Illegal connection judgment method based on set coverage
A connection judgment and illegal technology, applied in the transmission system, electrical components, etc., can solve the problems of information leakage, inability to identify and steal illegal equipment, etc., and achieve the effect of improving work efficiency, convenient and quick judgment method, and reducing work burden
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
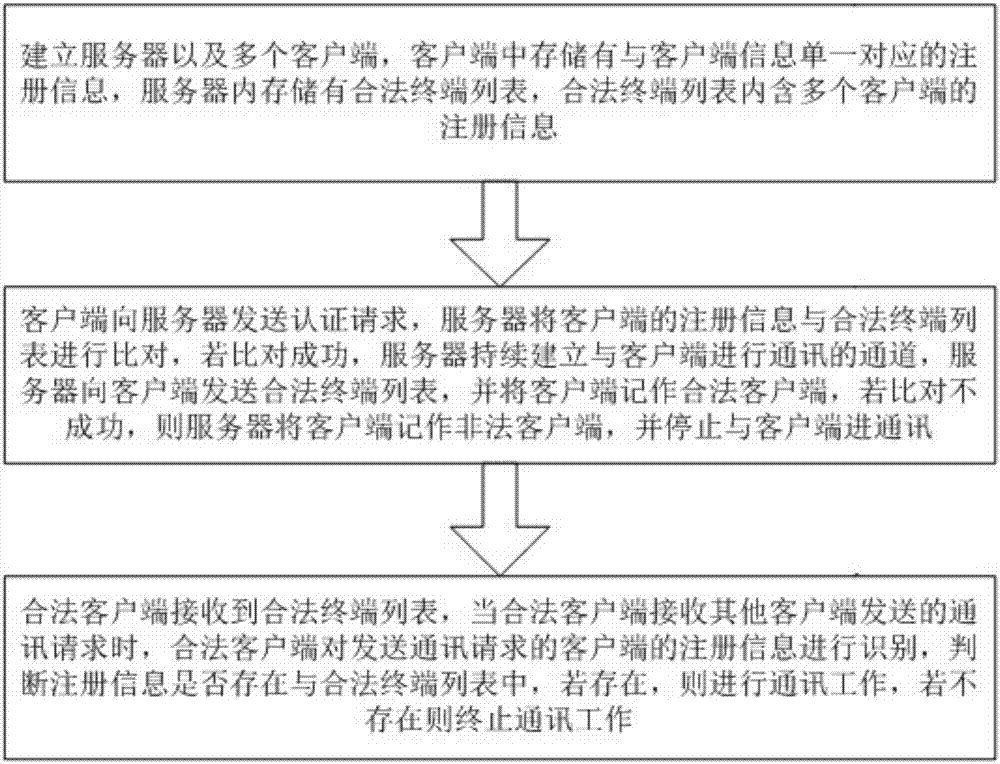
[0050] Preferred embodiment 1, step 2, the client sends an authentication request to the server, and the server compares the registration information of the client with the legal terminal list;
[0051] If the comparison is successful, the server continues to establish a communication channel with the client, and the server sends a list of legal terminals to the client, and records the client as a legal client;
[0052] If the comparison is unsuccessful, the server will record the client as an illegal client and stop communicating with the client. At the same time, the server will call the illegal client to mark the illegal client's tag information, and store the tag information in the illegal connection address book , to record the number of illegal client accesses; the above tag information contains the unique identification of the terminal; through the tag information, both the server and the client can perform accurate identification.
[0053] By illegally connecting to th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com