A method and system for abnormal UA detection and analysis based on rules
An abnormal and regular technology, applied in the field of network information, which can solve the problems of key field processing, effective mapping and labeling pollution, abnormal characters in key fields, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
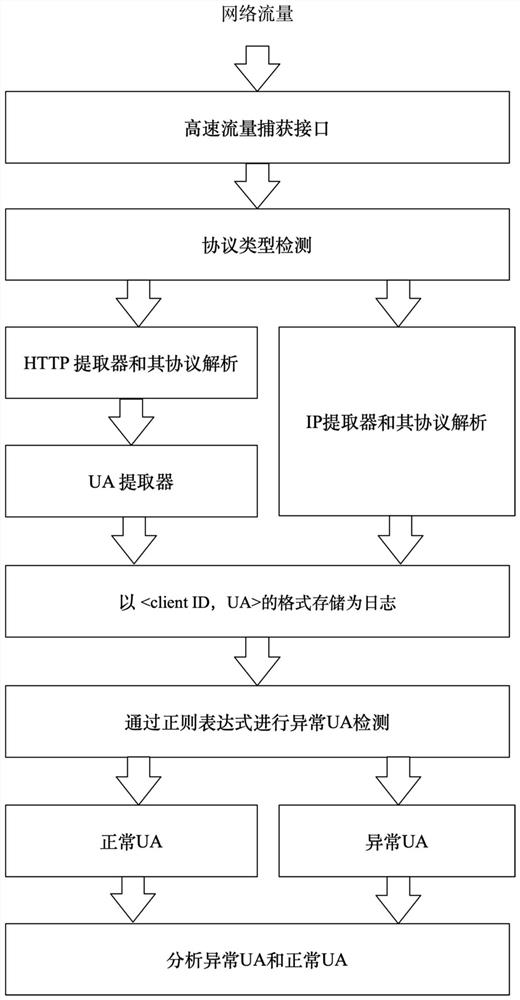
[0033] In order to make the above-mentioned features and advantages of the present invention more obvious and easy to understand, a rule-based abnormal UA detection and analysis method disclosed in the present invention will be described in detail below in conjunction with the accompanying drawings, as shown in figure 1 The flow chart shown includes the following steps:
[0034] 1. Detection stage:
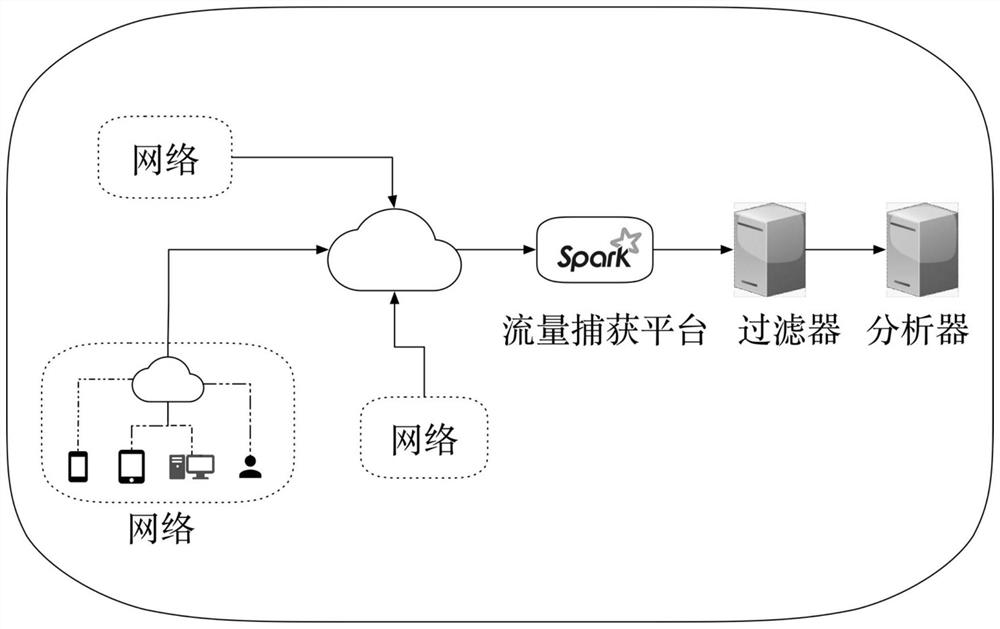
[0035] (1) Network traffic capture: use Spark-based high-speed network traffic capture platform to capture high-speed traffic and wait for processing.
[0036] (2) Network traffic filtering and key field extraction: analyze the above captured traffic, filter HTTP traffic from all network traffic according to the HTTP format, and extract the UA field and client IP information according to the HTTP format , form a log in the format of and store it.
[0037] (3) Abnormal UA detection: Detect the extracted UA through regular expressions to determine whether there are abnormal chara...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com