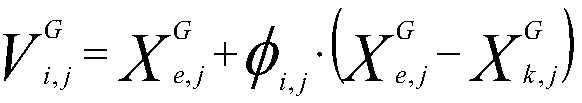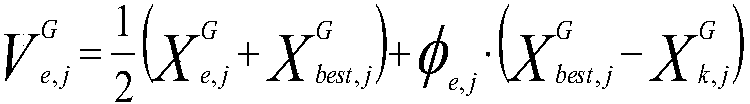A DDoS attack detection method based on an intelligent bee colony algorithm
A bee colony algorithm and attack detection technology, applied in the field of cloud security, can solve problems such as no very suitable solution, rare, wide range of attacks, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0060] The present invention will be further elaborated below by describing a preferred specific embodiment in detail in conjunction with the accompanying drawings.
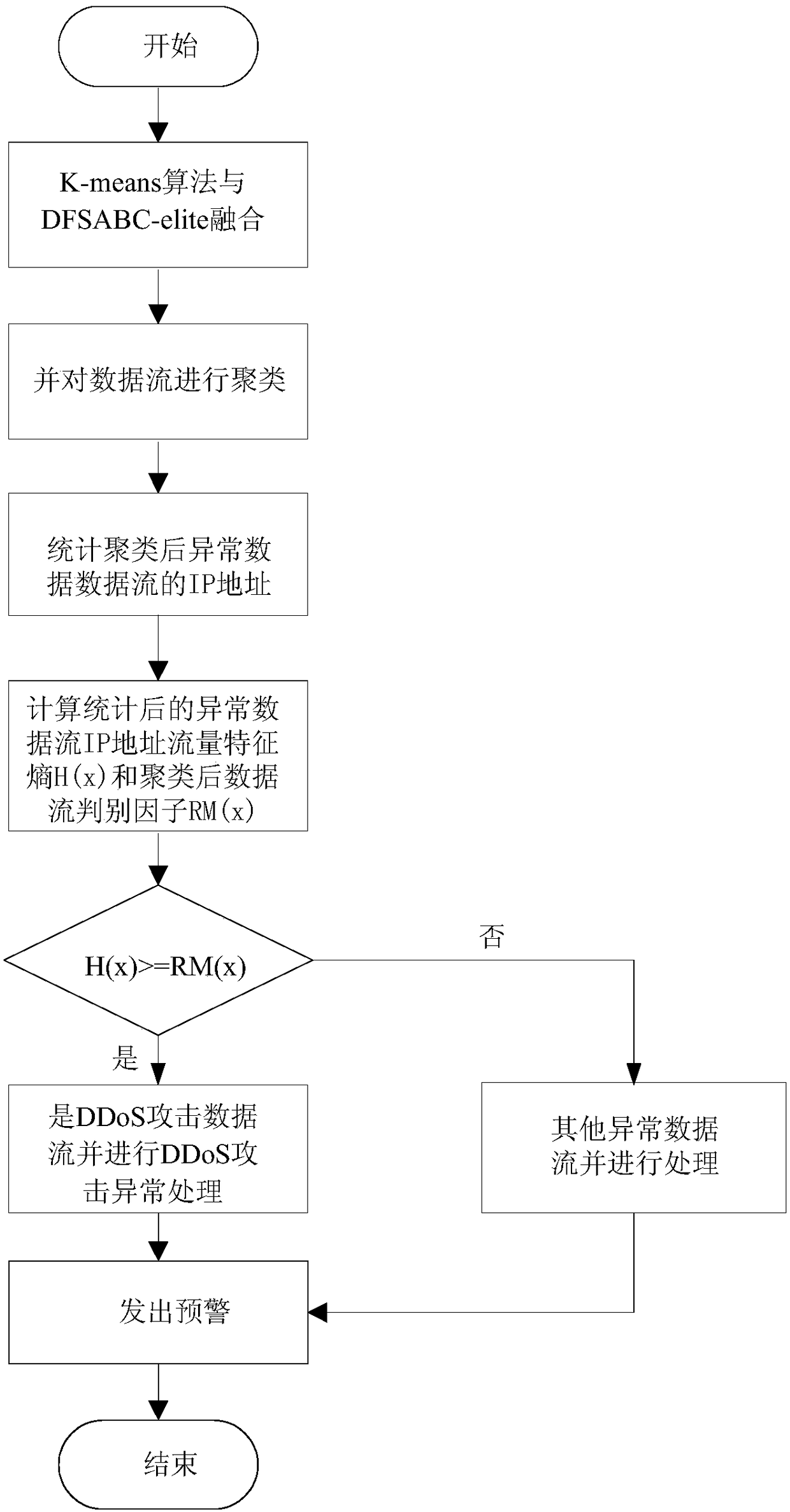
[0061] Such as figure 1 As shown, a kind of DDoS attack detection method based on the intelligent bee colony algorithm of the present invention, this method has obviously improved the performance effect in terms of intra-class compactness, inter-class separation, clustering accuracy, algorithm time-consuming and DDoS detection accuracy . The detection method includes the following process:
[0062] Step S1, merging the clustering algorithm K-means and DFSABC_elite, using the advantage of DFSABC_elite to jump out of the local optimum to improve the defect that the clustering algorithm K-means is overly dependent on the original cluster center.
[0063] Step S2. According to the clustering result, the normal flow data flow and the abnormal flow data flow are respectively clustered, and each is classified into one...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com