Asset management system based on network asset information collection
An asset management system and information collection technology, applied in the field of network information security, can solve the problems of incomplete grasp of information asset information, difficulty in timely and accurate discovery of loopholes and repairs, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0043] Embodiments of the present invention will be described in detail below. It should be emphasized that the following description is only exemplary and not intended to limit the scope of the invention and its application.
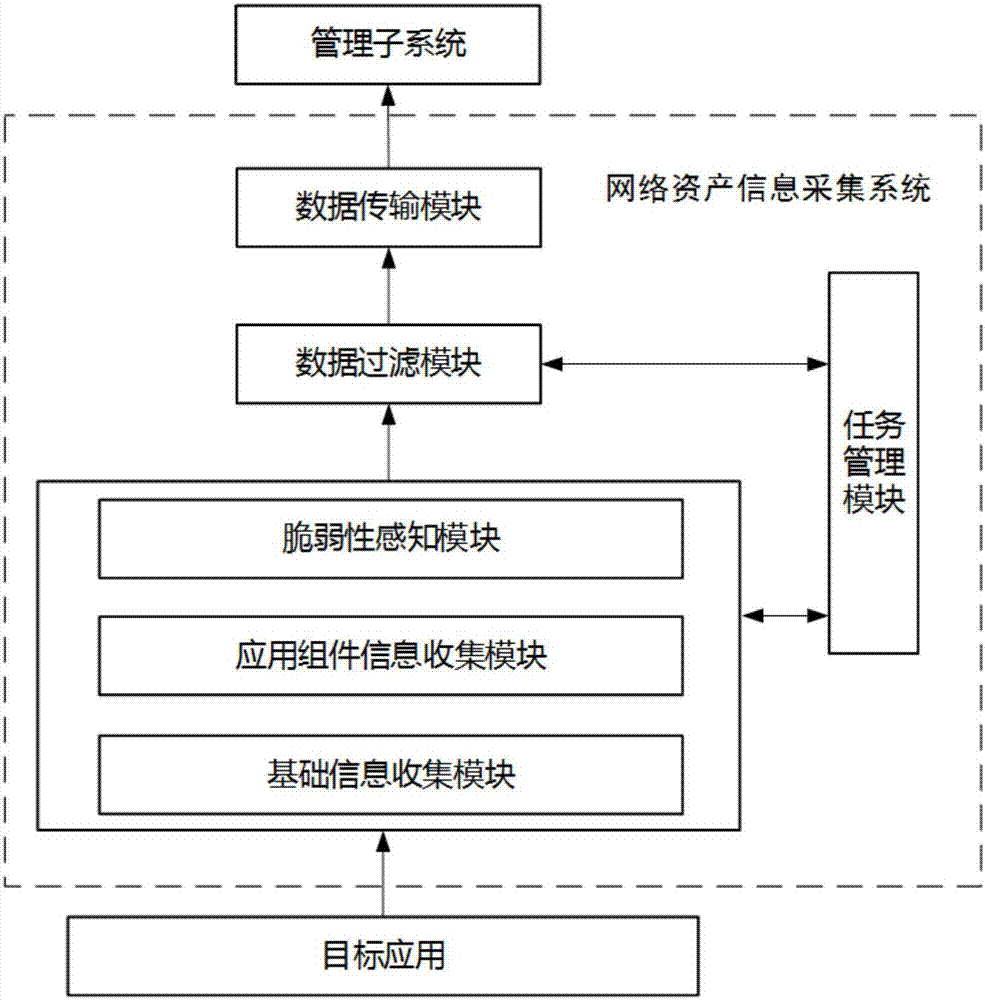
[0044] refer to figure 1 , in one embodiment, an asset management system based on network asset information collection includes a network asset information collection system, and the network asset information collection system includes: a basic information collection module configured to discover networked hosts and perform host Fingerprint identification of the operating system, to detect the type of operating system of the remote target host; an application component fingerprint collection module, which is configured to discover one or more of the version, service port, and protocol interaction characteristics of the network application or component Application program or component fingerprint information; vulnerability awareness module, which is con...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com