Access behavior data processing method, system and device, and readable storage medium
A data processing and behavior technology, applied in the electronic field, can solve the problems of data redundancy and low user credit coverage.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
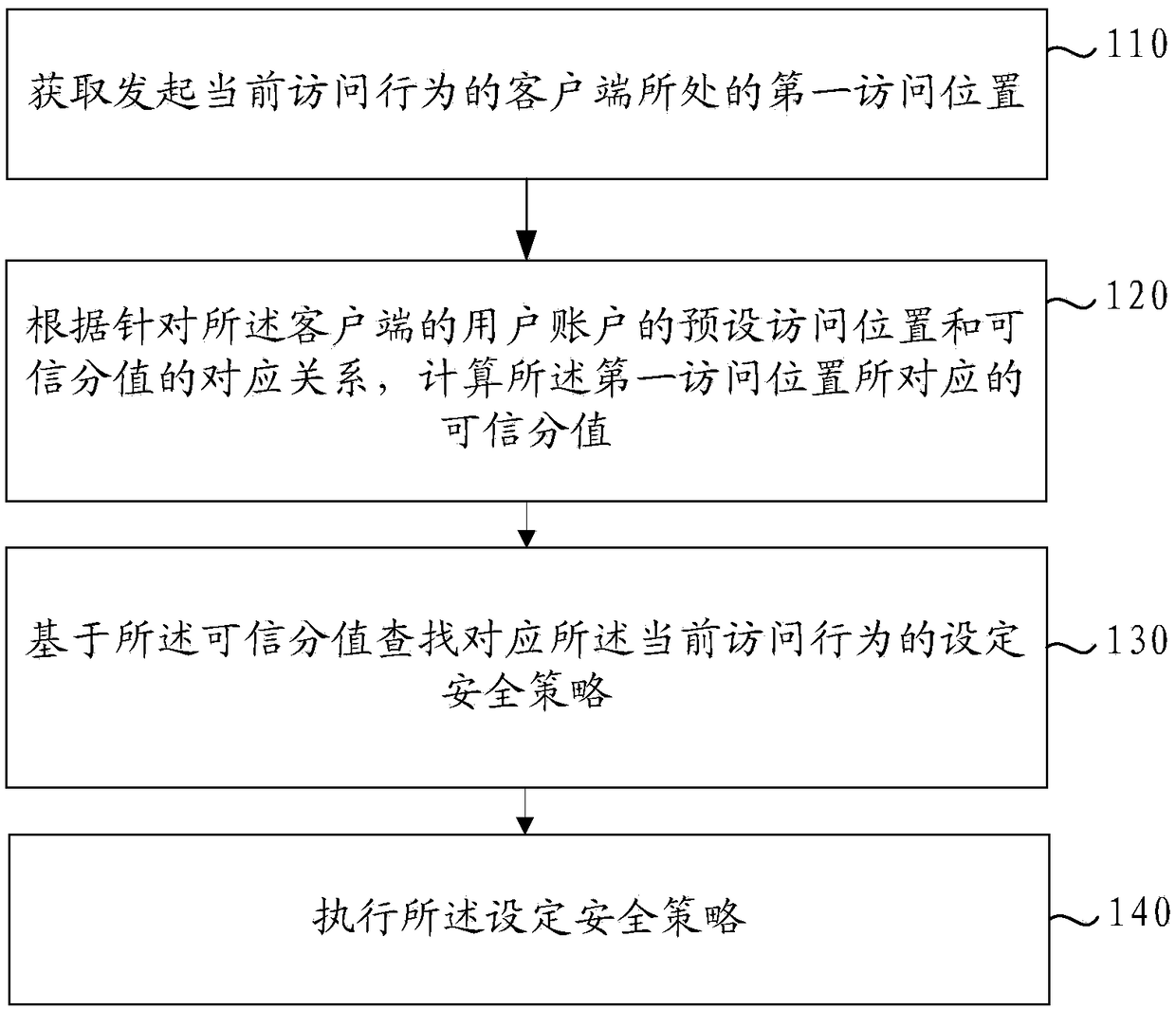
[0037] refer to figure 1 , which shows a flow chart of the steps of a method for processing access behavior data, the specific steps of which are as follows:
[0038] Step 110, acquiring the first access location where the client that initiates the current access behavior is located.
[0039] In the embodiment of the present invention, the corresponding relationship between the access location and the trusted score may be preset for the user account of the application in advance. In practical applications, according to the historical access behavior and the corresponding access location recorded by the user after using the application client, the corresponding relationship between the access location and the trustworthiness score is constructed.
[0040] It should be noted that the access location in this embodiment of the present invention may be an area. The block area can be identified by the Geohash code obtained by using the Geohash algorithm as described above. Such ...
Embodiment 2
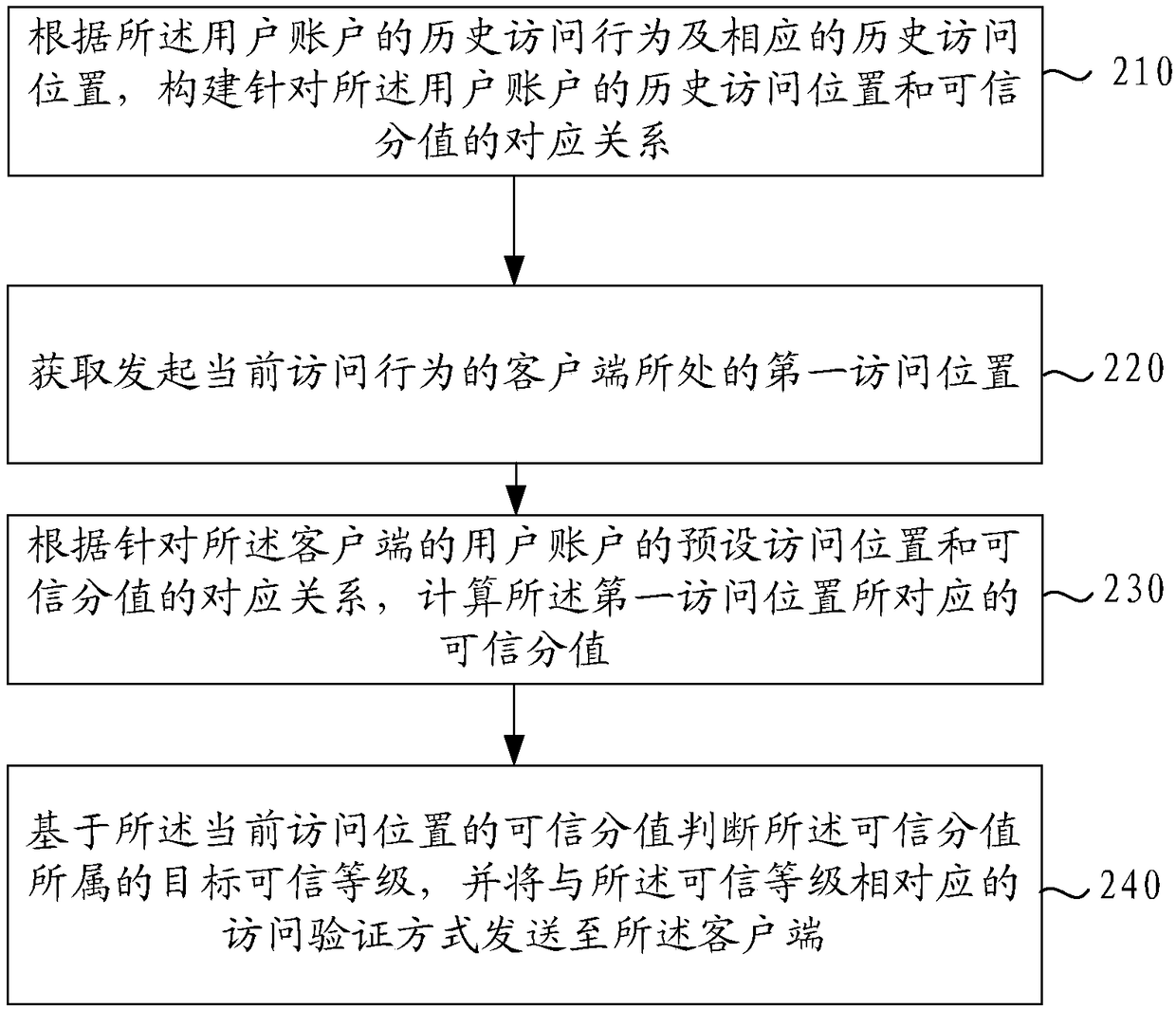
[0058] refer to figure 2 , which shows a flow chart of the steps of a method for processing access behavior data, the specific steps of which are as follows:
[0059] Step 210, according to the historical access behavior of the user account and the corresponding historical access location, construct the corresponding relationship between the historical access location and the credibility score for the user account.
[0060] In the embodiment of the present invention, after each user uses the application client to perform various aforementioned access behaviors, for example, after user account A makes payment and the payment is successful, the server can record when and where user account A made the payment. payment behavior. Then, the embodiment of the present invention can construct the corresponding relationship between the access location and the credibility score for the user account of each user according to the historical access behavior and the corresponding access lo...
Embodiment 3
[0214] refer to image 3 , which shows the relationship between modules in a structural block diagram of an access behavior data processing system, the system comprising:
[0215] Security pre-module 301, scoring module 302, business module 303, among which
[0216] The security front module 301 includes an access location acquisition submodule 3011 and a security policy search submodule 3012,
[0217] The access location acquisition submodule 3011 is used to acquire the first access location where the client that initiates the current access behavior is located;
[0218] The security policy lookup submodule 3012 is configured to look up a set security policy corresponding to the current access behavior based on the credibility score;
[0219] The scoring module 302 includes a credible score acquisition sub-module 3021,
[0220] The credible score acquisition sub-module 3021 is used to calculate the credible score corresponding to the first access location according to the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com