Multi-chaos system based method of encrypting images related to plaintext
A chaotic system and encryption method technology, applied in the field of information security, can solve the problems of unpredictability, inability to effectively resist attack technology, and low security of low-dimensional cryptographic systems.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
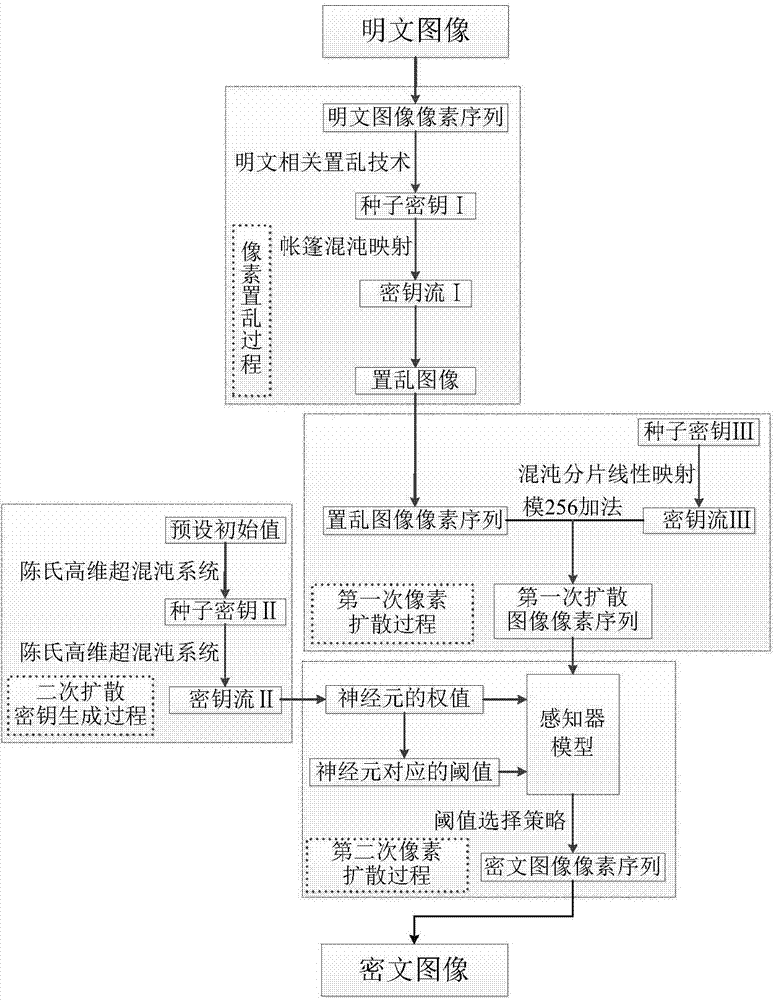
[0046] The specific implementation steps are as figure 1 The overall structure diagram and Image 6 The method flow chart is as follows:
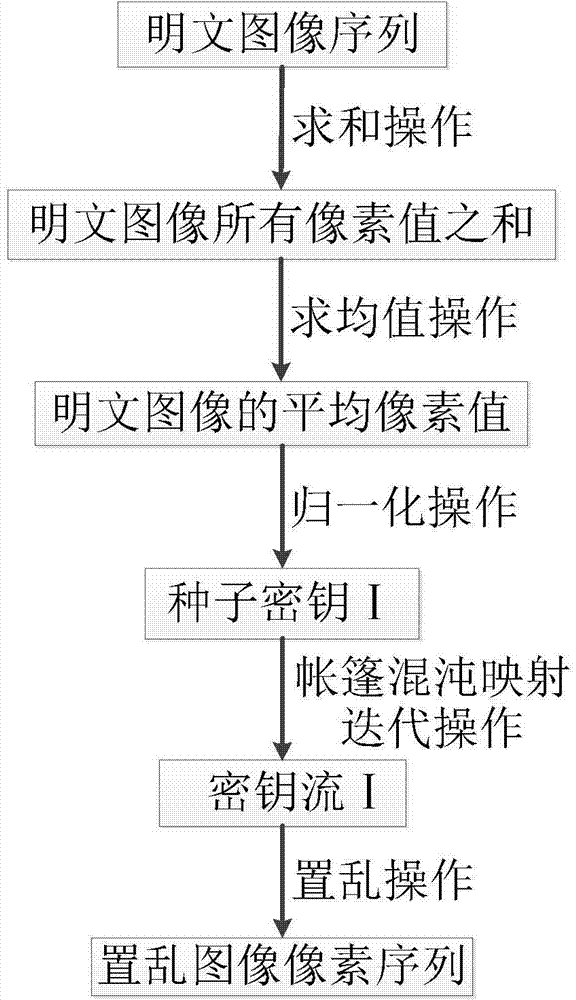
[0047] Step 1: Obtain the pixel data information of the plaintext image, and convert the pixel data information of the plaintext image into a sequence of plaintext images Calculate the sum of the pixel values of all pixels in the plaintext image, and calculate the average pixel value of the pixels, and perform normalization on the obtained average pixel value to obtain the initial value e of the tent chaos map as the seed key Ⅰ. Use the tent chaotic map to iterate L times to obtain a random sequence of real numbers Generating Keystream I Go to step 2;
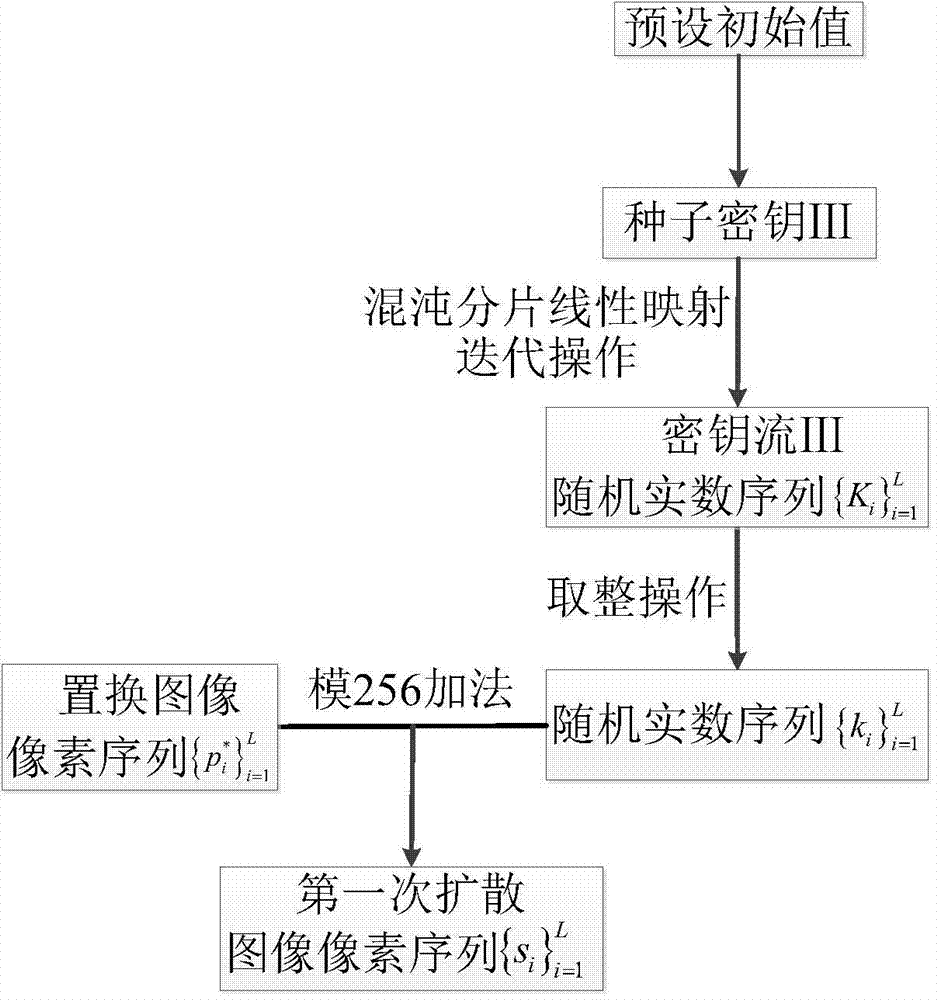
[0048] Step 2: Read a sequence of random real numbers Rearrange the values of this random sequence of real numbers from small to large to obtain a new sequence of real numbers Record the replacement subscript sequence in it plaintext image sequence according to The repla...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com