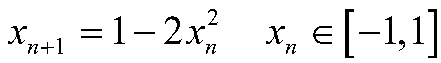Method for realizing random bit non-blind watermark based on chaos
An implementation method, a technology of random bits, applied in the fields of information security, image processing, and computer applications, which can solve the problems of different and unable to extract watermark information.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
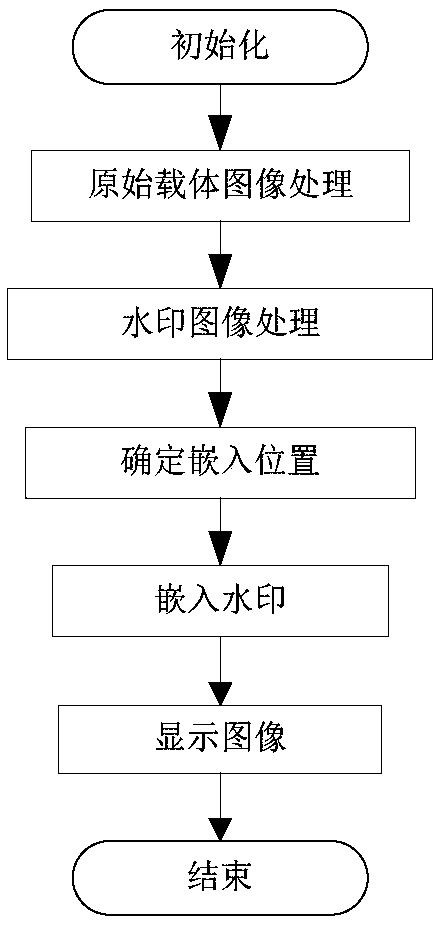
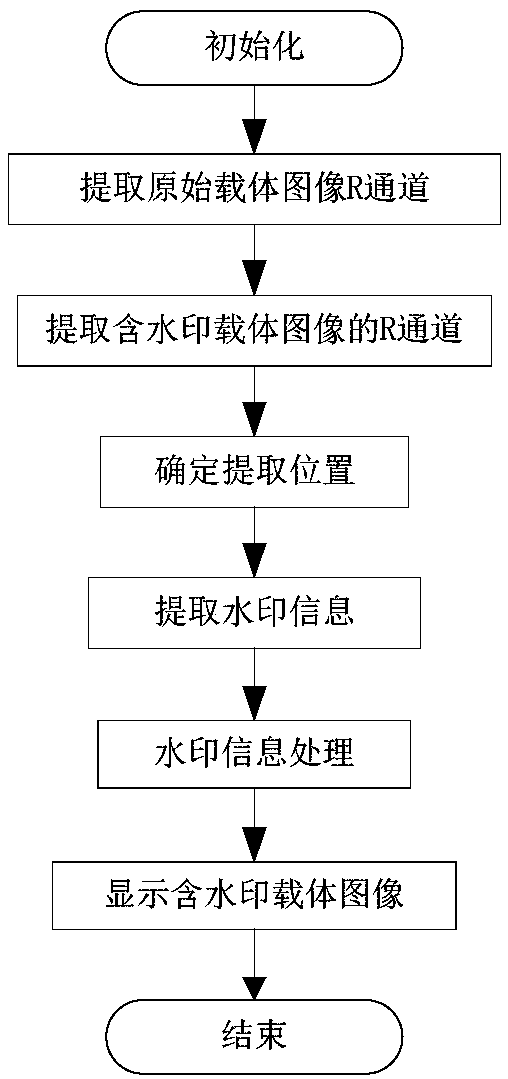
[0100] The random bit non-blind watermark is operated on each pixel in the carrier, and the position of the embedded watermark is not fixed. The specific implementation steps are divided into embedding process and extraction process.
[0101] For the convenience of understanding, the watermark here is only embedded in the R channel of the carrier image. In actual processing, the watermark can be embedded in multiple channels, and the method of embedding watermark in other channels is the same as that in R channel.
[0102] 1 Embedding process
[0103] The embedding process calculates the original watermark information with the carrier image and then embeds it into the carrier image.
[0104] (1) Original carrier image processing
[0105] Read in the original carrier image, obtain the size of the image, decompose it into channels, and divide it into R channel, G channel, and B channel.
[0106] For example, there is the original carrier image O, whose size is 4*4, which is ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com