Equipment control method, device, server and system
A device control and server technology, applied in the field of device control methods, devices and servers, can solve problems such as potential safety hazards and data leakage, and achieve the effects of preventing security vulnerabilities, reducing energy consumption, and preventing experimental data leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
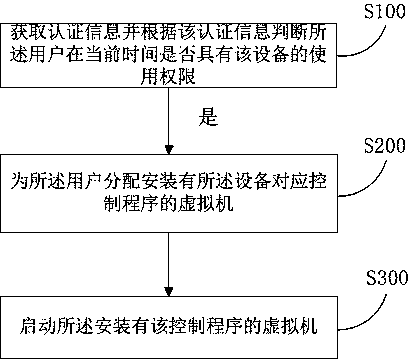
[0099] Such as figure 1 As shown, according to an aspect of the embodiments of the present invention, a device control method is provided, the method comprising:
[0100] S100: Obtain authentication information and judge whether the user has the right to use the device at the current time according to the authentication information, the authentication information including user name, password, and device identification;
[0101] S200: If the user has the right to use the device at the current time, allocate a virtual machine installed with a control program corresponding to the device to the user;
[0102] S300: Start the virtual machine installed with the control program.
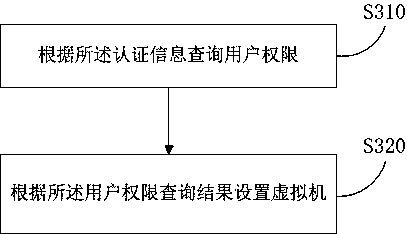
[0103] Specifically, the authentication information of the user is obtained, and the authentication information includes user name, password, and device identification; according to the authentication information, it is queried whether the user has the right to use the device corresponding to the device i...
specific Embodiment approach
[0148] Specifically, a specific implementation manner of the method includes:
[0149] Obtain authentication information, where the authentication information includes a user name, password, and device identification;
[0150] judging whether the user is a legal user according to the authentication information;
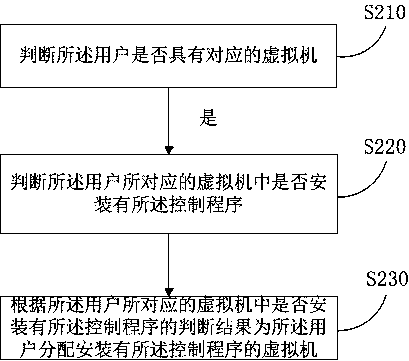
[0151] If the user is a legal user, determine whether the user has the right to use the device at the current time;
[0152] If the user has the right to use the device at the current time, determine whether the user has a corresponding virtual machine;
[0153] If the user has a corresponding virtual machine, determine whether the control program is installed in the virtual machine corresponding to the user;
[0154]If the control program corresponding to the device is not installed in the virtual machine corresponding to the user, determine whether the virtual machine operating system corresponding to the user is compatible with the control program;
[0155] If t...
Embodiment 2
[0165] Such as Figure 9 As shown, according to an aspect of yet another embodiment of the present invention, an equipment control device is provided, the device comprising:
[0166] Judging module 201, configured to obtain authentication information and judge whether the user has the right to use the device at the current time according to the authentication information, the authentication information including user name, password, and device identification;
[0167] An allocation module 202, configured to allocate a virtual machine installed with a control program corresponding to the device to the user if the user has the right to use the device at the current time;
[0168] The starting module 203 is configured to start the virtual machine installed with the control program.
[0169] When users use the device control program in the virtual machine, they do not need to arrange a physical machine on the laboratory site, but only need to connect to the virtual machine throug...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com