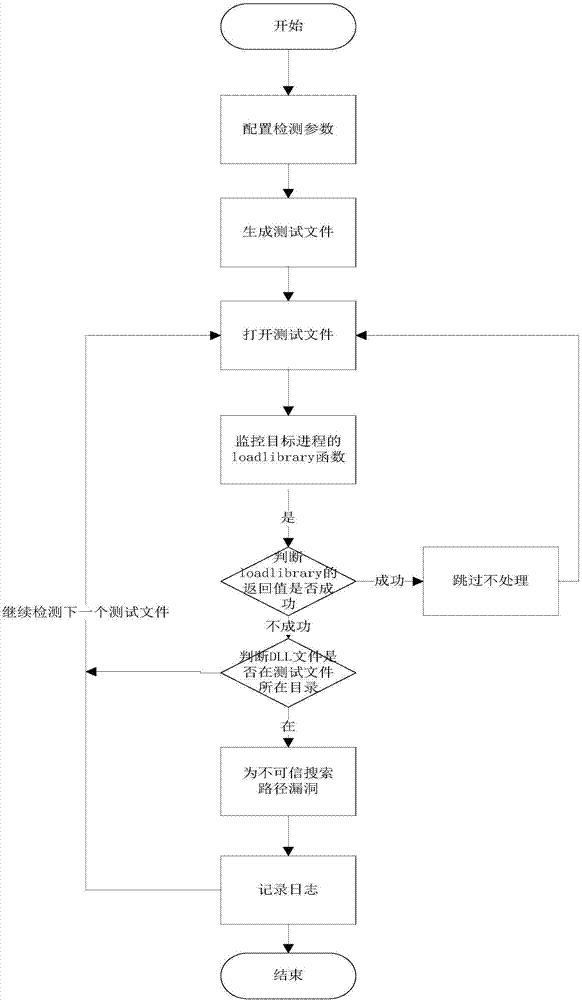
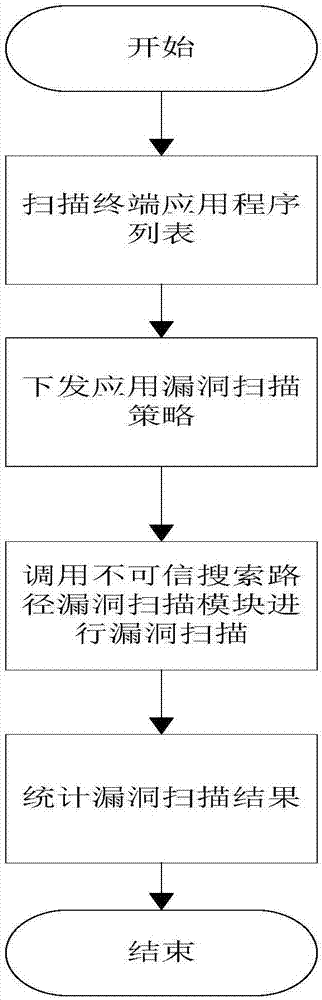
[0072] like figure 2 , illustrates the detection flowchart when Windows loads the dynamic link library. Specifically, it is loaded according to: the directory where the application is located → the current directory → the Windows SYSTEM directory → the Windows directory → the path specified by the PATH environment variable. If the DLL is not in the directory where the application is located, it will search in turn. If we open a file in a certain folder, the current directory of the software will change to this folder, and the software will load the DLL at this time. If it is not in the directory where the application program is located, it will search in this folder. At this time, if the Trojan horse file is disguised as this DLL file, it will be loaded by the software and executed successfully. This is the Untrusted Search Path Vulnerability Untrusted Search Path Vulnerability , the process of detecting untrusted search path vulnerabilities in Windows is as follows:
[007...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com