Network Behavior System Based on Simulation and Virtual Reality
A network security system, network technology, applied in the direction of transmission system, database model, data processing input/output process, etc., can solve the problem of insufficient number or speed of attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
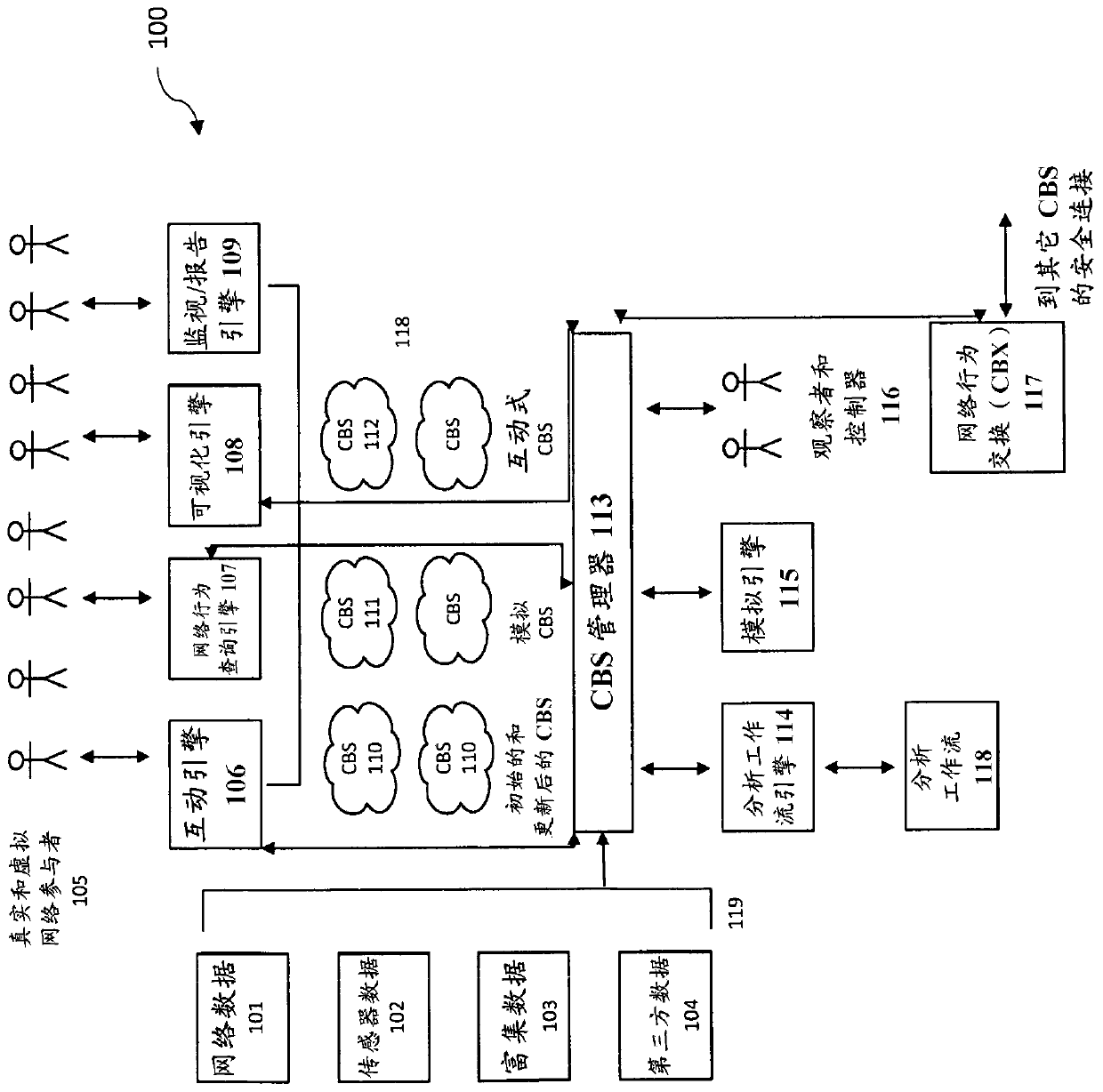
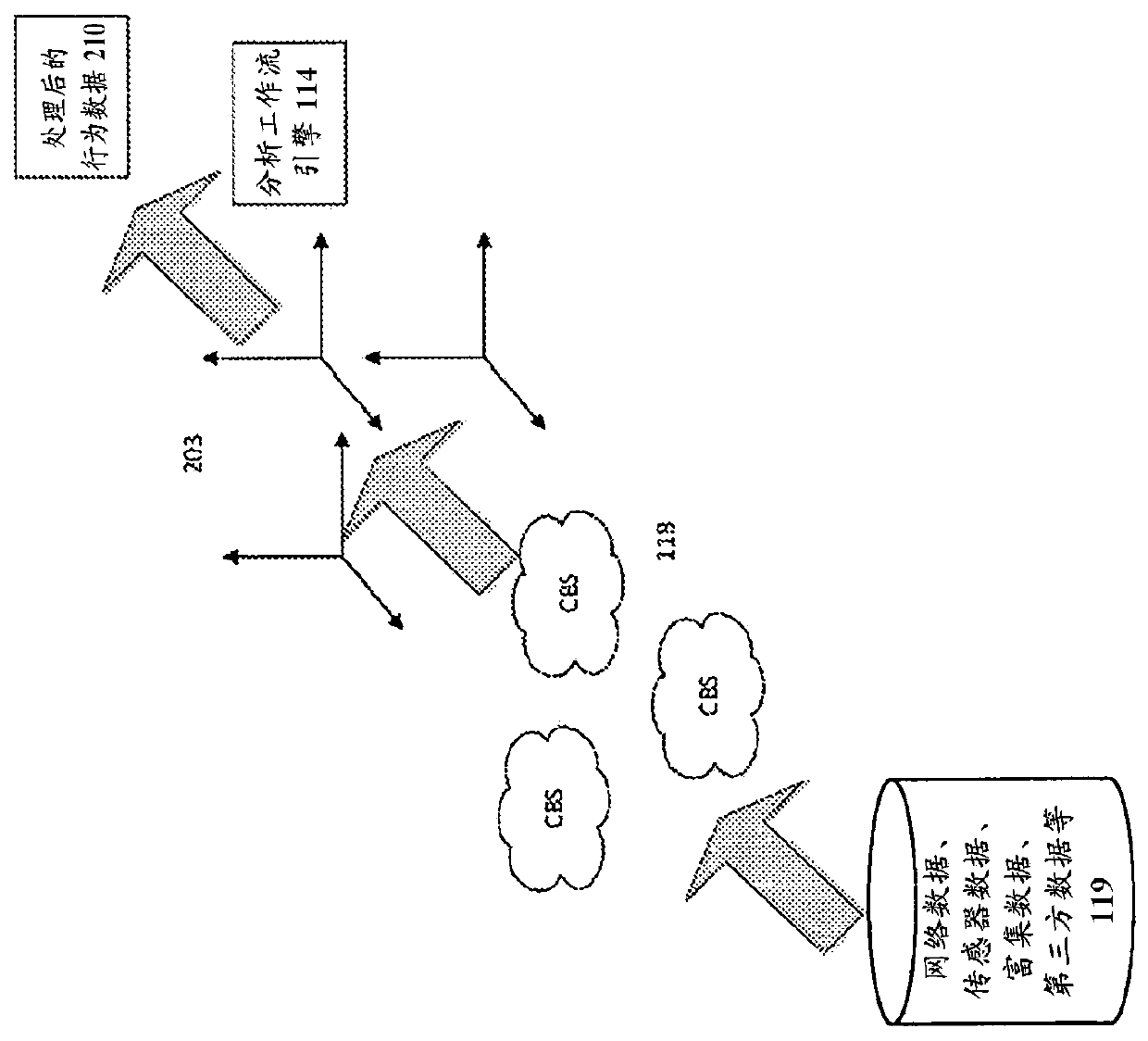
[0036] In some embodiments, simulation and virtual reality systems are used to enhance operational capabilities and training of cyber defenders by sharing with each other behavior-related information, including observed behavior-related information, calculated Behavior-related information and behavior-related information generated when multiple real or virtual network participants from one or more organizations participate in scenarios, simulations, and virtual reality environments.
[0037] In some embodiments, behavior-related information is exchanged in a secure and privacy-preserving manner using a networked behavior exchange, so that two or more organizations can exchange information as part of scenarios, simulations, and virtual reality environments to enhance training, improve organizational or improve the defenses of multiple organizations sharing information.
[0038] cyberspace
[0039] Some embodiments of the cybersecurity system are based on the cyber behavior spa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com