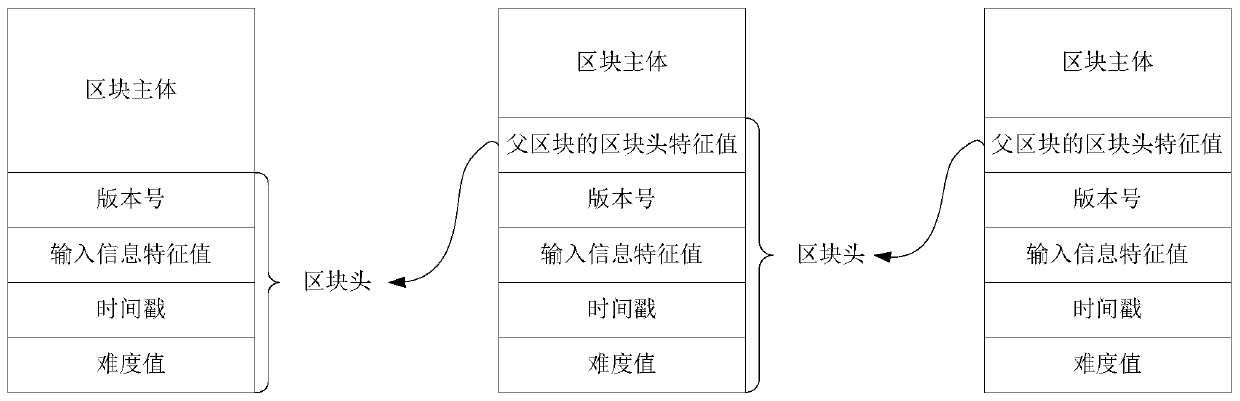
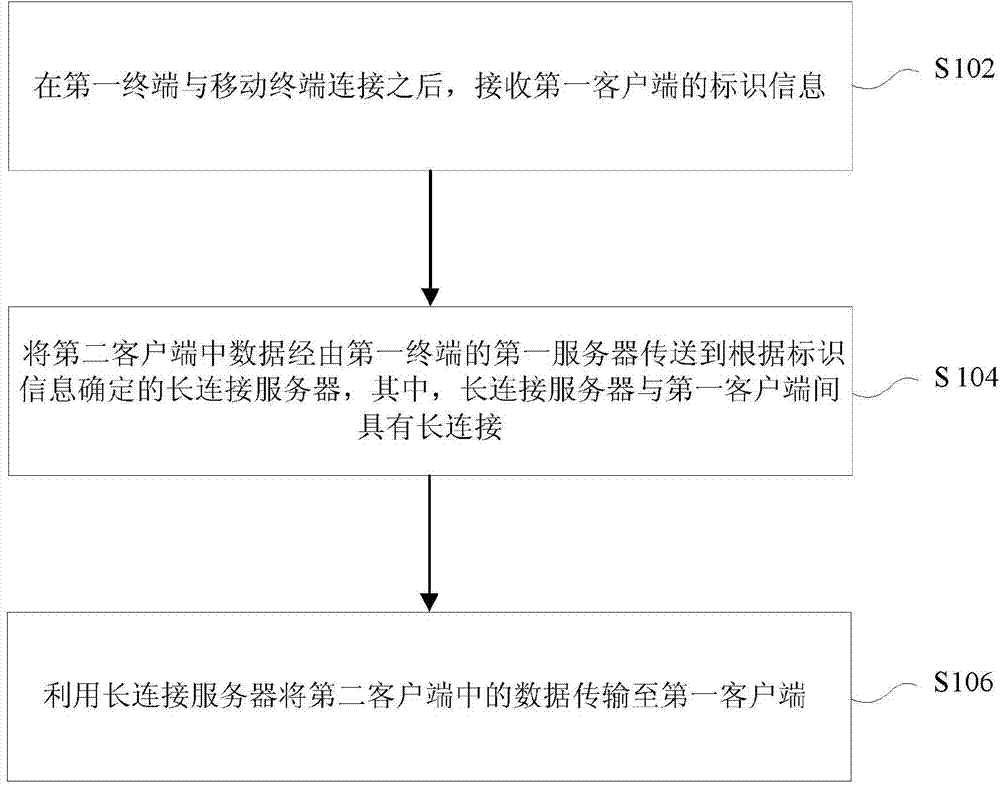
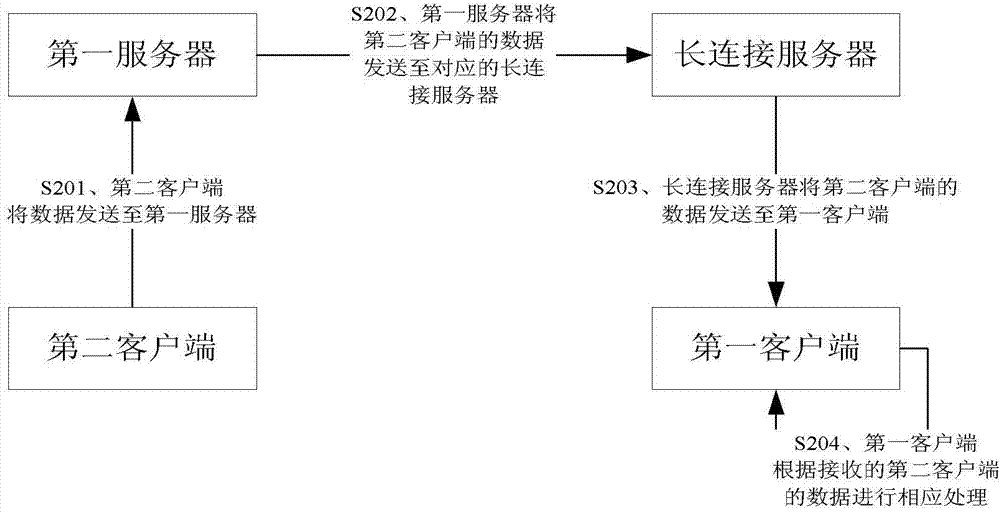
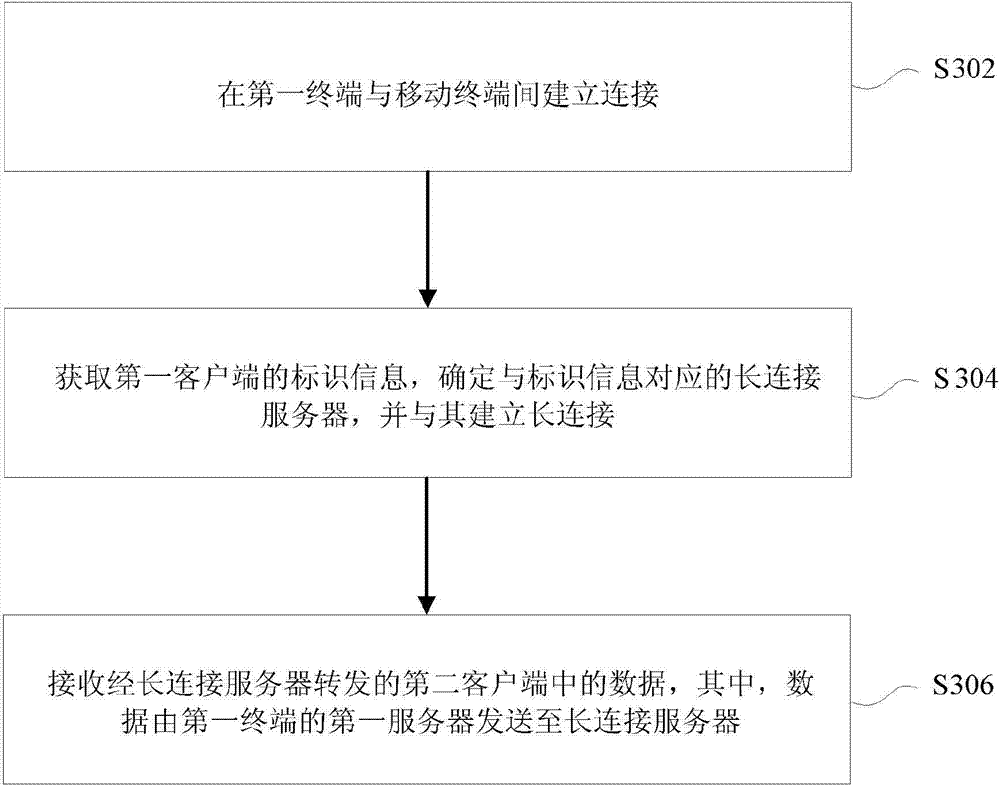
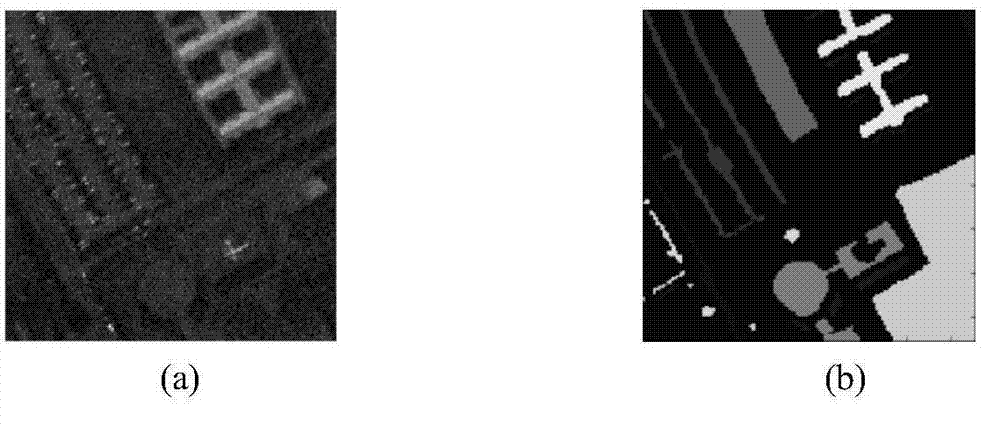
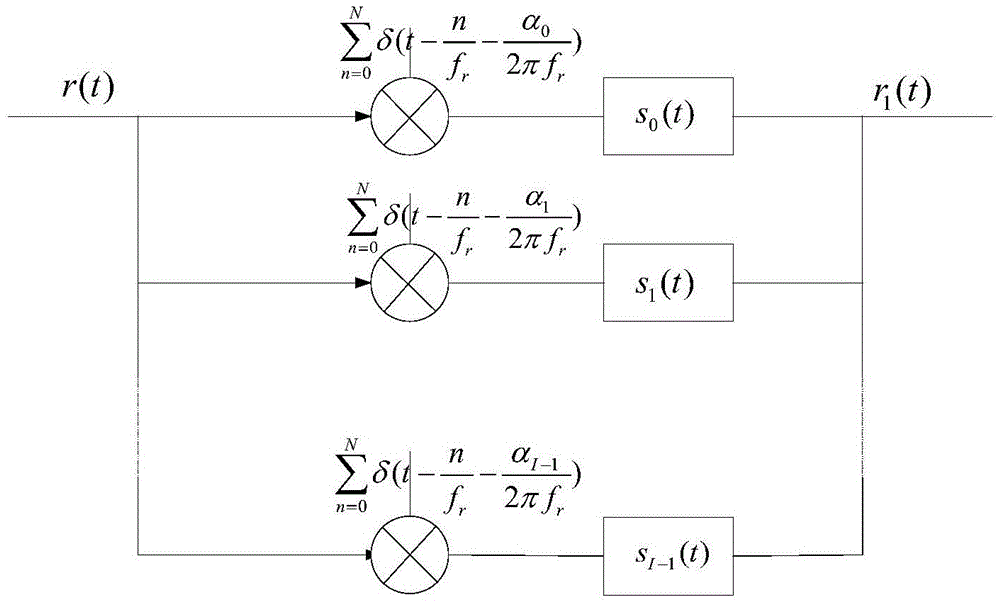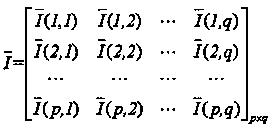Patents
Literature
100results about How to "Avoid data redundancy" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
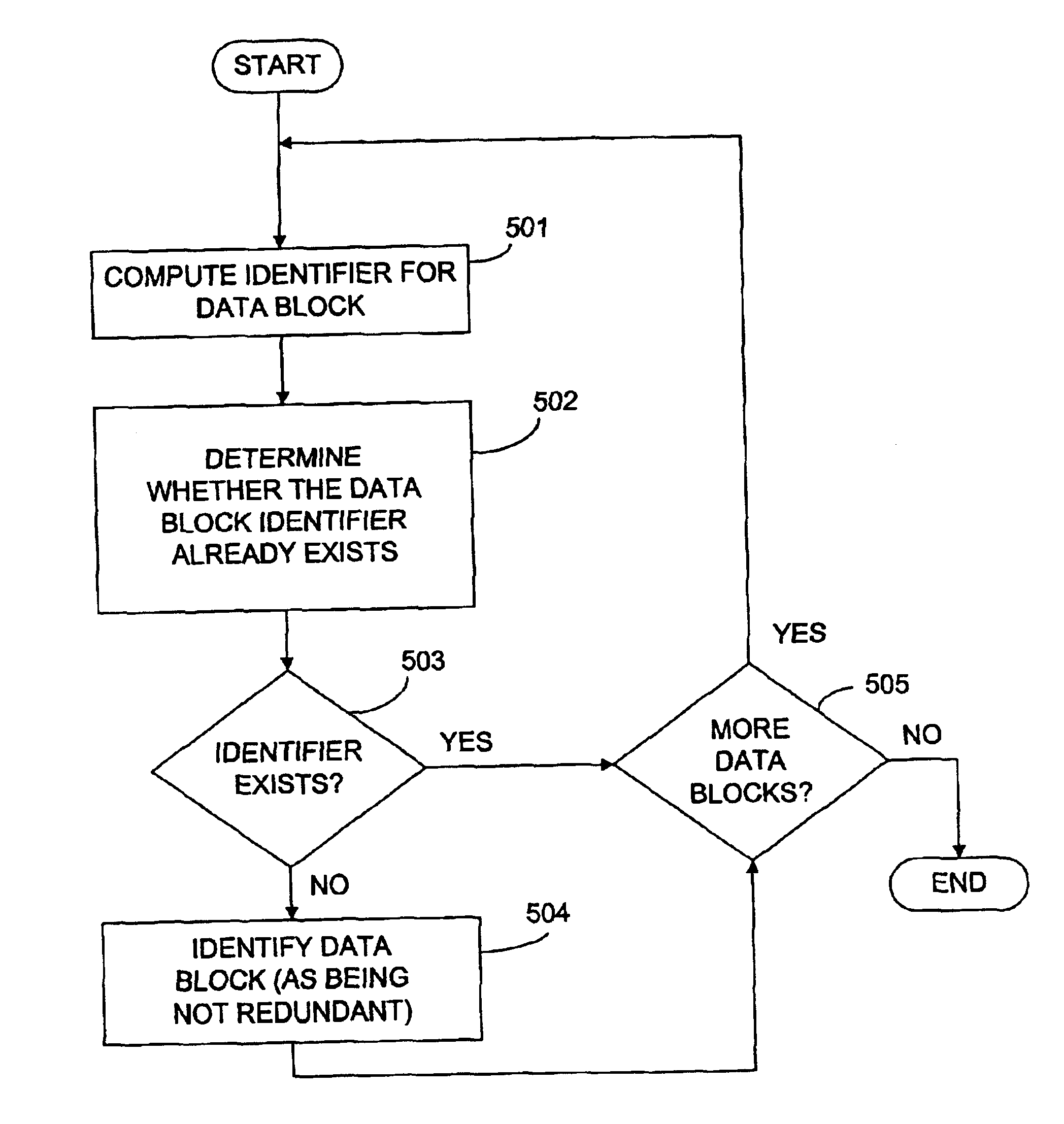
Methods and systems for eliminating data redundancies
InactiveUS6889297B2Removing data redundancySave memory spaceData processing applicationsError detection/correctionData miningData redundancy
Owner:ORACLE INT CORP
Central master data management
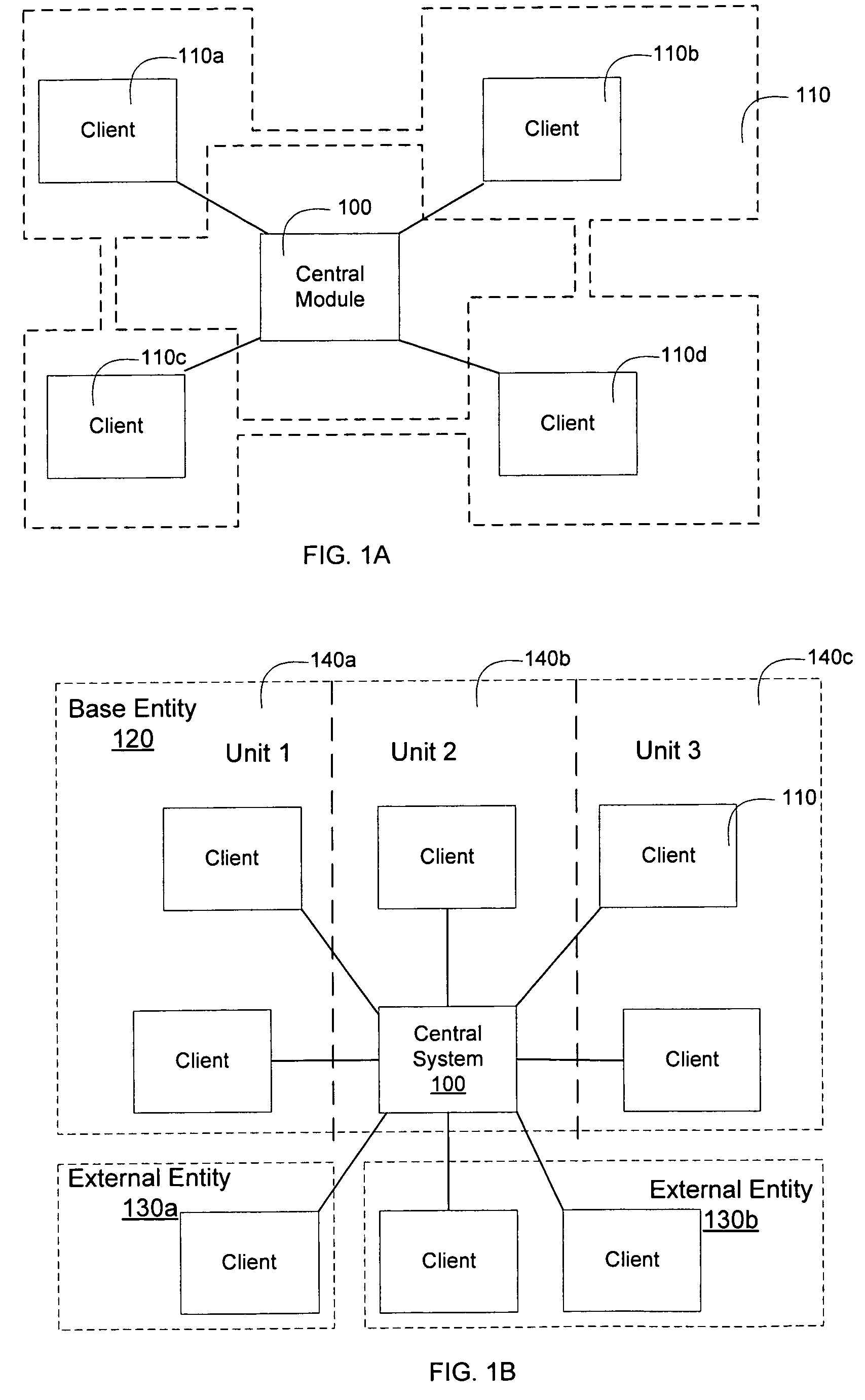
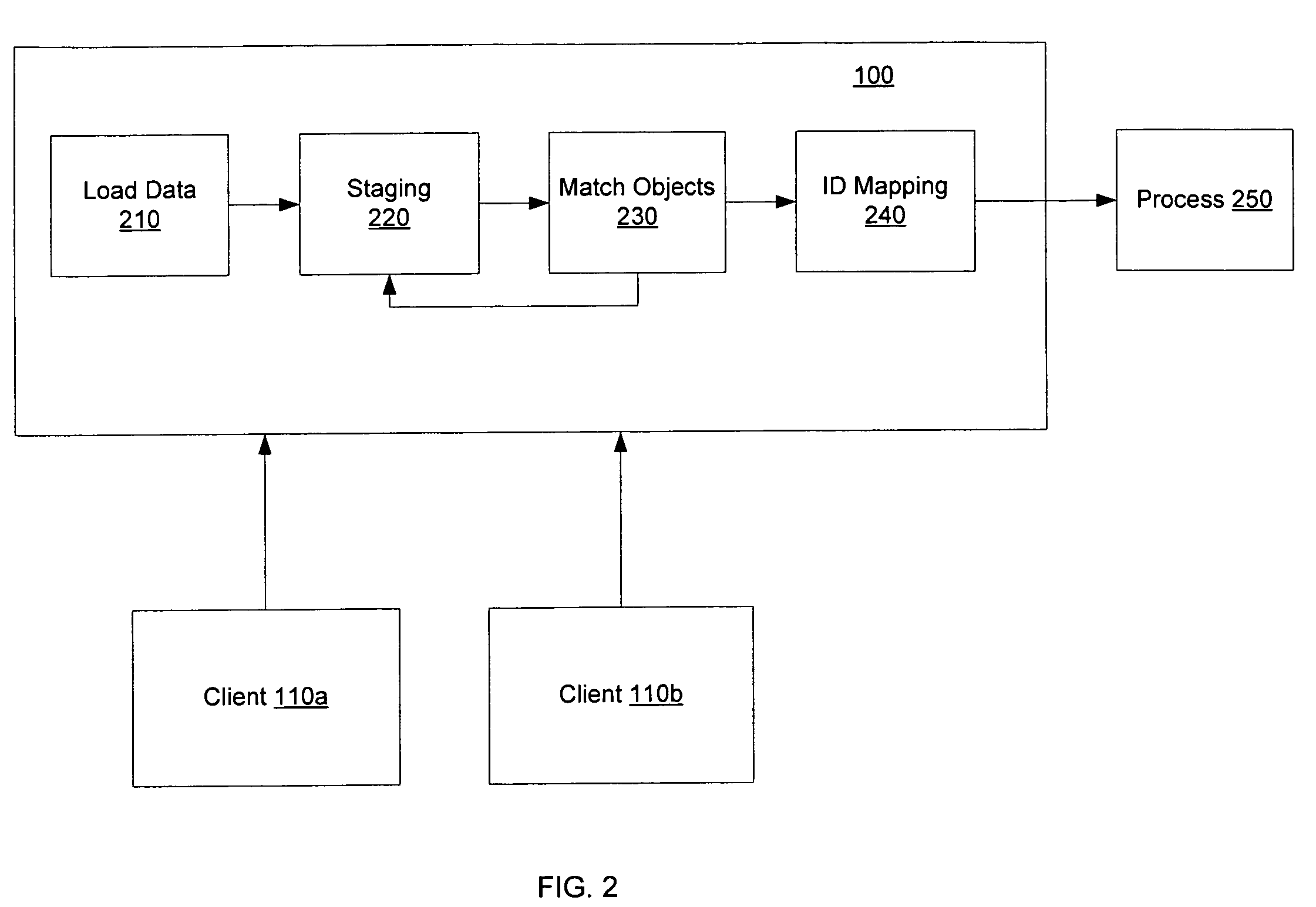
ActiveUS7509326B2Avoid data redundancyImproved cross-group reportingDigital data processing detailsDigital computer detailsObject definitionClient-side
Methods and apparatus, including computer program products, for sharing data. The technique includes creating at least one data object in a central system, the data object including a complete object definition, and dependencies to other objects, mapping at least one data object to other data objects in the central system, and distributing data objects from the central system to one or more client systems, where the one or more client systems.
Owner:SAP AG
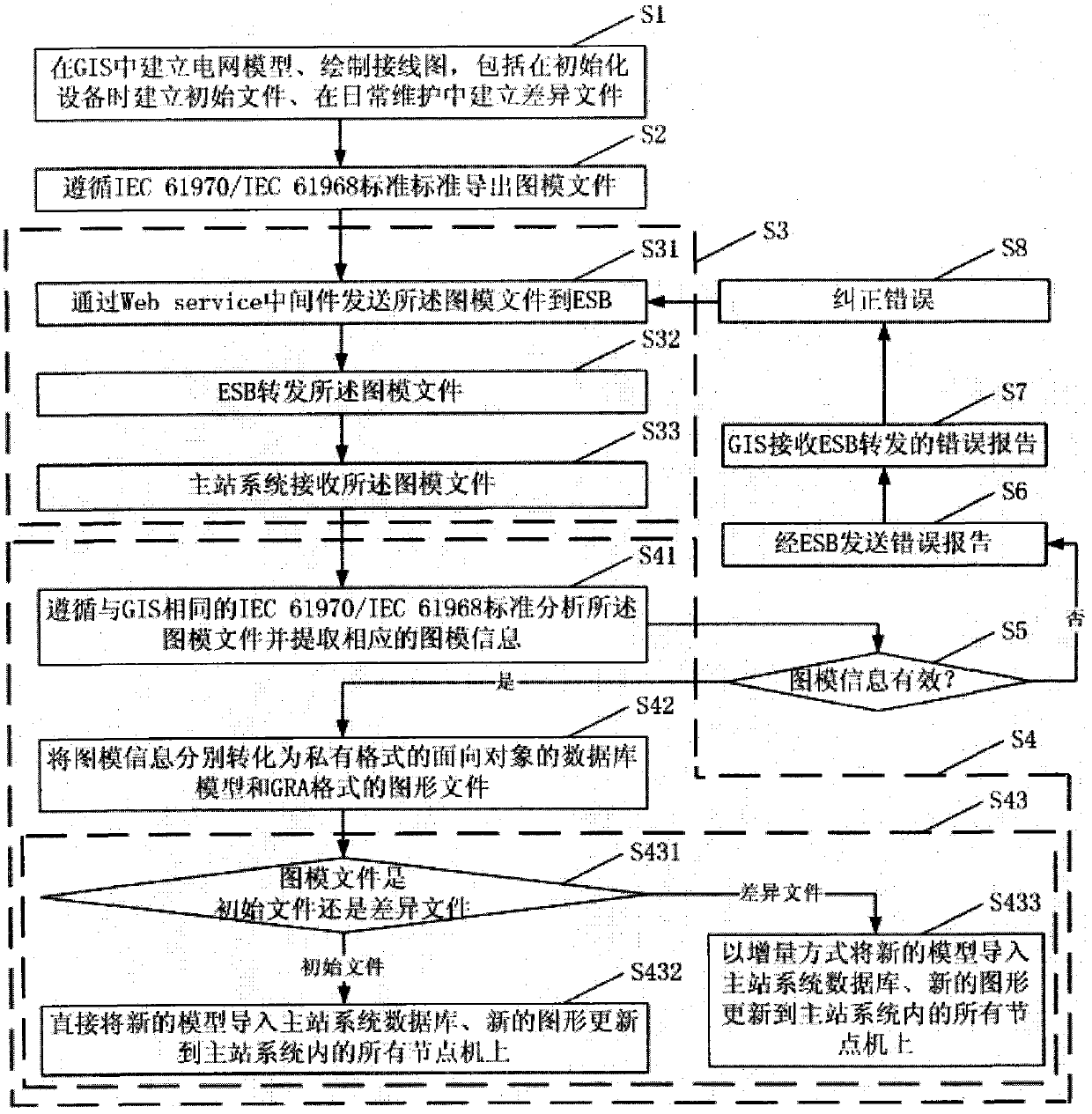
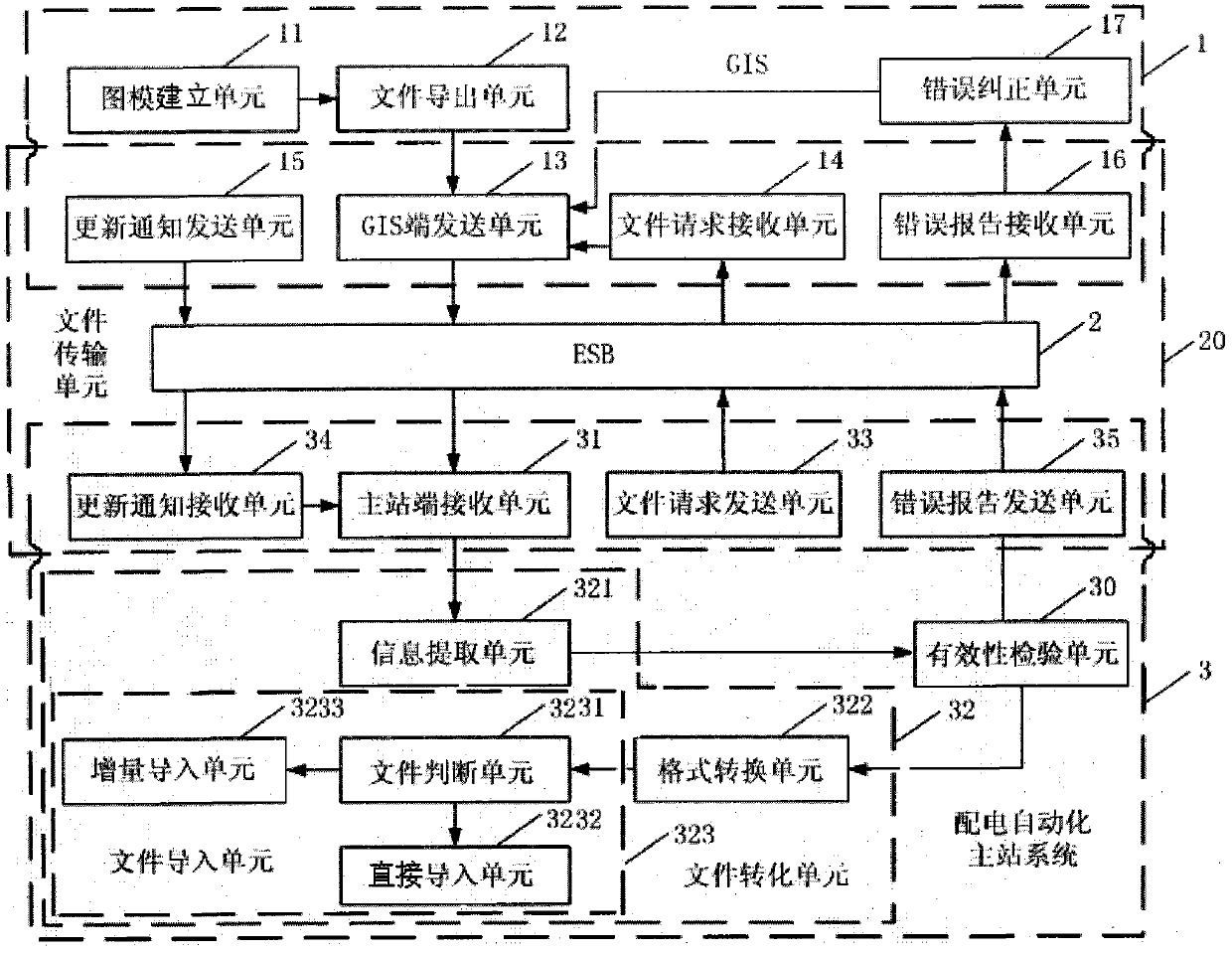
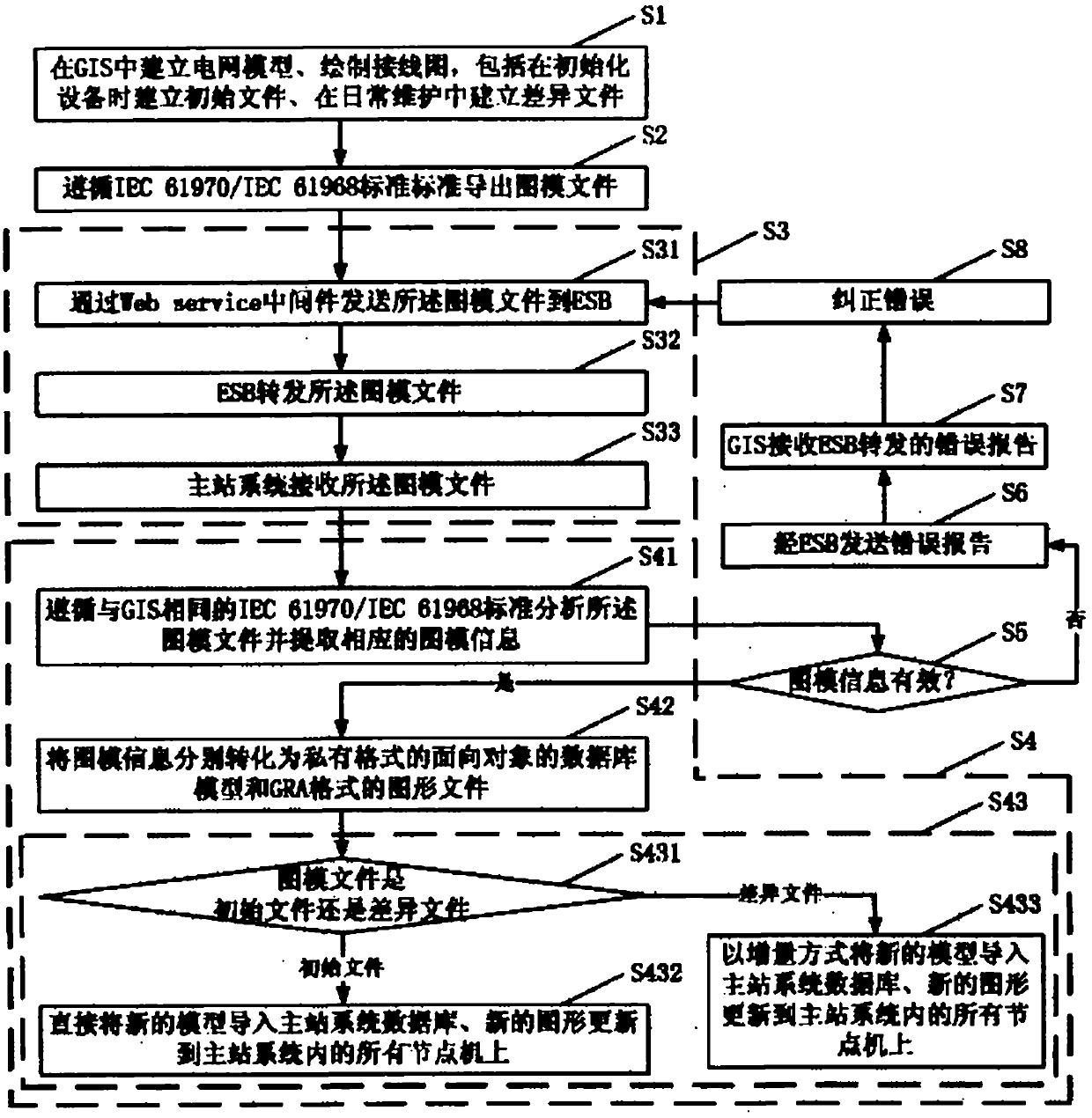
Method and system for realizing data sharing between power distribution main station system and power distribution GIS (Geographic Information System)
InactiveCN102185383AAchieve integrationRealize data sharingCircuit arrangementsTransmissionPower equipmentElectric power
The invention discloses a method for realizing data sharing between a power distribution main station system and a power distribution GIS (Geographic Information System). The method comprises the following steps of: establishing a pattern model: establishing a corresponding model scanning file and a figure scanning file for power equipment belonging to a power distribution grid in the GIS; exporting files: exporting the model scanning file and the figure scanning file into a model information file in the format of xml and a pattern information file in the format of SVG (Video Graphics Array) which follows the IEC 61970 / IEC 6196I standard; transmitting files: transmitting the exported model information file and the pattern information file from the GIS to the main station system; and converting files: after the main station system receives the model information file and the pattern information file, converting the files into a model file and a pattern file of private formats of the main station system for saving respectively. The invention further discloses a system for realizing data sharing between a power distribution main station system and a power distribution GIS. By adopting the method and the system, system combination and data sharing inside a power grid information system can be realized effectively, and the investment and maintenance costs are lowered greatly.
Owner:广东电网公司深圳供电局
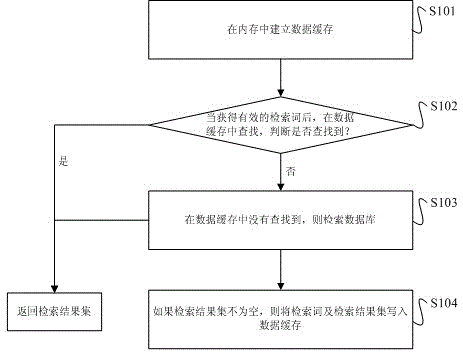
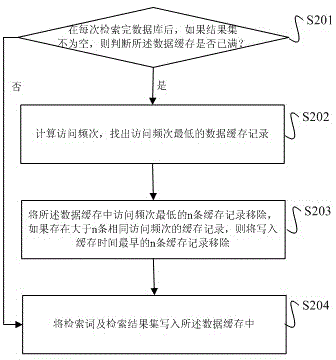
Method and device for increasing retrieval speed in database retrieval system
InactiveCN103336849AImprove retrieval speedImprove cache utilizationSpecial data processing applicationsResult setRetrieval result
The invention relates to a method and a device for increasing a retrieval speed in a database retrieval system and belongs to the technical field of database retrieval. The method comprises the following steps: establishing a data cache in an internal storage; after obtaining an index word, searching in the data cache; if a cache record of a corresponding index word is found in the data cache, generating and returning a retrieval result set according to the cache record and ending the retrieval at this time; if the cache record is not found in the data cache, retrieving the database and returning the retrieval result set; and if the retrieval result set is not empty, writing the index word and the retrieval result set into the data cache. The invention also discloses the device for increasing the retrieval speed in the database retrieval system. In the mode of caching after using, the device reduces the system resource consumed by establishing the cache and increases the use ratio of the cache. In the mode of caching the result set, the caching mechanism is more convenient and quick.
Owner:KUNMING UNIV OF SCI & TECH
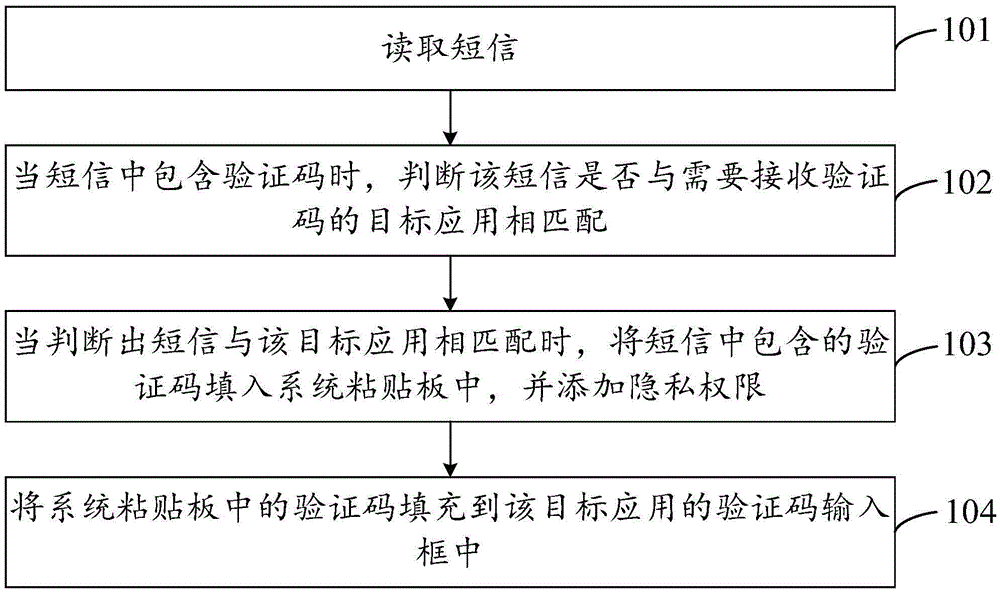
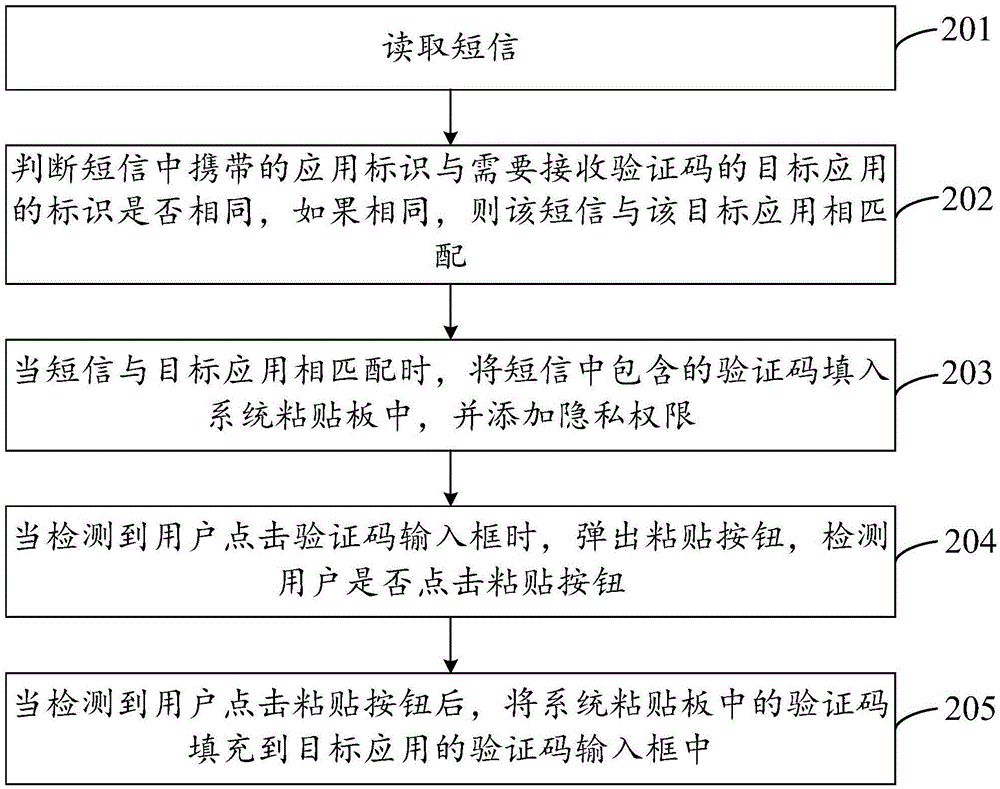
Verification code input method and device
InactiveCN105553663AIncrease privacy permissionsEasy to operateUser identity/authority verificationMessaging/mailboxes/announcementsComputer hardwareFilling-in
The invention provides a verification code input method and device, and the method comprises the steps: reading a short message; judging whether the short message is matched with a target application which needs to receive a verification code or not when the short message contains the verification code; enabling the verification code in the short message to be filled in a system paste board when the short message is matched with the target application, and adding privacy authority, wherein the privacy authority is used for shielding other applications different from the target application; and enabling the verification code in the system paste board to be filled in a verification input frame of the target application. In conclusion, the method can automatically analyzes the verification code, matched with the target application which needs to receive the verification code, from the content of the short message, and fills the verification code into the corresponding verification input frame. A user does not need to specially search the verification code from the short message, so the method and device are relatively simple in operation. In addition, the method adds privacy authority to the content of the system paste board, thereby preventing the leakage of the privacy of the user.
Owner:XIAOMI INC
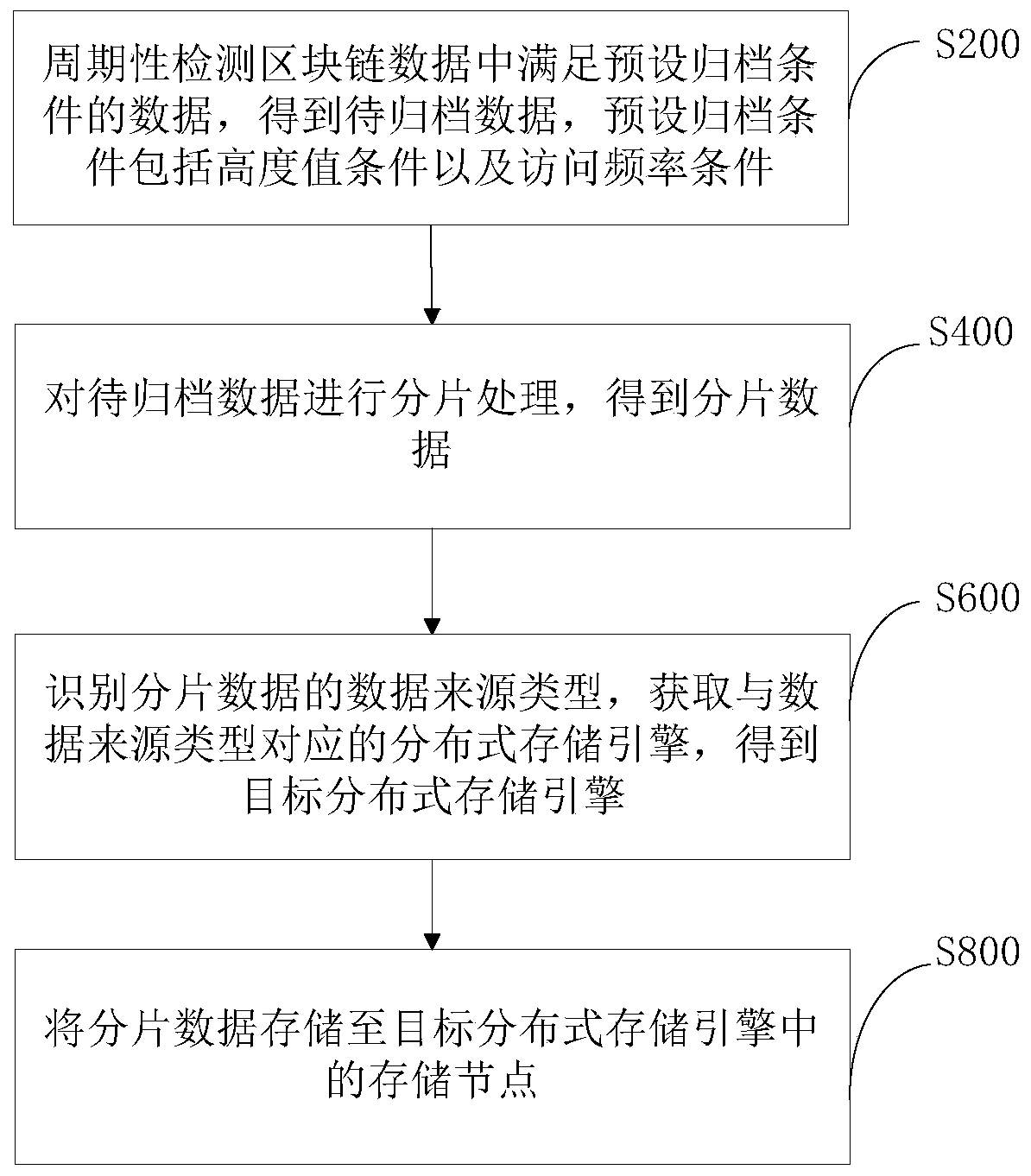
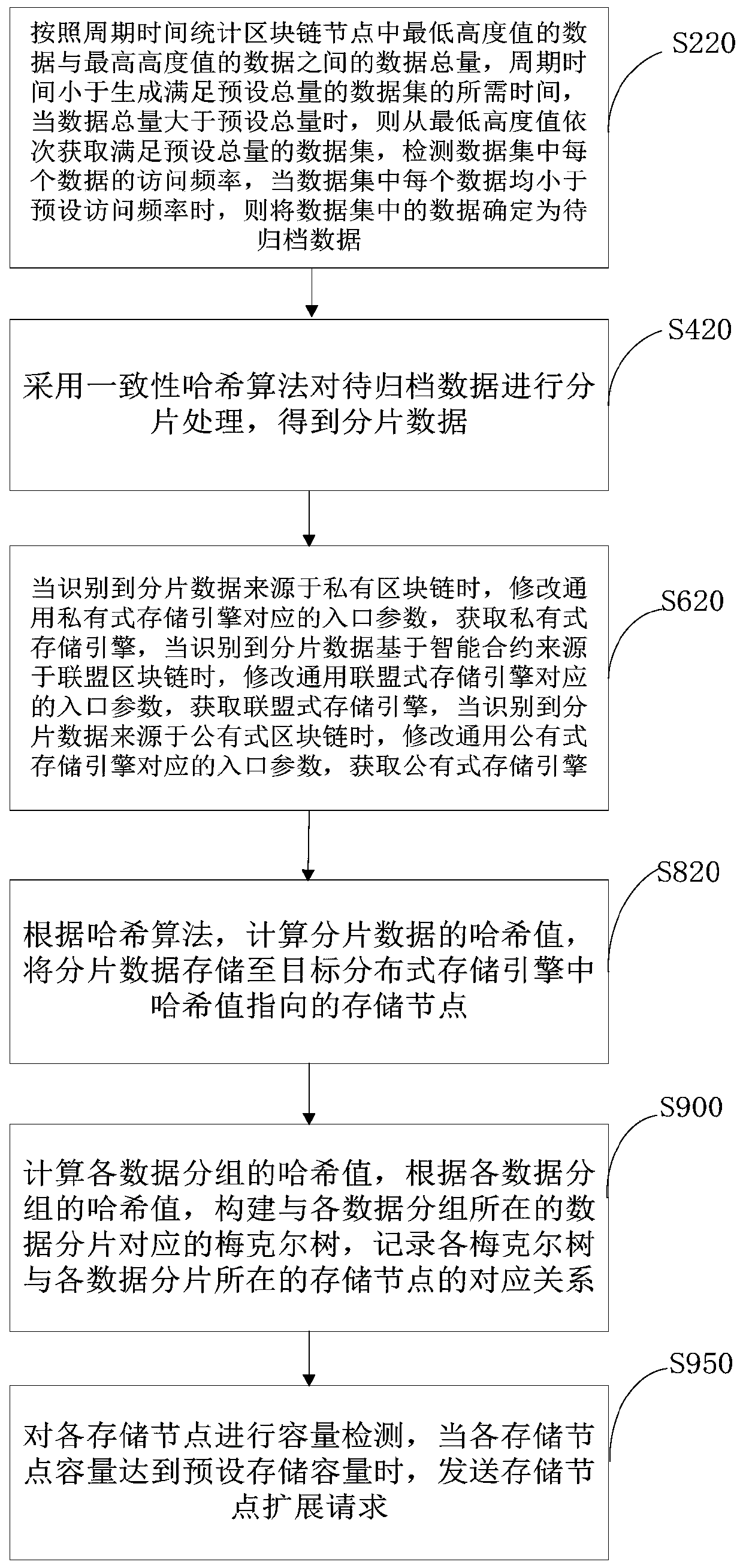
Block chain data archiving storage method and device, computer equipment and storage medium
PendingCN110442644AImprove processing efficiencyAchieve expansionDatabase distribution/replicationSpecial data processing applicationsLinear growthSource type
The invention relates to the field of block storage systems, and a blockchain data archiving storage method and device, computer equipment and a storage medium. The method comprises the following steps: periodically detecting to-be-archived data and fragmenting the to-be-archived data; and completing data archiving. Data redundancy is avoided, the storage mode can be flexibly selected according tothe fragmented data source type; the safety availability of the data is guaranteed, the fragmented data is distributed to the storage nodes in the corresponding distributed storage engines, the capacity expansion of the storage space of the block chain data is realized in a distributed storage mode, the requirement of the linear growth of the block chain data on the storage space is met, and thedata processing efficiency is improved.
Owner:ONE CONNECT SMART TECH CO LTD SHENZHEN
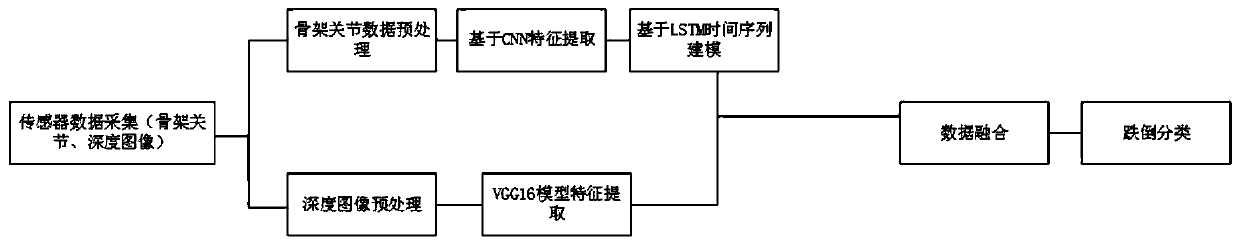
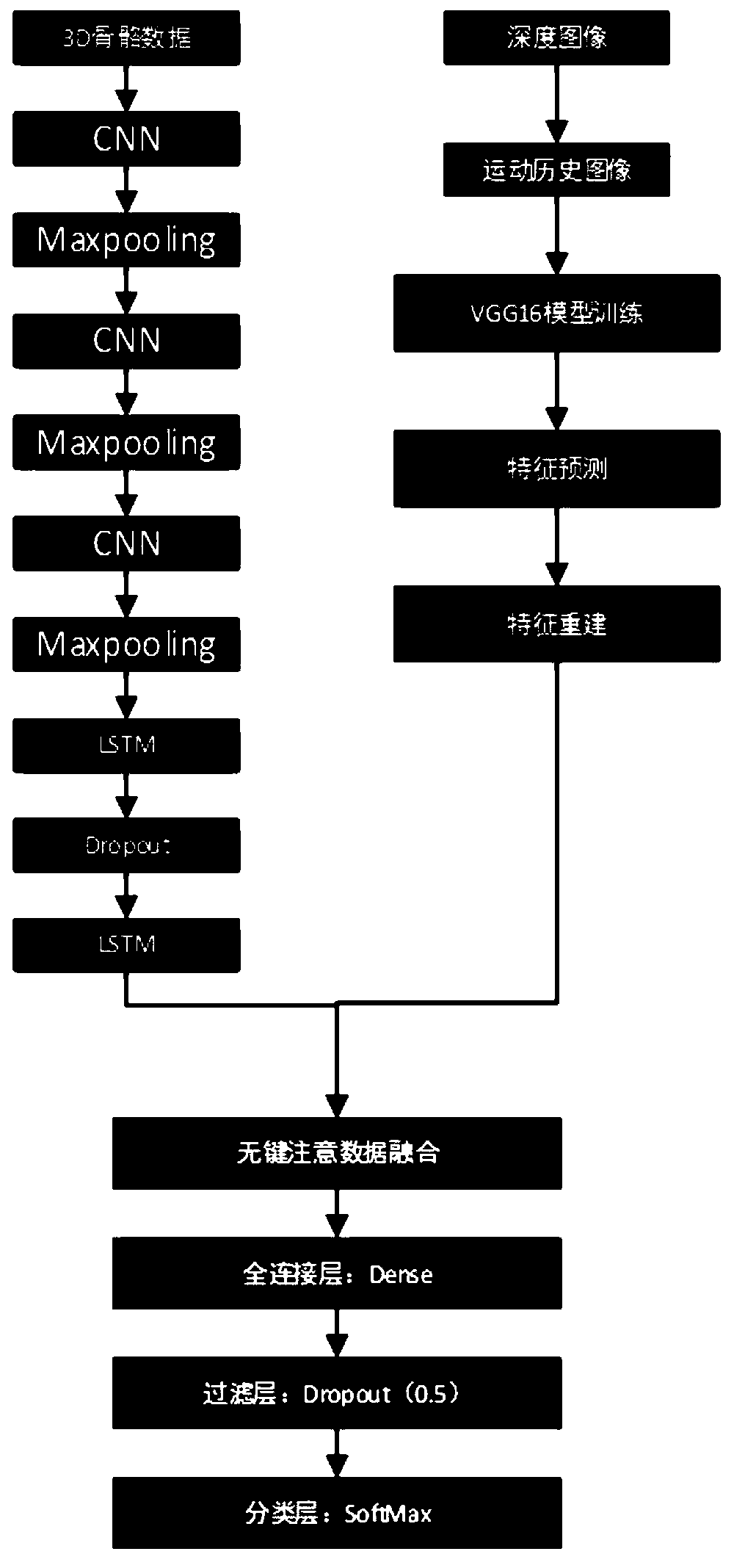
Human body tumble detection method based on multi-source heterogeneous data fusion
InactiveCN110633736AAvoid issues such as monitoring violations of human privacyAvoiding violations of human privacy and other issuesCharacter and pattern recognitionDiagnostic recording/measuringHuman bodyPattern recognition
The invention belongs to the field of human body tumble detection, and provides a human body tumble detection method based on multi-source heterogeneous data fusion. The method comprises the followingsteps: acquiring a behavior depth image and skeleton information of a human body through Kinect, and getting rid of constraints of a wearable sensor on selection of the sensor; secondly, solving theproblem that wearable sensors cannot be used in specific scenes such as bathrooms and toilets, and meanwhile, avoiding the problem that human privacy is invaded due to the fact that a common camera isused for monitoring; meanwhile, extracting features from multi-source heterogeneous data through a deep learning model, introducing keyless attention fusion into a data fusion mode, and avoiding dataredundancy and calculation complexity generated by data-level fusion. Compared with the prior art, the accuracy of tumble detection is remarkably improved.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Mobile agent acquisition and storage method suitable for Internet of things
InactiveCN101883444ARealize distributed collectionReduce difficultyNetwork topologiesTransmissionInteraction agentThe Internet
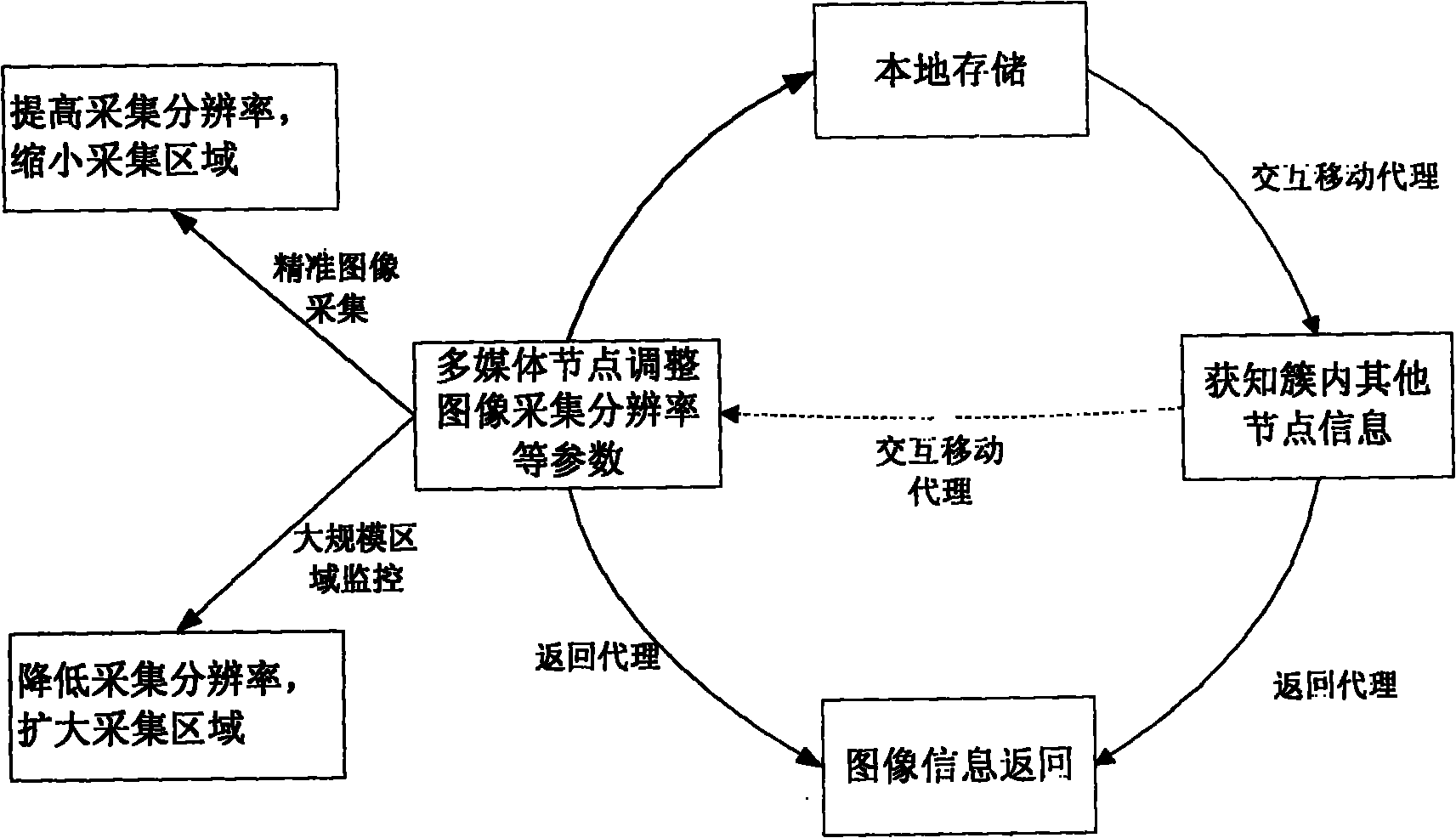
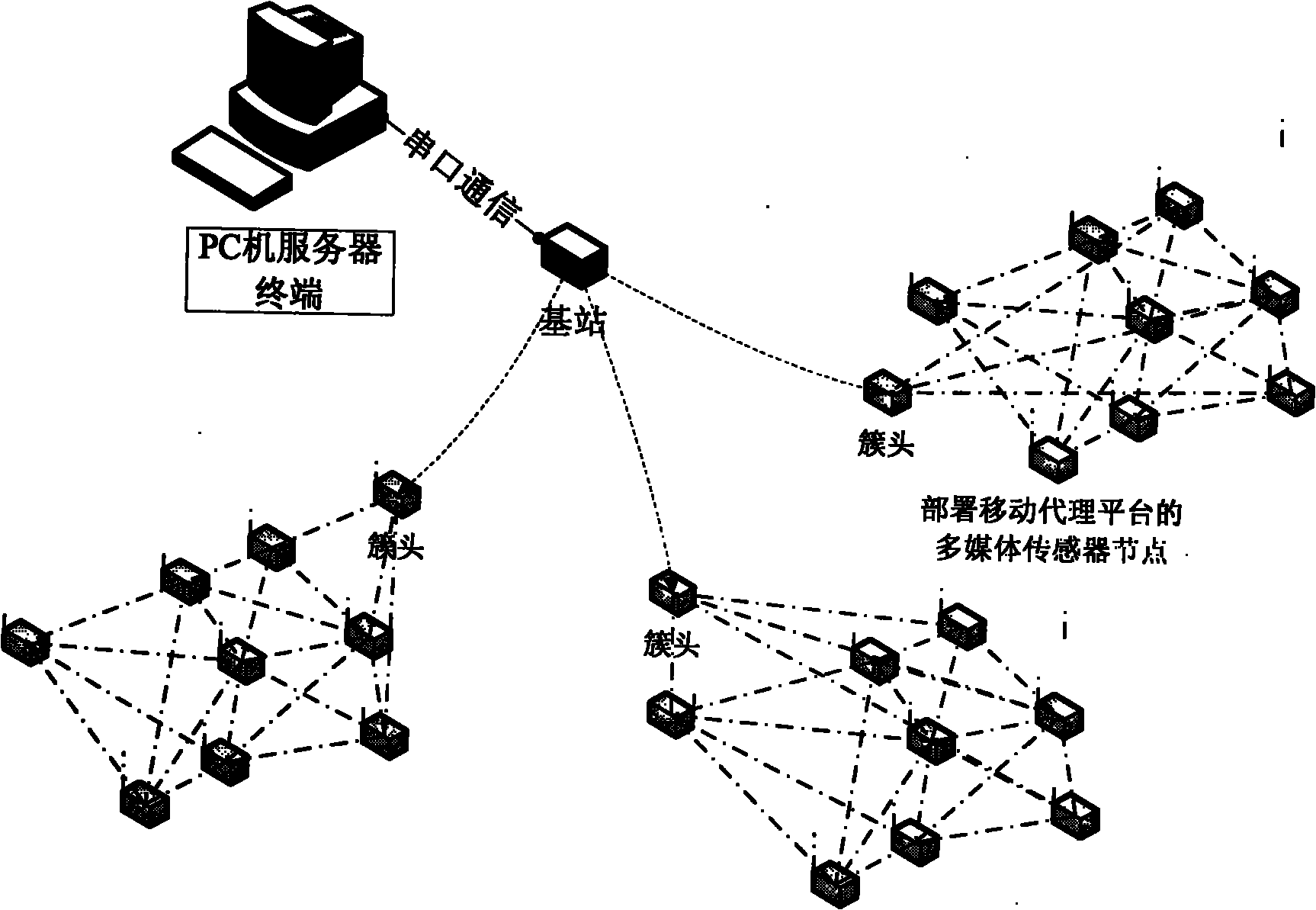
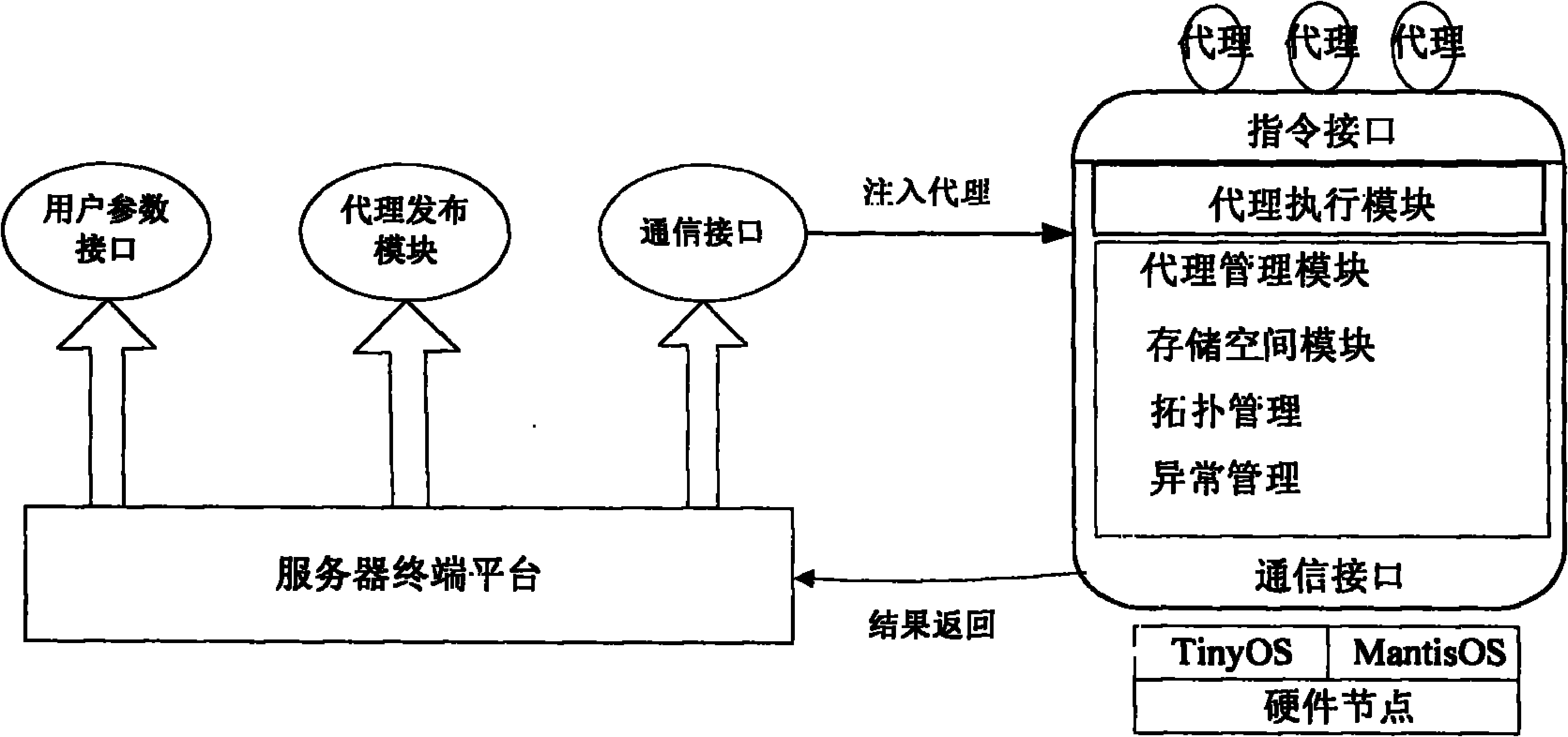
The invention relates to a mobile agent acquisition and storage system suitable for Internet of things, which is an acquisition and storage scheme applied to the Internet of things and is mainly used for solving the problems of large data transmission quantity, complex network task and the like under the environment of the Internet of things. The mobile agent storage and management system suitable for the Internet of things is developed and has the characteristics that: a multimedia node acquires image information in real time and stores the image information in a local storage space module; an interaction agent is generated by nodes, carries the image information identifier and the storage space information of the node, performs interaction on nodes in a traversal cluster and allows an acquisition node to adjust the working state per se according to the storage space information of other nodes; an inquiry agent is generated by user parameters and comprises all inquiry parameter information; after receiving the inquiry agent, a cluster head node generates a return agent traversal node according to task parameters and returns a matched image block to the cluster head node through the acquisition node; and the cluster head node directly returns an identifier-attached image block to a base station server and performs image fusion through a terminal so as to form a complete and clear monitoring area image.
Owner:NANJING UNIV OF POSTS & TELECOMM
Device and method for monitoring an electrical network
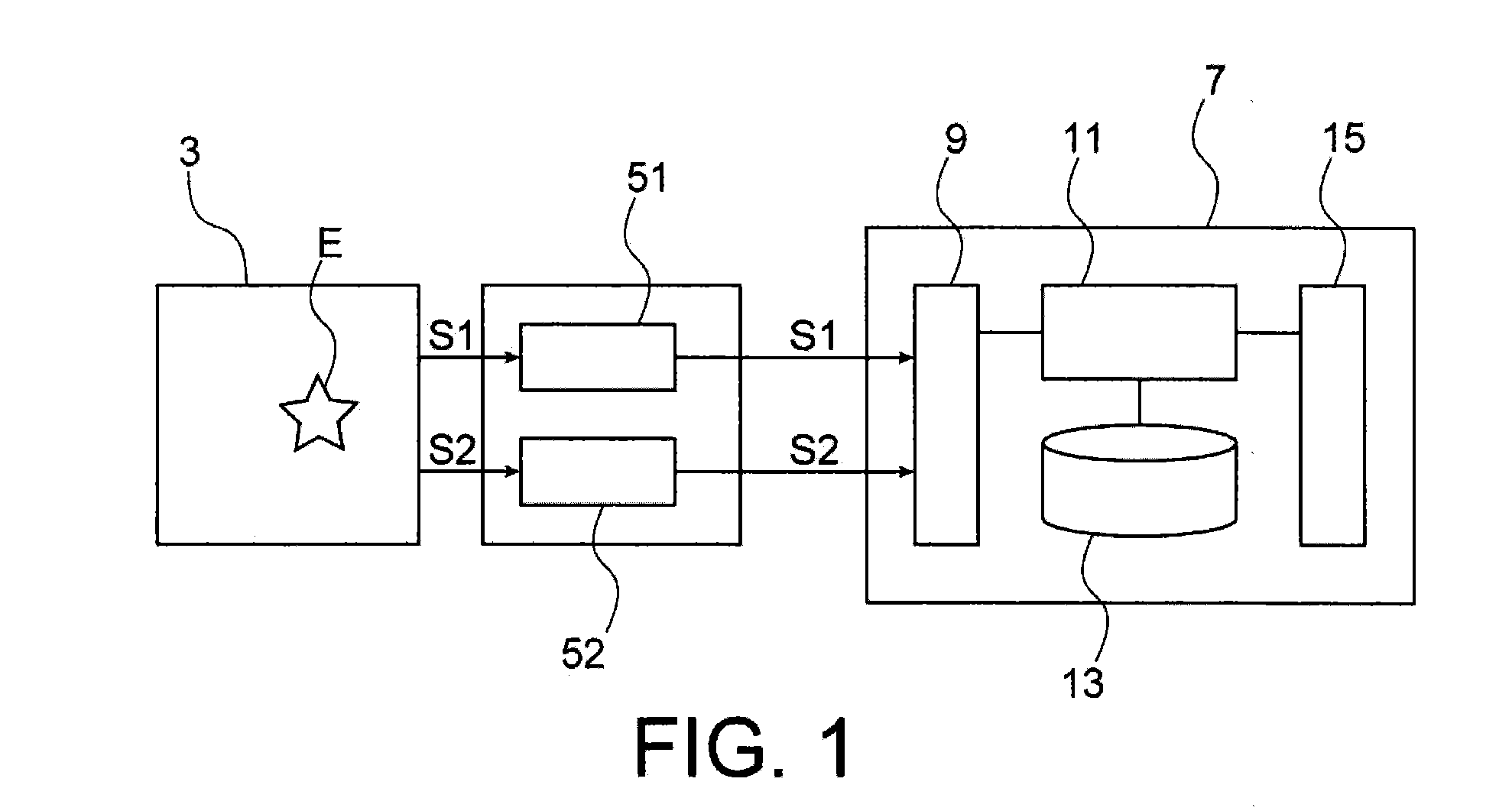
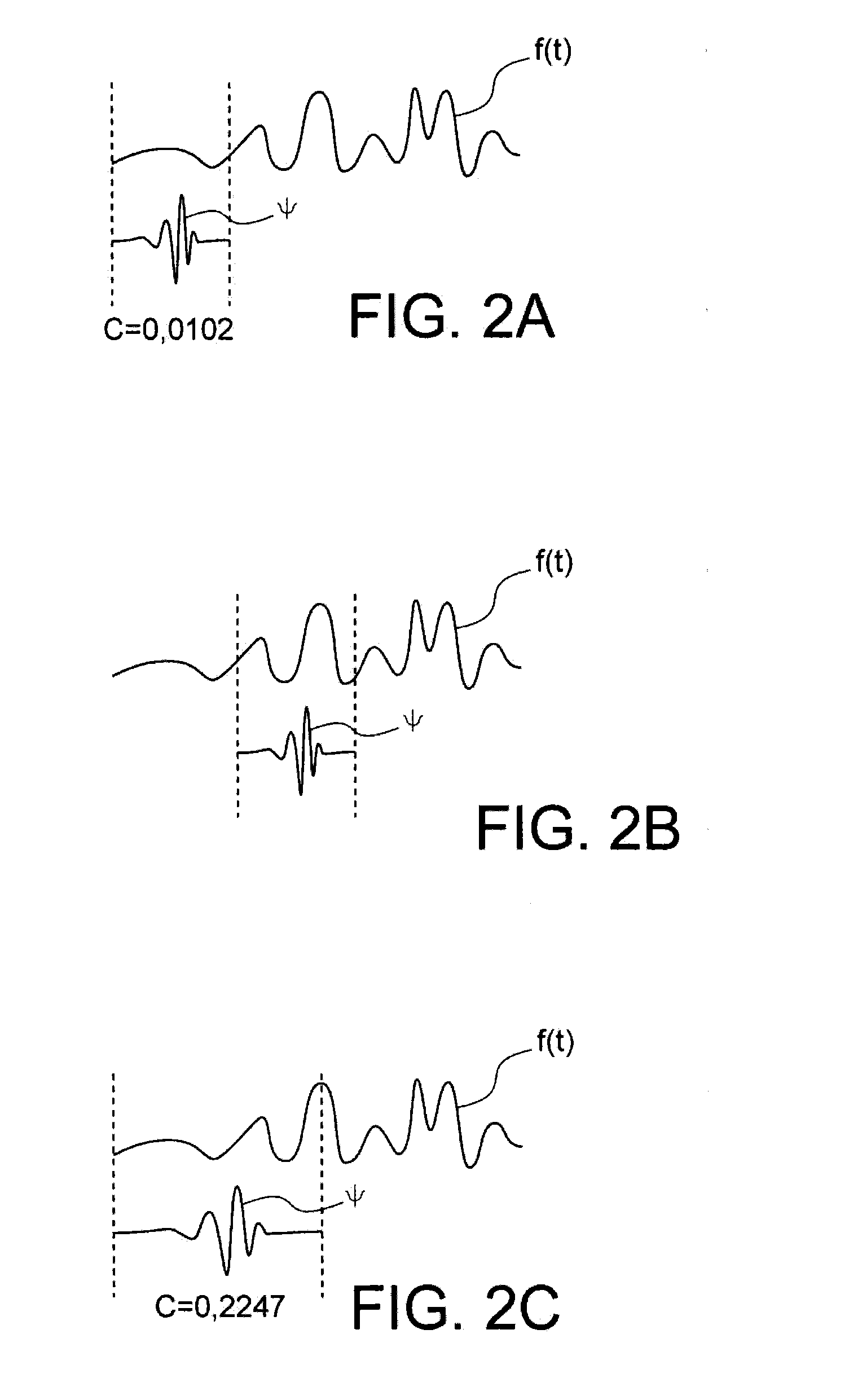
ActiveUS20150204935A1Spatial location is accurateReliable reconstructionFault location by conductor typesSpecial data processing applicationsPower gridEngineering
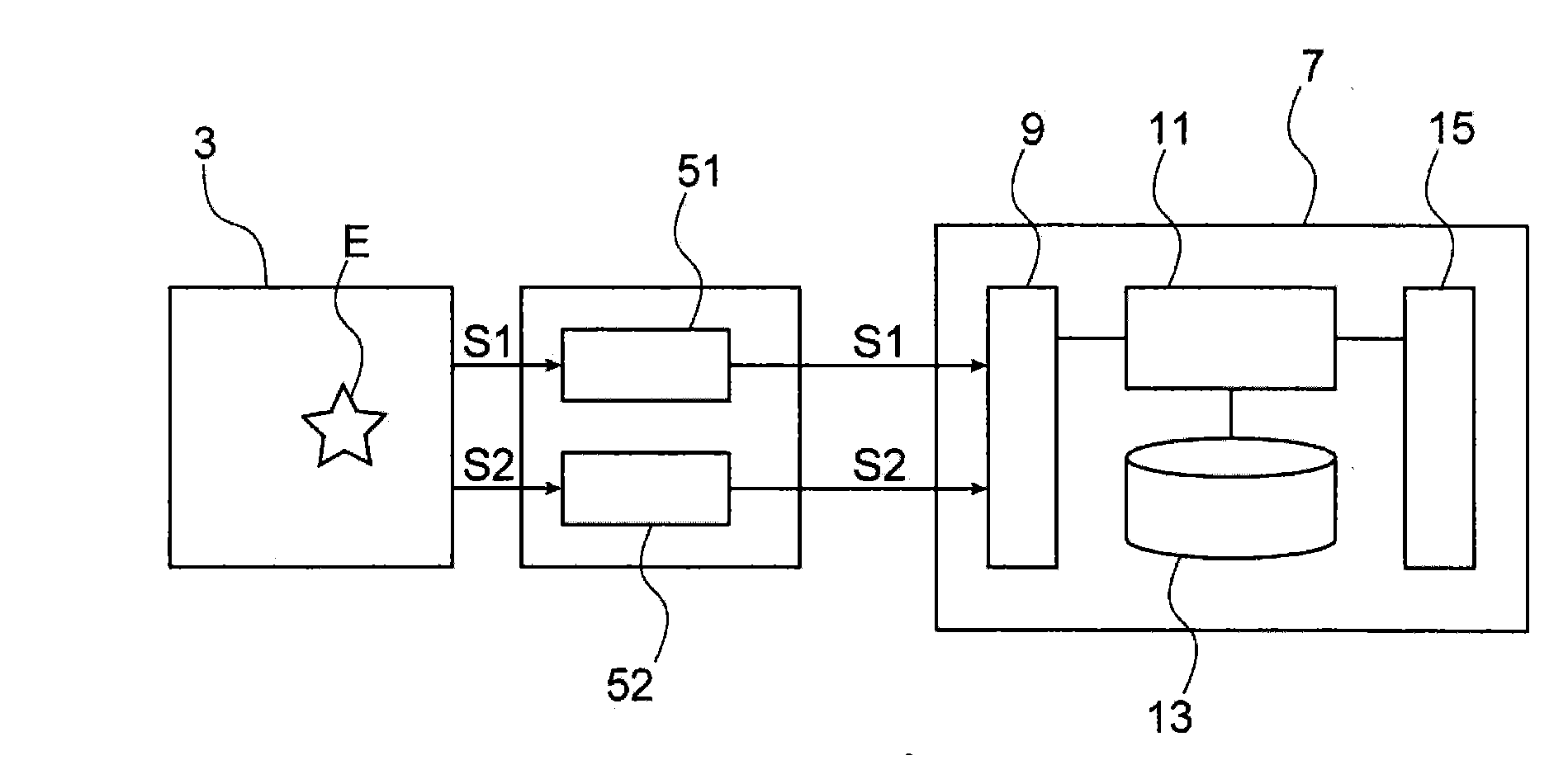
A method and device for monitoring an electrical network, including: a mechanism detecting electrical signals and additional signals produced in the electrical network, the additional signals being of a different physical nature to the electrical signals; a mechanism for processing the electrical signals to define a first time reference representing a detection time of the electrical signals emitted upon a fault event arising in the electrical network; a mechanism processing the additional signals to define a second time reference representing a detection time of the additional signals emitted upon the fault event arising in the electrical network; and a processor spatially locating the fault event in the electrical network according to the first and second time references.
Owner:KLONOWSKI THOMAS +1
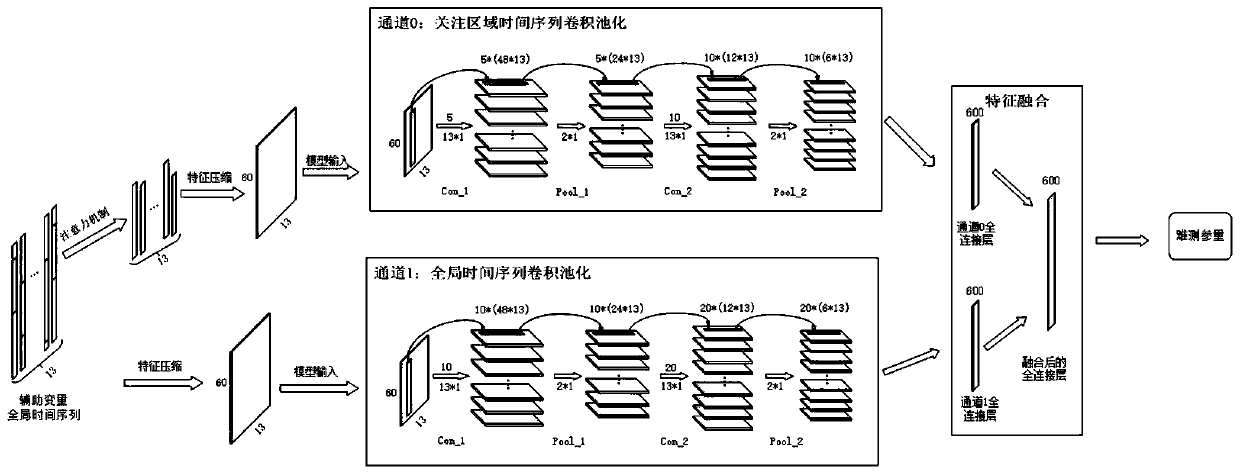
Multi-time scale convolutional neural network soft measurement method based on attention mechanism
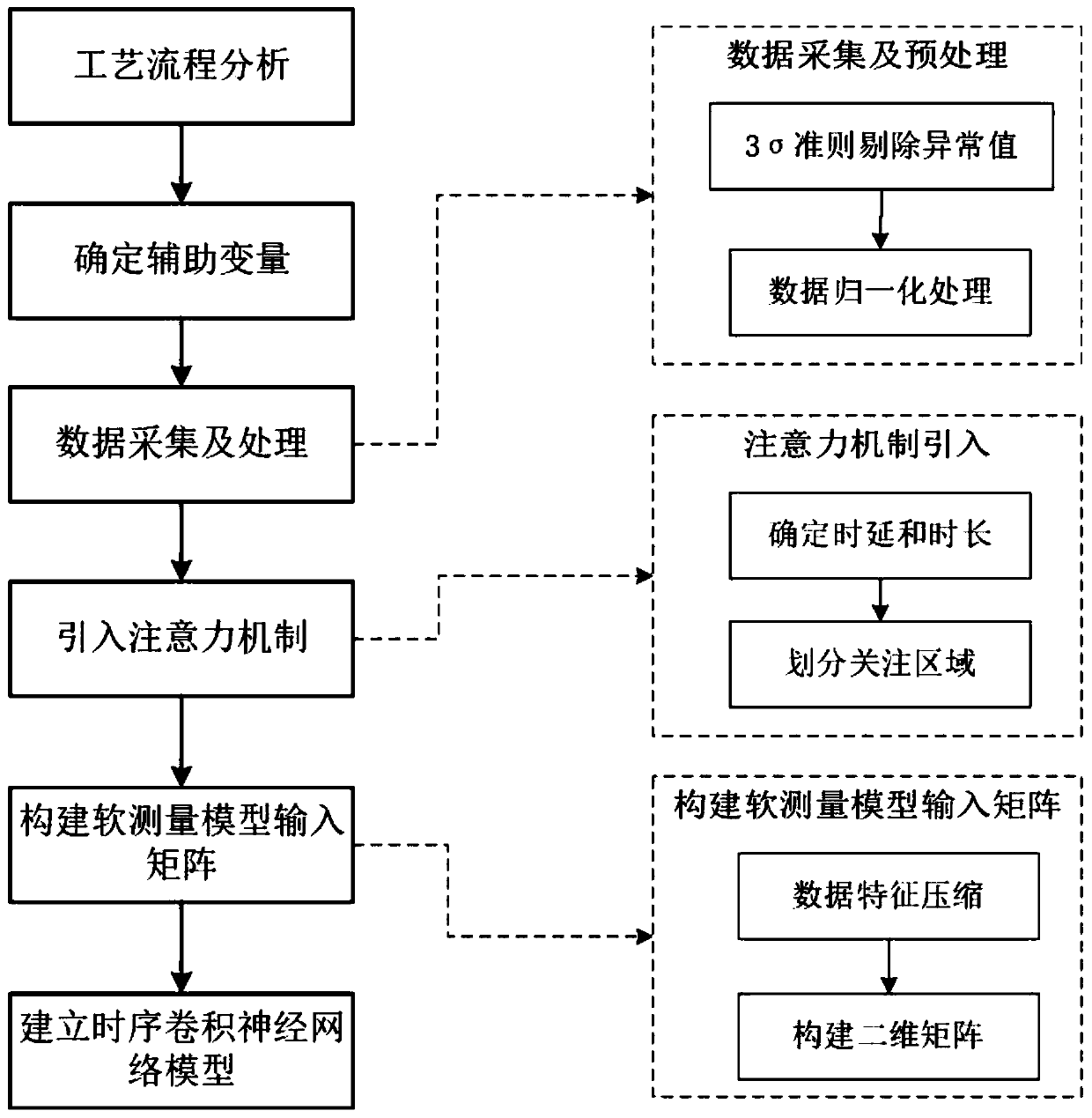
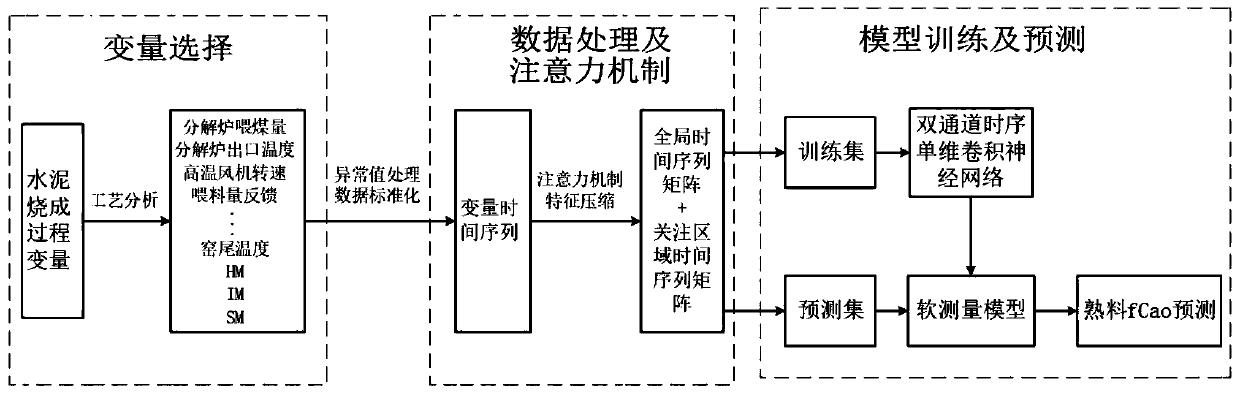
ActiveCN110378044ASolve the problem of real-time estimationStrong generalizationDesign optimisation/simulationNeural architecturesNerve networkTime delays
The invention relates to a multi-time scale convolutional neural network soft measurement method based on an attention mechanism, and belongs to the technical field of soft measurement. The method comprises the following steps: 1, determining an auxiliary variable, carrying out data processing, selecting an easily-measured variable related to a difficult-to-measure parameter as the auxiliary variable of a soft measurement model, and collecting a time sequence of the auxiliary variable and the difficult-to-measure parameter; abnormal value elimination is carried out on the collected time sequence; 2, selecting an attention mechanism and an attention area, and dividing the attention area according to the time delay and the effective time scale of each auxiliary variable relative to the difficult-to-measure parameters; 3, constructing the input of a soft measurement model, forming a matrix by the time sequence of each auxiliary variable, and determining the input of the soft measurement model by combining the attention area of the attention mechanism; 4, establishing a time sequence convolutional neural network soft measurement model; 5, training a time sequence convolutional neural network soft measurement model; and 6, carrying out real-time estimation on unmeasured parameters by utilizing the time sequence convolutional neural network model trained in the step 5.
Owner:YANSHAN UNIV
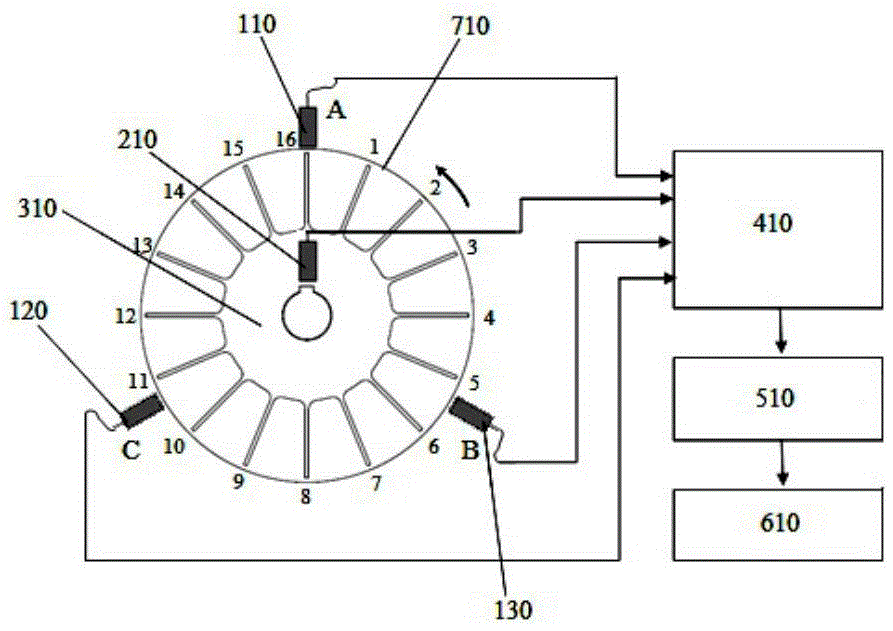
Undersampled leaf apex timing vibration signal reconstruction method and device thereof
ActiveCN105509876AImprove accuracyAvoid data redundancySubsonic/sonic/ultrasonic wave measurementUsing wave/particle radiation meansVibration measurementEngineering
The invention provides an undersampled leaf apex timing vibration signal reconstruction method and a device thereof. The method comprises the steps of (1) acquiring the displacement sampling data of a non-uniform blade end based on a blade end timing vibration measurement system; (2) determining the vibration characteristics of a high-speed blade and the frequency band range of the high-speed blade; (3) based on the periodic non-uniform sampling theory, completing the interpolation reconstruction for the vibration signal of the blade. The vibration displacement is acquired by a first blade end timing sensor and a second blade end timing sensor, wherein the first blade end timing sensor and the second blade end timing sensor are arranged in a casing. Based on the method, reconstructed signals are agonic and non-biased. Meanwhile, only by means of two blade end timing sensors, corresponding data can be acquired. In this way, not only data can be acquired completely and accurately, but also the cost is effectively reduced.
Owner:NAT UNIV OF DEFENSE TECH
Inhomogeneous undersampled blade end timing vibration signal reconstruction method and device
ActiveCN105466550AImprove accuracyAvoid data redundancySubsonic/sonic/ultrasonic wave measurementUsing wave/particle radiation meansVibration measurementEngineering
The invention provides an inhomogeneous undersampled blade end timing vibration signal reconstruction method and device, and the method comprises the following steps: 1), obtaining inhomogeneous blade end displacement sampling data through employing a blade end timing vibration measurement system; 2), determining the vibration characteristics and frequency band range of a high-speed blade; 3), achieving the interpolation reconstruction of a blade vibration signal based on a periodic inhomogeneous sampling principle. The method causes no deviation and aliasing during signal reconstruction.
Owner:NAT UNIV OF DEFENSE TECH
Hyperspectral remote sensing image vector C-V model segmentation method based on wave band selection
ActiveCN103854281AImprove Segmentation AccuracySplitting speed is fastImage analysisSpectral curveComputer vision
The invention discloses a hyperspectral remote sensing image vector C-V model segmentation method based on wave band selection. Firstly, according to a spectral curve, wave bands high in contrast ratio between a target and the background are selected, further, according to relevant coefficients of the wave bands, the wave bands high in relevancy are removed so that a new wave band combination can be formed, and therefore according to the determined wave band assembly, a hyperspectral image vector matrix is established; on the basis, a vector C-V segmentation model based on the vector matrix is constructed, the edge guiding function based on gradient is introduced into the model, on the basis that a traditional C-V model is reserved to perform image segmentation based on area information, the capacity for capturing the target boundary in heterogeneous areas and under complex background conditions is enhanced through edge detail information of images, segmentation precision of the hyperspectral remote sensing images is improved, segmentation speed of the hyperspectral remote sensing images is increased.
Owner:清影医疗科技(深圳)有限公司
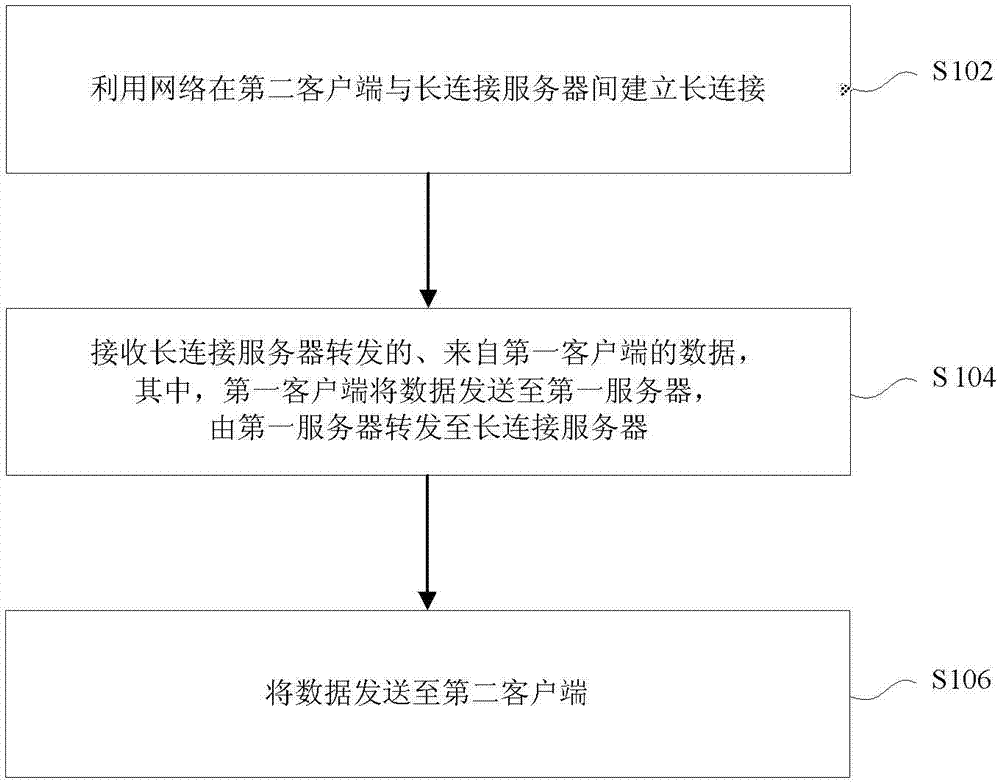
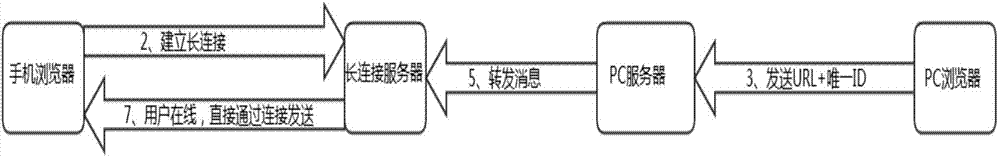
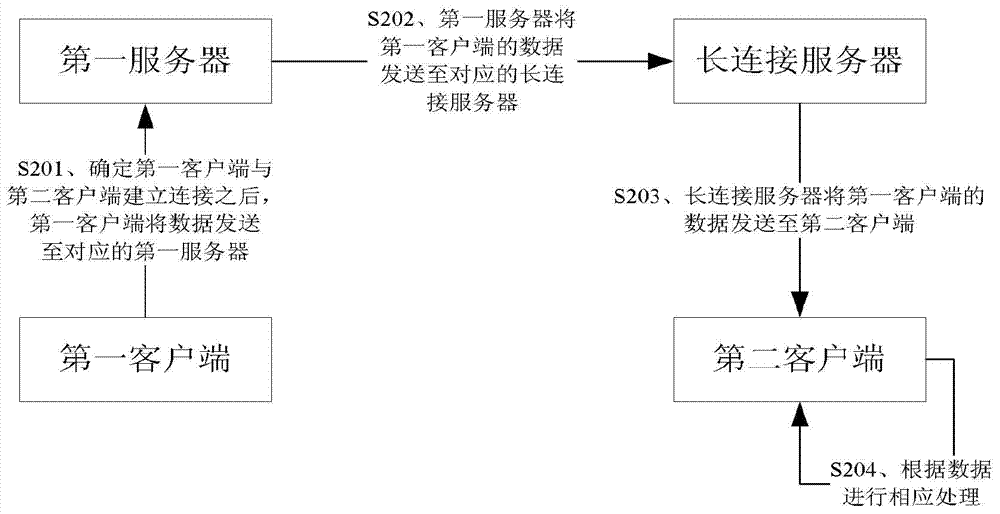
Data transmission method, data transmission equipment and data transmission system
ActiveCN103501331ASolve duplication of operationsSolve the duplication of obtaining informationTransmissionData transmission circuitData transmission systems
The invention provides a data transmission method, data transmission equipment and a data transmission system. The method comprises the following steps of establishing a long connection between a second client and a long connection server by utilizing a network; receiving data which is forwarded by the long connection server and comes from a first client; sending the data to a first server by the first client, and forwarding to the long connection server by the first server. According to the data transmission method, the data transmission equipment and the data transmission system provided by the invention, the information sharing problem between the first client and the second client is solved, so that a user can synchronize information between the two clients in time, and therefore, the phenomenon that the user performs repeated and complicated operations on different clients is avoided, the user time is shortened, and the user experience is enhanced.
Owner:BEIJING QIHOO TECH CO LTD
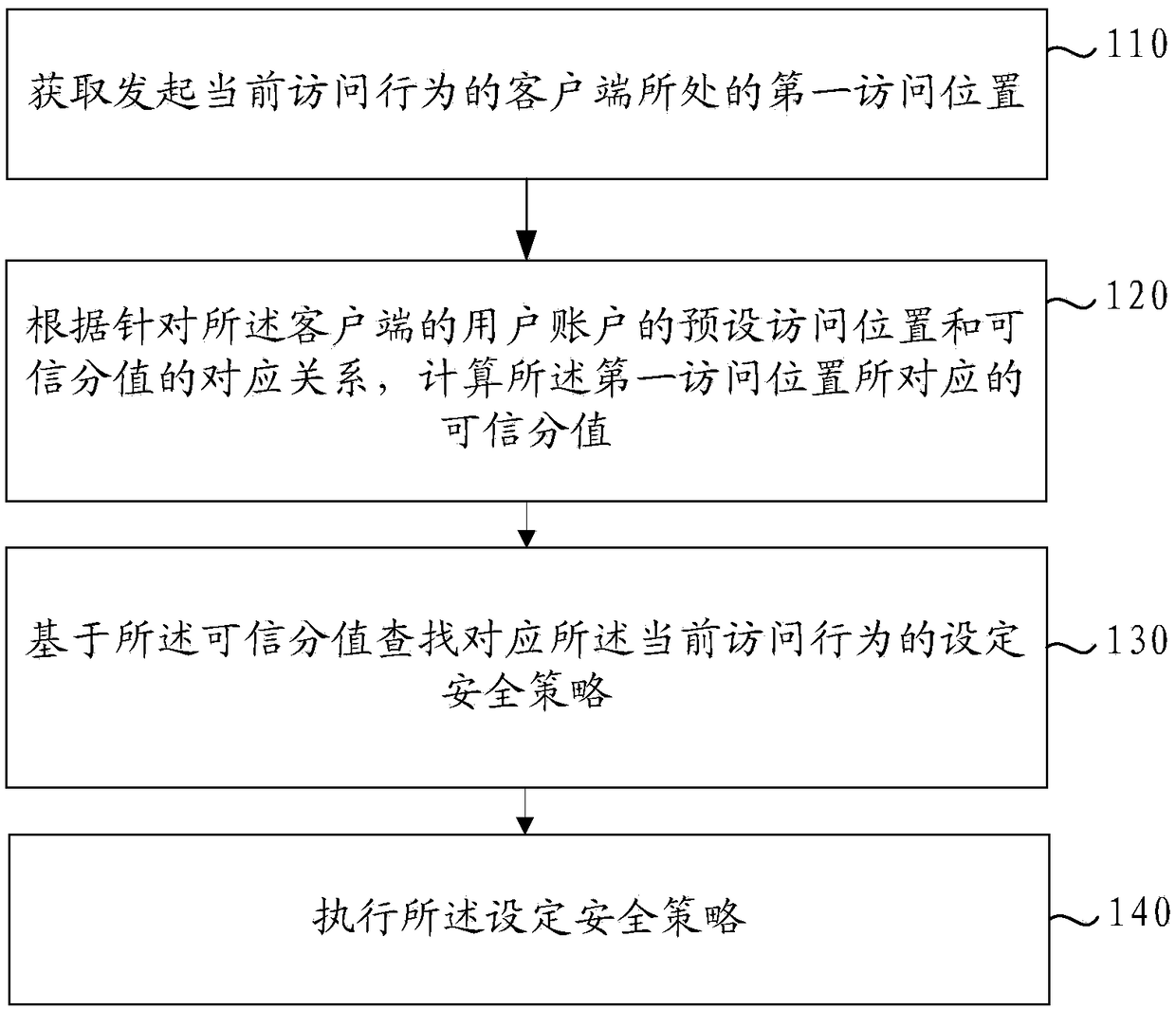
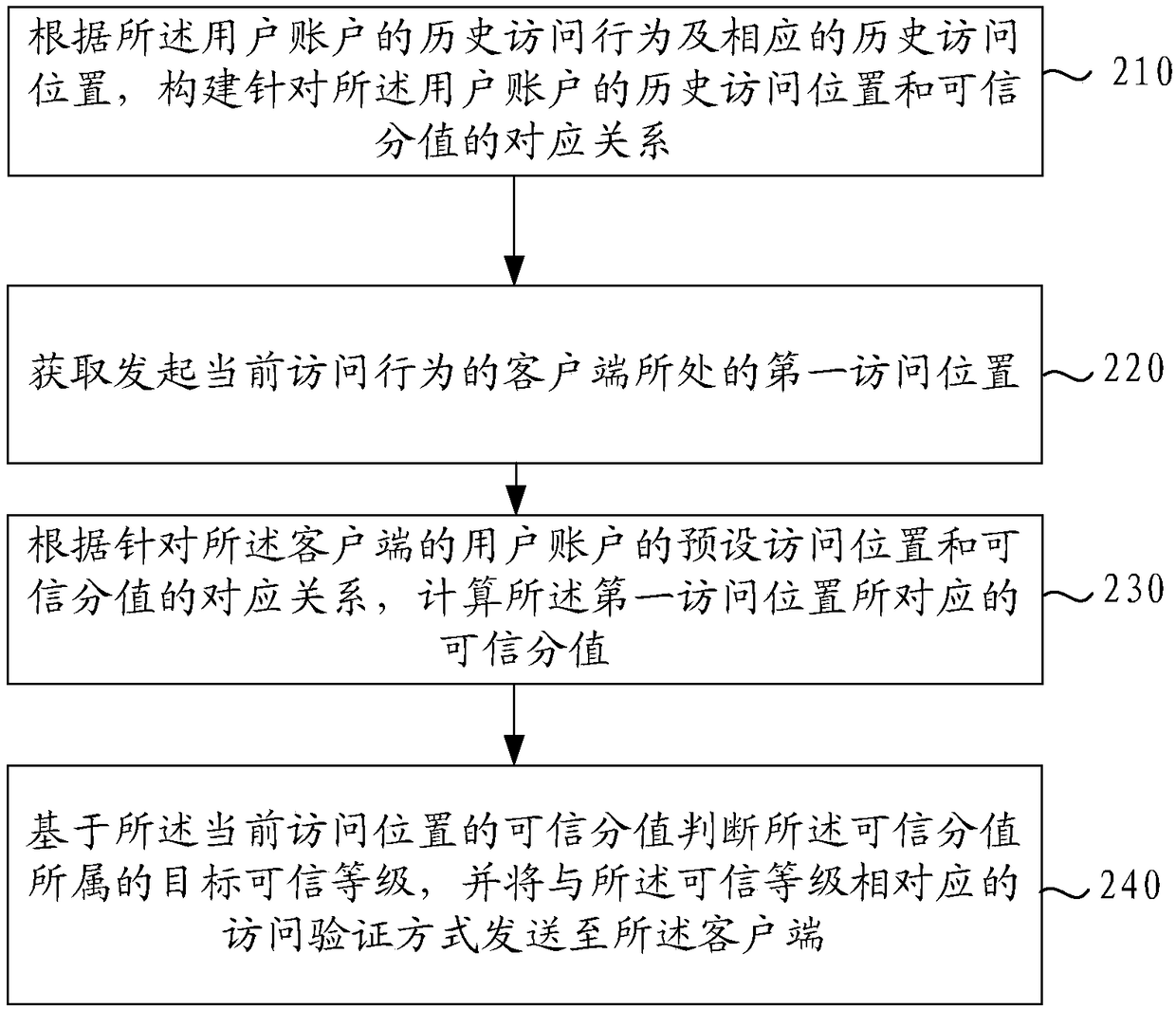
Access behavior data processing method, system and device, and readable storage medium
ActiveCN108156132ASolve the problem of low credit calculation coverageAvoid data redundancyTransmissionSecurity policyTrust score
The invention provides an access behavior data processing method, system and device, and a readable storage medium. The method comprises the steps of acquiring a first access position of a client initiating a current access behavior; according to a correspondence between a preset access position of a user account of the client and a trust score, calculating a trust score corresponding to the firstaccess position; searching, based on the trust score, a set security policy corresponding to the current access behavior; and executing the set security policy. Through adoption of the method, trustscores of a target position executing access are accumulated, and a corresponding set operation is performed according to a correspondence between the trust score of the current access behavior and atrust score of a position at where access behavior occurs. Compared with a set processing operation based on trust score for device environment in the prior art, the method has the advantages of higher coverage and more reliable, accurate security management.
Owner:BEIJING SANKUAI ONLINE TECH CO LTD
Method of generating human body three-dimensional data model library
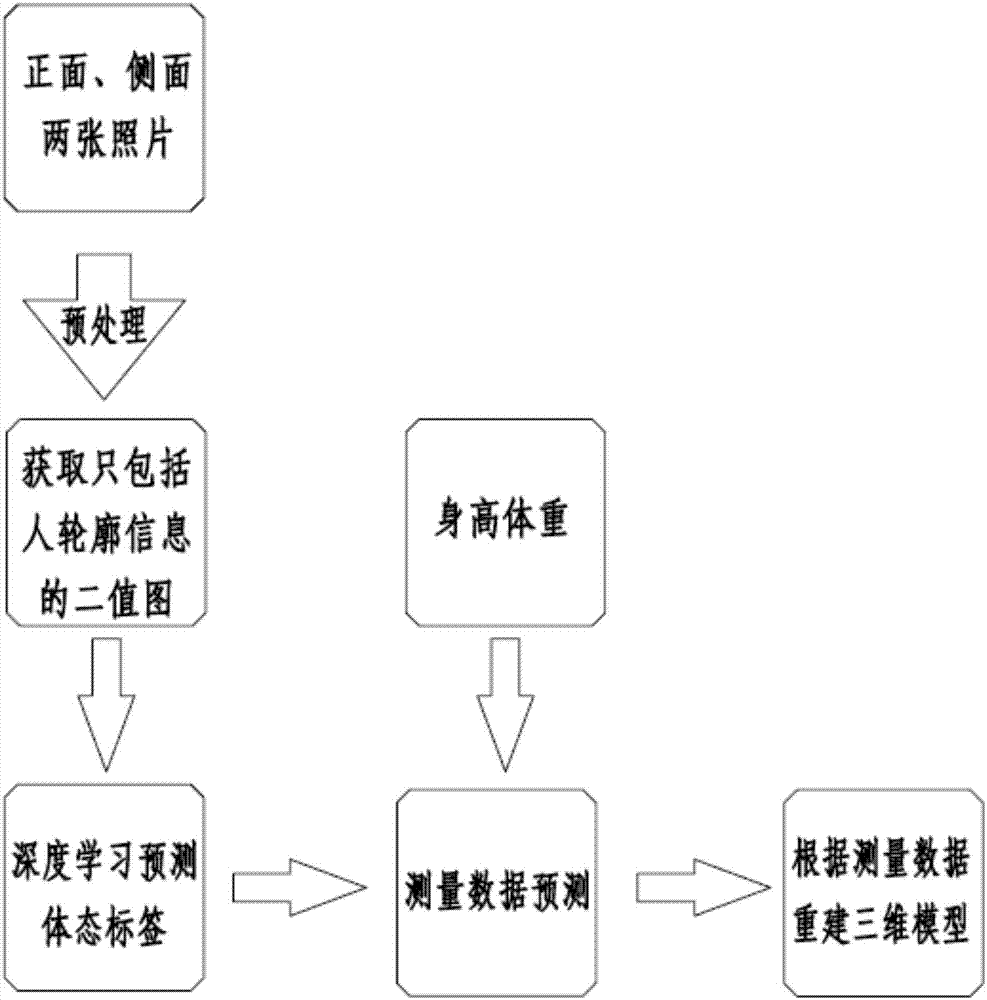
InactiveCN107170039AHigh precisionImprove efficiencyImage enhancementImage analysisHuman bodyMeasurement precision
The invention belongs to the field of data measurement, and particularly relates to a method of generating a human body three-dimensional data model library, so as to solve problems that data in the existing database are imperfect, the acquisition range is small, the acquisition is single, and the data accuracy is poor. The method comprises the following steps: 1) a human body three-dimensional virtual model library is built; 2) the weight and the offset of a virtual model posture label are obtained through learning; 3) a PCA main feature value is acquired; and 4) the model data are calculated. The method can build the human body database in a low cost, high precision and high efficiency mode, the measurement time can be greatly shortened, the measurement precision and the efficiency are improved, and the posture trend of the human body can be evaluated.
Owner:XIAN SUANIER ELECTRONICS TECH
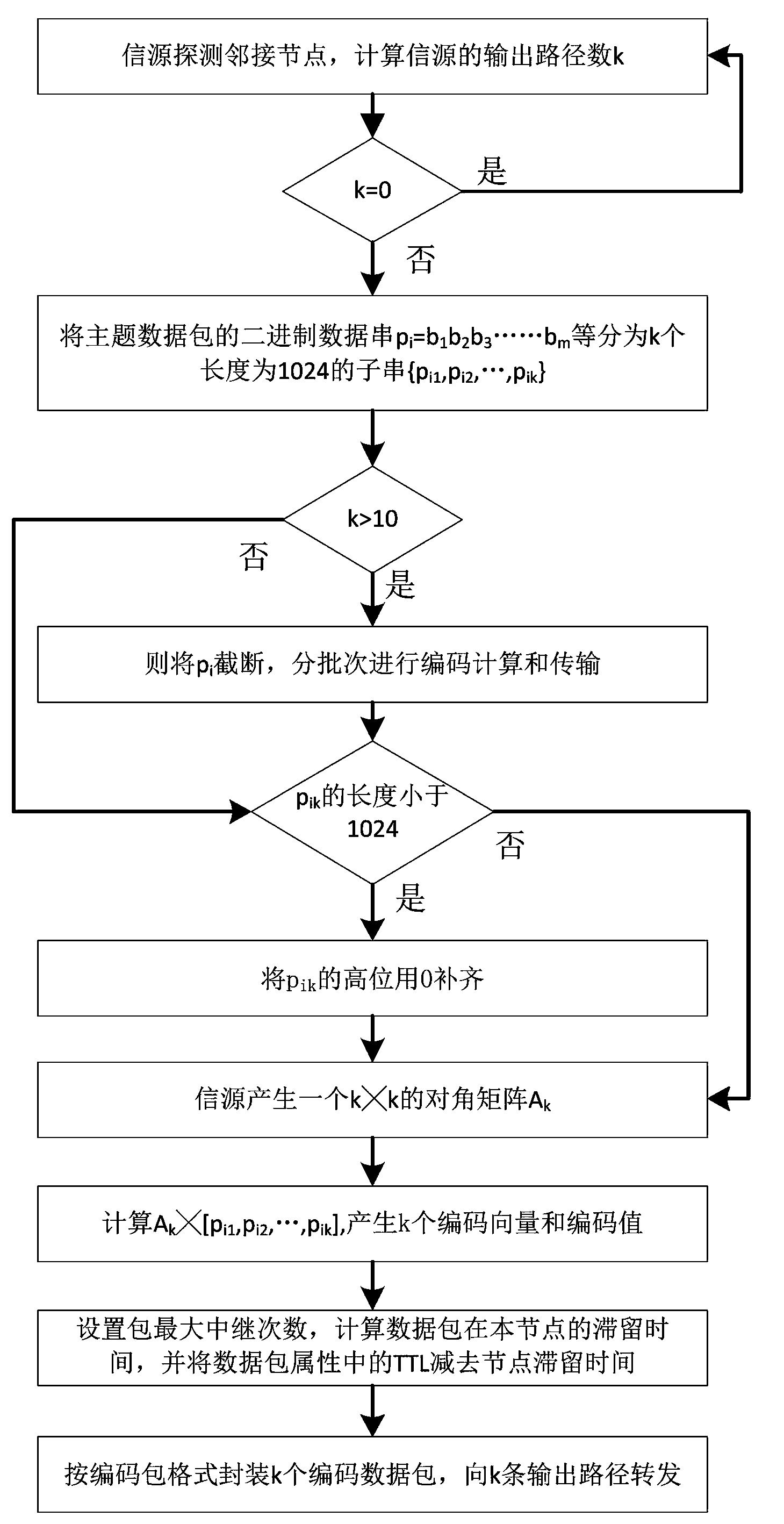
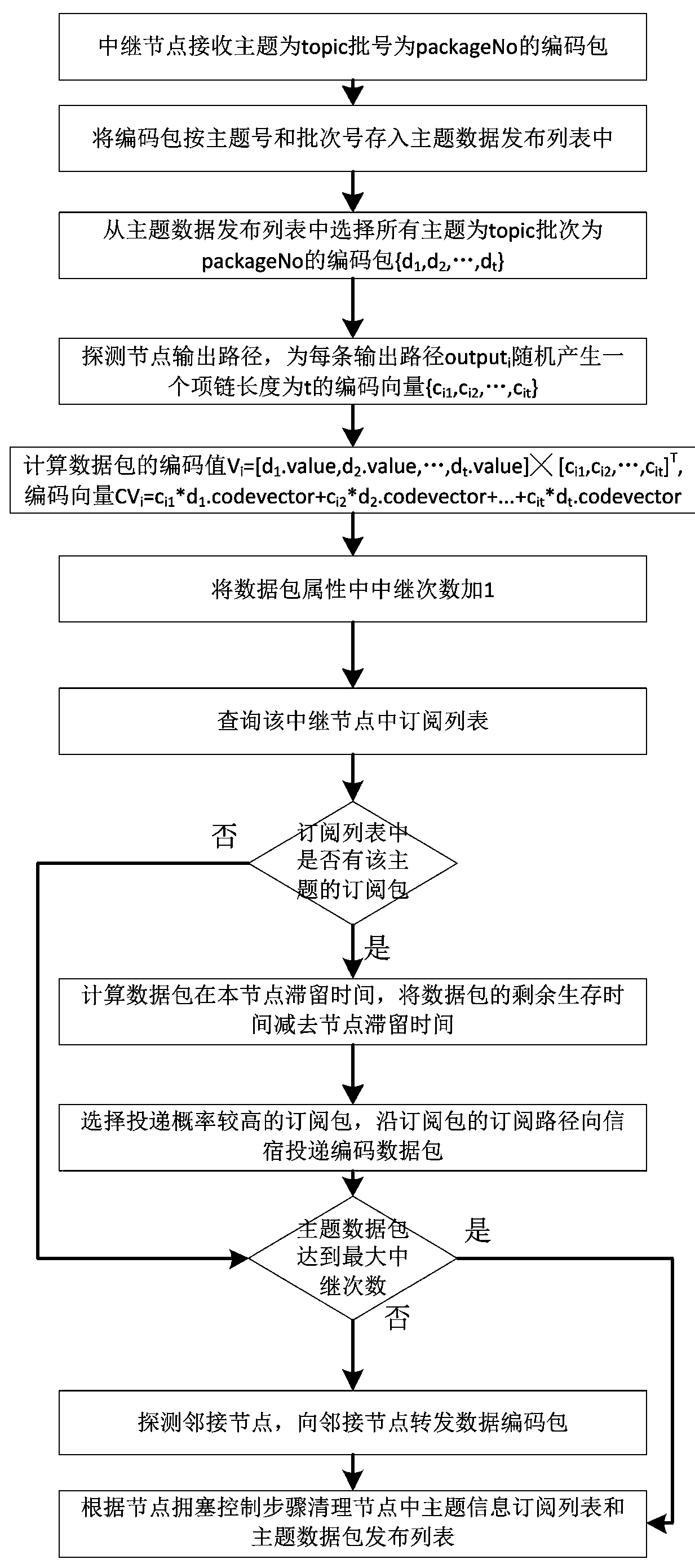
Data subscription and distribution method applicable to delay-tolerant and disconnection-tolerant network
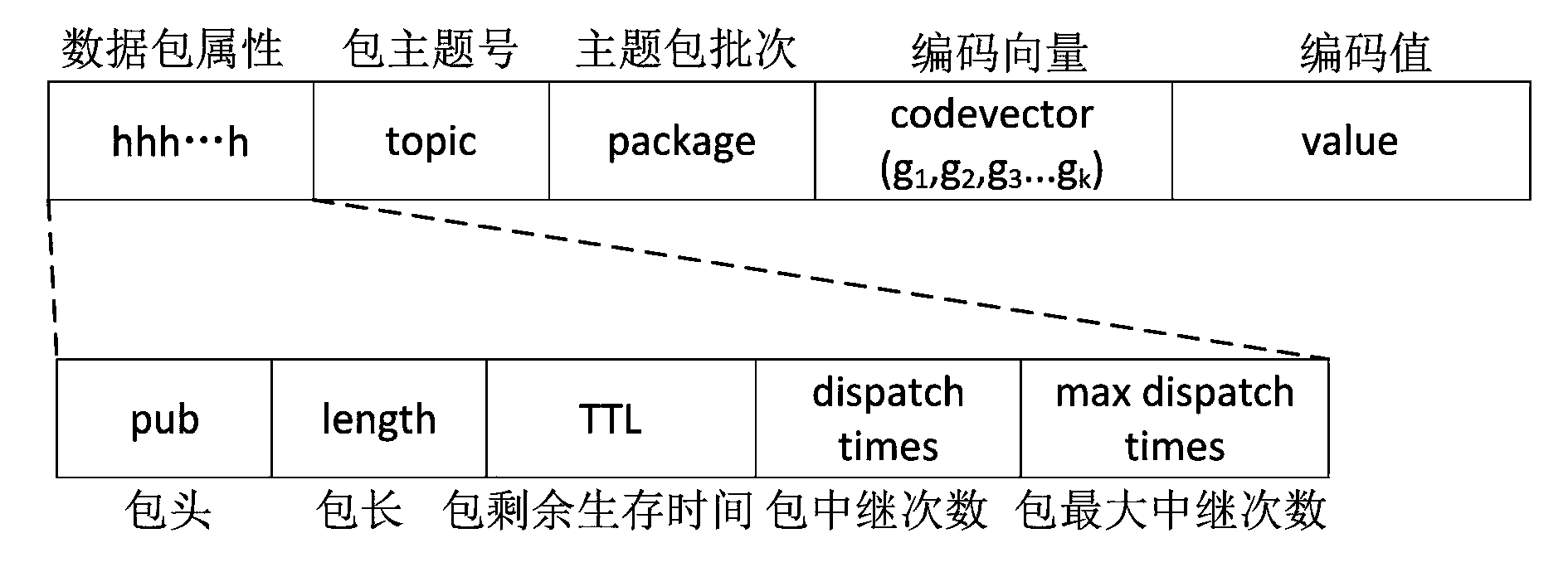
ActiveCN104301237ASolve the problem of low data distribution efficiencySolve the loadError prevention/detection by using return channelData switching networksData packDistribution method
The invention relates to the field of data distribution, in particular to a data subscription and distribution method applicable to a delay-tolerant and disconnection-tolerant network. The method is achieved through the technical scheme. According to the technical scheme, the data subscription and distribution method applicable to the delay-tolerant and disconnection-tolerant network includes the steps that first, information source nodes perform data packet code issuing; second, relay nodes perform code forwarding; third, an information sink issues a theme subscription packet; fourth, the theme subscription packet is processed by the relay nodes; fifth, the relay nodes perform congestion control processing on a theme data issuing table and a theme information subscription table; sixth, information sink nodes perform data decoding; seventh, ACK data packets are processed by the relay nodes. Through the method, a network code transmission mechanism, a data subscription and distribution mechanism and functions such as a data congestion control function are fused, and the function of data distribution in a delay-tolerant and disconnection-tolerant network environment is achieved.
Owner:湖北交通职业技术学院
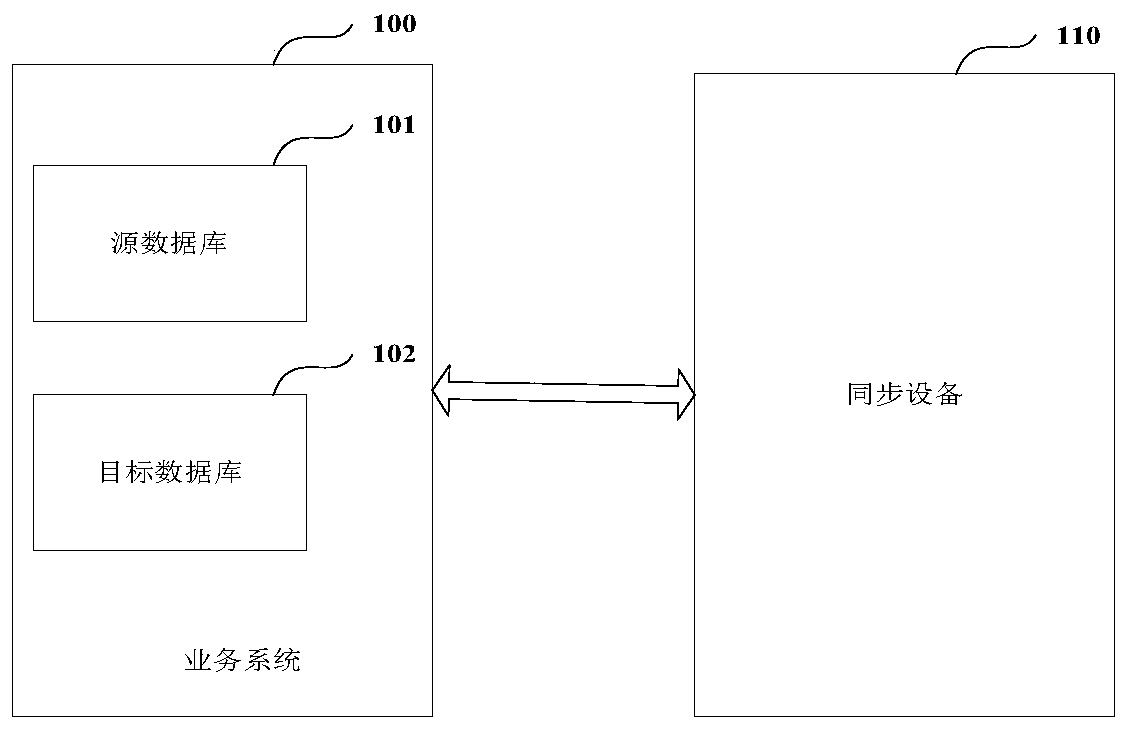
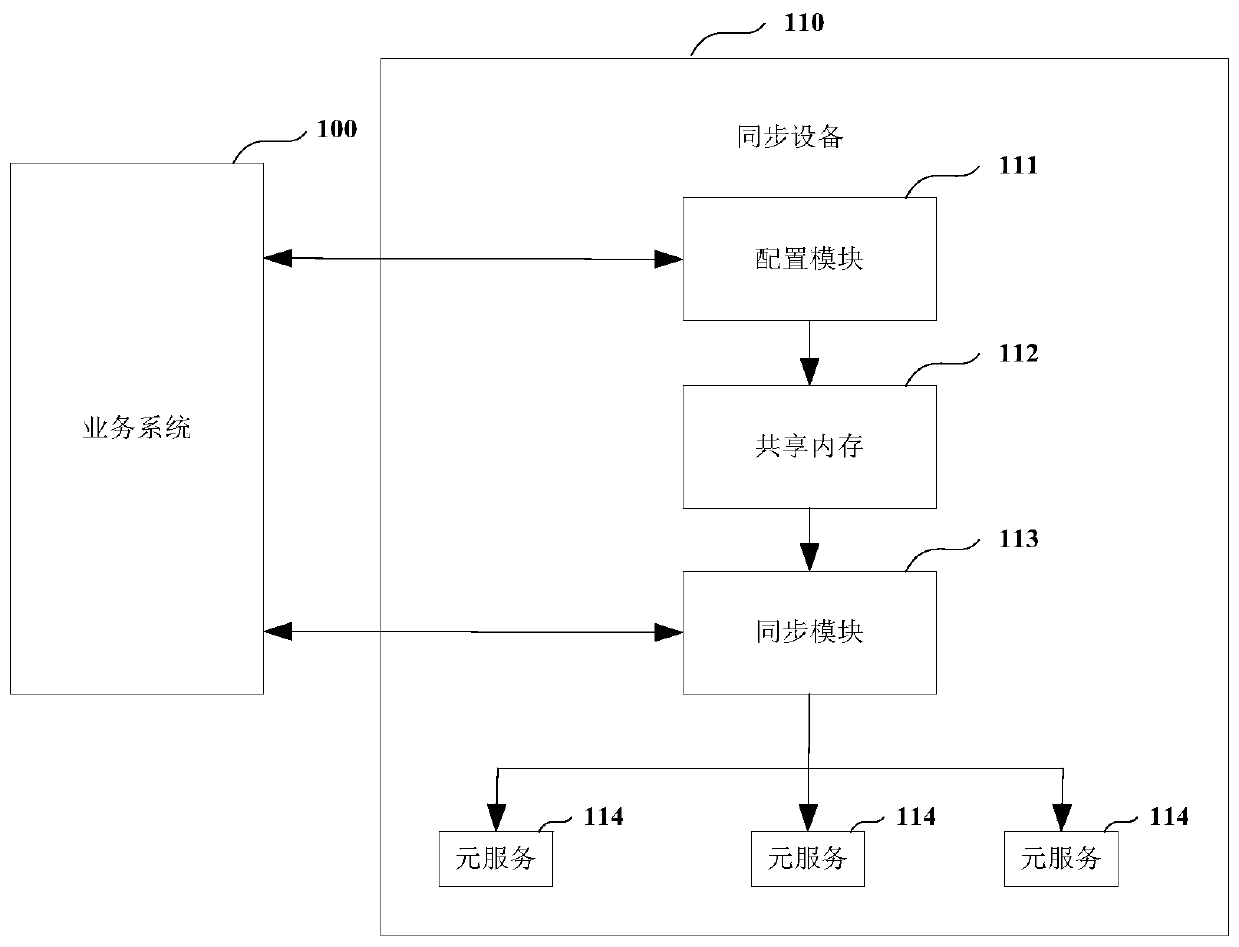
Data synchronization method and device, equipment and medium
ActiveCN111460031AReduce complexityReduce operation and maintenance costsDatabase distribution/replicationSpecial data processing applicationsData synchronizationEngineering
The invention belongs to the technical field of data processing, and discloses a data synchronization method and device, equipment and a medium. The data synchronization method includes: configuring different service synchronization processes in advanceafter a synchronization request message sent by a service system is received, obtaining service process identification information and field parameter information contained in the synchronization request message, obtaining a service synchronization process corresponding to the service process identification information; and executing a service synchronization process according to the field parameter information to achieve data synchronization, therefore, the specified data stored in the source database can be synchronized to the target database according to the field parameter information, the problem of data redundancy caused by full data synchronization is avoided, different service systems can be accessed, and the complexity of accessand management of the service systems is reduced.
Owner:TENCENT TECH (SHENZHEN) CO LTD +1
Configurable data processing method and system and mobile platform
InactiveCN105245622AGood experienceImprove user experienceTransmissionApplication serverMobile object
Owner:CHINA CONSTRUCTION BANK
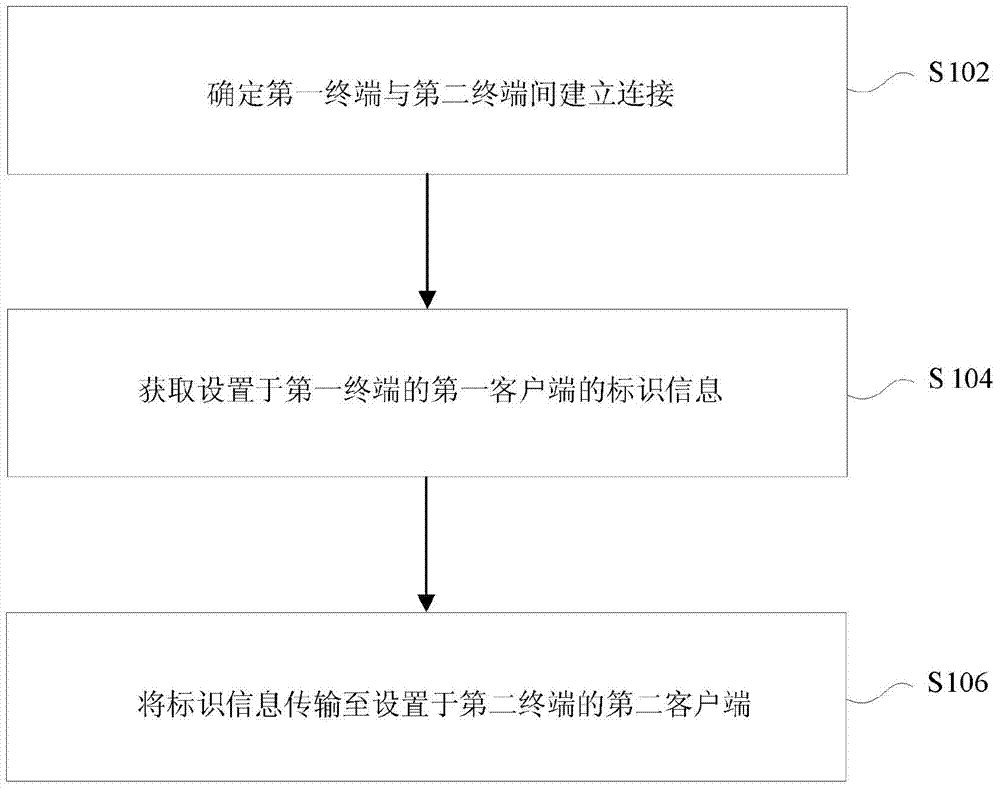
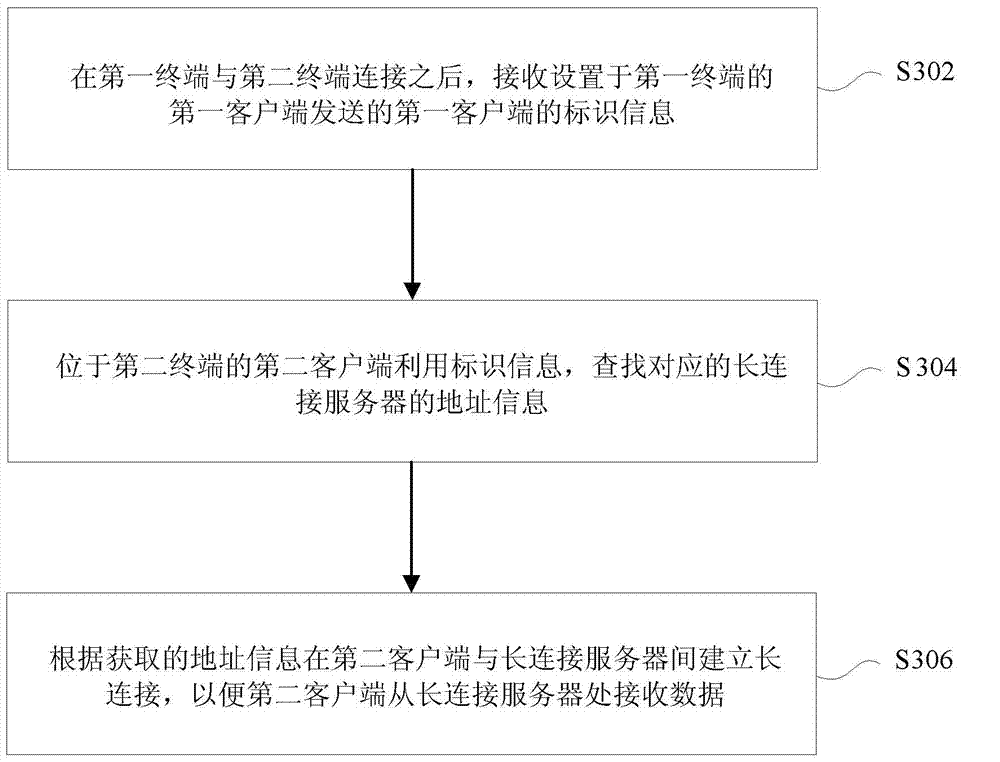
Data transmission method, data transmission equipment and network system
InactiveCN103501332ARealize data transmissionSolve the problem that data transfer cannot be performedTransmissionUser needsComputer terminal
The invention provides a data transmission method, data transmission equipment and a network system. The data transmission method comprises the following steps of installing a first client to a first terminal, installing a second client to a mobile terminal, and receiving the identification information of the first client after the first terminal and the mobile terminal are connected; sending data in the second client to a long connection server by a first server of the first terminal, wherein the long connection server is determined according to the identification information, and a long connection exists between the long connection server and the first client; transmitting the data in the second client to the first client by utilizing the long connection server. By adopting the data transmission method, the data transmission equipment and the network system provided by the invention, the problems that wasting of resources is caused and the efficiency is low due to the fact that data transmission cannot be performed between different clients and user requirements had to be reintroduced when a new client is enabled can be solved.
Owner:BEIJING QIHOO TECH CO LTD +1
High-spectrum quick abnormity detection method adopting kernel recursion
ActiveCN104766313AAvoid data redundancyReduce workloadImage analysisImaging processingBackground information
The invention belongs to image processing, and relates to the field of high-spectrum image abnormity target detection, in particular to a high-spectrum quick abnormity detection method adopting kernel recursion. The method includes the steps that high-spectrum data are read in, a kernel matrix of background information is initialized, a causal relationship of background pixel updating is built, a recursion equation of the kernel matrix KB(n) is built to update the kernel matrix, and a high-spectrum image is quickly detected through a KRX operator. An updating model adopting background information causality is provided, the background information is quickly updated through changes of detected pixels, and data redundancy caused by repeatedly extracting the background information is avoided. A brand new kernel matrix is built, so that the problem that dimension of the kernel matrix changes along with increasing of the number of the background pixels is effectively solved, and meanwhile, the kernel matrix does not need to be calculated every time in an algorithm. The recursion concept of the Kalman filter theory is introduced, workload in actual processing can be greatly reduced, and abnormal target detection efficiency is improved.
Owner:HARBIN ENG UNIV
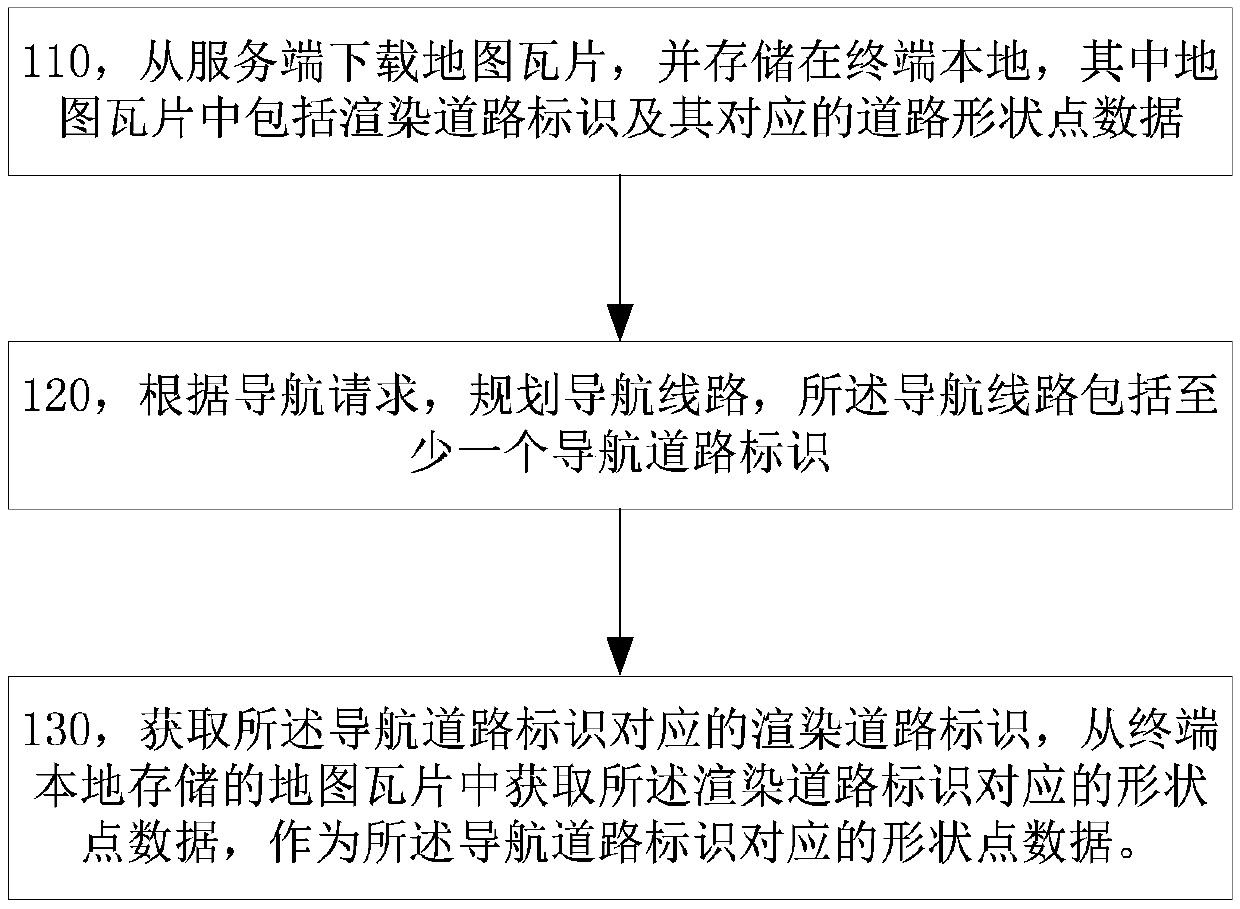
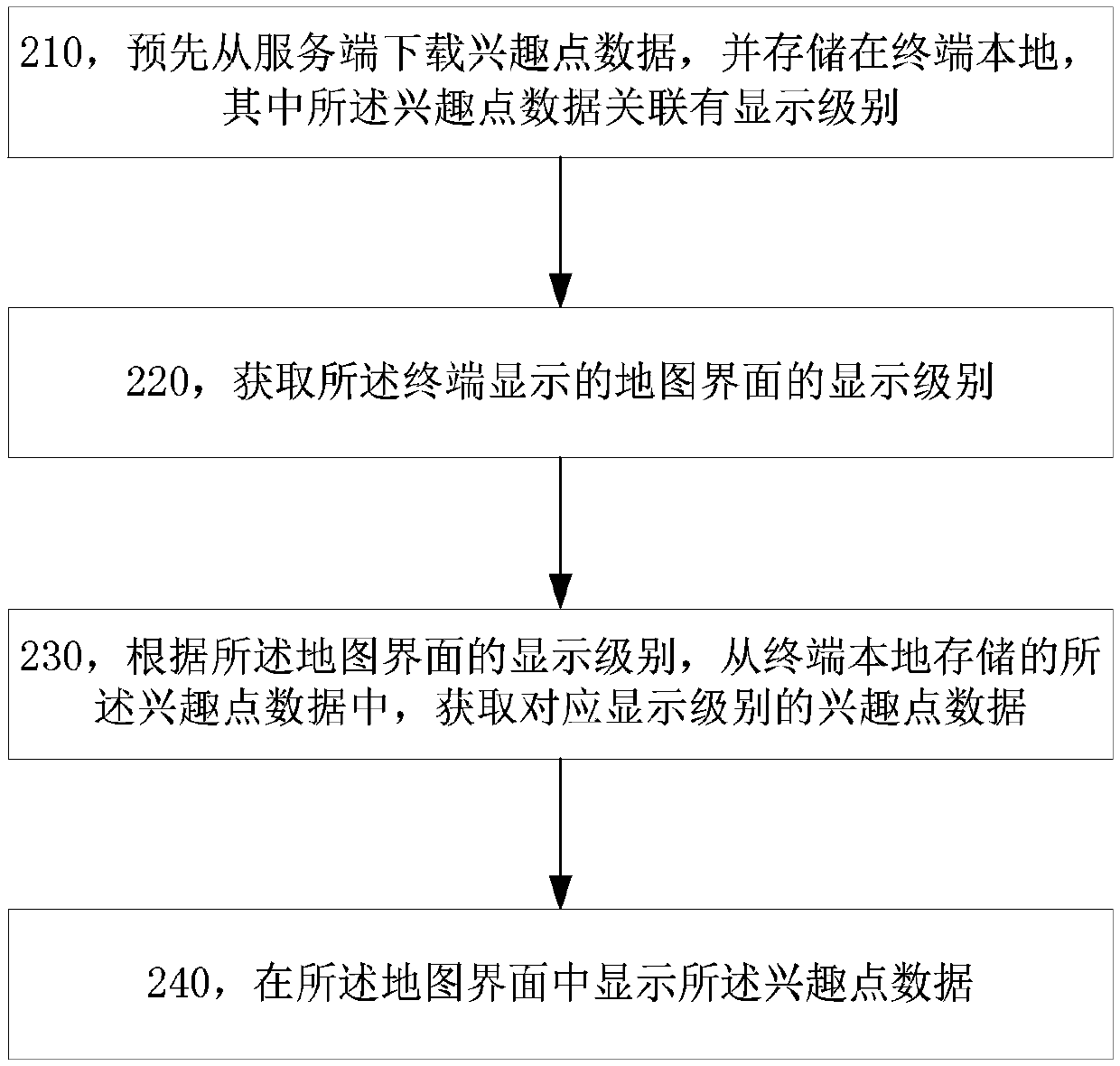
Method and terminal for processing road data and interest point data in map
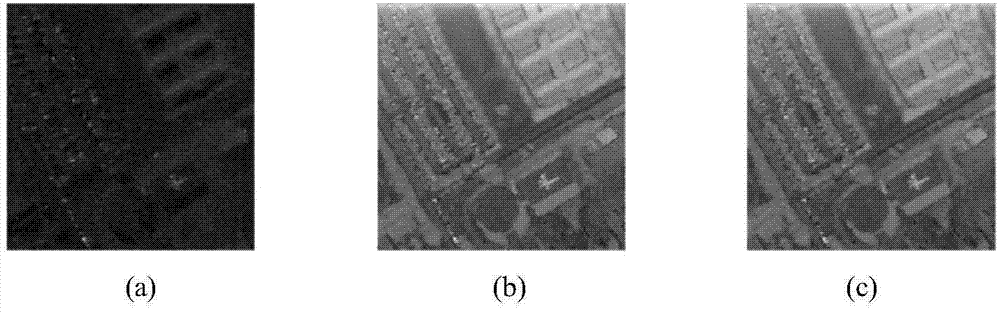
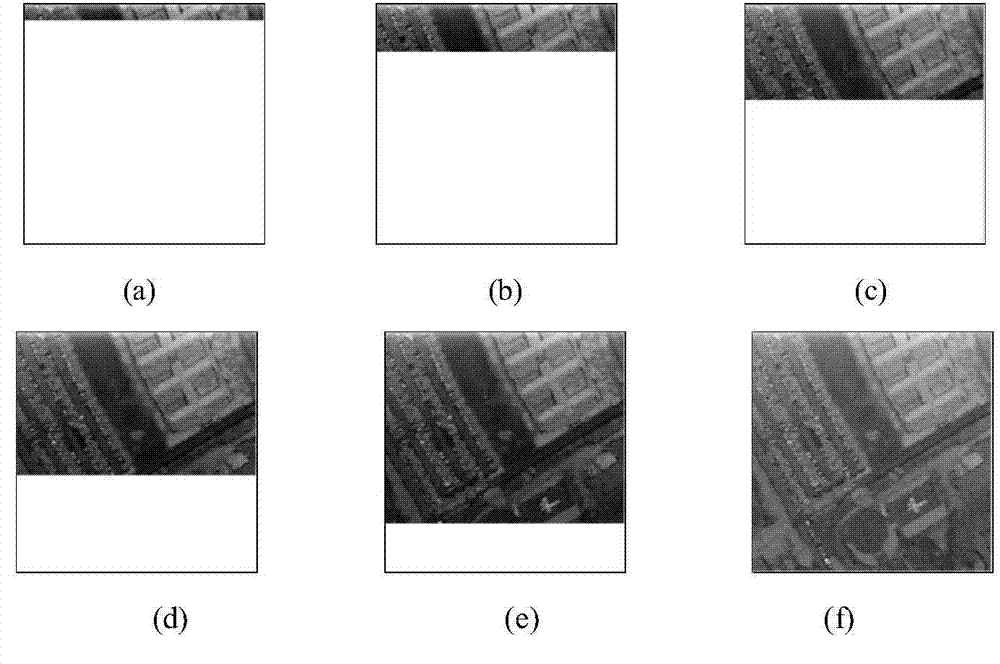
ActiveCN110887499AAvoid data redundancyTakes up little storage spaceInstruments for road network navigationComputer visionData transmission
The invention discloses a method and a terminal for processing road data and interest point data in a map. During navigation, a rendered road sign corresponding to a navigation road sign is obtained,and then shape point data corresponding to the rendered road sign is obtained from an offline map tile to serve as shape point data corresponding to the navigation road sign. A terminal further downloads interest point data associated with a display level from a server and stores the interest point data, and the interest point data corresponding to the display level can be obtained from the locally stored interest point data during map interface display and offline search. The method is advantaged in that functions of navigation, interest point search and the like can be realized by using offline map data with small data volume, data redundancy is avoided, the data transmission quantity can be reduced, and the occupied storage space is small.
Owner:ALIBABA (CHINA) CO LTD
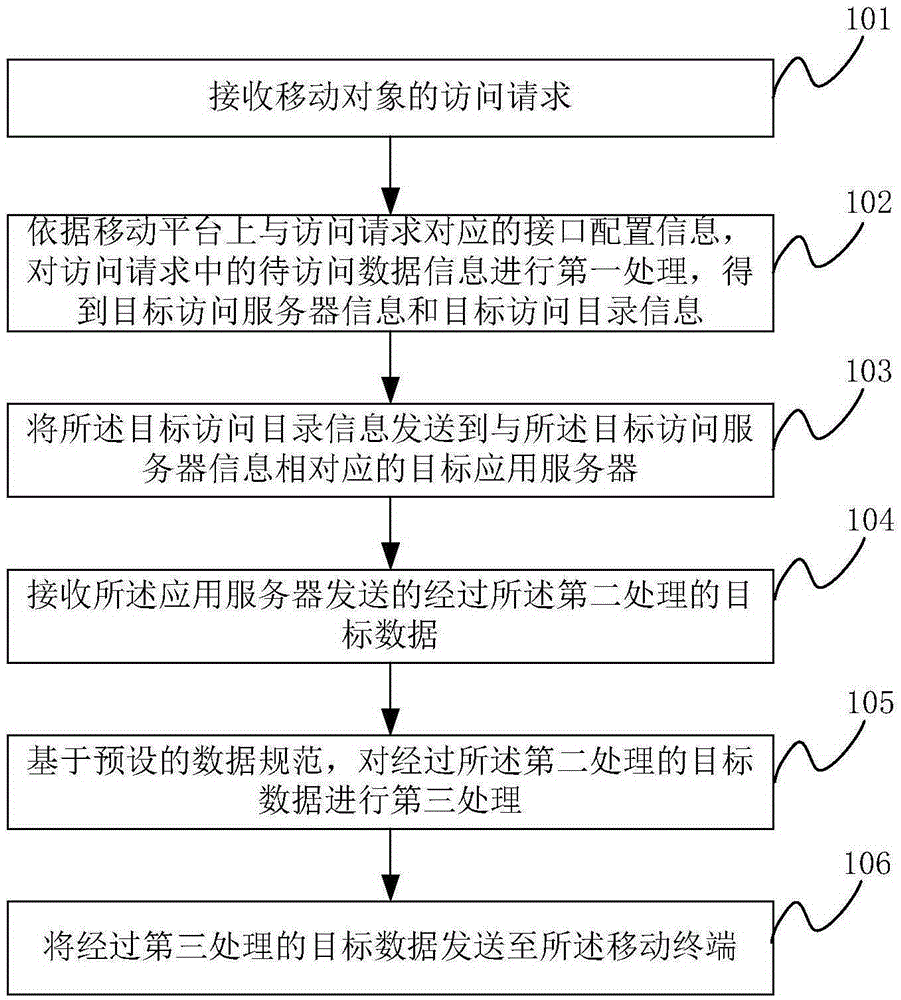
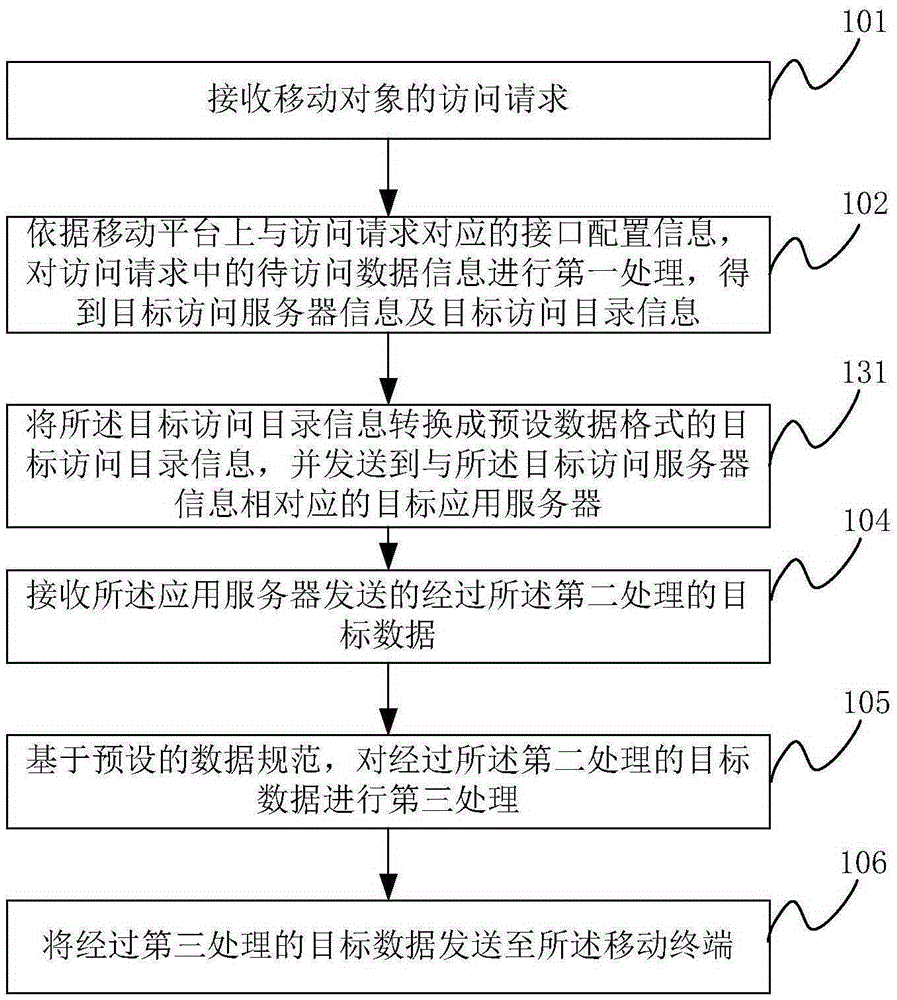
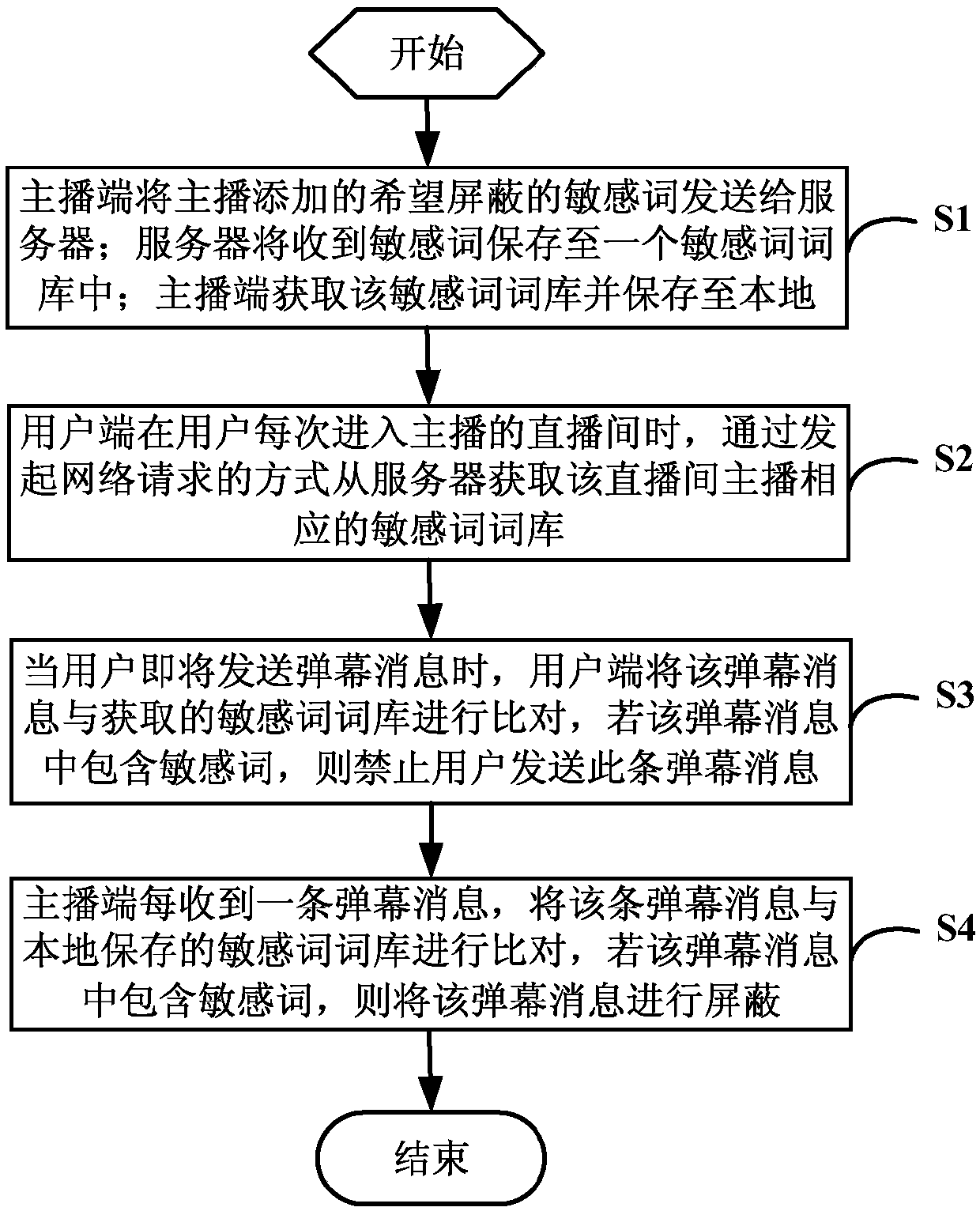
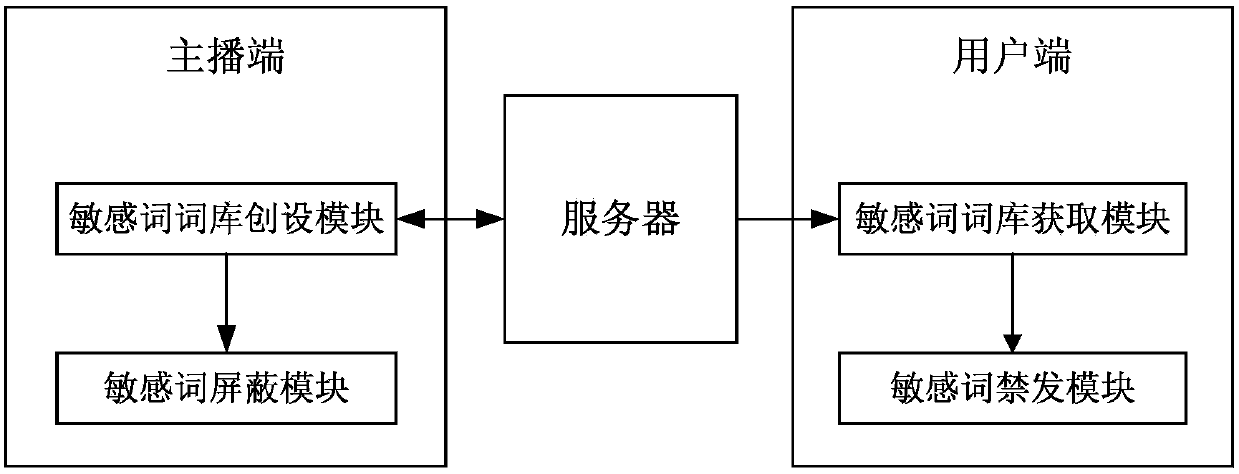
Multi-end cooperative bullet screen message blocking method, storage medium, equipment and system
InactiveCN109660869AImprove experienceRelieve pressureSelective content distributionQuality of serviceThe Internet
The invention discloses a multi-terminal cooperative bullet screen message blocking method, a storage medium, equipment and a system, and relates to the technical field of internet mobile terminal application development. The method comprises the steps that an anchor end sends sensitive words added by the anchor to a server for storage, and obtains a sensitive word library from the server for storage; a user end obtains a corresponding sensitive word library when the user enters a live broadcast room; when the user is about to send a bullet screen message, the bullet screen message is comparedwith the sensitive word library, and if the bullet screen message contains sensitive words, the user is forbidden from sending the bullet screen message; each time the anchor end receives one bulletscreen message, the bullet screen message is compared with a locally stored sensitive word library, and if the bullet screen message contains sensitive words, the bullet screen message can be blocked.According to the method and device, the blocking process of the sensitive word bullet screen messages can be transmitted to the user end and the anchor end for cooperative processing, so that the pressure of the server is greatly reduced, the service quality of the server is high, and the user experience is good.
Owner:WUHAN DOUYU NETWORK TECH CO LTD
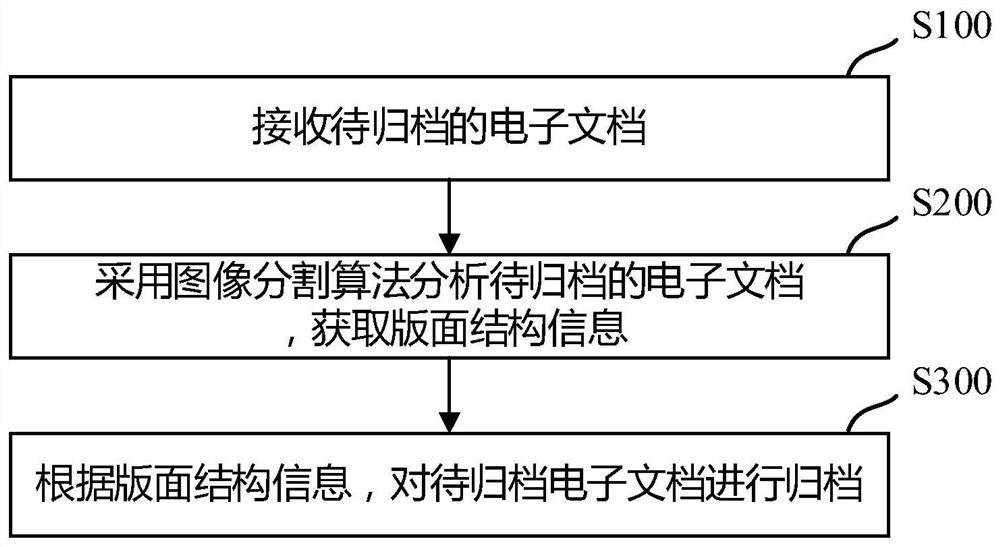
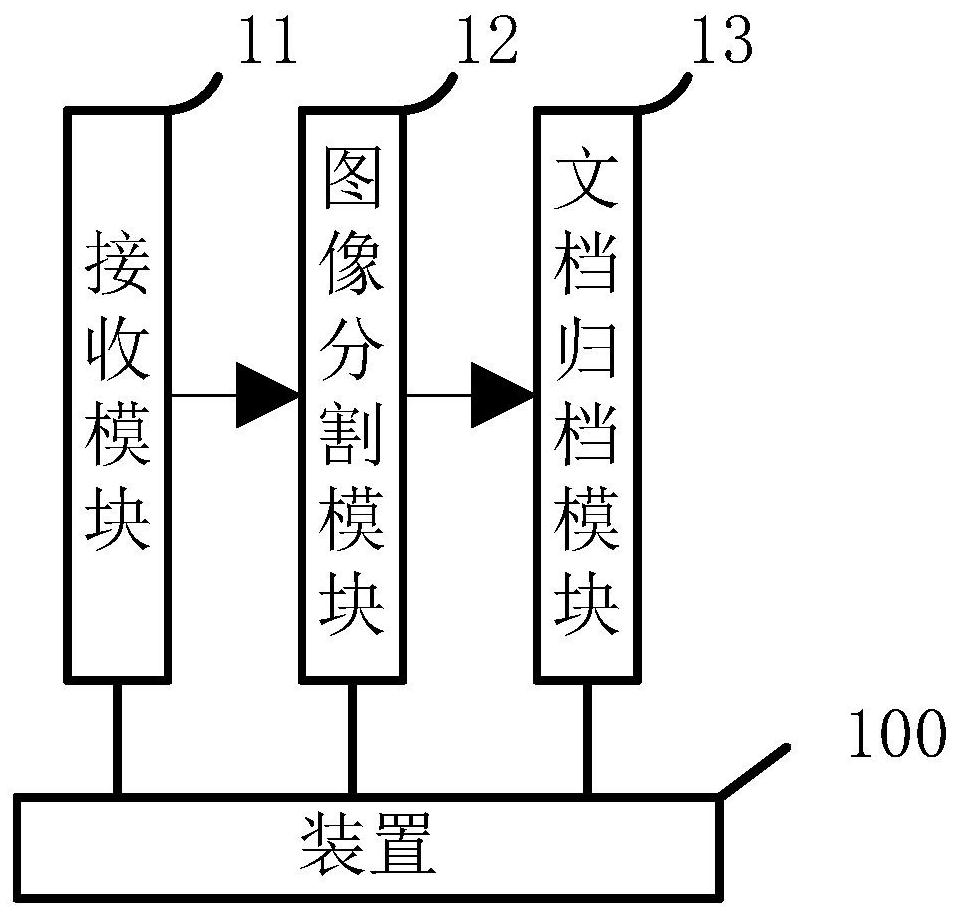
Electronic document filing method and device
ActiveCN112733658AImplement classificationHigh precisionImage enhancementImage analysisElectronic documentImage segmentation algorithm
Owner:BEIJING THUNISOFT INFORMATION TECH
Data transmission method, data transmission equipment and data transmission system
InactiveCN103501335ASolve the problem that data transfer cannot be performedSolve wasteTransmissionUser needsComputer terminal
The invention provides a data transmission method, data transmission equipment and a data transmission system. The data transmission method comprises the following steps of determining whether a connection is established between a first terminal and a second terminal or not; acquiring the identification information of a first client installed in the first terminal; transmitting the identification information to a second client of the second terminal. By adopting the data transmission method, the data transmission equipment and the data transmission system provided by the invention, the problems that wasting of resources is caused and the efficiency is low due to the fact that data transmission cannot be performed between different clients and user requirements had to be reintroduced when a new client is enabled can be solved.
Owner:BEIJING QIHOO TECH CO LTD +1
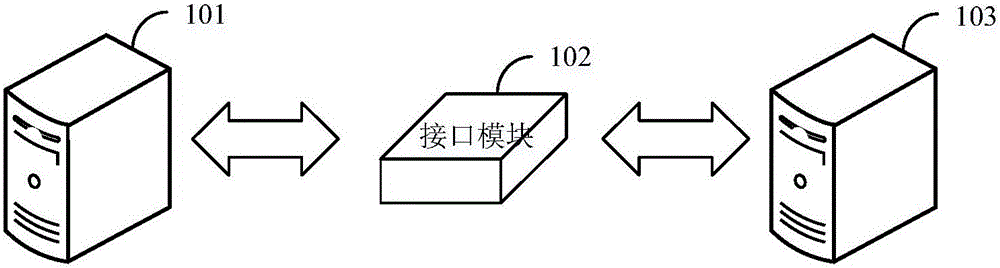
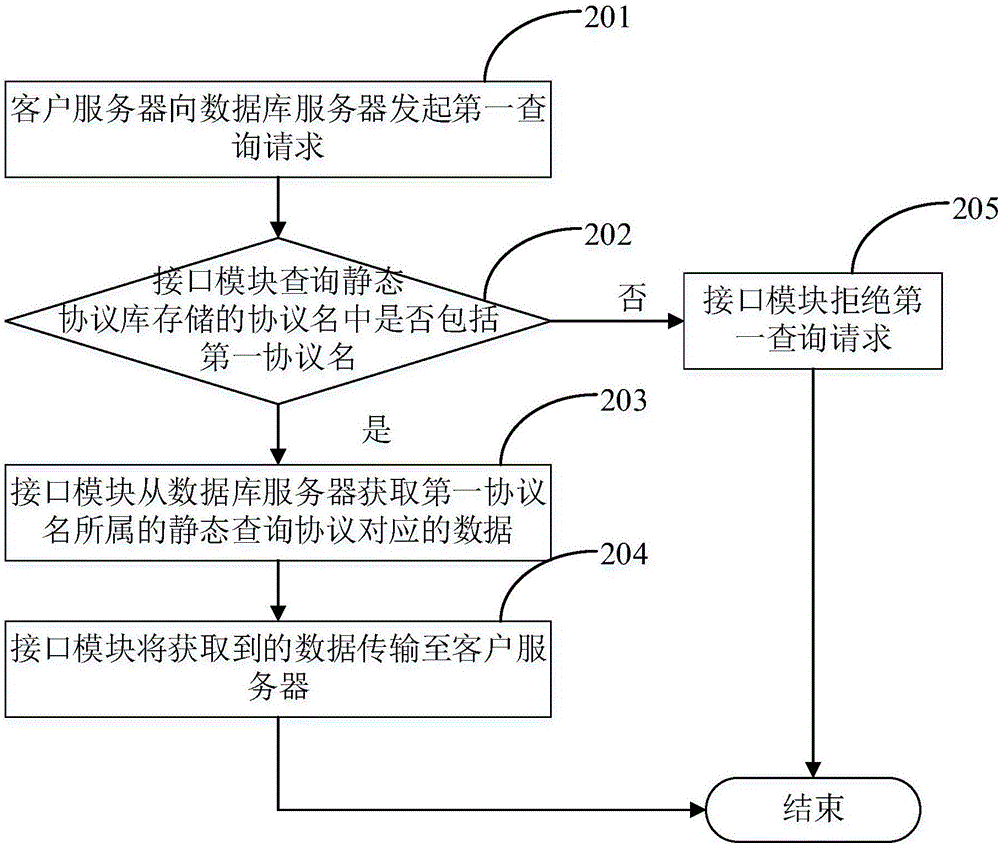
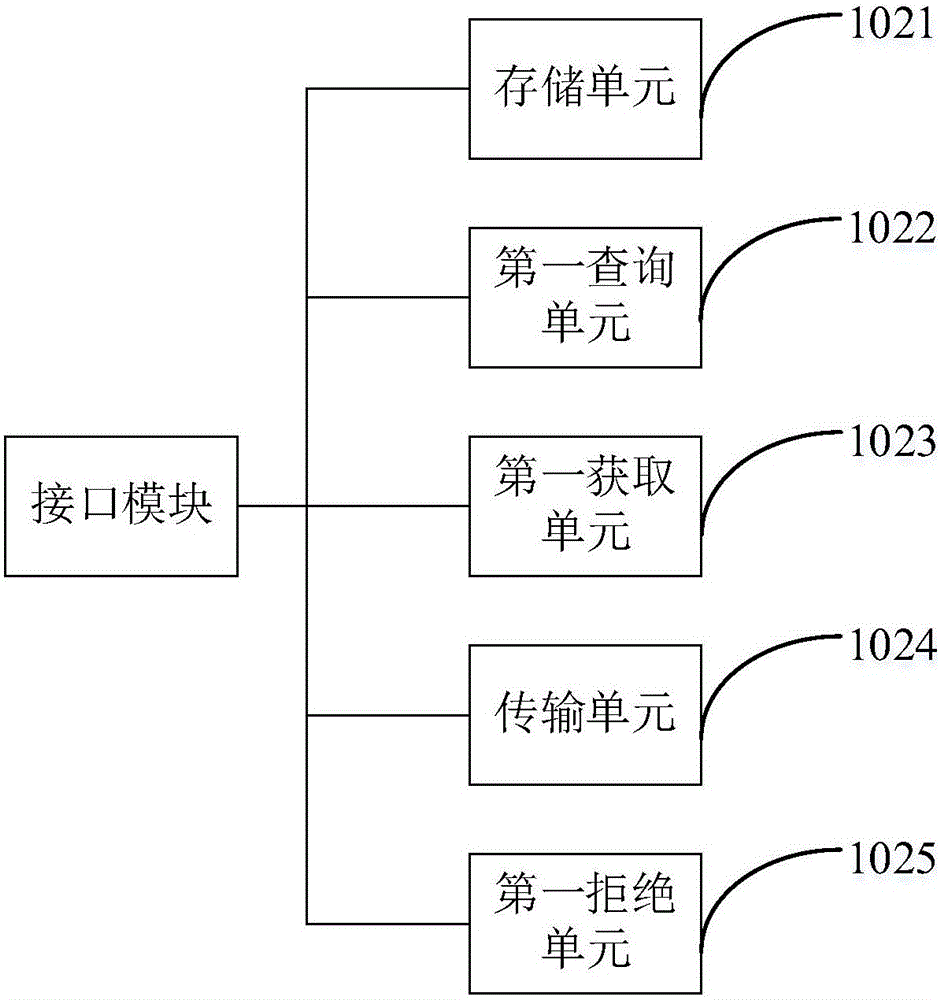
Data inquiry method and system
ActiveCN106202361AImprove data transfer efficiencyAvoid data redundancy and transmission channel congestionSpecial data processing applicationsClient-sideData transmission
The invention discloses a data inquiry method and system. The method comprises the following steps: adding an interface module into a database server; setting a static protocol base for storing static inquiry protocols, wherein the static inquiry protocols correspond to data in the database server; sending a first inquiry request to the database server by a client server, wherein the first inquiry request carries a first inquiry protocol; inquiring whether the static inquiry protocol matched with the first inquiry protocol is stored in the static protocol base or not by the interface module; if so, acquiring data corresponding to the static inquiry protocol matched with the first inquiry protocol and transmitting the data to the client server; otherwise, rejecting the first inquiry request. By adopting the data inquiry method and system, the disadvantages in the prior art that data redundancy and blocked transmission channels are caused when a client and a target source server are in interface butt joint are overcome; and an interface model and a customer server are matched and the aim of data slimming by utilizing the static inquiry protocols and dynamic inquiry protocols is realized, so that the data transmission efficiency is improved.
Owner:SHANGHAI CTRIP COMMERCE CO LTD
Instance deployment method and system
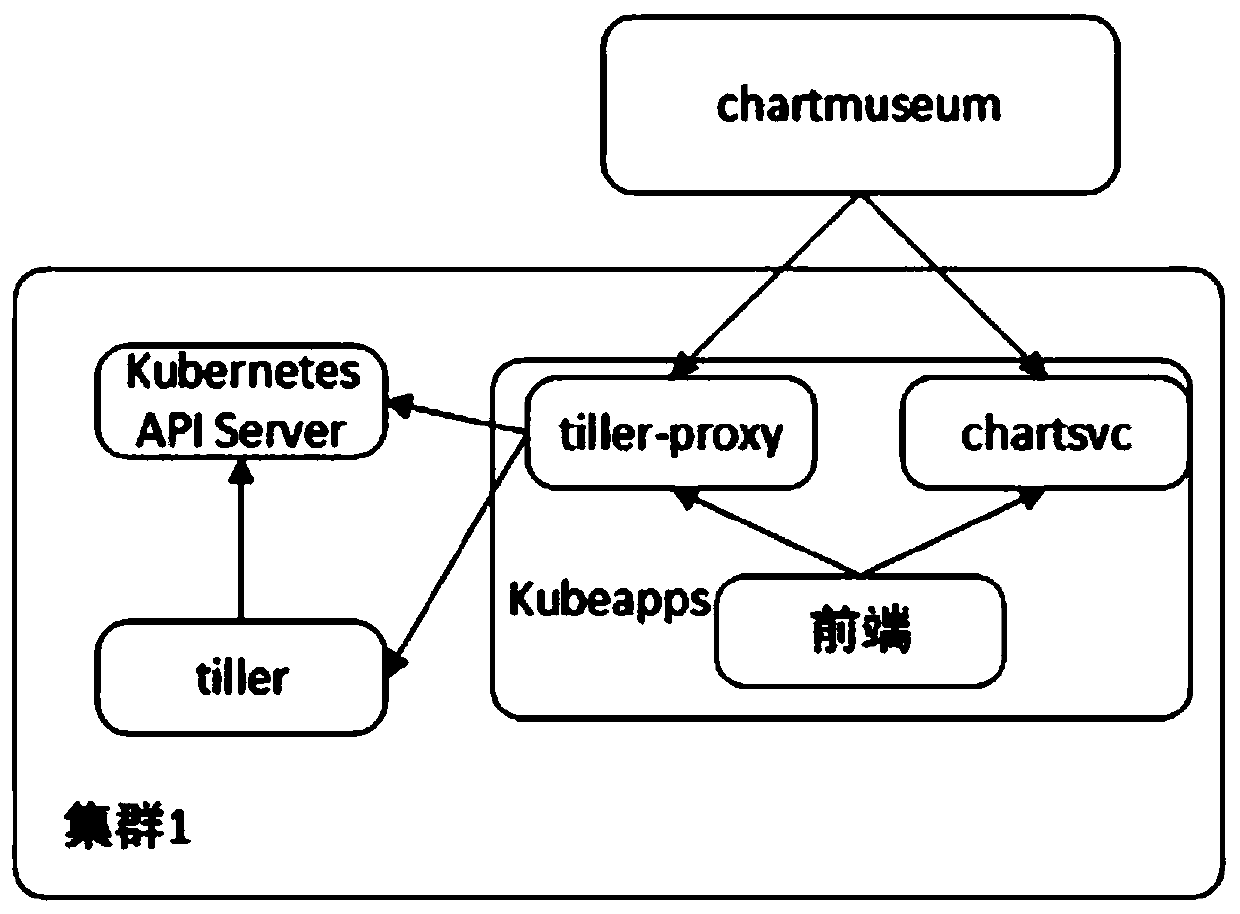
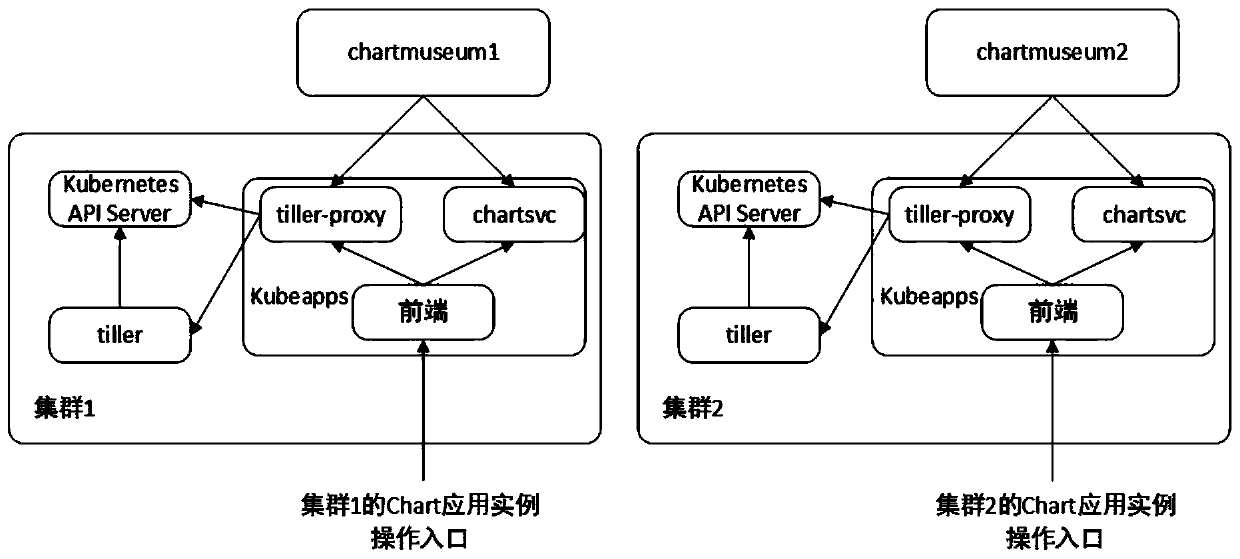
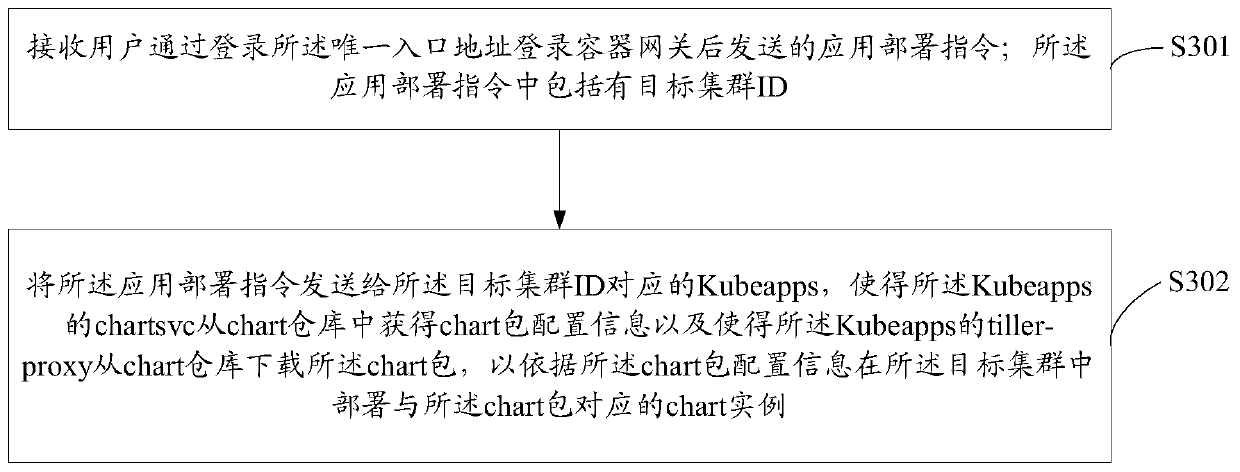
PendingCN110990025AImplement deploymentSave cluster resourcesSoftware deploymentEnergy efficient computingOperating systemDistributed computing
The embodiment of the invention provides an instance deployment method and system. The method is applied to a cluster management system. The cluster management system comprises a container gateway forsetting a unique entry address for a plurality of clusters. The method comprises the following steps that: an application deployment instruction sent by a user after logging in the container gatewaythrough logging in the unique entry address is received, the application deployment instruction comprises a target cluster ID; the application deployment instruction is sent to Kubeapps correspondingto the target cluster ID, so that the chartsvc of the Kubeapps obtains chart packet configuration information from a chart warehouse, and the tiler-proxy of the Kubeapps downloads a chart packet fromthe chart warehouse, so that a chart instance corresponding to the chart packet is deployed in the target cluster according to the chart packet configuration information. Therefore, the deployment ofthe chart instances in the plurality of clusters can be realized through the container gateway provided with the unique entry address, and a front end is not needed to be deployed for the clusters; and therefore, cluster resources are saved, and data redundancy is avoided.
Owner:WUXI CHINAC DATA TECH SERVICE
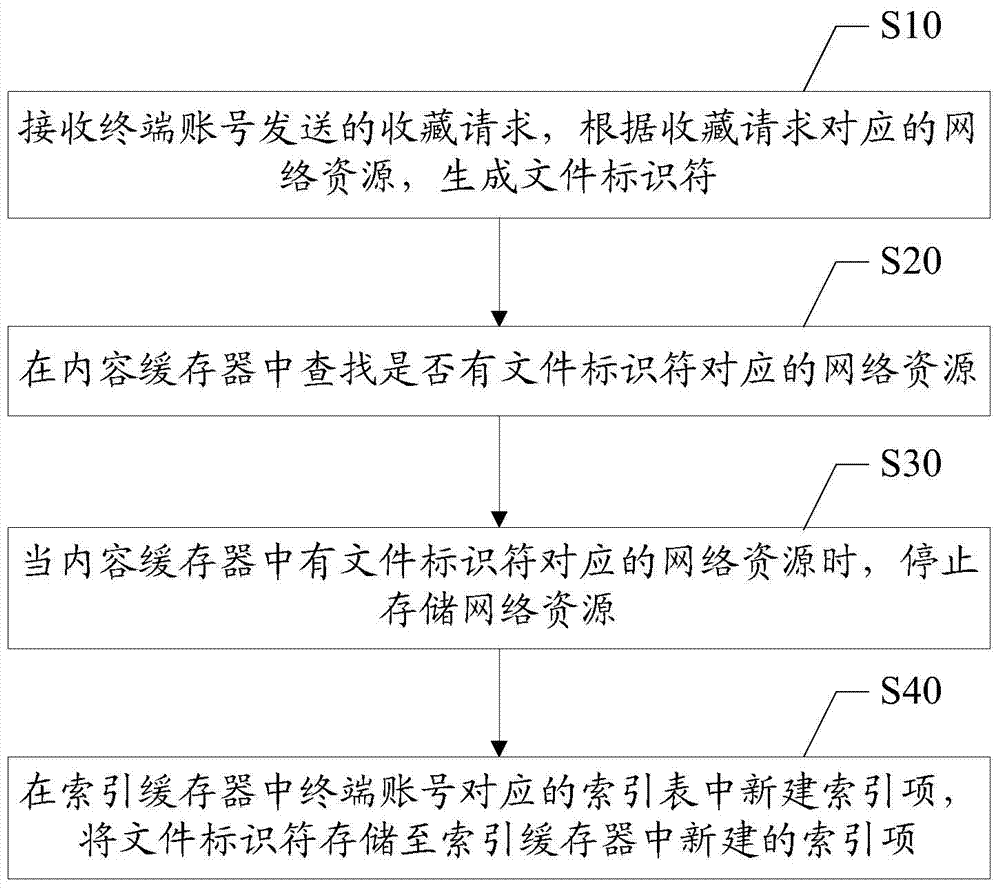
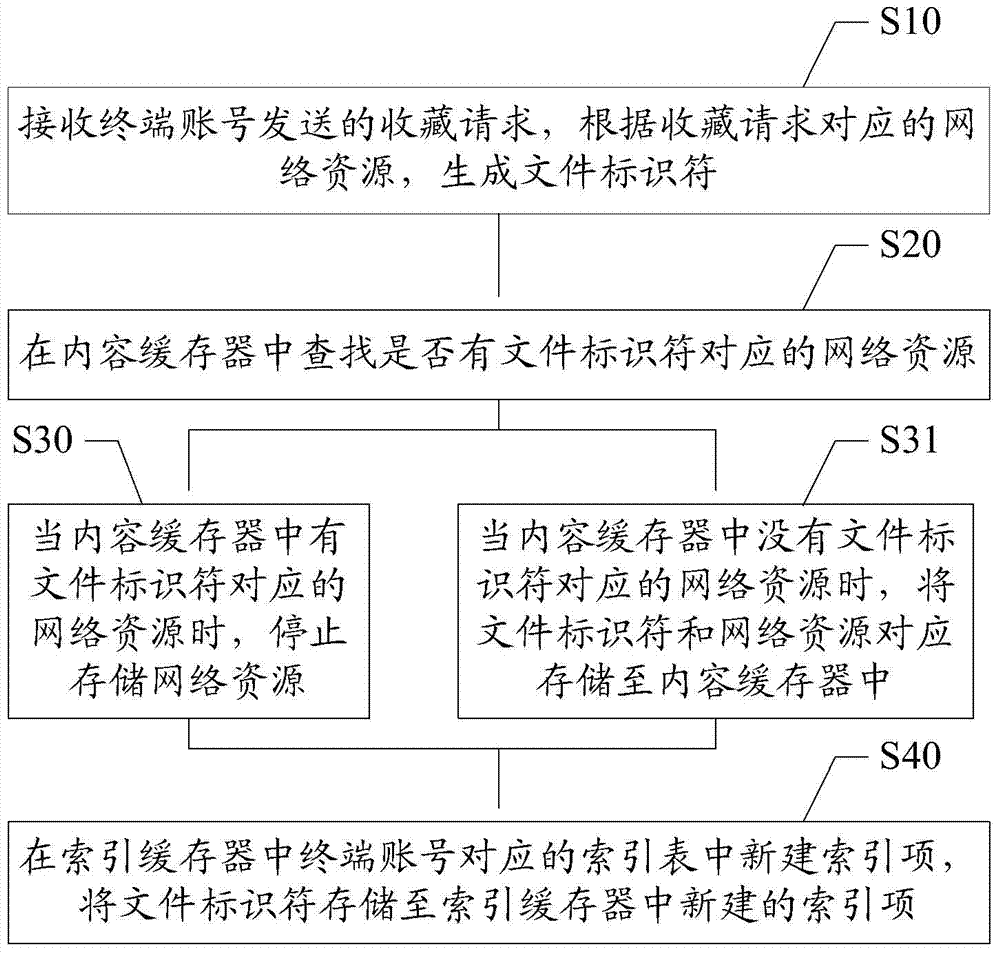
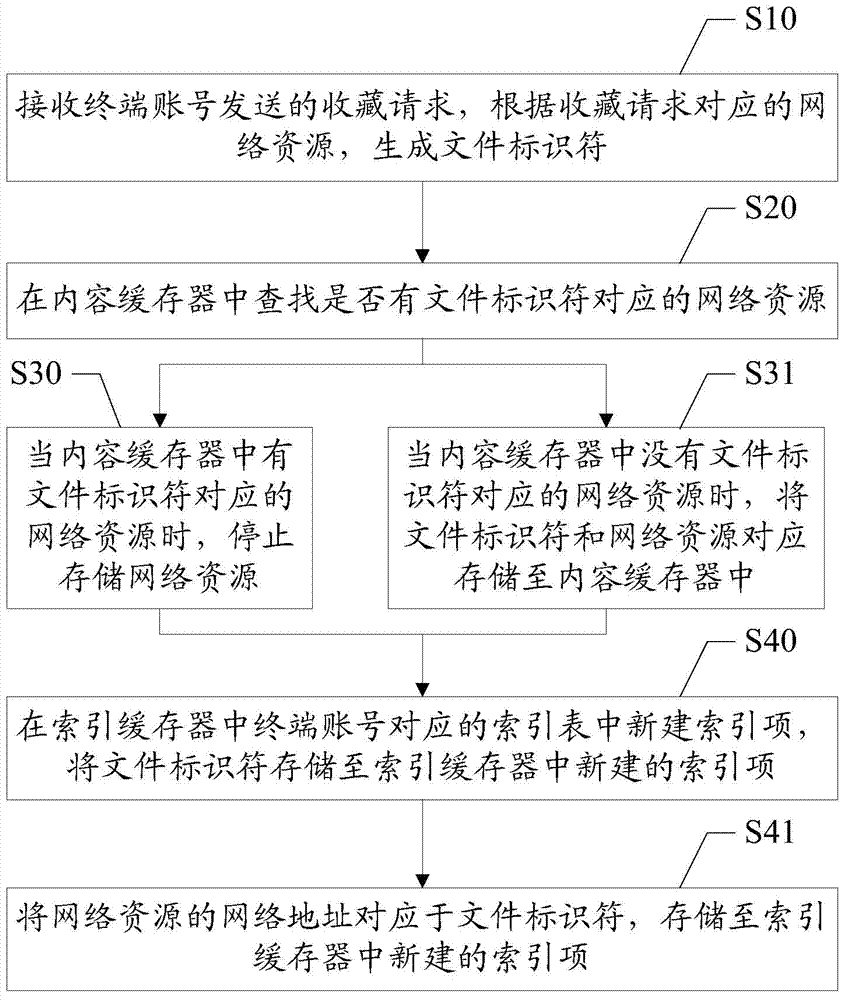
Network resource collection processing method and server
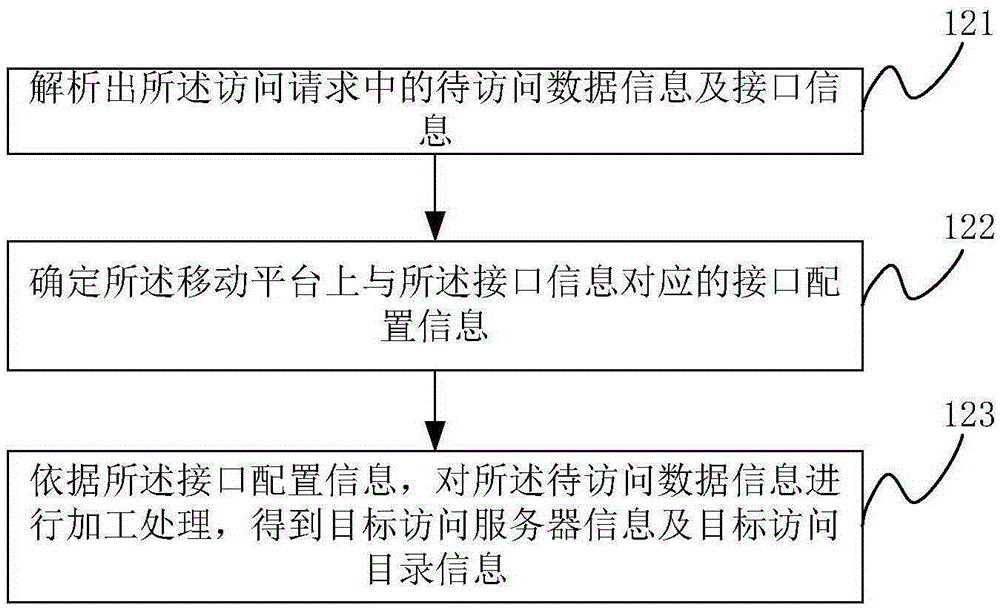
The invention discloses a network resource collection processing method and a server. The network resource collection processing method comprises the following steps: receiving a collection request sent by a terminal account, and generating a file identifier according to network resources corresponding to the collection request; looking up whether or not network resources corresponding to the file identifier exist in a content buffer; when the network resources corresponding to the file identifier exist in the content buffer, stopping storing the network resources; and newly building an index entry in an index table corresponding to the terminal account in an index buffer, and storing the file identifier in the newly-built index entry in the index buffer. Indexes and the network resources are stored separately, and the network resources are not stored repeatedly when the network resources are already stored in the content buffer, so that data redundancy caused by repeated storage is avoided; the storage space occupied by the network resources is reduced; and the waste of the storage space is avoided.
Owner:TENCENT TECH (SHENZHEN) CO LTD
A soil moisture data acquisition method and device
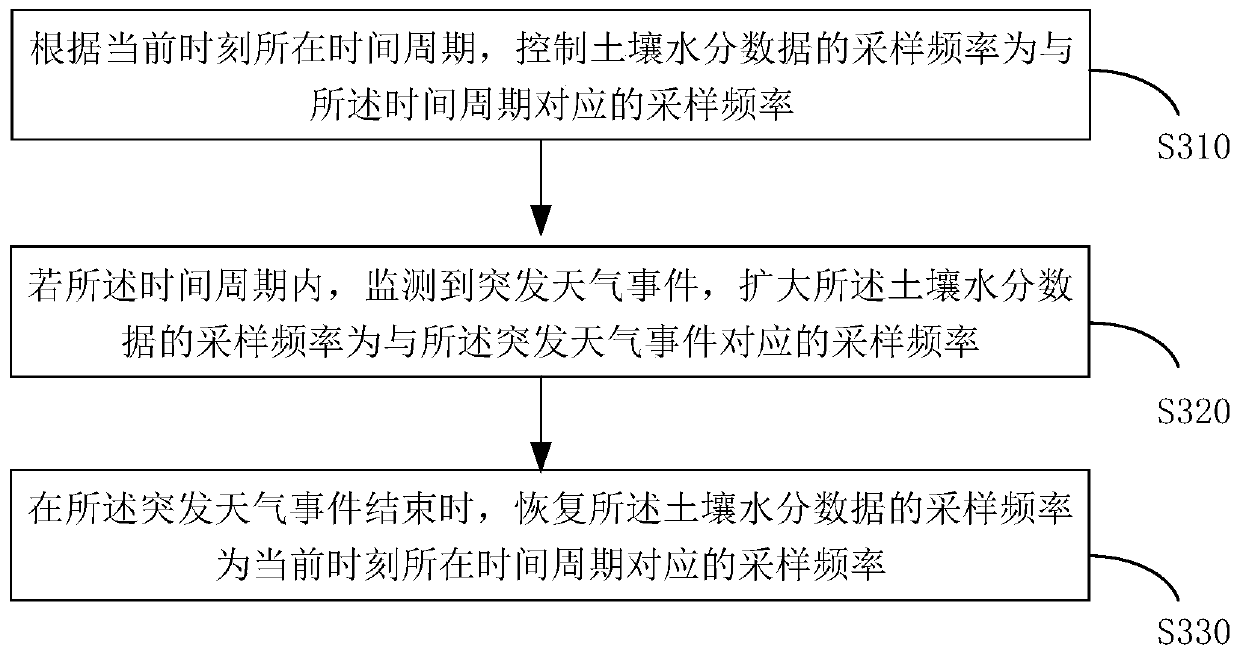
InactiveCN109711757AKeep abreast of moisture changes in timeLess infiltrationEarth material testingResourcesData acquisitionMoisture
The embodiment of the invention provides a soil moisture data collection method and device, and relates to the technical field of environment monitoring, and the method comprises the steps: controlling the sampling frequency of soil moisture data to be a sampling frequency corresponding to a time period according to the time period of a current moment; if the sudden weather event is monitored within the time period, the sampling frequency of the soil moisture data is increased to be the sampling frequency corresponding to the sudden weather event; and recovering the sampling frequency of the soil moisture data as the sampling frequency corresponding to the time period of the current moment when the sudden weather event is finished. According to the scheme, when weather changes, the sampling frequency can be expanded in time, then complete soil moisture data can be collected, the sampling frequency can be recovered at other times, and therefore data redundancy is avoided, and energy consumption of data collection is reduced.
Owner:QINGHAI UNIVERSITY
Data management method and data management device
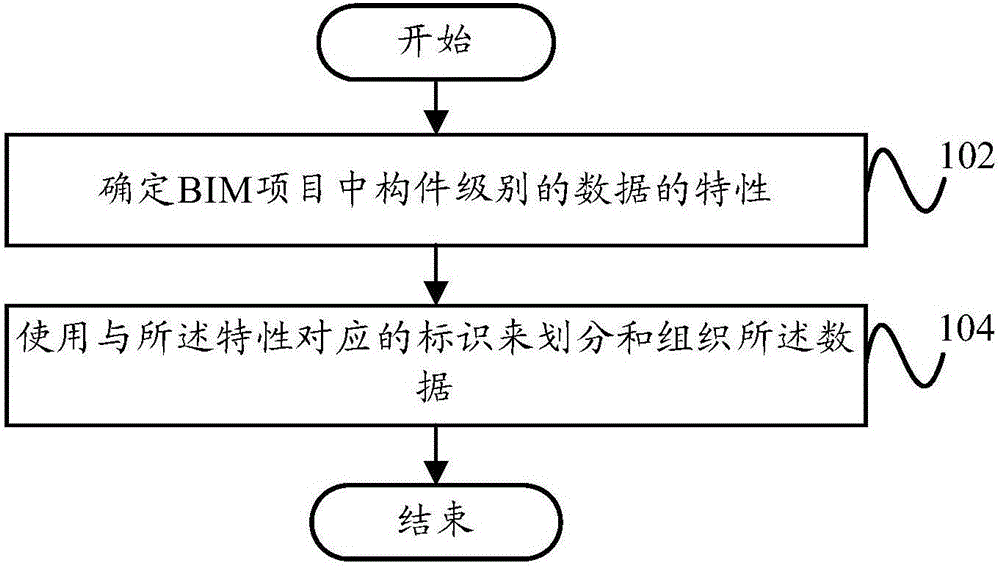
InactiveCN106354824AAvoid data redundancyAvoid excessive costSpecial data processing applicationsData managementBuilding information modeling
The invention provides a data management method and a data management device. The data management method includes the steps: determining characteristics of data of component levels in a BIM (building information modeling) item; using identifications corresponding to the characteristics to divide and organize the data. According to the technical scheme, a large amount of data redundancies can be avoided, so that high storage cost is avoided, and the access performance of the data is ensured.
Owner:GLODON CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com