Access control system, access control robot and operating method thereof
An operation method and robot system technology, applied to instruments, time registers, single input/output registers, etc., can solve the problems of high cost, low security, unfavorable access control system promotion, etc., to prevent theft Brushing or proxy brushing, the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
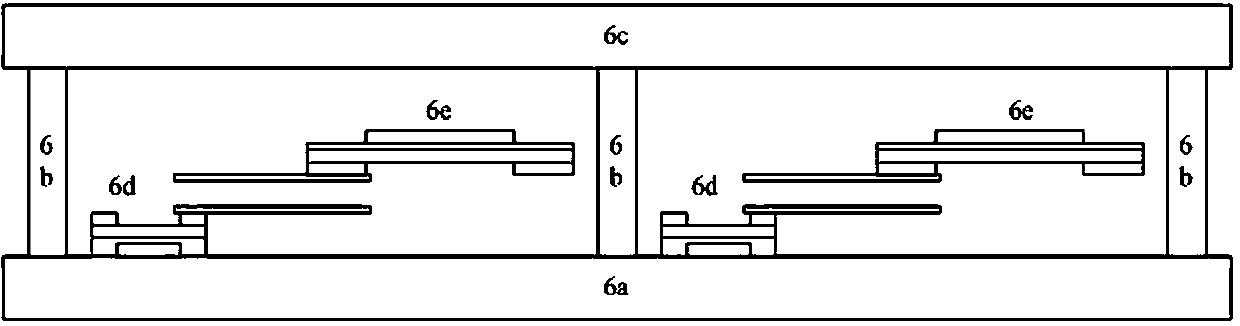
[0036] The features and technical effects of the technical solution of the present invention will be described in detail below with reference to the drawings and in conjunction with exemplary embodiments, and an access control system, robot and operation method thereof that can efficiently prevent theft or replacement of brushes and improve security are disclosed. It should be pointed out that similar reference signs indicate similar structures. The terms "first", "second", "upper", "lower", etc. used in this application can be used to modify various system components or method steps. . Unless otherwise specified, these modifications do not imply the spatial, order, or hierarchical relationship of the modified system components or method steps.
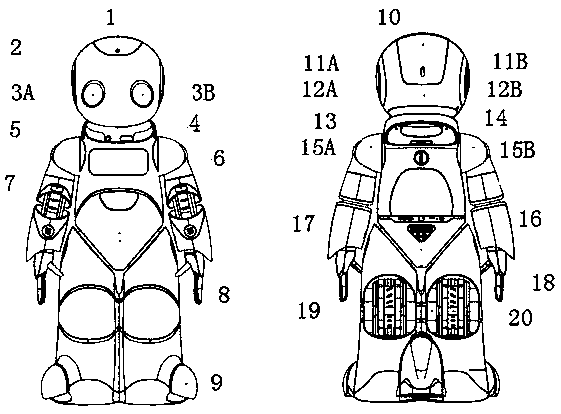
[0037] Such as figure 1 As shown, the access control robot according to the embodiment of the present invention includes: a high-sensitivity microphone 1 located on top of the head, used to collect or receive surrounding sound informatio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com