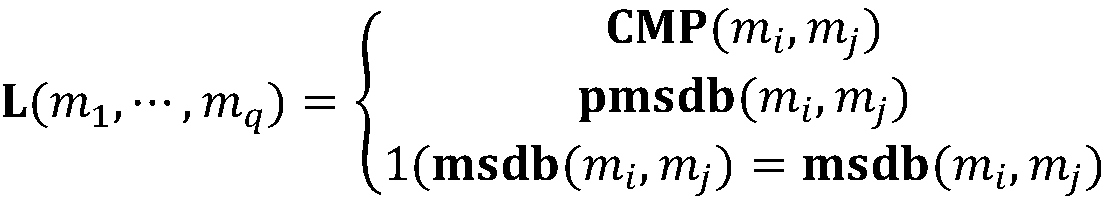Weak-leakage and high-efficiency exposing encryption method
An encryption method and encryption algorithm technology, applied in the field of encryption, can solve problems such as low efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0060] Taking the encryption and comparison of the integer data "1011" and "987" in the database as an example, the specific implementation of the algorithm will be described in detail below.
[0061] In view of the fact that there are many schemes for the key hash algorithm, pseudo-random function and trapdoor permutation function that can be used in practical applications, SHA256 is exemplarily used as the algorithm of the pseudo-random function and key hash function in the following description. The data is expressed in hexadecimal, the security parameter λ is 128, and the plaintext space is assumed to be 10 bits.
[0062] 1. Algorithm initialization phase
[0063] Randomly select a subkey k with a length of 128 bits as;
[0064] 2A8D8F6503CF1A36CC548712AB840D52.
[0065] Then, randomly select another subkey with a length of 128 bits as:
[0066] A6810D0C6EF46EF324CC513D28650005,
[0067] Combined with HMAC-SHA256 to generate ∈ (different data length requirements can be...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com