A real-time network abnormal behavior detection system and method based on big data
A real-time network and detection system technology, applied in the field of network security management, can solve the problems of not being able to analyze and provide data in full traffic, unsatisfactory streaming processing performance, and low collection efficiency, etc., to facilitate management, ensure reliability and efficiency. , the effect of saving labor costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
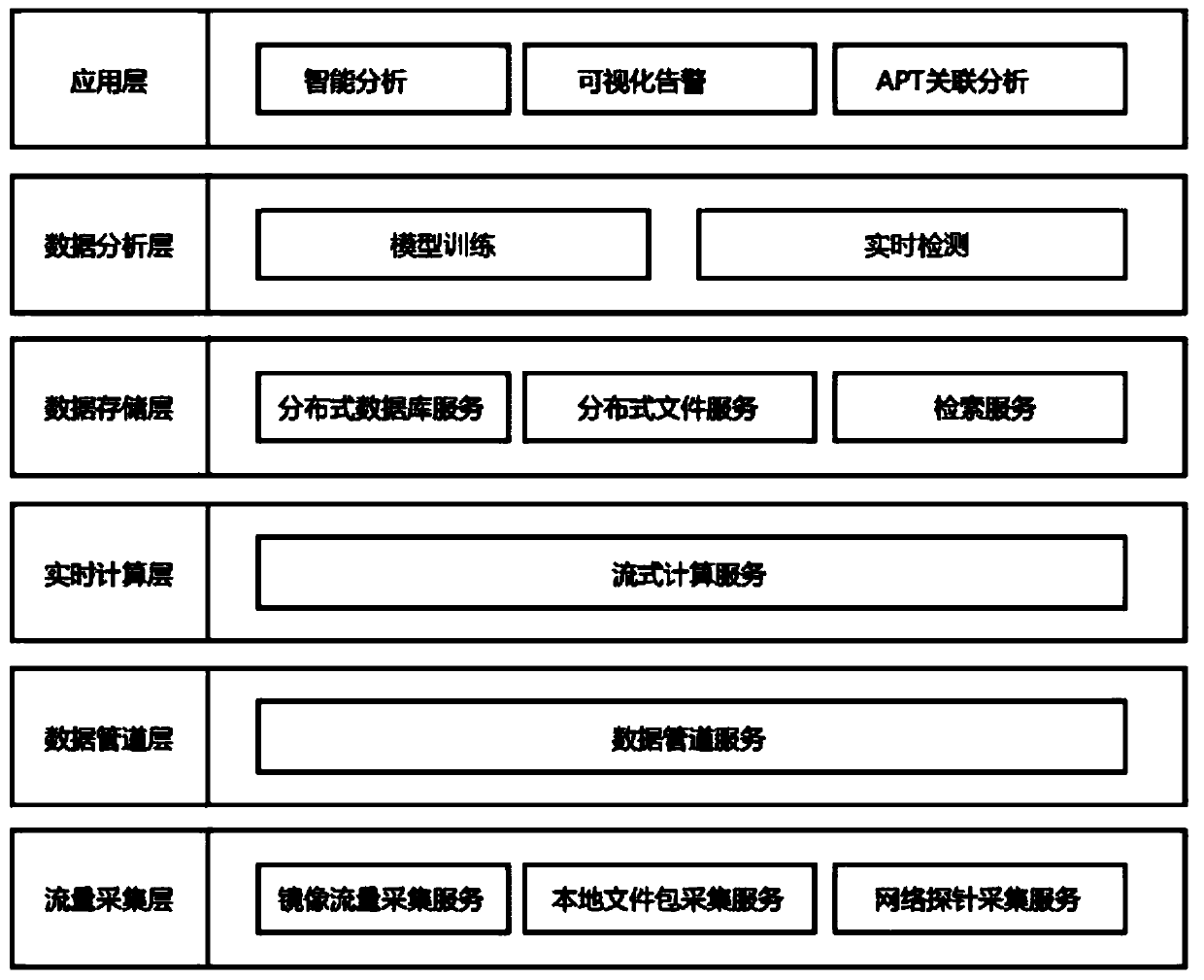
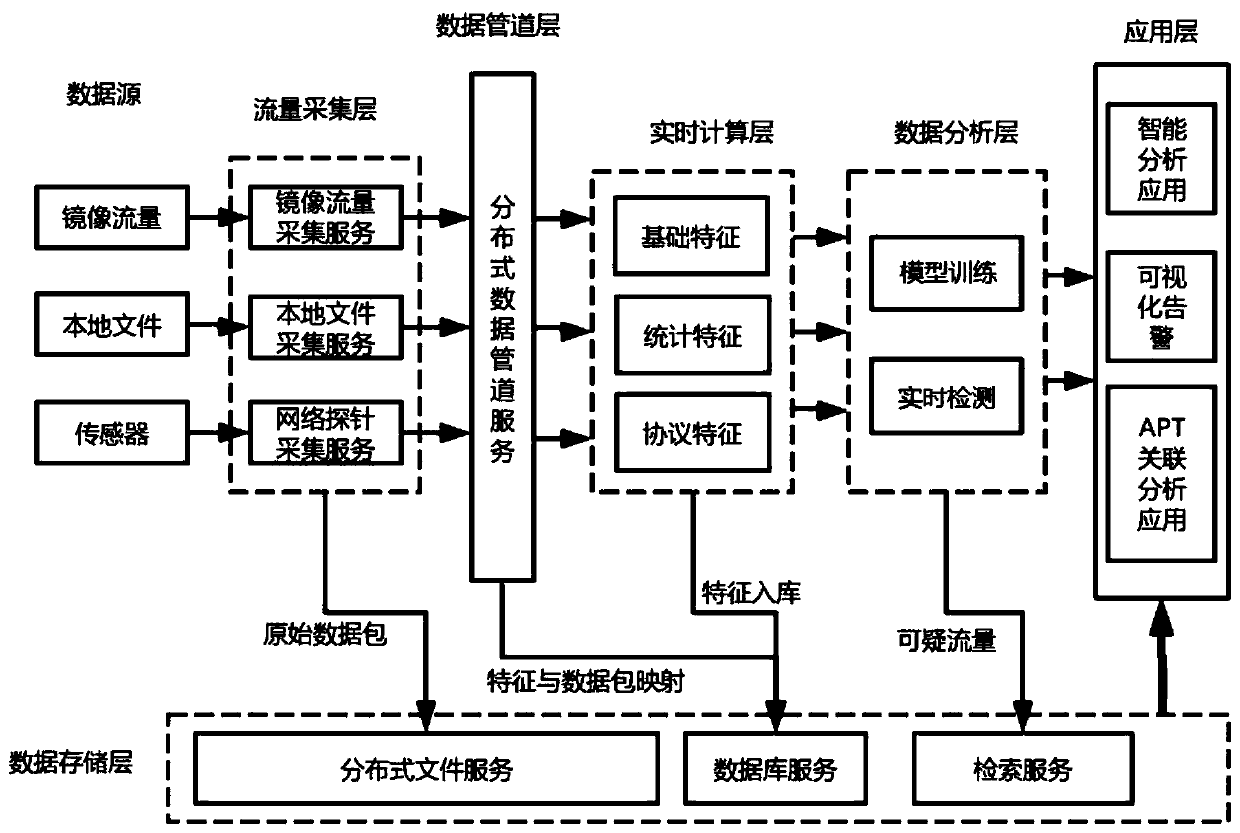
[0073] A real-time network abnormal behavior detection system based on big data, such as Figure 1~2 As shown, it includes traffic acquisition layer, data pipeline layer, real-time computing layer, data storage layer, data analysis layer and application layer.
[0074] As a preferred solution, the traffic collection layer includes a mirrored traffic collection module that collects traffic mirrored from the switch, a local file collection module that collects local files, and a network probe that collects sensor data Acquisition module. The three modules can all provide traffic collection services, and the traffic collection services include data packet capture services, data packet analysis services, local storage services, data feature extraction services, data stream serialization services, and data transmission services.
[0075] The traffic acquisition layer captures data packets through the data packet capture service, then preprocesses the collected data, and then trans...
Embodiment 2
[0116] A big data-based real-time network abnormal behavior detection method, comprising a flow collection layer, a data pipeline layer, a real-time calculation layer, a data storage layer, a data analysis layer and an application layer, specifically comprising the following steps:
[0117] S1: The traffic collection layer collects traffic data from the data source, and preprocesses the data, and then sends the preprocessed data to the distributed message system in the data pipeline layer, and saves the original data packets to the data storage layer;
[0118] S2: The real-time computing layer obtains preprocessed data from the distributed message system, obtains basic features from the data and extracts statistical features, and then adds the statistical features and protocol features to the basic features to form a total features, and then save the total features to the data storage layer;
[0119] S3: The data analysis layer obtains the general features from the data storag...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com